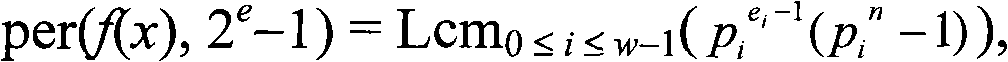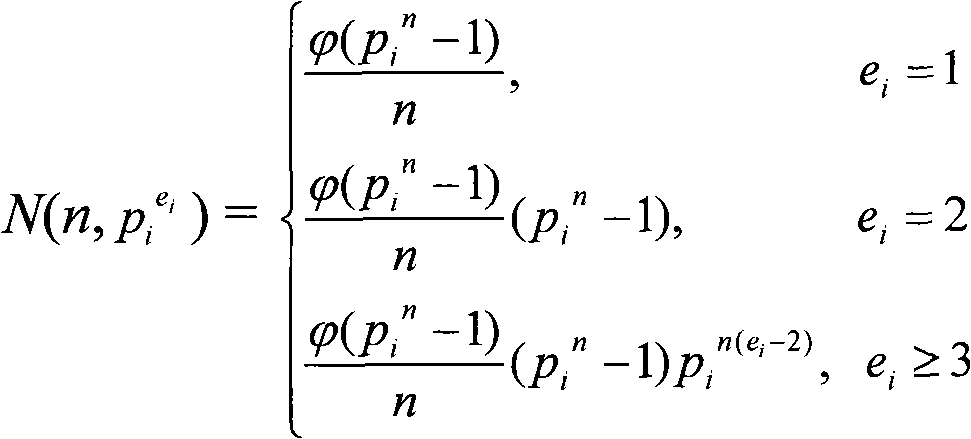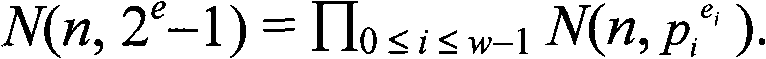Pseudorandom sequence generation method and pseudorandom sequence encryption method
A pseudo-random sequence and generation method technology, applied in the field of information security, can solve the problems of difficulty in success, the weight sequence does not have algebraic equivalence, and the realization efficiency cannot be satisfied, so as to reduce the difficulty and complexity, and achieve a sequence cryptosystem Simple, easy-to-implement effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will provide a pseudo-random sequence generation method with bit-equivalent entropy-preserving output sequence, and at the same time provide a method for constructing a stream cipher system with the sequence generated by this method as the core sequence source, and design a specific stream The cryptographic system is named "Flying-Ring".
[0020] (1) Sequence generation method
[0021] The sequence obtained by the sequence generation method provided by the present invention is referred to as "loop Z / (2 e -1) Upper Primitive Sequence", the specific generation method is as follows:
[0022] (1) The parameters e and n are all positive integers greater than or equal to 2;
[0023] (2) Select polynomial f(x)=x n -(c n-1 x n-1 +c n-2 x n-2 +...+c 0 ), c i ∈{0,1,...,2 e -2}, i=0, 1, ..., n-1, satisfy the following properties: for integer 2 e Any prime number power factor p greater than 1 of -1 w , where p is a prime number, f(x)(mod p w ) The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com