Method for detecting Solaris system fault by utilizing mandatory access control
A technology of mandatory access control and system failure, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as network application insecurity, lack of key files, lack of audit data integrity protection, etc., to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
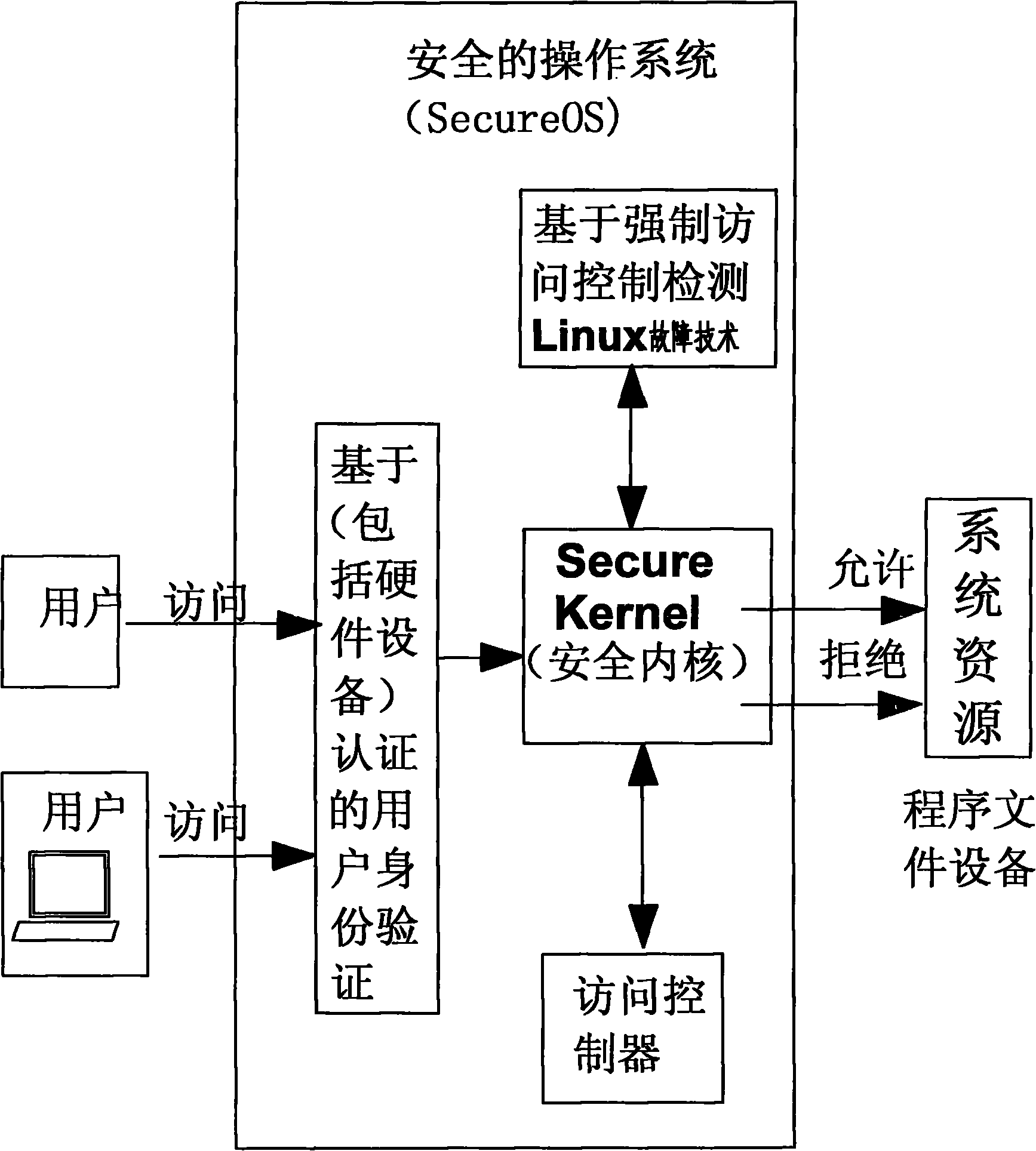
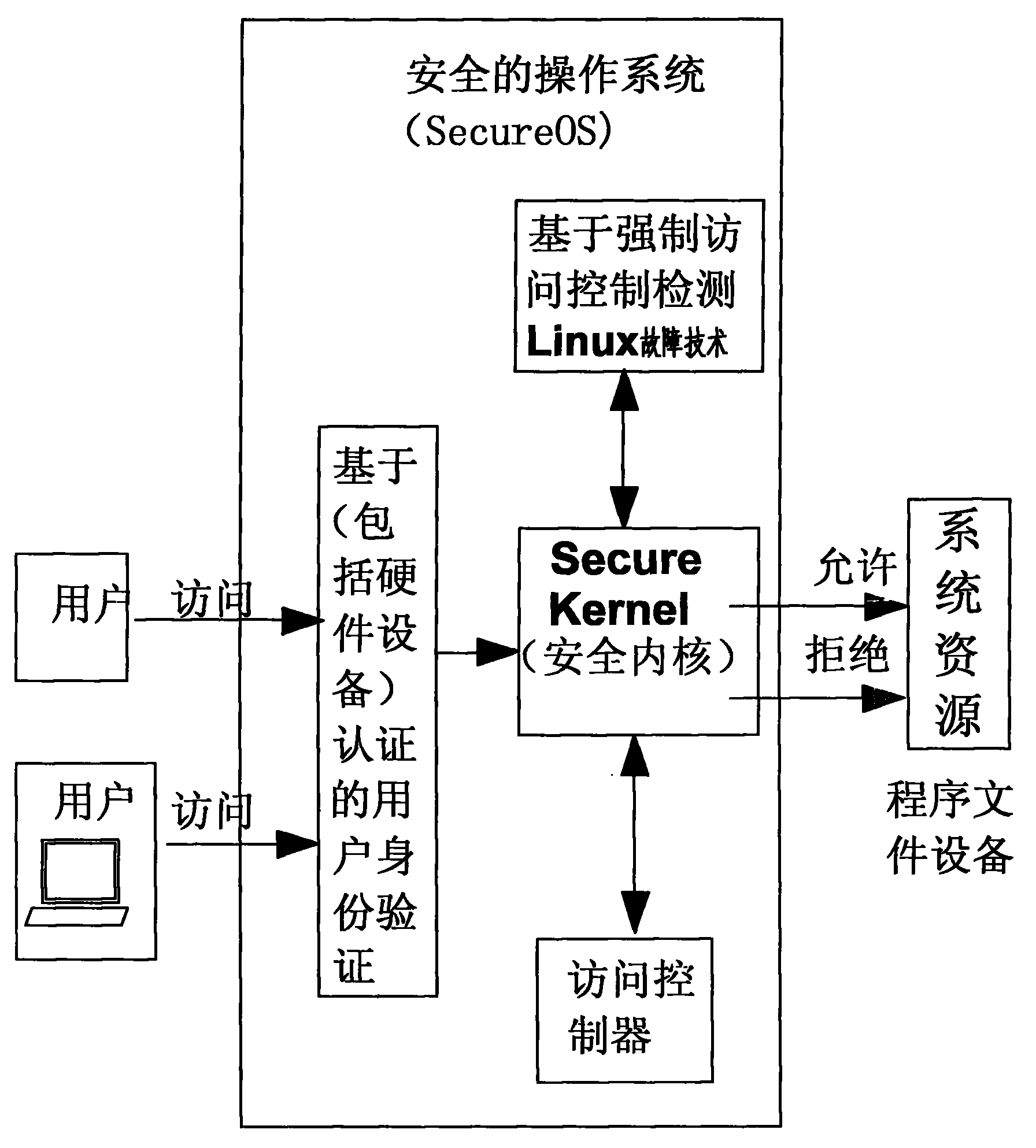
[0039] The method of the present invention is described in detail below with reference to the accompanying drawings.
[0040] It mainly consists of the following modules:
[0041] 1. Mandatory access control MAC
[0042] Mandatory access control MAC is divided into two parts: one is based on the user's access control to files, and the other is based on the process's access control to files. The process is bound to the user principal when it is running, so the process itself is also a principal. When an object is protected by a security token, even the root user cannot access the object unless it has MAC permissions.
[0043] 2. Anti-abnormal termination of important system processes
[0044] In order to prevent hackers from terminating some important system processes, a set of mechanisms is provided to prevent some important processes from being terminated abnormally by anyone, thus ensuring the normal operation of the service.
[0045] 3. User network mandatory access con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com