Identification method of inside and outside network messages
A network message and identification method technology, which is applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems that affect the processing performance and cannot identify the message of forged address, and achieve limited resource usage and processing method simple effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
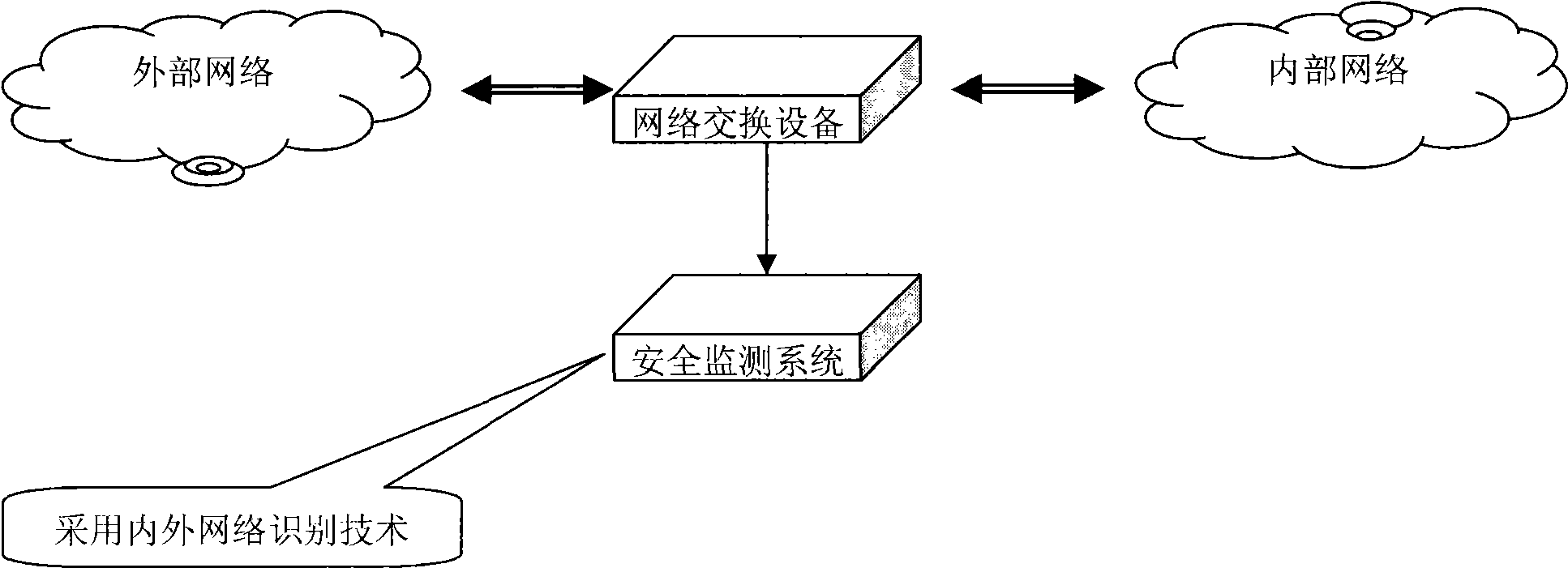
[0016] This embodiment is a method for identifying internal and external network messages. The hardware used in the method includes: the Internet, local area networks, computer terminals, servers, workstations, and routers to form an application environment, such as figure 1 shown. From the perspective of internal and external networks, the application environment can be divided into the following parts:
[0017] ●Internal network: refers to the internal local area network environment used for user work, generally including hosts, servers, network equipment, etc.;
[0018] ●External network: refers to the internet international network;
[0019] ●Network switching equipment: refers to the network equipment that completes the data exchange between the internal network and the external network, such as various routers, proxy servers, etc.;
[0020] Security monitoring equipment: Refers to the security monitoring equipment connected to the network switching equipment, receiving...
Embodiment 2
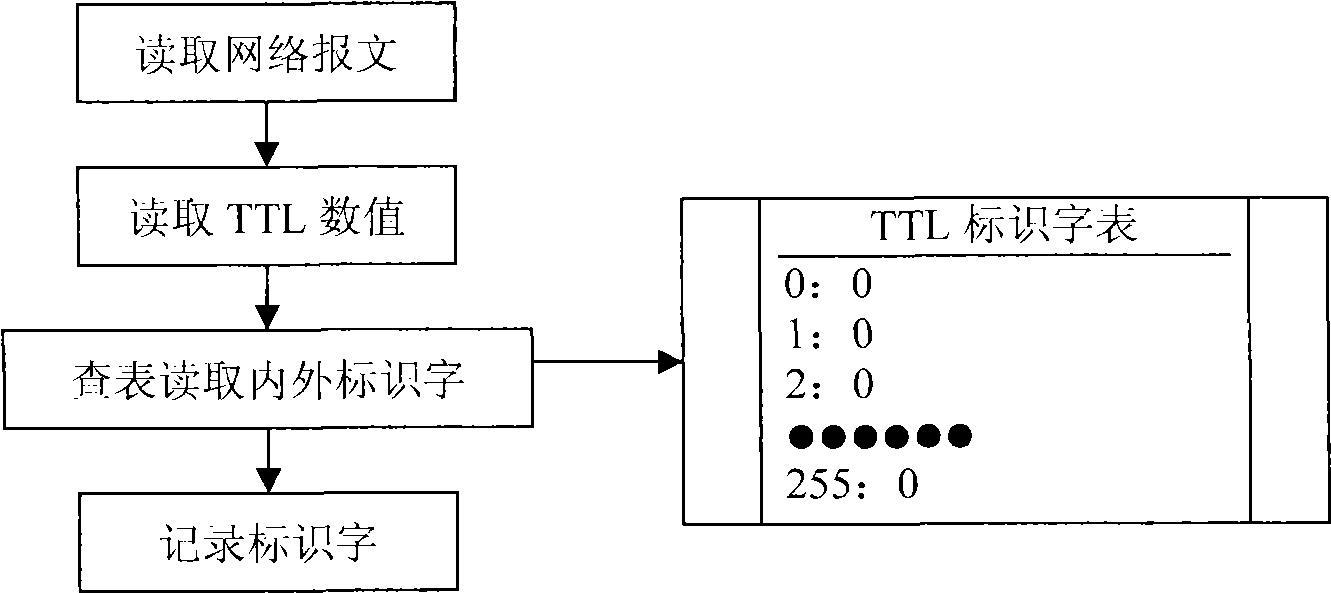
[0030] This embodiment is a refinement of embodiment one, and is about the sub-steps in the steps analyzed in embodiment one:
[0031] Determine whether it is an external network packet or an internal network packet according to the depreciation of the TTL value;
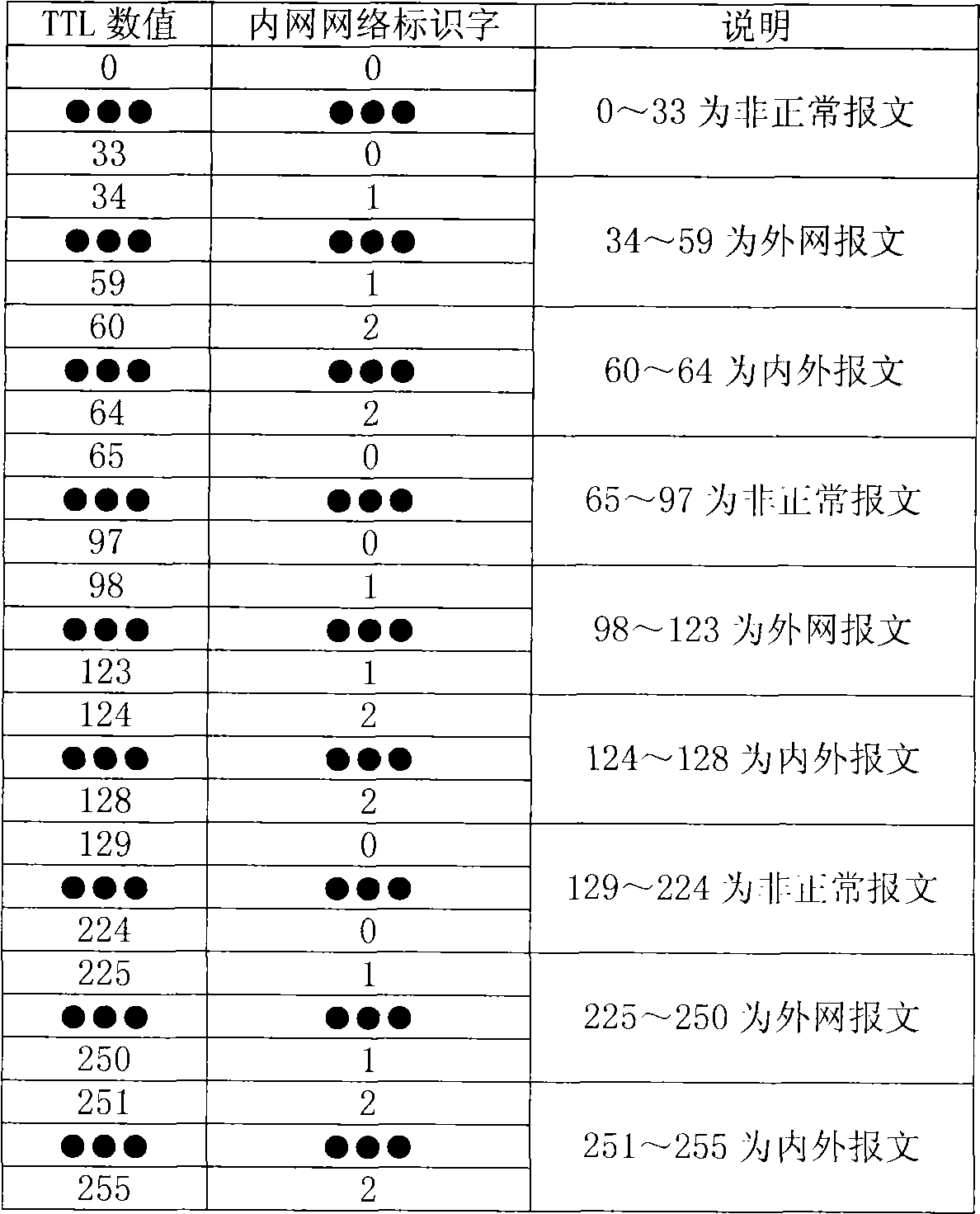
[0032] At the same time, read the TTL distribution table of the internal and external network packets, and confirm the relationship between the network identification words: 0 indicates abnormal packets, 1 indicates external network packets, and 2 indicates internal network packets, so as to determine the text and intranet messages.
[0033] figure 2 Describes the TTL distribution table of internal and external network packets. TTL is a time-to-live value of a network packet, which is decremented by one each time a packet passes through a router. Since the internal network is relatively simple and there are few or no routers, the value of TTL will not be decremented more than 5 times from the sending point of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com