User safety protection method of broadband access equipment
A technology for access equipment and security protection, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as inability to access the Internet, hidden dangers of DHCP access, etc., to achieve a simple implementation scheme and reduce packet processing amount of effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
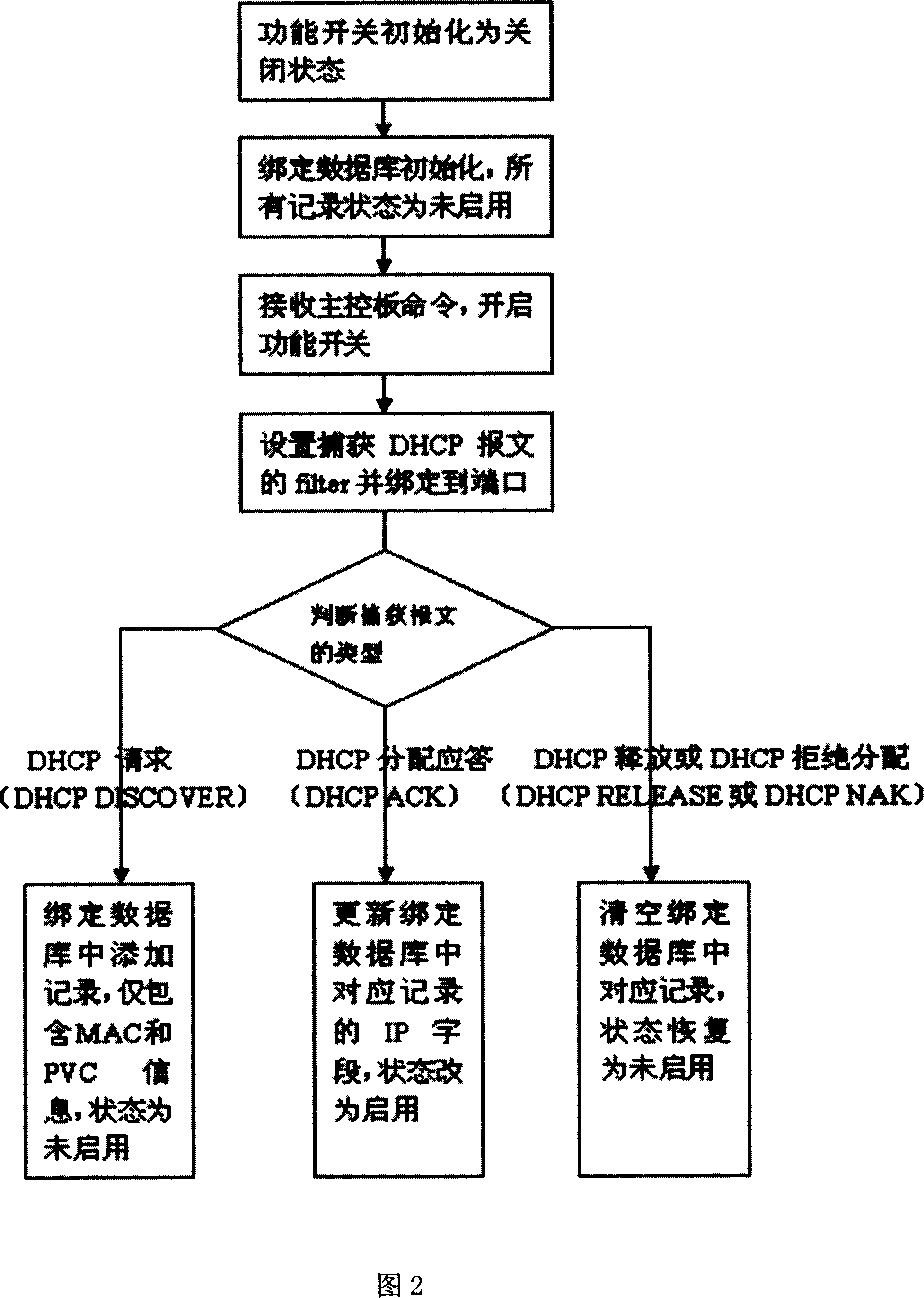
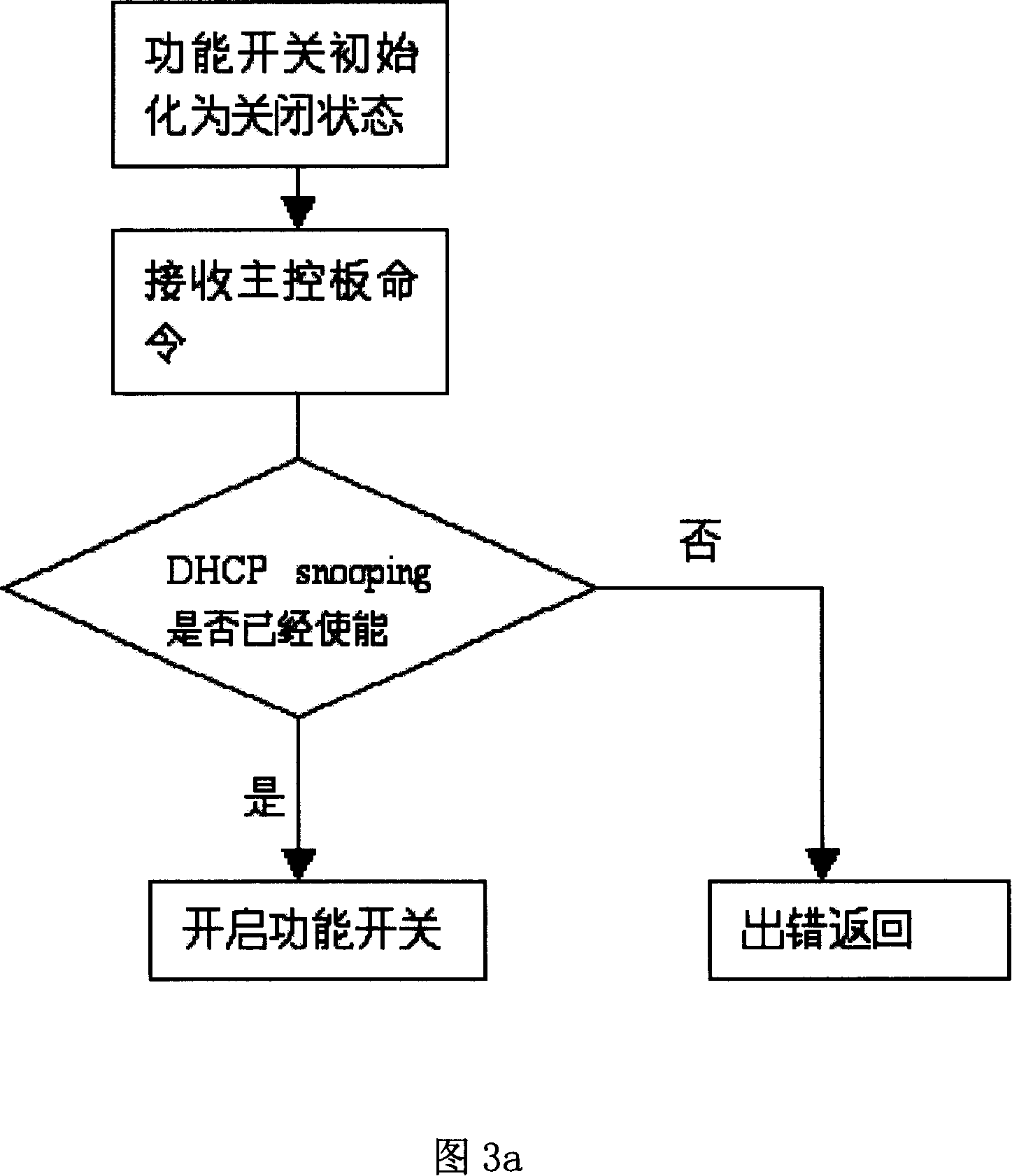
[0035] The DHCP snooping function is realized on a digital subscriber line access multiplexer (Digital Subscribe Loop Access Multiplexer, DSLAM). Its specific functions include: extracting uplink and downlink DHCP messages, creating and maintaining a binding database (binding database) for user ports, each entry in the database includes the following fields: user host IP address, user host MAC Address, permanent virtual circuit channel (Permanent Virtual Circuit, PVC) used by the user, and record status status (indicating whether the record is enabled), where IP / MAC / PVC are key fields.
[0036] On the basis of realizing the DHCP snooping function, realize the IP Source guard function: restrict and filter the passage of user packets: users cannot access the network before obtaining a legal IP address through DHCP, and at this time DSLAM only captures DHCP packets and discards them. All other packets; illegal packets that steal other people's IP addresses will be discarded at th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com