Safety scanning register, safety scan chain and scanning method of safety scan chain
A technology of scanning registers and security scanning, which is applied in the direction of instruments, measuring devices, measuring electronics, etc., can solve the problems of large increase in area, inability to provide full-speed testing, increase of chip testing cost and difficulty, and achieve the goal of protecting key information security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be described in detail below in conjunction with specific embodiments with reference to the accompanying drawings. Embodiments of the invention should not, however, be limited to the examples set forth herein.
[0044] For the sake of simplicity, the same label as the port is used below to indicate the signal input or output from this terminal, where "1" indicates high level, "0" indicates low level; "X" indicates an uncertain value ; The up arrow "↑" indicates the rising edge of the signal, and the down arrow "↓" indicates the falling edge of the signal.
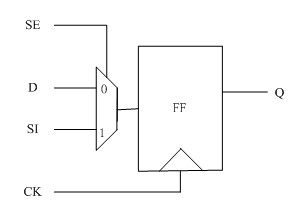
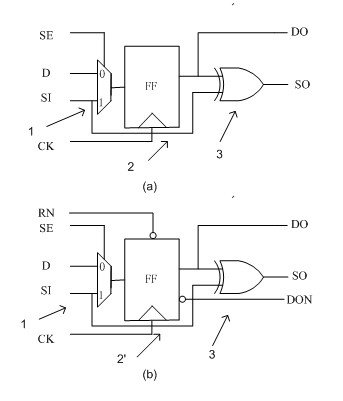
[0045] figure 2 In the circuit schematic diagram shown in (a), the security scan register includes the following 4 input terminals and 2 output terminals:
[0046] The data input terminal (D terminal) is used to receive the function input signal;
[0047] A scanning input terminal (SI terminal), used for receiving a scanning input signal;
[0048] A scanning enable terminal (SE termina...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com