Method for supporting various CA (Certification Authority) identity authentications
An identity authentication and CA authentication technology, applied in the field of supporting multiple CA identity authentication, can solve problems such as heavy workload, low product maturity, and low system stability, and achieve the effect of ensuring confidentiality and preventing replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
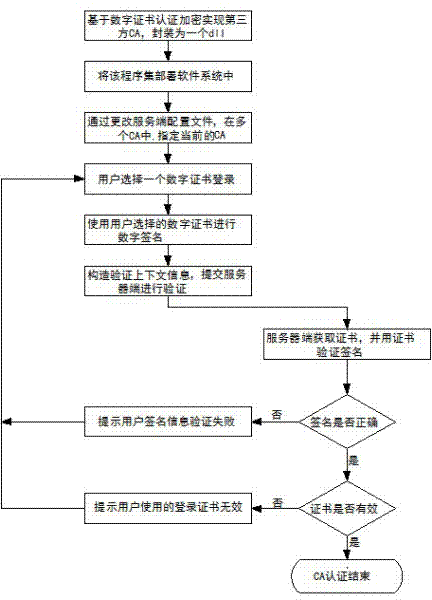
[0057] as attached figure 1 Shown, the concrete realization step of the inventive method comprises:
[0058] Step 1: Implement a third-party CA based on digital certificate authentication and encryption. According to the defined digital certificate authentication and encryption interface, combined with the third-party CA to be implemented, the program that realizes the digital certificate authentication and encryption is packaged into an assembly, generally a dll.
[0059] Step 2: Deploy the assembly. Publish the assembly deployment to the software system.
[0060] Step 3: Specify the certification CA. Change the server configuration file to specify the CA to use among multiple CAs.
[0061] Step 4: The client starts and obtains the authentication configuration information of the server.
[0062] According to the obtained authentication methods, the login window will obtain the dll and type name of the class that implements the corresponding interface from t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com