Method for auditing safely system log
A system log and security audit technology, applied in the computer field, can solve the problem of unable to prevent adding its own log, unable to prevent attackers from deleting the log, etc., to achieve the effect of improving credibility, eliminating dependencies, and ensuring confidentiality and integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
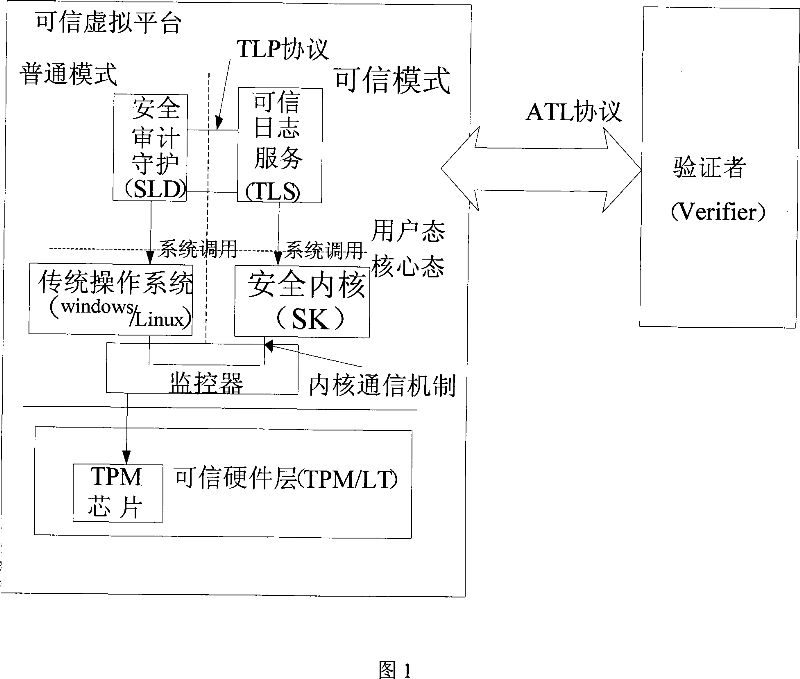
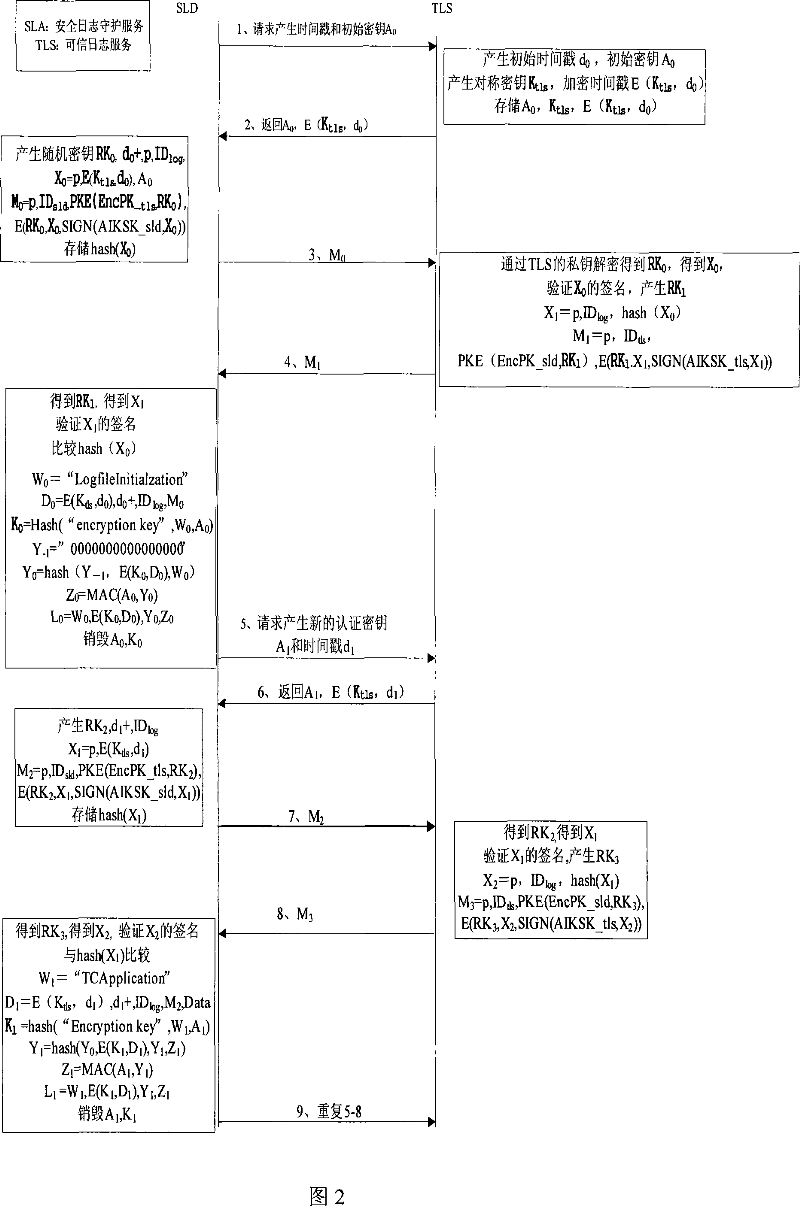
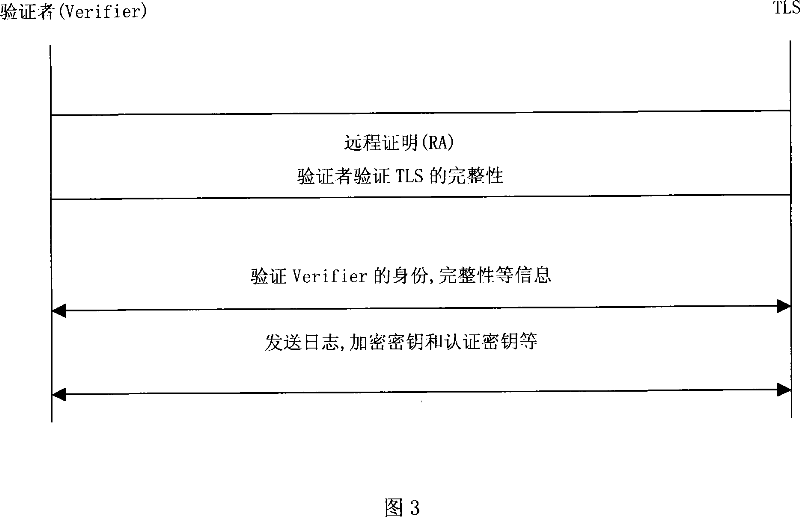
[0059] As shown in FIG. 1 : it is a structural diagram of a security audit log in the most simplified mode. In the figure, the security audit daemon module (SLD) and the trusted log service module are located on a virtual platform, which may be Microsoft's next-generation operating system Vista or a system platform based on a microkernel, such as Nizza. The security audit guard module runs on a traditional operating system, such as the windows system. The security audit guard module is responsible for generating log information and interacting with the trusted log service module to ensure that the generated log information is tamper-proof. The security audit guard module stores a pair of public and private key pairs generated by the TPM. The trusted log service module runs in the trusted mode. The trusted log service module stores a pair of public-private key pairs generated by the TPM for signing and authentication of messages. The log service can be verified by the remote ce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com