Method and terminal for increasing data transmission safety by using multi-encryption method
A technology of data transmission security and encryption method, which is applied in the transmission system, user identity/authority verification, electrical components, etc., can solve the problem of stealing important information, etc., and achieve the effect of difficult cracking, convenient level, and guaranteed security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
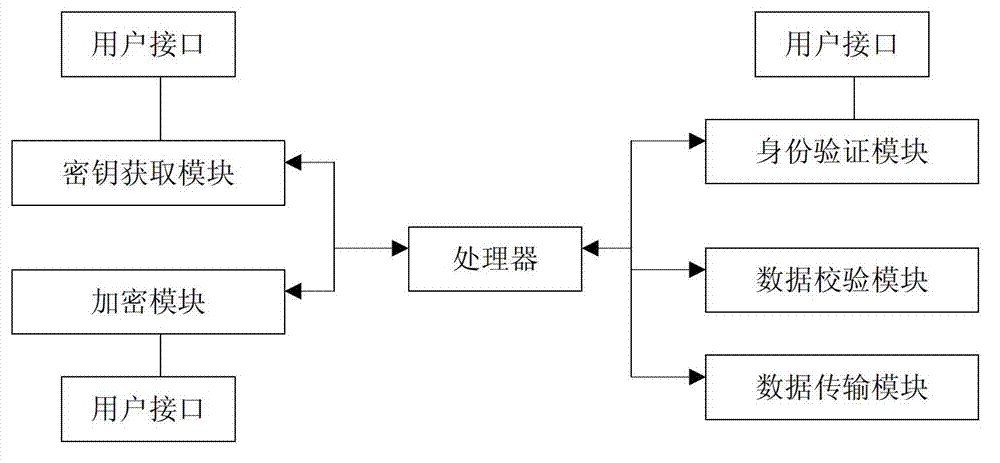
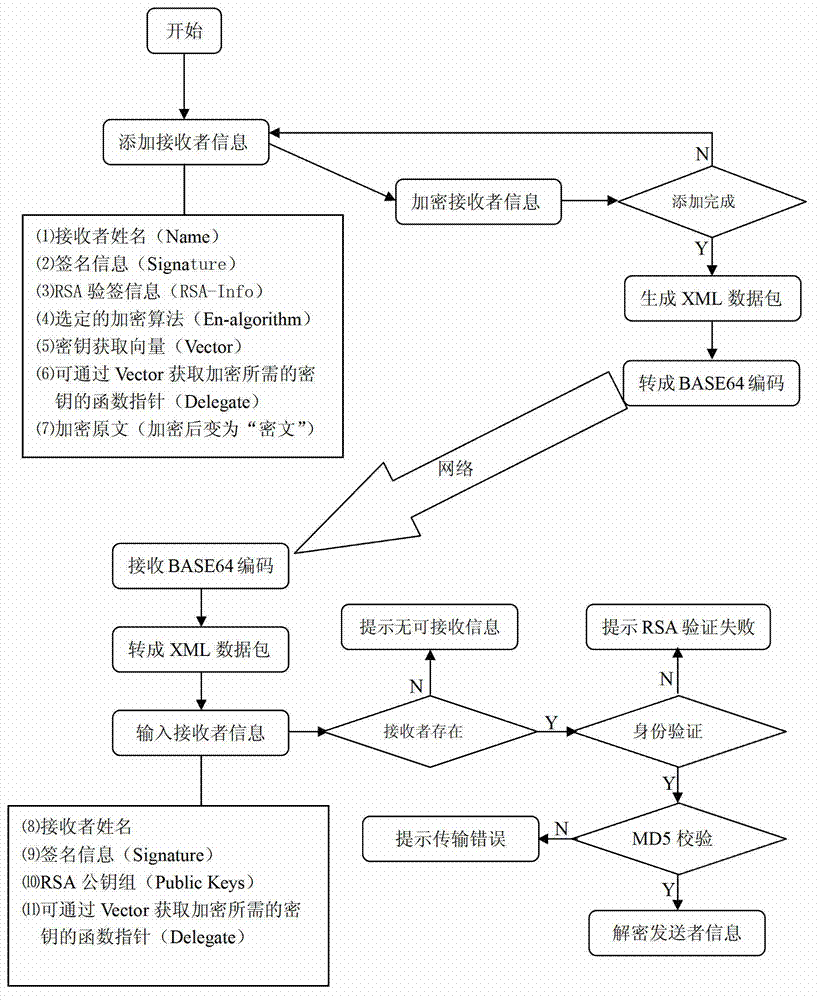
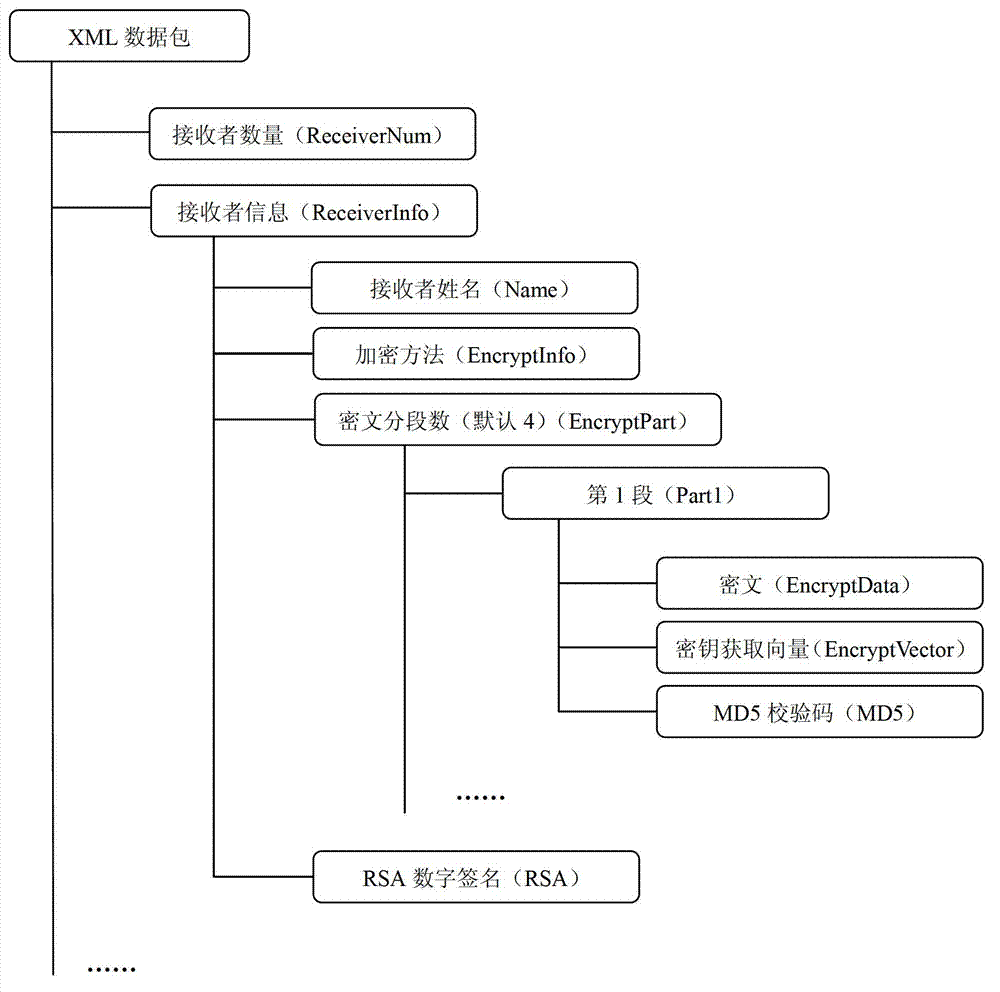
[0037] Such as Figure 1-5 As shown, a method for improving data transmission security with multiple encryption methods includes the following steps:
[0038] (a) First, add receiver information at the sending end; the receiver information at the sending end includes: receiver name Name, sender name Signature, RSA signature verification information RSA-Info, selected encryption method En-algorithm, encryption Key acquisition vector Vector, function pointer Delegate and encrypted original text that can obtain the key required for encryption through Vector;
[0039] (b) Encrypt the receiver's information at the sender: the sender performs RSA digital signature on the signature information agreed between himself and the receiver and his own RSA private key, then chooses an encryption method, and uses the key to obtain the vector and the available Obtain ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com