Authentication method and system for mobile communication terminal
A mobile communication terminal and authentication technology, applied in the field of wireless communication, to achieve the effect of reducing the loss of mobile phones, preventing theft of mobile phones or mobile phone cards, and preventing theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
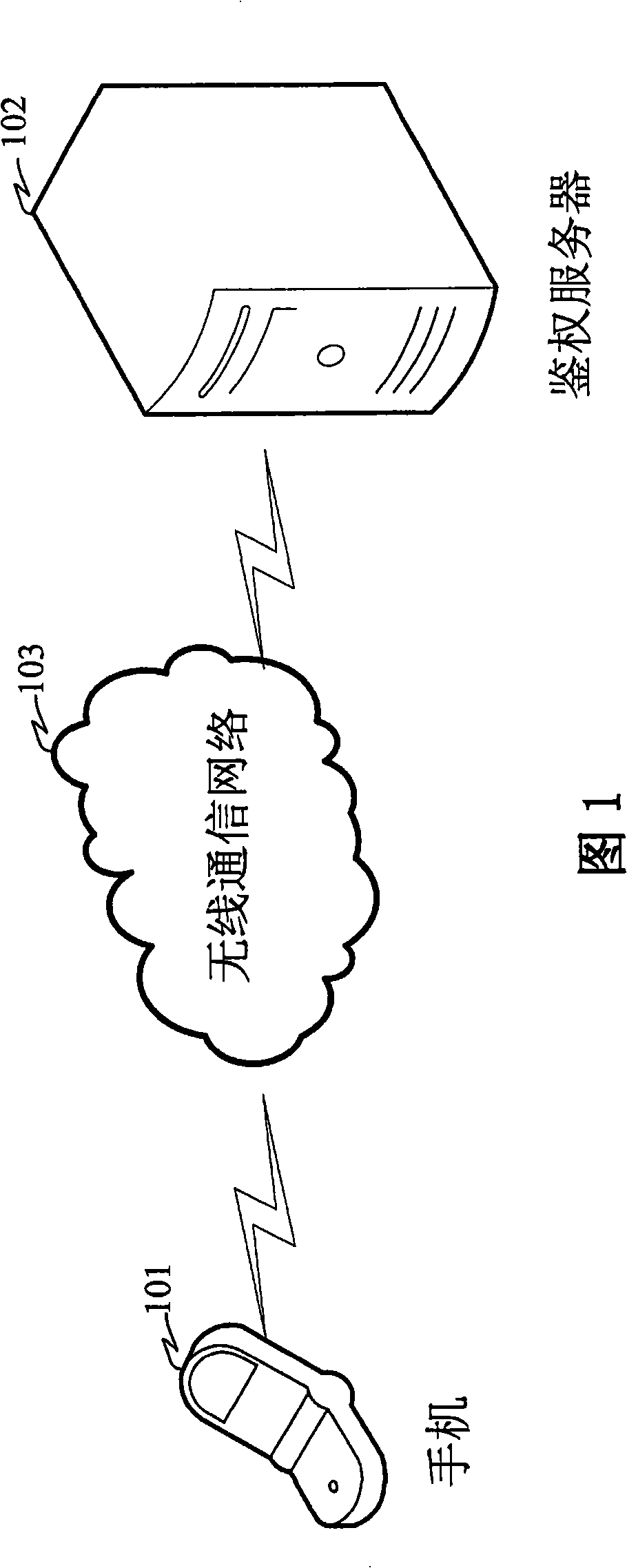
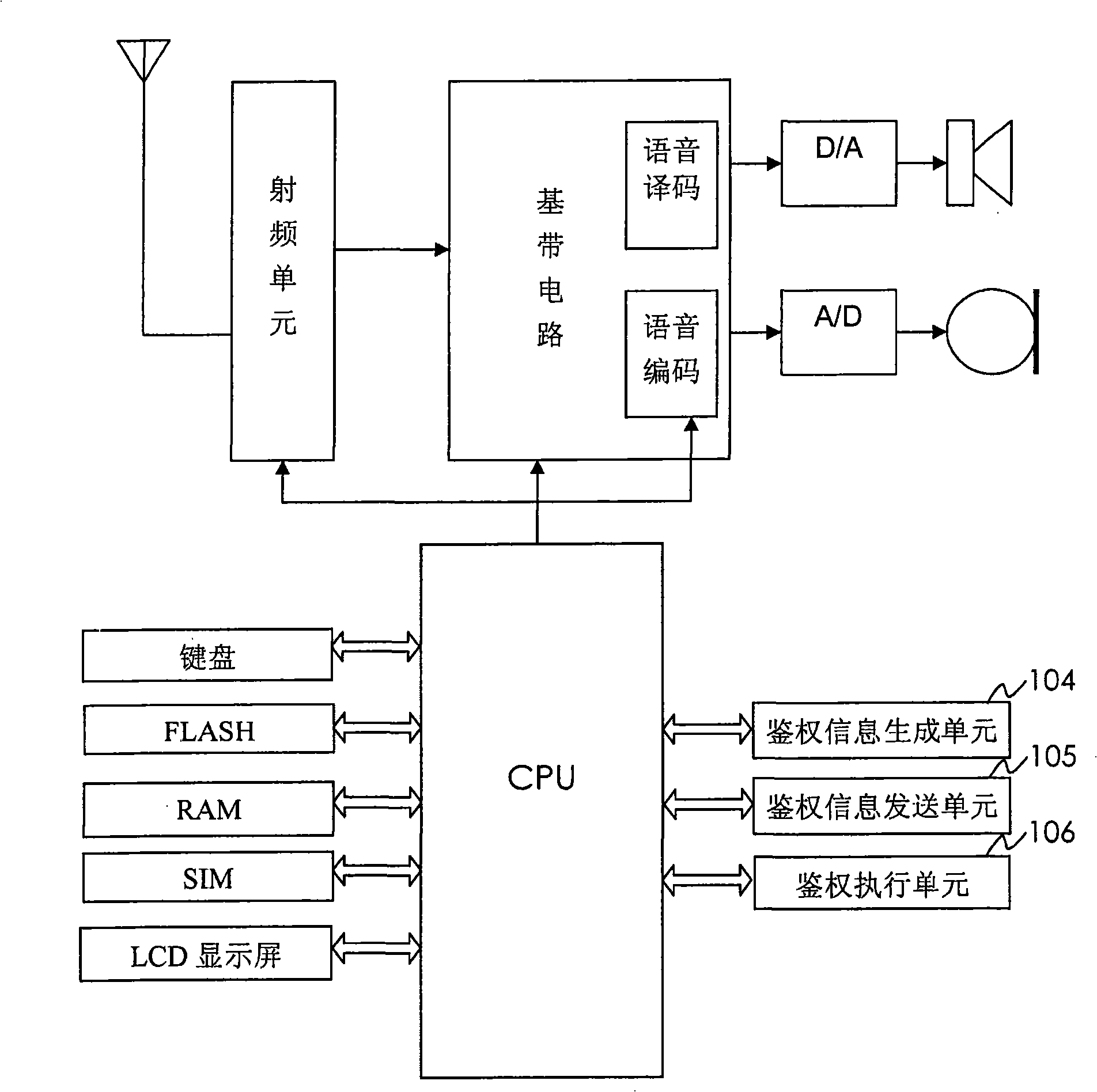
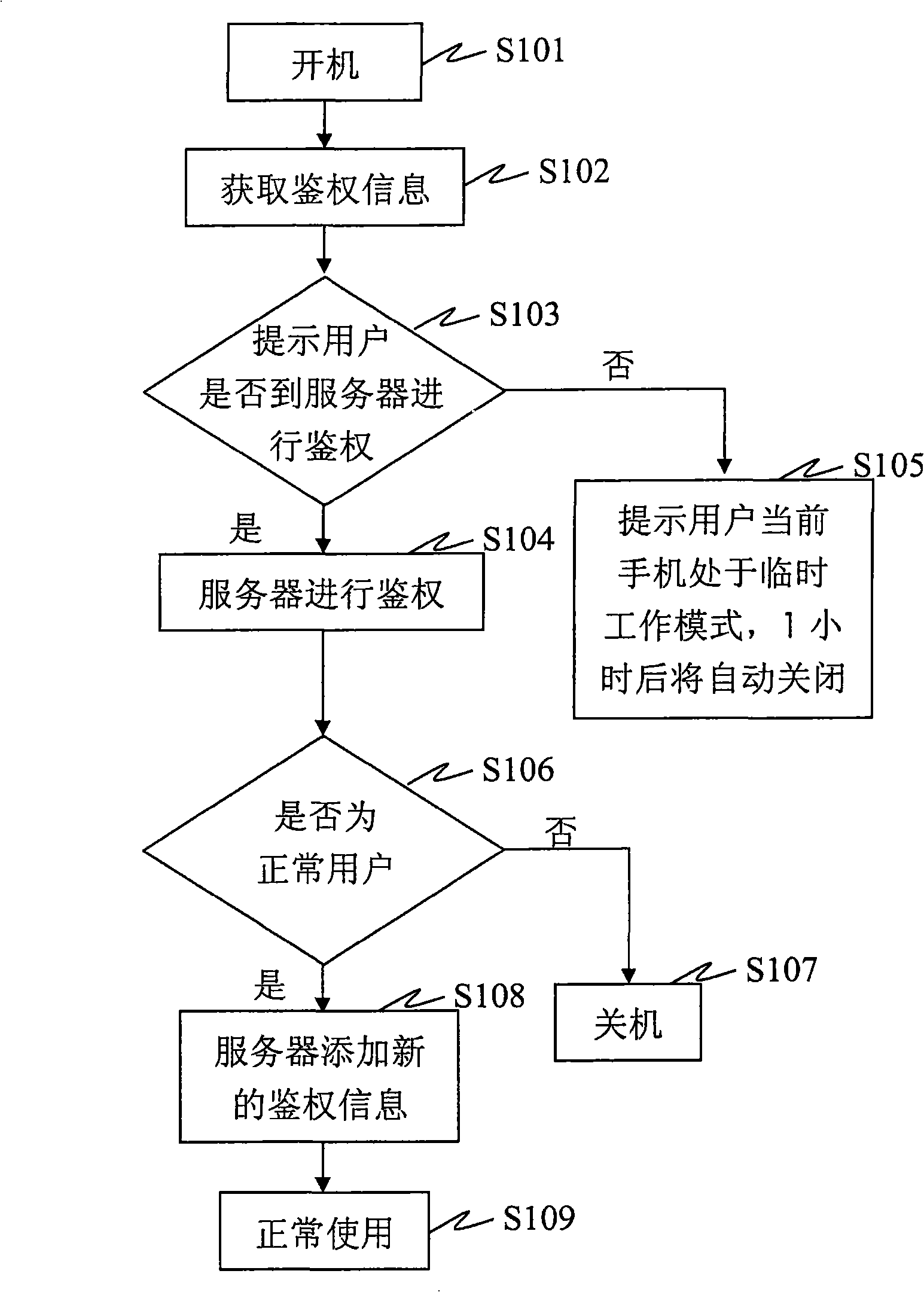
[0035] Figure 1 shows a schematic diagram of an authentication system for a mobile communication terminal according to Embodiment 1 of the present invention. figure 2 Shown is a structural block diagram of an authentication system for a mobile communication terminal according to Embodiment 1 of the present invention, in which a mobile communication terminal (a mobile phone in this embodiment) 101 communicates with an authentication server 102 through a wireless communication network 103, wherein the The mobile communication terminal of Embodiment 1 includes a radio frequency unit, a baseband circuit, an MCU control circuit, a keyboard, and a display. The mobile communication terminal also includes: an authentication information generating unit 104 for obtaining a mobile communication terminal identity, a SIM card identity, and a user password , Generate authentication information; the authentication information sending unit 105 is used to send the above authentication information...
Embodiment 2
[0046] Figure 6 Shown is a structural block diagram of an authentication system for a mobile communication terminal according to Embodiment 2 of the present invention. The mobile communication terminal includes a radio frequency unit, a baseband circuit, an MCU control circuit, a keyboard, and a display. The mobile communication terminal also includes: identification code acquisition Unit 301, used to obtain the IMEI of the mobile communication terminal as the mobile communication terminal identifier, and the IMSI of the SIM card as the SIM card identifier; the user password input unit 302, used to input the user password; the authentication information sending unit 303, used to The above-mentioned mobile communication terminal identifier, SIM card identifier, and user password are sent to the authentication server as authentication information for authentication; the authentication execution unit 306 is configured to receive the authentication result performed by the above-ment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com