Equation password encryption method
An encryption method and equation technology, applied in the field of equation encryption, can solve the problems of high cost, hidden dangers, and not yet generalized, etc., and achieve the effect of high leakage prevention and simple docking and upgrading.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to fully understand the technical content of the present invention, the technical solution of the present invention will be further introduced and illustrated below in conjunction with specific embodiments.
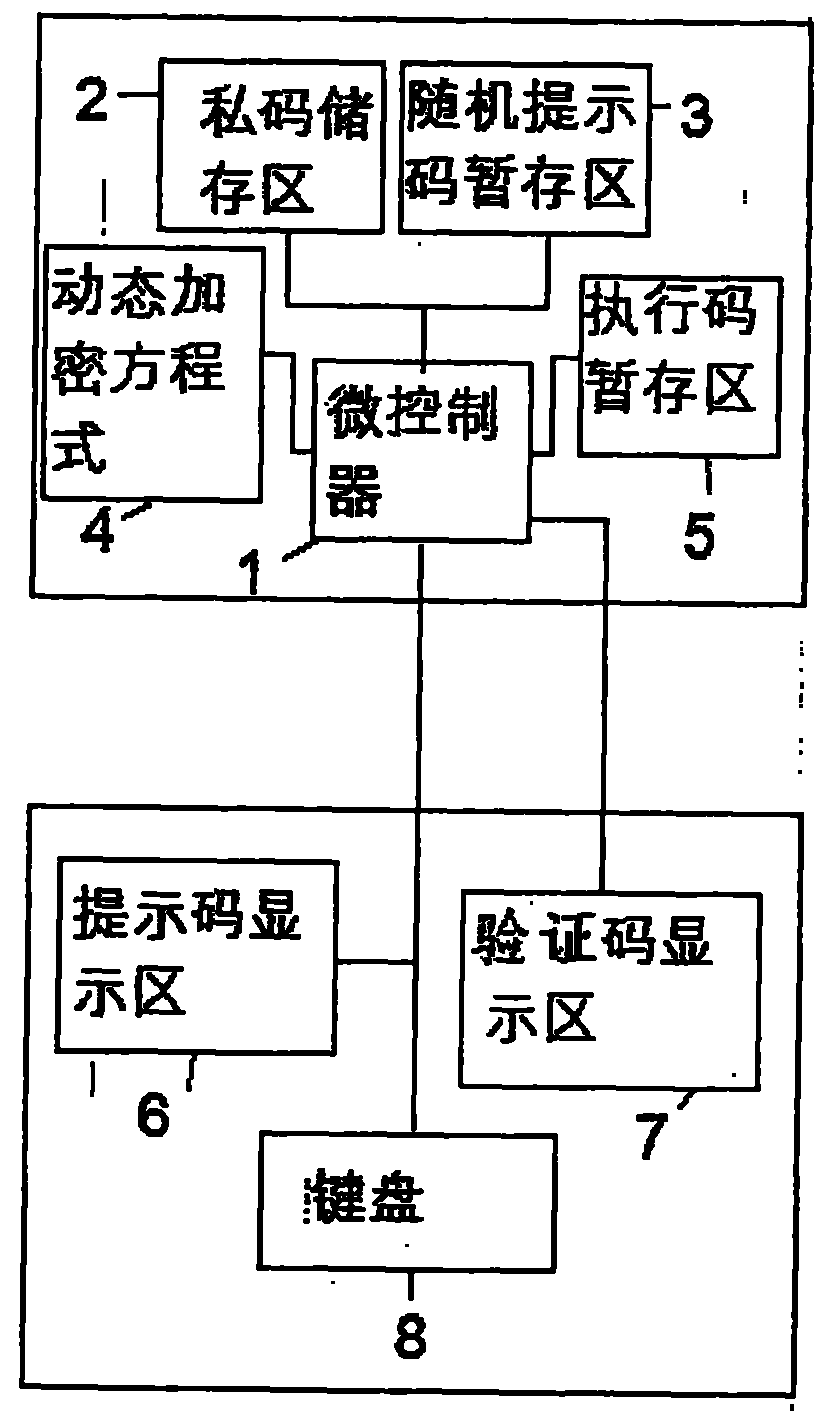
[0035] according to figure 1 Shown:
[0036](1) MCU processor 1, which is a processor that can be programmed and can perform calculations.
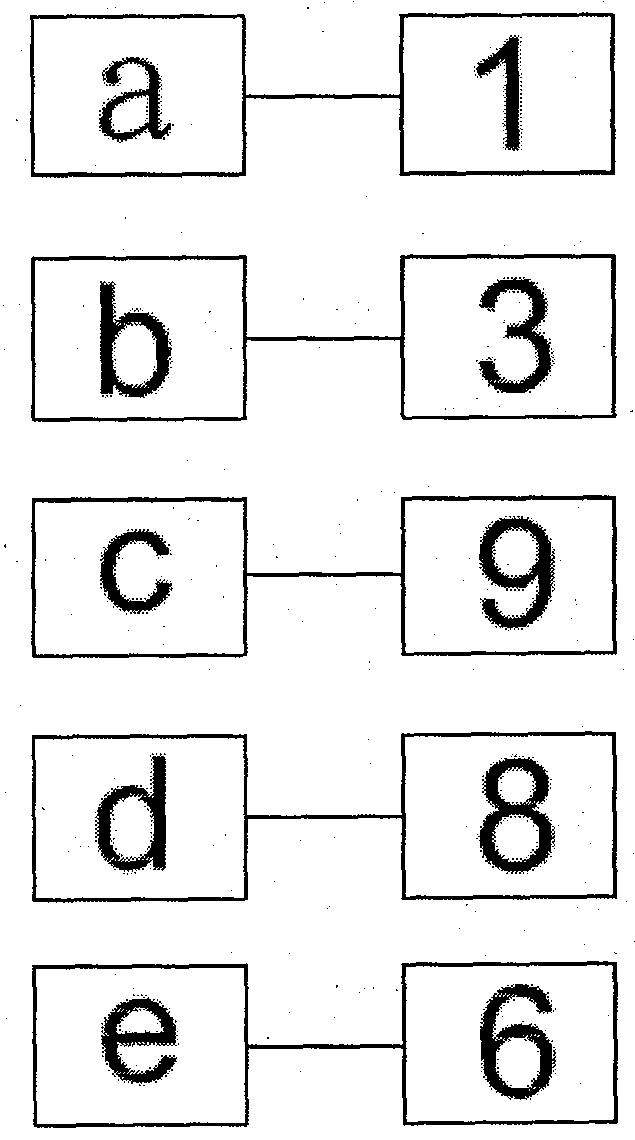
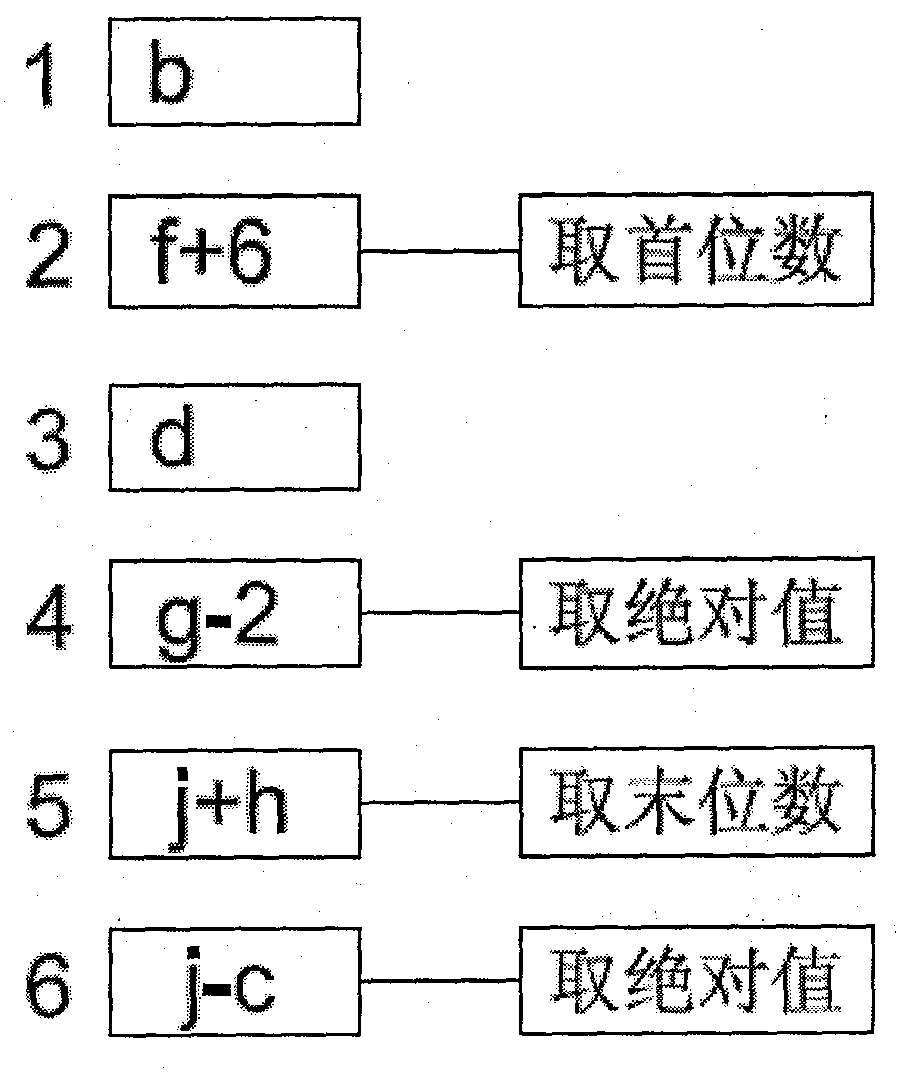
[0037] (2) Private password storage area 2, an area for storing static private passwords. When setting a password, it is the same as the traditional way of setting a password. This is a long-term constant password that verifiers need to use all the time! Store this password in private password storage area 2. The digital setting of this static password must match the expression of the equation. For example, if the equation has addition and subtraction operations, it is necessary to use a static password with any combination of numbers from 0-9 totaling 10 numbers; and equations with multiplication and division In t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com