Improved method for expanding and transforming jitter and modulating watermark
A technology of jitter modulation and expansion transformation, applied in image data processing, instrumentation, image data processing, etc., can solve the problems of inflexibility, loss of carrier signal quality, and the problem of amplitude scaling attacks not being well solved.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
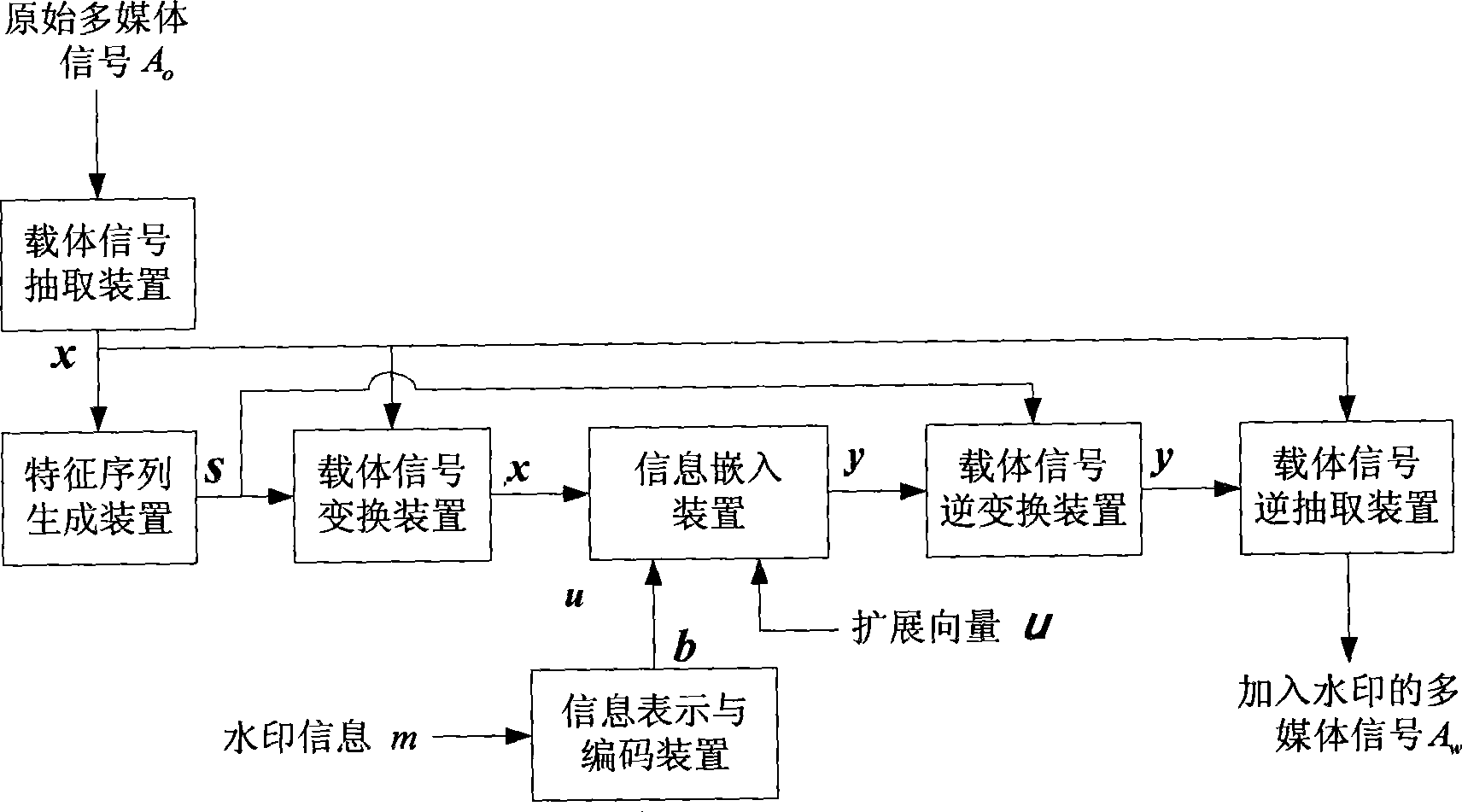
[0033] Watermark Carrier A o For an image signal, an improved STDM watermarking method is implemented. The watermark embedding process is as follows: figure 1 shown, including the following steps:
[0034] 1) From A o The block DCT (DCT: Discrete Cosine Transform) domain extracts the carrier signal x. A o Divide into multiple non-overlapping sub-blocks, each block contains 8×8 pixels, and then perform DCT transformation on each block. Perform zigzag sorting on the 64 DCT coefficients in each block, and select 62 DCT coefficients with ordinal numbers ranging from 3 to 64. Arrange all the extracted DCT coefficients into a large sequence as the carrier signal. Then, the extracted carrier signal is scrambled according to a certain random order, and the final carrier signal generated is denoted as x, and its length is N. This step is realized by the carrier signal extraction device.
[0035] 2) Express the information m to be embedded as a binary sequence b of length p, wher...
Embodiment 2
[0078] The difference from Example 1 is that
[0079] In step 5 of the watermark embedding method, the method of calculating the feature sequence s. The DC component of each 8×8 image sub-block constitutes a vector, which has nothing to do with the watermarking process. In this embodiment, the average value of the vector is used, denoted as C00, to construct the feature sequence s. Specifically, the feature sequence s is taken as
[0080] s=C00I N
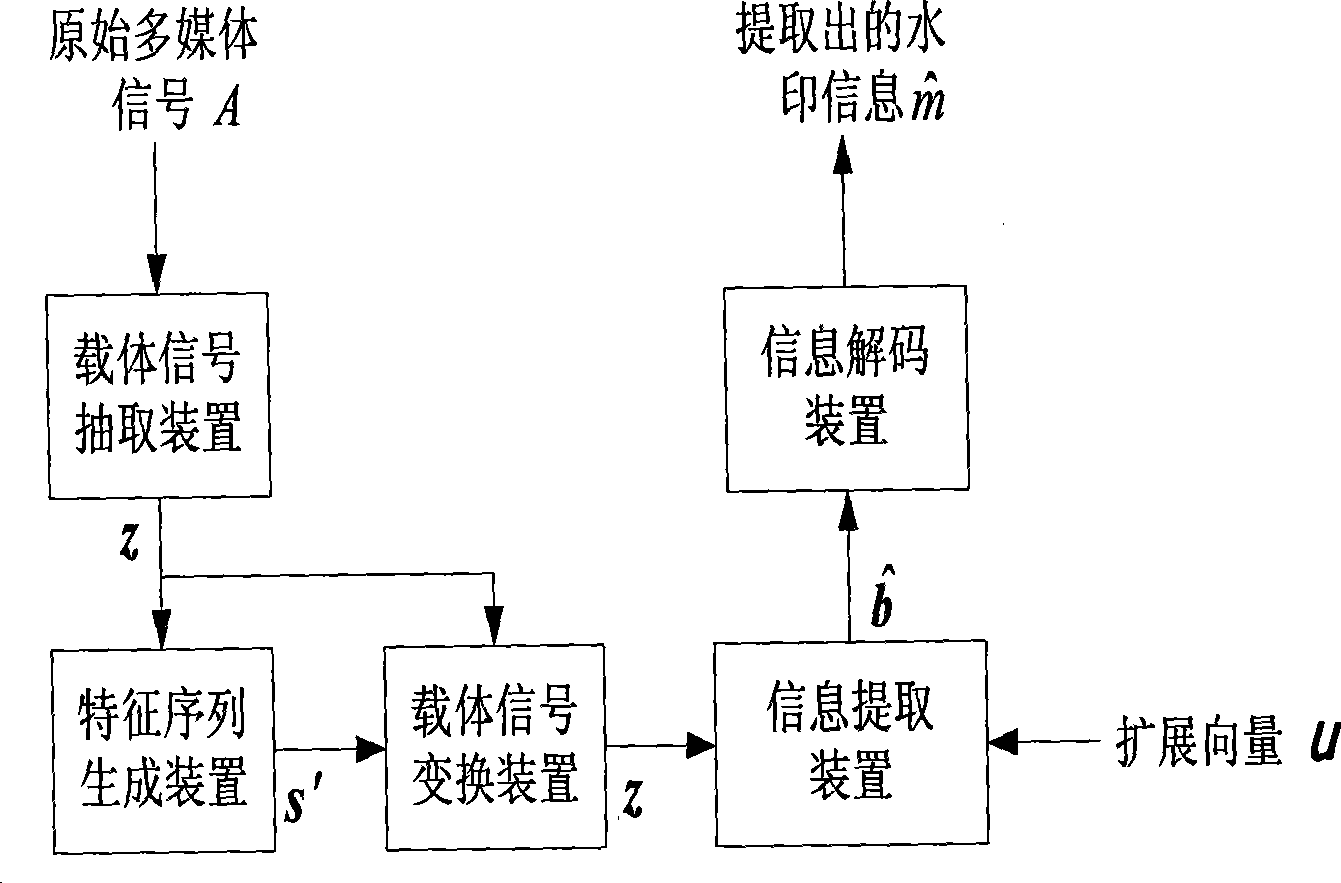
[0081] At the same time, in step 4 of the watermark detection method, the method of calculating the feature sequence s' is also modified accordingly.
Embodiment 3
[0083] The difference from Example 1 is that
[0084] The component along the watermark embedding direction is eliminated from the carrier signal, and the vector v which has nothing to do with the watermark embedding process can be obtained. for x j , j=1, L, p, can be determined v j = x j - x T j uu / u T u . This embodiment uses each sub-vector v j The absolute value of the mean of constructs the feature sequence s. Specifically, the jth subvector s of the feature sequence s j take as
[0085] In step 5 of the watermark embedding method, the method of calculating the feature sequence s. In this embodiment, the standard deviation of each sub-vector of the carrier signal is used to construct the feature sequence s. Let the function Var{} d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com