High-secrecy mobile information safety system and safety method for distributed secret keys
A mobile information and security system technology, applied in computer security devices, telephone communications, branch equipment, etc., can solve the problems of inability to meet user mobile information security, infeasibility, and high cost, and achieve high-secrecy mobile information security guarantee, scalability The effect of strong sex and safety improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
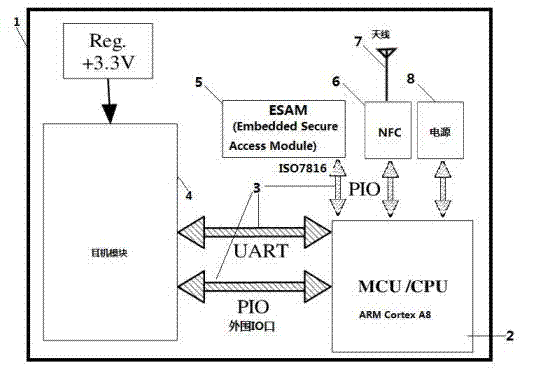
[0027] Embodiment 1: a security device of a mobile information security system, such as figure 1 As shown in , it includes a client 3 installed on a mobile phone 1 to communicate with a server 2 and a security device 5 installed in an earphone 4 to communicate with the mobile phone 1. It is characterized in that the earphone 4 is connected with a hardware-based Security device 5 for encryption or biometric identification. The security device 5 stores at least one of key, password, digital certificate, and biometric information for identifying users, supports SWP protocol, PBOC specification, QPBOC protocol, and integrates with TF card.
Embodiment 2
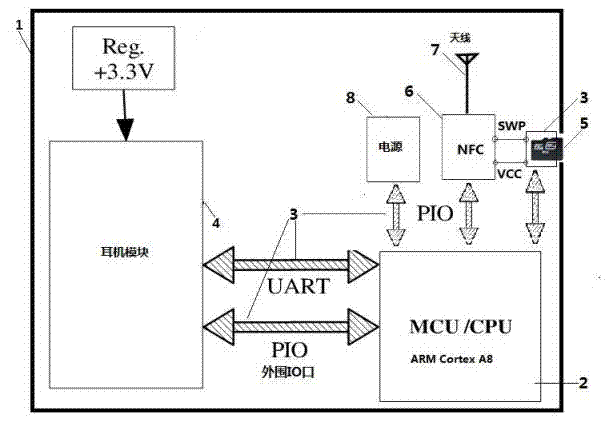
[0028] Embodiment two: a kind of NFC earphone that is used for mobile information security protection, such as figure 2 As shown in , it includes an ARM Cortex A8 single-chip microcomputer 2 installed in a housing 1, an earphone module 4 connected to the single-chip microcomputer 2 through a UART interface module 3, and a mobile information security protection device connected to the single-chip microcomputer 2 through a PIO interface module 3 An ESAM security device 5 , an NFC module 6 for communicating with the outside world, an antenna 7 for receiving external NFC signals and obtaining working energy, and a power supply 8 , and the antenna 7 is connected to the NFC module 6 . ESAM security device 5 is an embedded security module based on hardware encryption, supports SWP protocol, PBOC specification, and QPBOC protocol, and can be combined with at least one of SIM card, Micro SD card, TF card, and USB device.
Embodiment 3
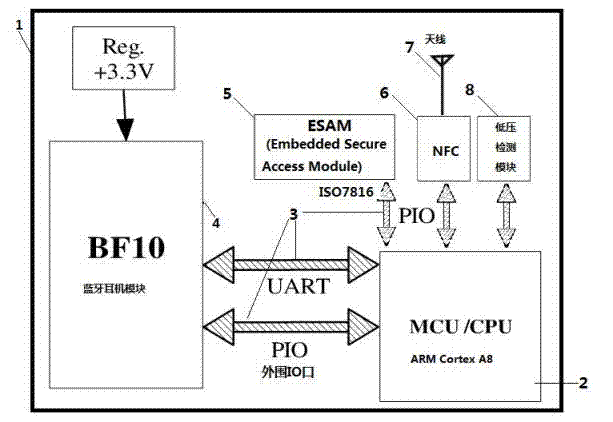
[0029] Embodiment three: a kind of NFC earphone that is used for mobile information security protection, such as image 3 As shown in , it includes an ARM Cortex A8 single-chip microcomputer 2 installed in a housing 1, a BF10 earphone module 4 connected to the single-chip microcomputer 2 through a UART interface module 3, and a BF10 earphone module 4 connected to the single-chip microcomputer 2 through a TF card socket interface module 3 and used for mobile information TF card information security device 5 for security protection, NFC module 6 for communicating with the outside world, antenna 7 for receiving external NFC signals and obtaining working energy, power supply module 8 for power supply, antenna 7 is connected to NFC module 6 . TF card information security device 5 is an information security card integrated with hardware-encrypted smart card and TF card, and supports SWP protocol, PBOC specification, QPBOC protocol, CUPMobile bank card application specification and CU...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com