Home security video system using internet technique
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
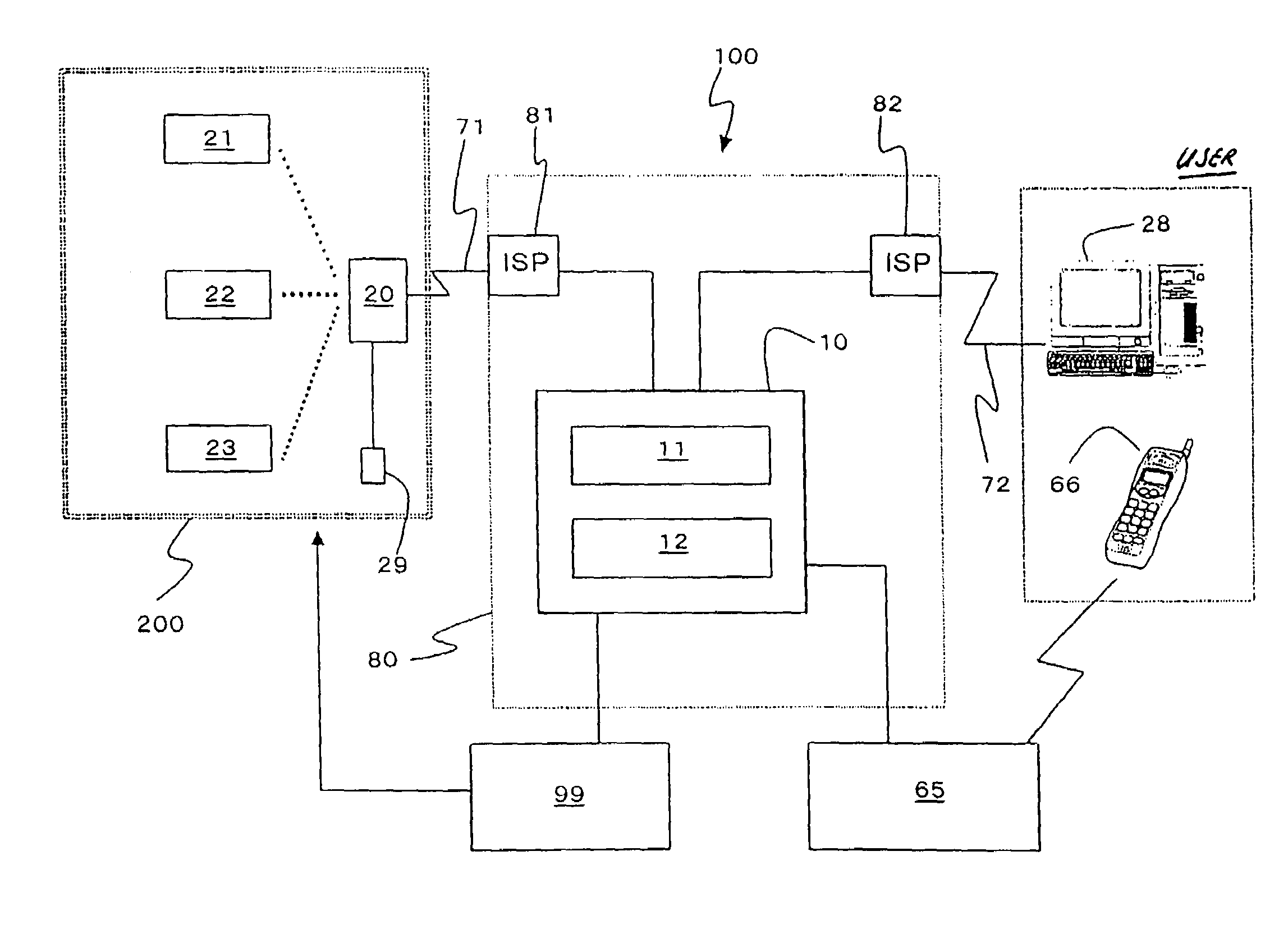
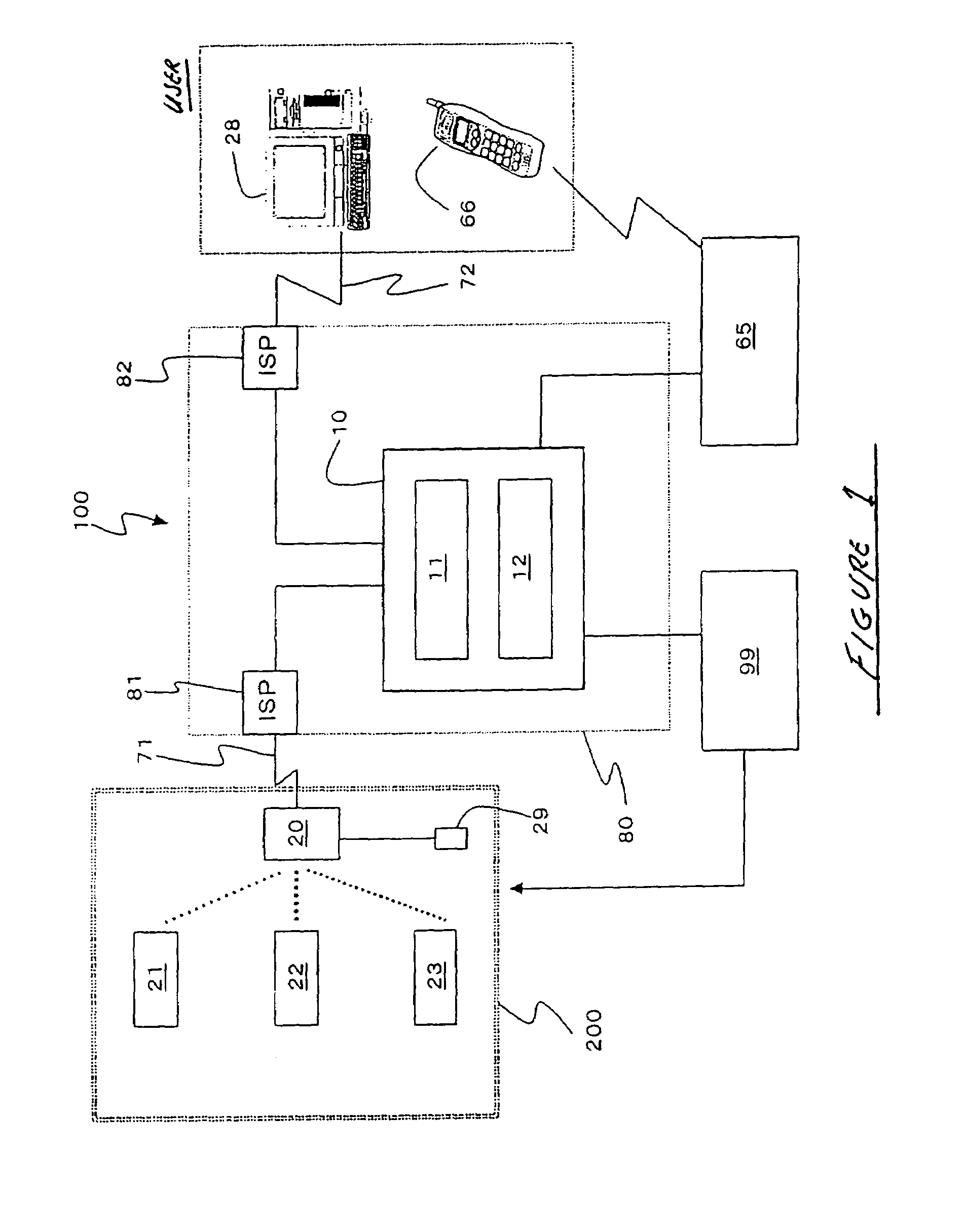
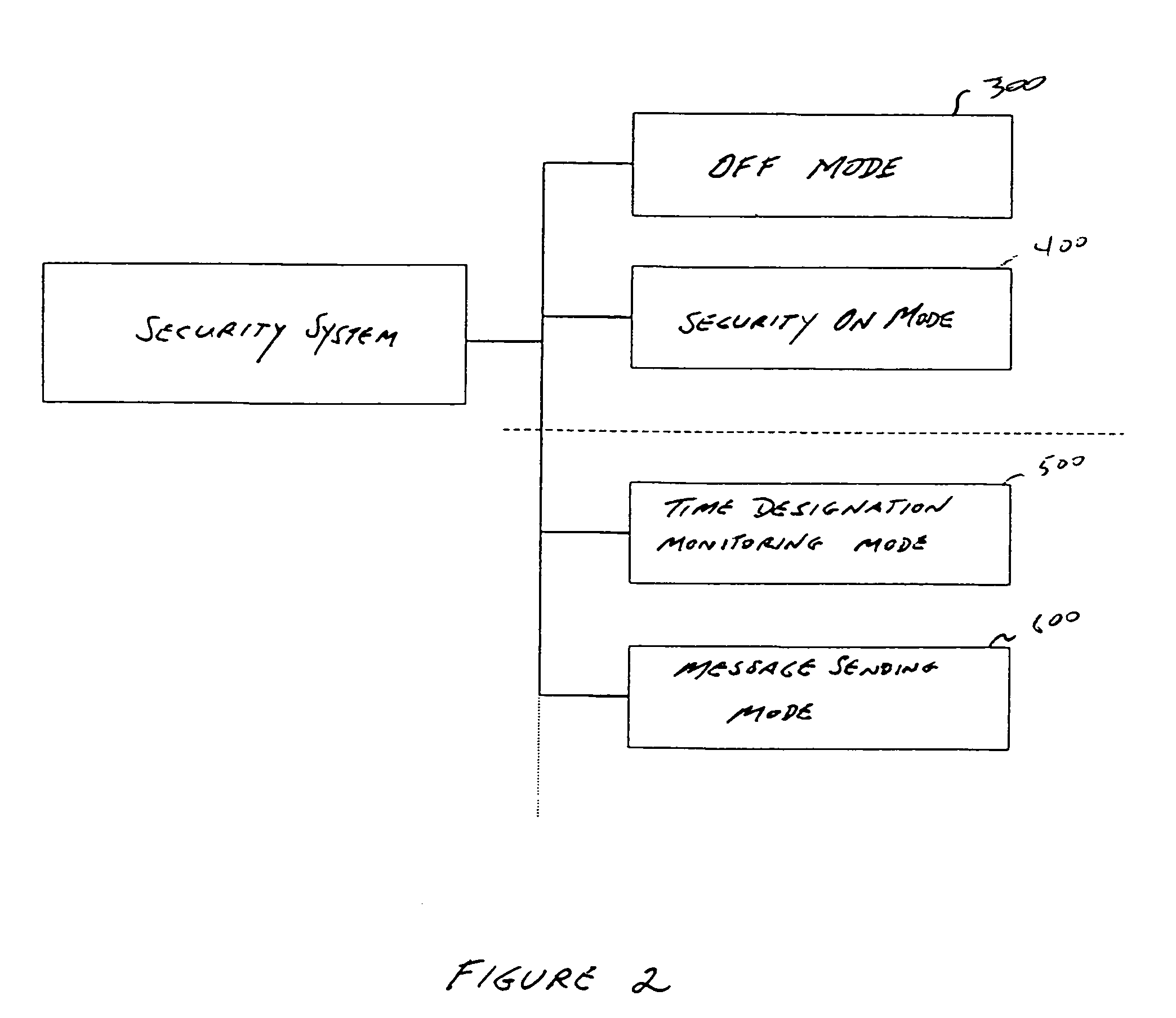
[0026]We shall now present a detailed description of the structure of the security system that is a desirable mode of execution of this invention by reference to the appended figures.
[0027]
10server means11web server12data base server20communications device21, 22, 23camera devices100 security system
[0028]FIG. 1 is a schematic diagram of the security system 100 that is a desirable embodiment this invention. It can be understood that this security system 100, which makes use of the internet line 80, is constructed with server means 10 as its center. Server means 10 contains the web server 11 and the database server 12. On the other hand, several camera devices 21, 22 and 23 and at least one communications device 20 are installed in the place 200 that is to be monitored in the buildings for each family. When security system 100 is used for home security, camera devices 21, 22 and 23 are installed in the necessary sites inside and outside the house. Although there are three camera device...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com