A logging-on process cipher protection method by means of background synchronization
A password-protected, background technology, applied in the computer field, can solve the problems of PIN code physical card issuance costs and high cost, not widely used, losses, etc., to prevent important information from leaking and avoid loopholes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
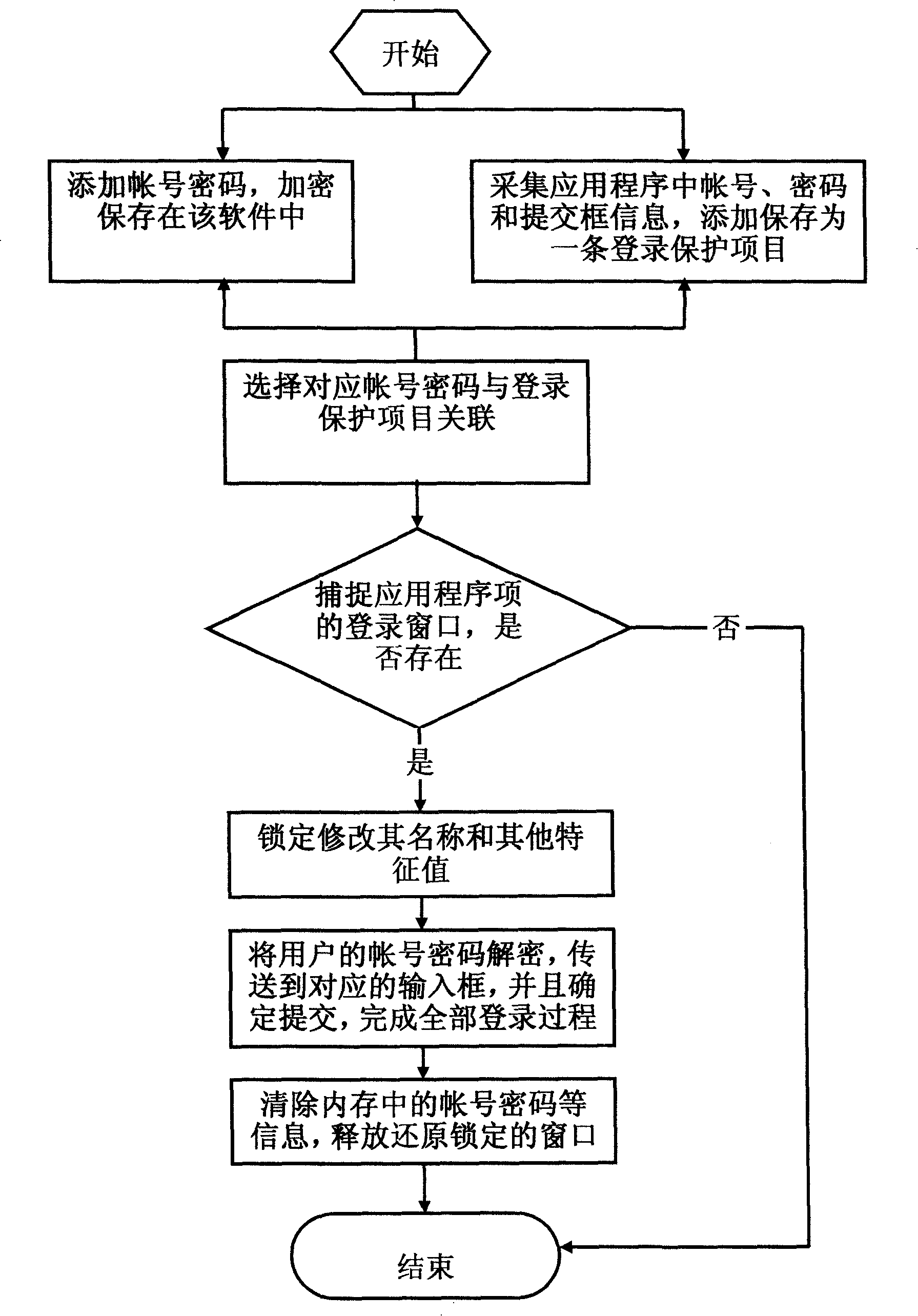
[0041] Password protection for applications, client software and webpages, applicable to online games, instant messaging clients, other local applications, various webpages, etc. It is necessary to collect and confirm the account number, password and submission box information in advance, such as figure 1 For the working principle process of the present invention Figure 1 , whose flow:
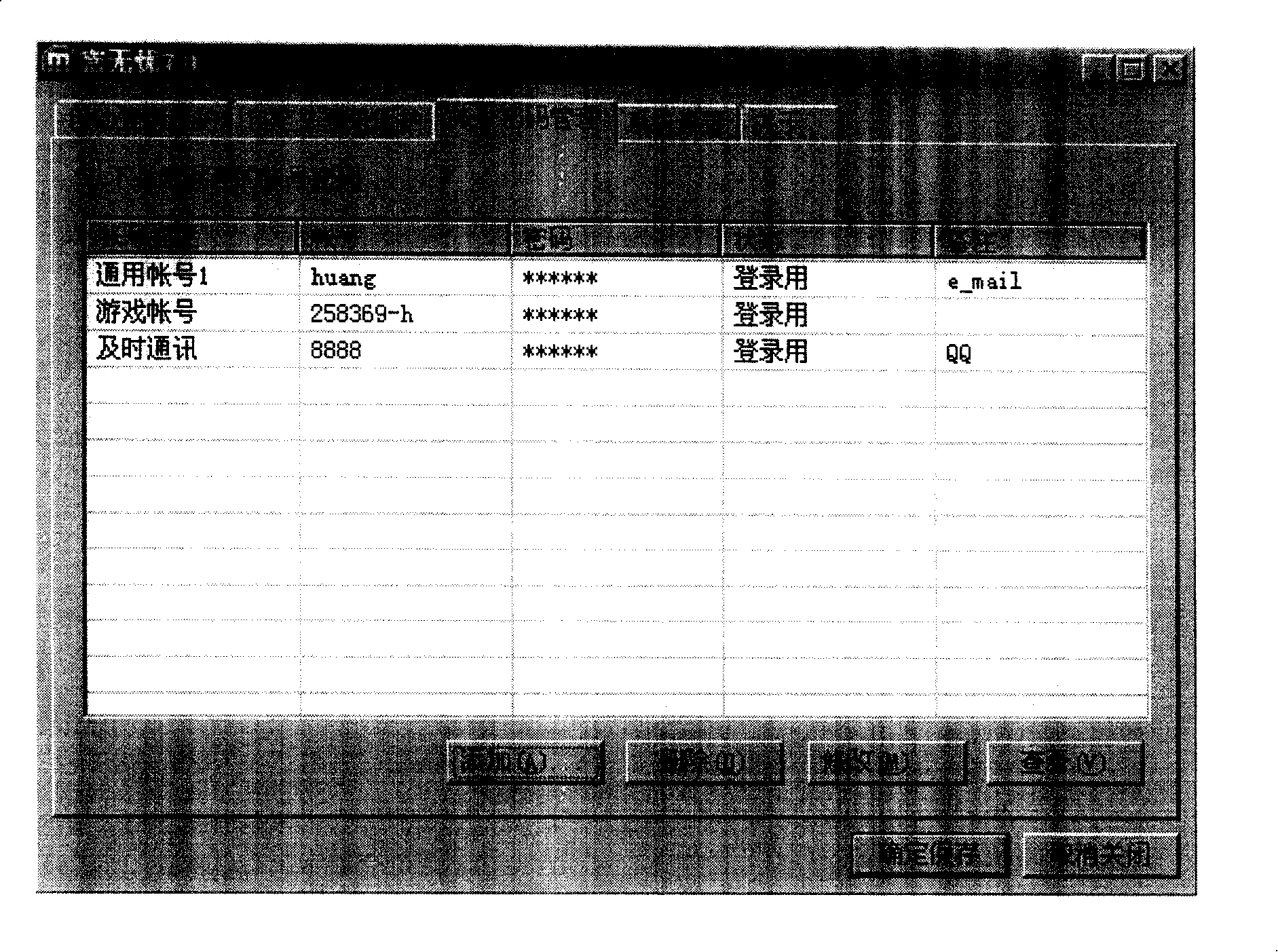
[0042] 1. Add account password, encrypted and saved in the software, such as image 3 Schematic diagram of the user interface of the "account password management" of the present invention;
[0043] 2. Collect characteristic information such as the account number, password input box, and submit button position value in the application program, client software, or web page that need to be logged in, and add and save it as an automatic login protection item record, such as Figure 4 It is a schematic diagram of the user interface of the "automatic login protection" of the present invention;
...
example 2
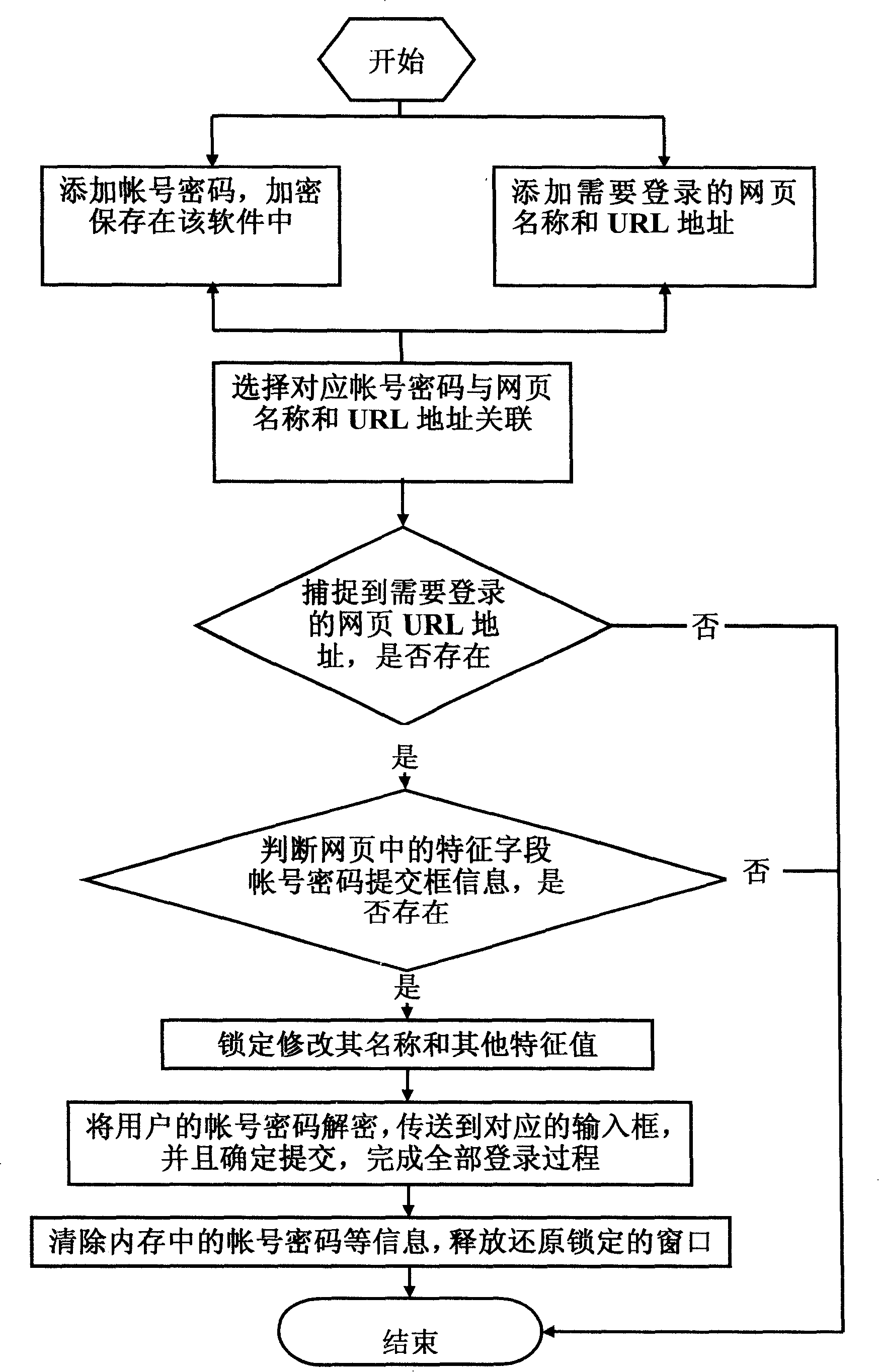
[0049] Password protection for webpage login, applicable to website pages such as e-mail, e-commerce, online banking, forum passwords, personal blogs, etc. The information in the account and password submission box can be determined through the feature field in the webpage, such as figure 2 For the working principle process of the present invention Figure II , its flow:
[0050] 1. Add account password, encrypted and saved in the software, such as image 3 Schematic diagram of the user interface of the "account password management" of the present invention;
[0051] 2. Add the name and URL address of the webpage that needs to be logged in, and save it as a custom login protection project record, such as Figure 5 It is a schematic diagram of the user interface of the "custom login protection" of the present invention;
[0052] 3. Select the corresponding account password to associate with the web page name and URL address in the "Custom Login Protection" project record, s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com