Host access control system and method
An access control and host technology, applied in the field of network security, can solve the problem of being unable to effectively prevent illegal hosts from accessing the intranet, and achieve strong controllability and scalability
Inactive Publication Date: 2010-09-01
BLUEDON INFORMATION SECURITY TECH CO LTD
View PDF4 Cites 8 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
The invention provides a host access control system and method to solve the problem that the prior art cannot effectively prevent illegal hosts from accessing the intranet
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
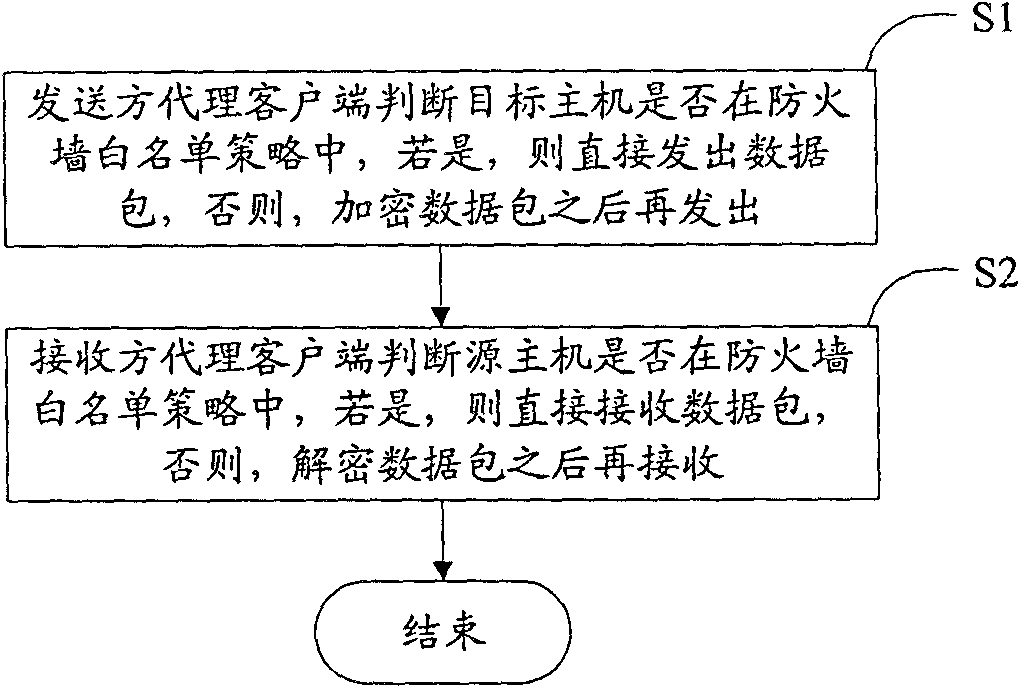
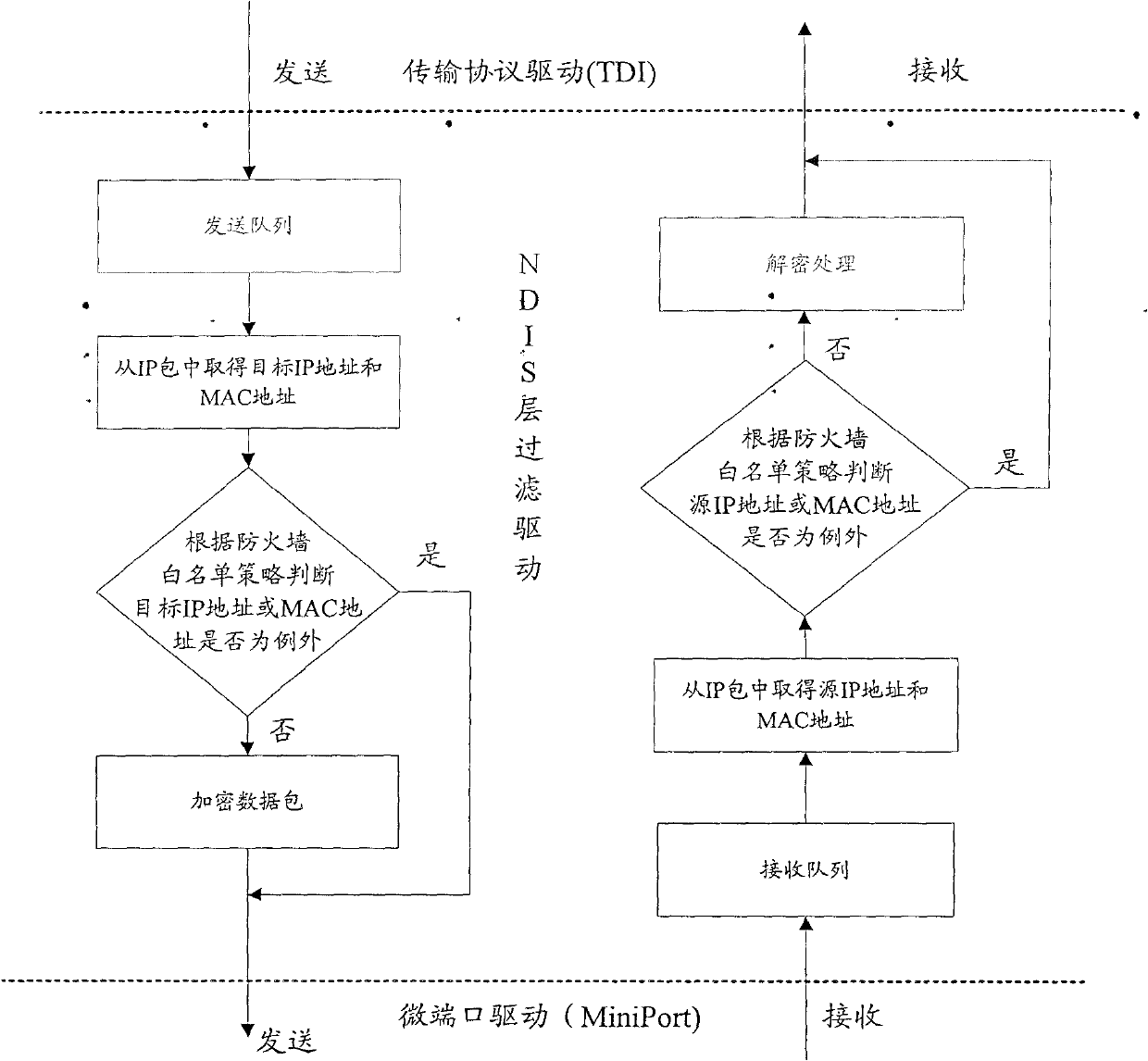
The invention discloses a host access control system and a host access control method, and relates to the field of network safety for solving the problem of incapability of effectively preventing illegal access of the host to an intranet in the prior art. The method comprises the following steps that: a sender agent client judges whether a target host is in a firewall white list strategy or not, if so, directly sends a data packet, and otherwise, sends the data packet after encryption; and a receiver agent client judges whether a source host is in the firewall white list strategy or not, if so, directly receives the data packet, and otherwise, receives the data packet after decryption. The system comprises the sender agent client and the receiver agent client. Because the data is transmitted among legal hosts in the safe intranet of the invention through the encryption and decryption of a key under unified management or the firewall white list strategy, the limitation aiming to a normal host access control system is solved; and therefore, the system and the method provide a set of host access control solution with high universality, safety, controllability and extensibility.
Description
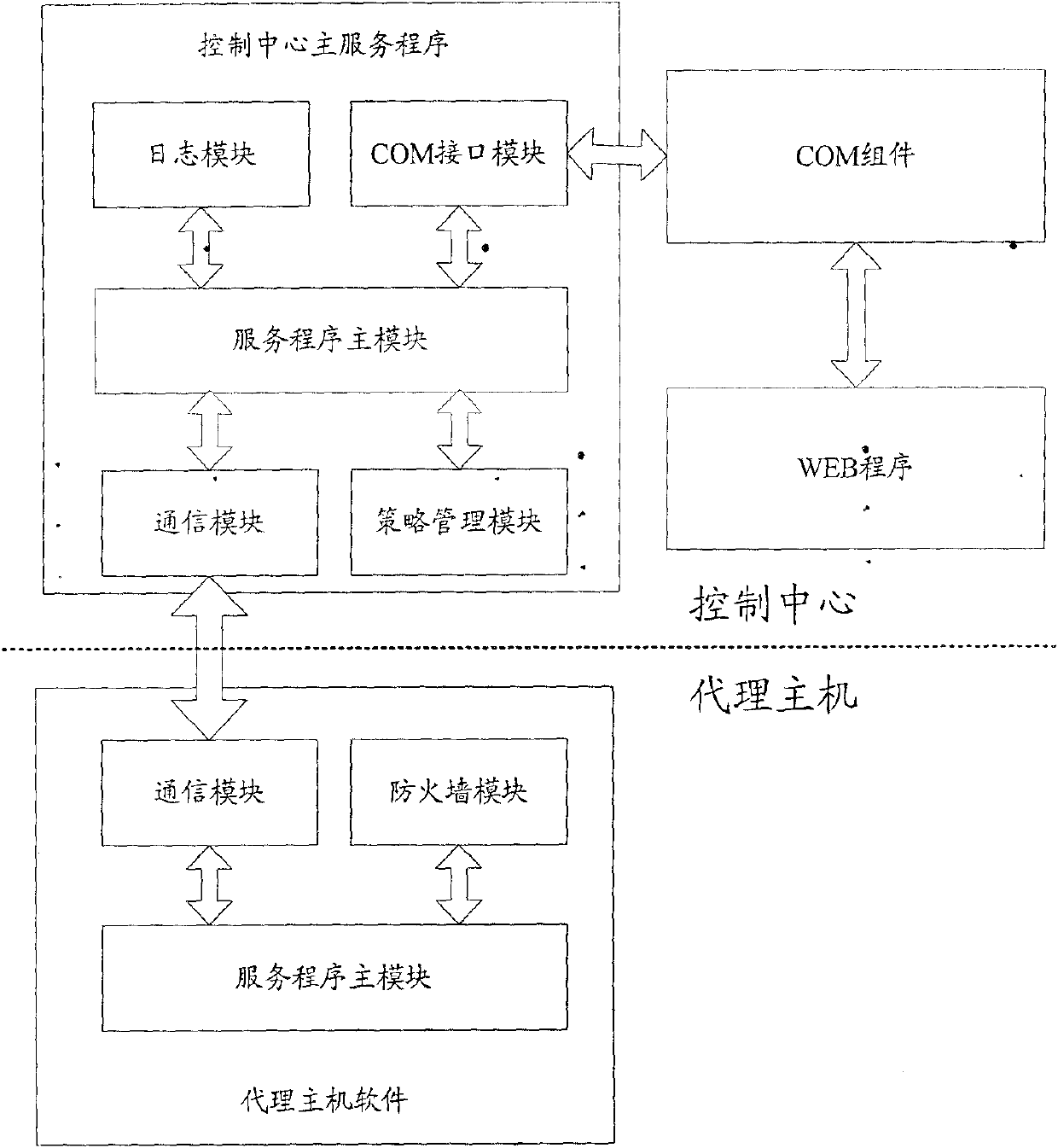
technical field The invention relates to the field of network security, in particular to a host access control system and method. Background technique With the rapid development of computer network applications in governments, enterprises and institutions, more and more attention has been paid to intranet security, especially the control of host access. At present, ARP (Address Resolution Protocol) spoofing or NAC (Network Admission control) technology is commonly used for host access control. The structural diagram of the host access control system in the existing technical solution based on ARP spoofing is shown in Figure 1. The system consists of a GUI management module, a packet capture module, an analysis module and a blocking module. The GUI management module is responsible for interacting with user processes, including login authentication, host policy (host whitelist) management, etc.; the packet capture module uses the packet capture method of the PCAP development...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L29/06H04L9/08
Inventor 柯宗贵柯宗庆
Owner BLUEDON INFORMATION SECURITY TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com