System and method for confidentiality-preserving rank-ordered search
a rank-ordered search and rank-ordered search technology, applied in the field of information search and retrieval, can solve the problems of low effort in addressing secure searching, system administrators and other personnel involved may not be trusted to have decryption keys, and conventional practices to accommodate such searches on hard-copy collections are extremely time-consuming and laborious
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
case 1
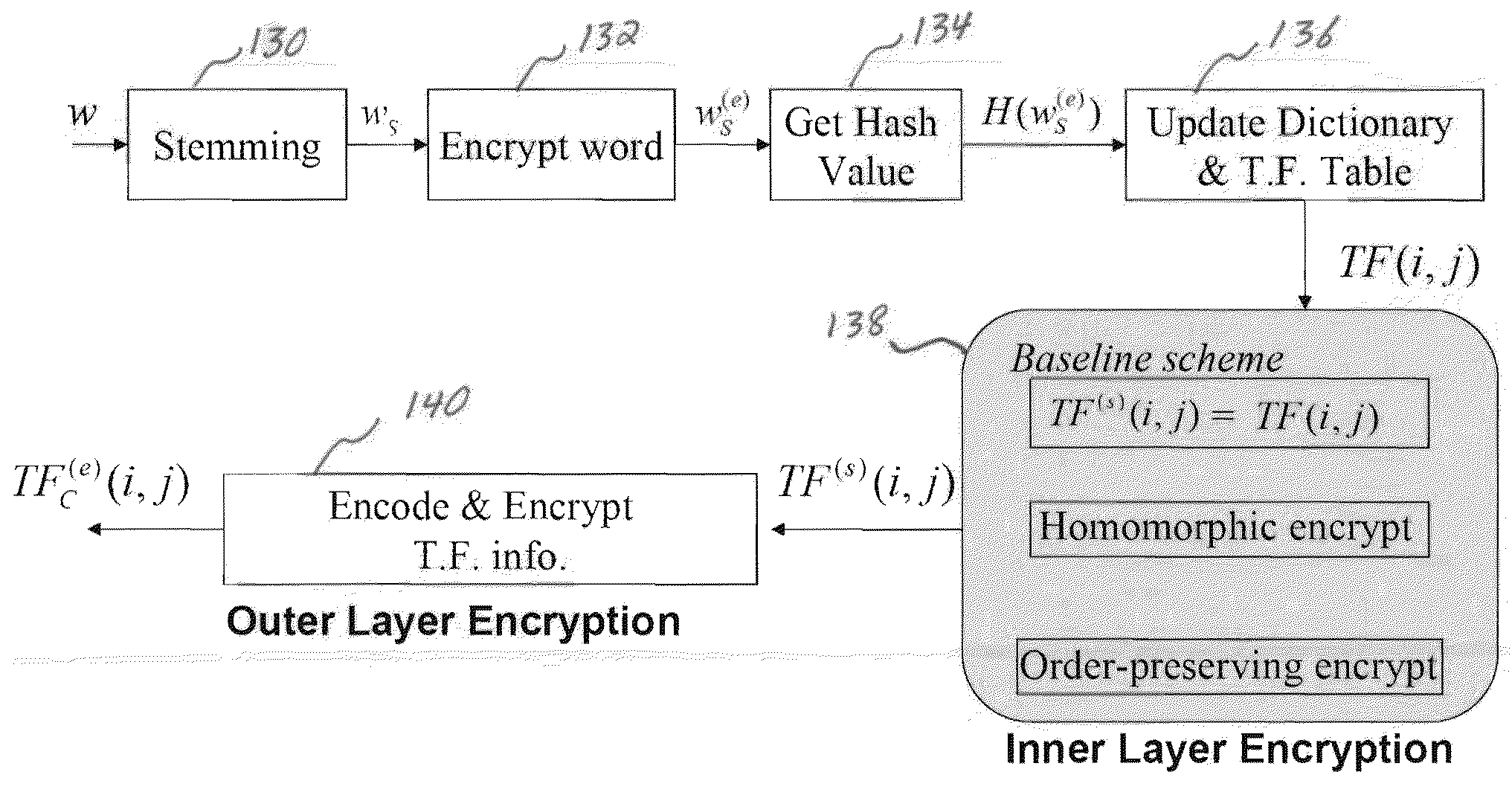
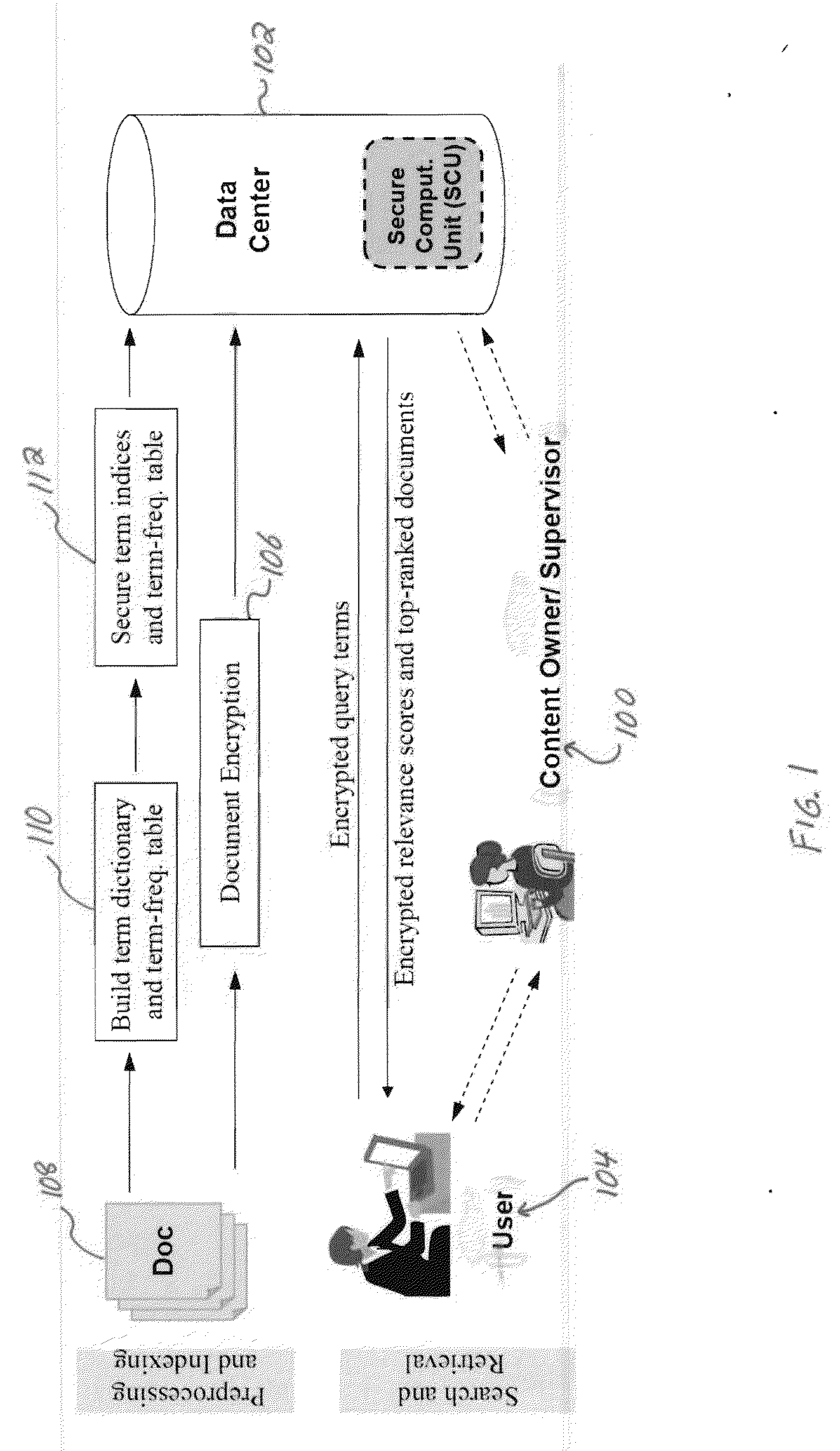
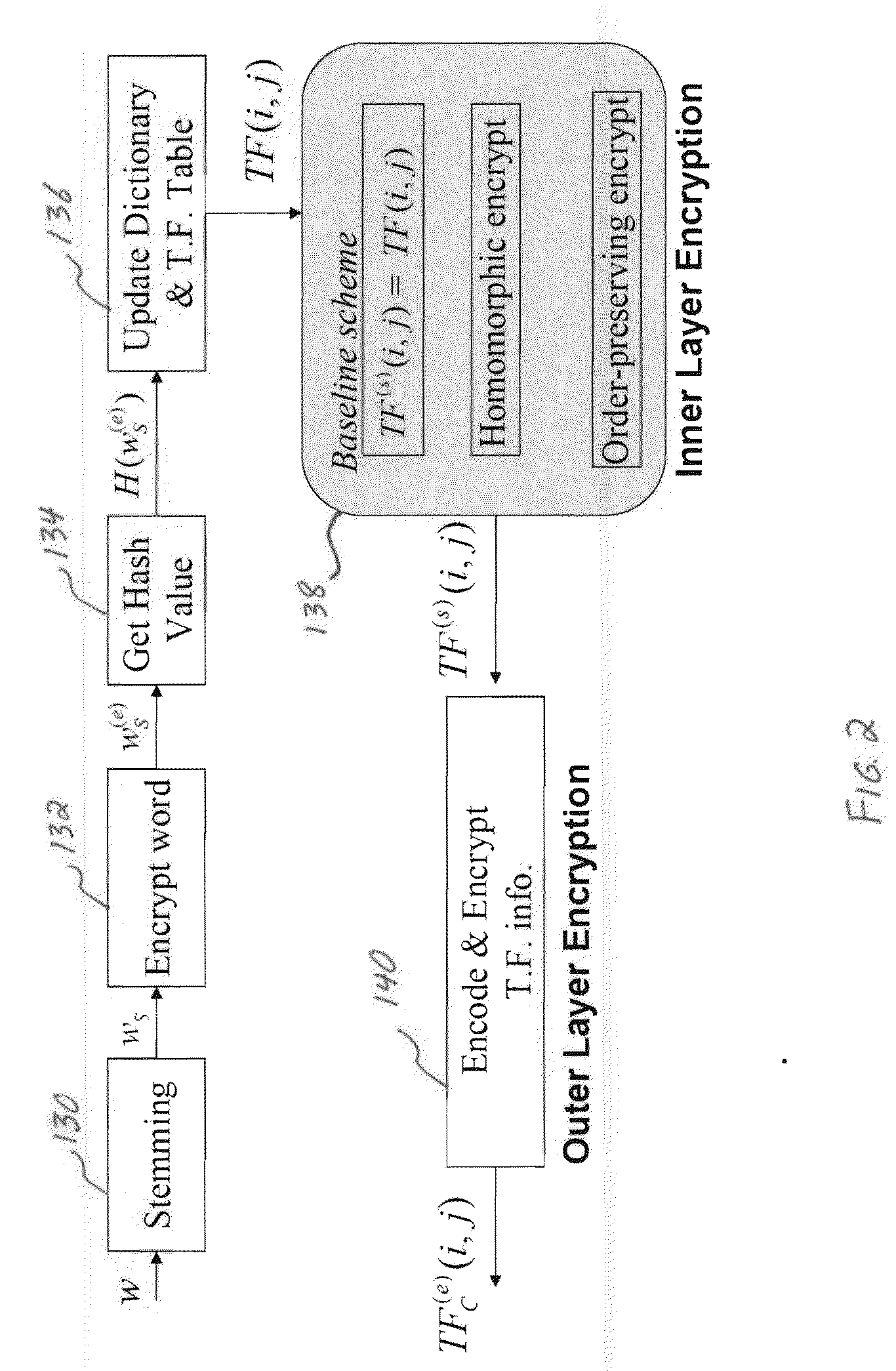
[0042] The content owner wants to search for some documents stored at the data center. He / she has a limited bandwidth connection with the data center, and needs to search through the encrypted content without downloading the entire collection. Furthermore, the content owner does not trust the data center with his / her unencrypted content. He / she wants to remotely search and retrieve top-ranked relevant documents without revealing the search terms, document content, and / or document index information to the data center. This scenario will be referred to as the confidentiality preserving baseline model, as discussed below, where the scheme enables both the confidentiality protection and the use of term frequency (discussed below) to achieve secure and efficient retrieval.
case 2
[0043] Next, consider the scenario where a user, who is not the content owner, wants to search for a particular phrase in the set of confidential documents held by the data center. This scenario may arise in a number of cases, for example, where the user may be a scholar or a low-level analyst who wants to search relevant documents from a private / classified collection, and may need clearance only for the top-ranked documents. The user may also be the opposing side in a litigation requesting relevant documents from a digital collection (e.g. e-mails) be turned in by the content owner's side. In general, the content owner does not trust the data center with the document content or the term frequency values. However, it is considered herein that the data center has a secure computing unit (SCU), which is trusted by the content owner to some degree. Depending on the level of trust on the SCU by the content owner, the following exemplary scenarios are identified:
case 2a
[0044] the content owner trusts the SCU both with the plain-text documents and the associated term-frequency table (discussed below).
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com