Universal traffic control method and system
A technology of flow control and flow control strategy, applied in the direction of transmission system, digital transmission system, electrical components, etc., can solve problems such as single control strategy, infeasibility, unreasonable utilization of network resources, etc., to avoid waste, improve flexibility, Good implementation flexibility and applicable effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
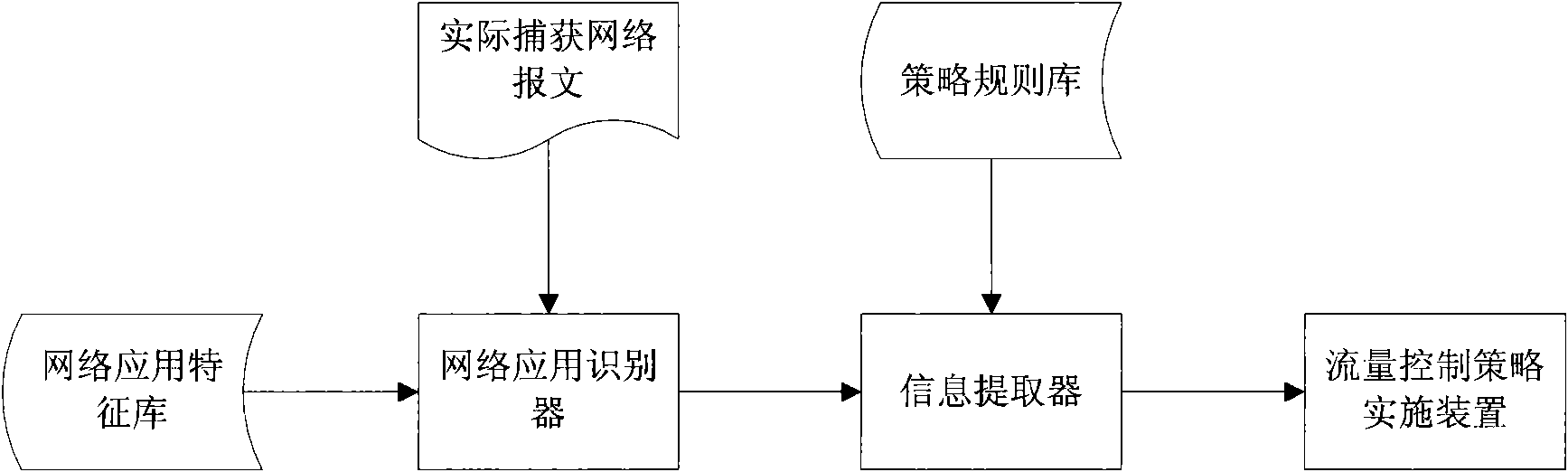
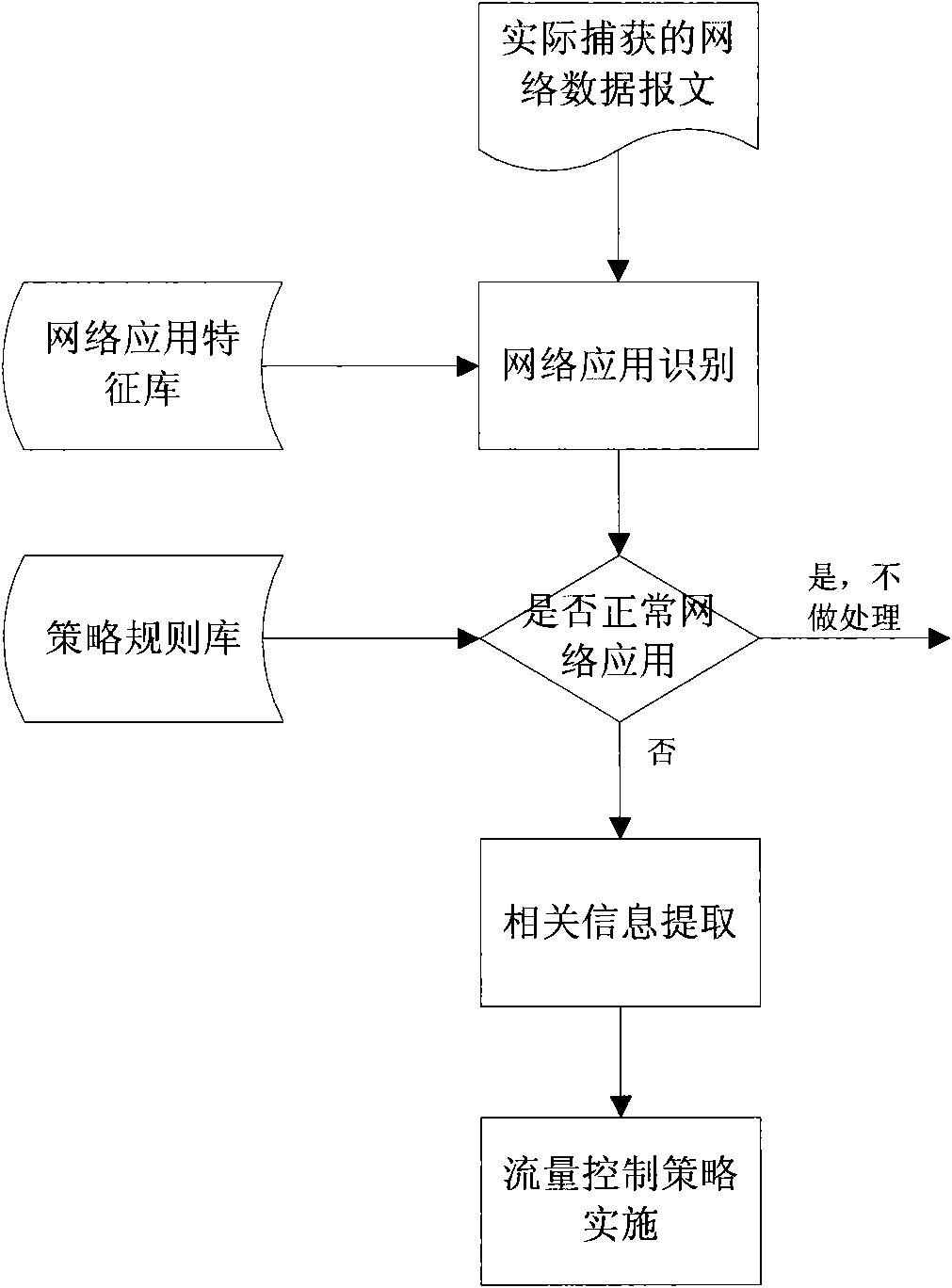
[0021] This embodiment is a method for dynamic flow control in a general network application process and the basic mode of the system, and its basic structure is as follows figure 1 shown. Including network application feature library, network application identifier, policy rule library, information extractor and traffic control policy implementation device, the system workflow is as follows: figure 2 Shown:
[0022] A general flow control method, comprising the following steps:
[0023] Network application identification steps;
[0024] Relevant information extraction steps;
[0025] Flow control policy implementation steps.
[0026] in:
[0027] ① Network application identification steps. Network application identification uses protocol analysis technology for hierarchical analysis based on the actual captured data messages, and identifies which network application the current data message belongs to according to the pre-set message characteristics of various network ...
Embodiment 2
[0031] This embodiment is a preferred solution of the network application identification step in Embodiment 1:
[0032] Use the layered data packet protocol analysis method to identify the network application of the current message according to the actual captured data message and the different characteristics of various network applications set in advance.
[0033] 1) The basic idea of this embodiment is: take the actually captured network message as a sample, analyze the data message according to the protocol format used in various network application processes, and rely on the data message transmitted during the communication process of the network application Among them, there are message characteristics or behavior characteristics to identify the type of network application. For example: "%13BitTorrent%20Protocol" can identify that the BitTorrent protocol or some client software using the BitTorrent protocol is being used, and it can be used as a static identification f...
Embodiment 3
[0041] This embodiment is a preferred solution for the relevant information extraction step in Embodiment 1:
[0042] Check the identification result provided by the network application identification step according to the preset network application control rules in the policy rule base, and extract relevant information from the data packets filtered according to the control rules for policy implementation.
[0043]The basic idea of this embodiment is: use the identified network application message provided by the network application identification step as a sample, and use the actual detection stored in the policy rule base as a pattern to first perform matching to determine whether the application in the current network environment is a policy Applications within the allowed range, and applications that are not allowed or must be restricted by the policy can be regarded as abnormal network applications. The policy rule settings here can be flexibly set according to differe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com