Program recognition method and device based on machine learning
A program identification and machine learning technology, applied in the computer field, can solve the problems of low efficiency and lag in identifying malicious programs, and achieve the effect of saving manpower and improving identification efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
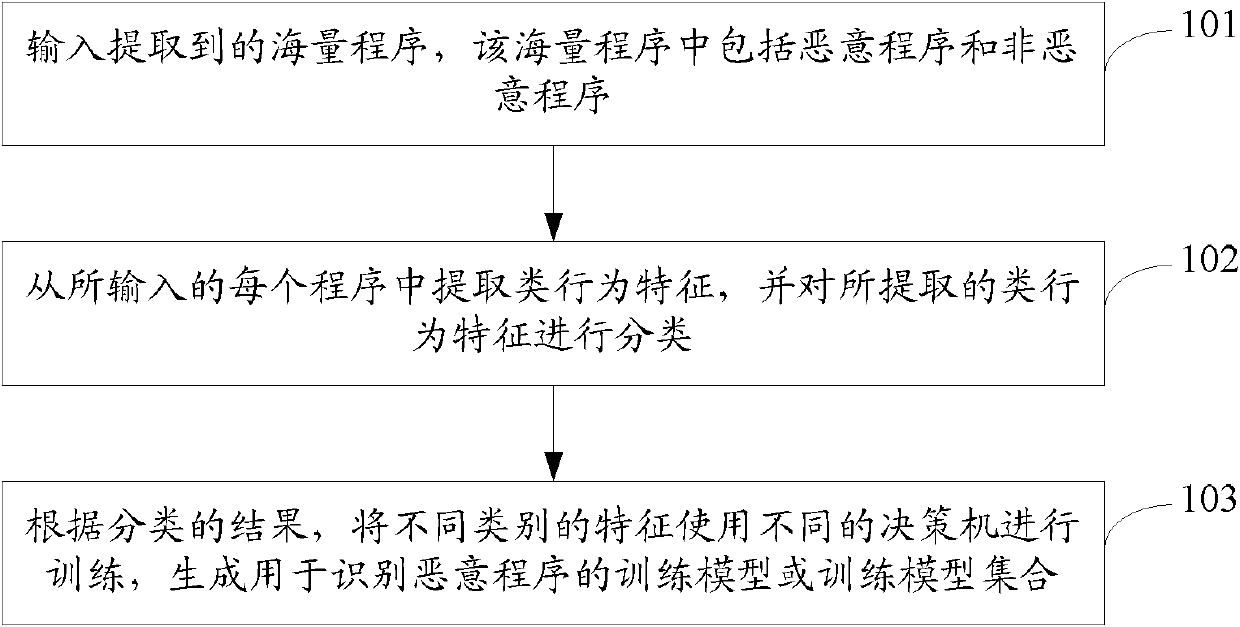
[0053] see figure 1 , a flow chart of the first embodiment of generating a model for identifying program types for this application:
[0054] Step 101: Input the extracted mass programs, the mass programs include malicious programs and non-malicious programs.
[0055] Step 102: extract class behavior features from each input program, and classify the extracted class behavior features.
[0056] Specifically, analyze each program file, extract predefined class behavior features from the program file, generate feature vectors according to the extracted class behavior features, and the black and white attributes of each feature vector, according to the known compiler entry instruction sequence Determine the type of compiler that compiles and generates the corresponding program.
[0057] The class behavior features in the embodiment of the present application are introduced in detail below. The class behavior features can be generally divided into import table library features an...
no. 1 example
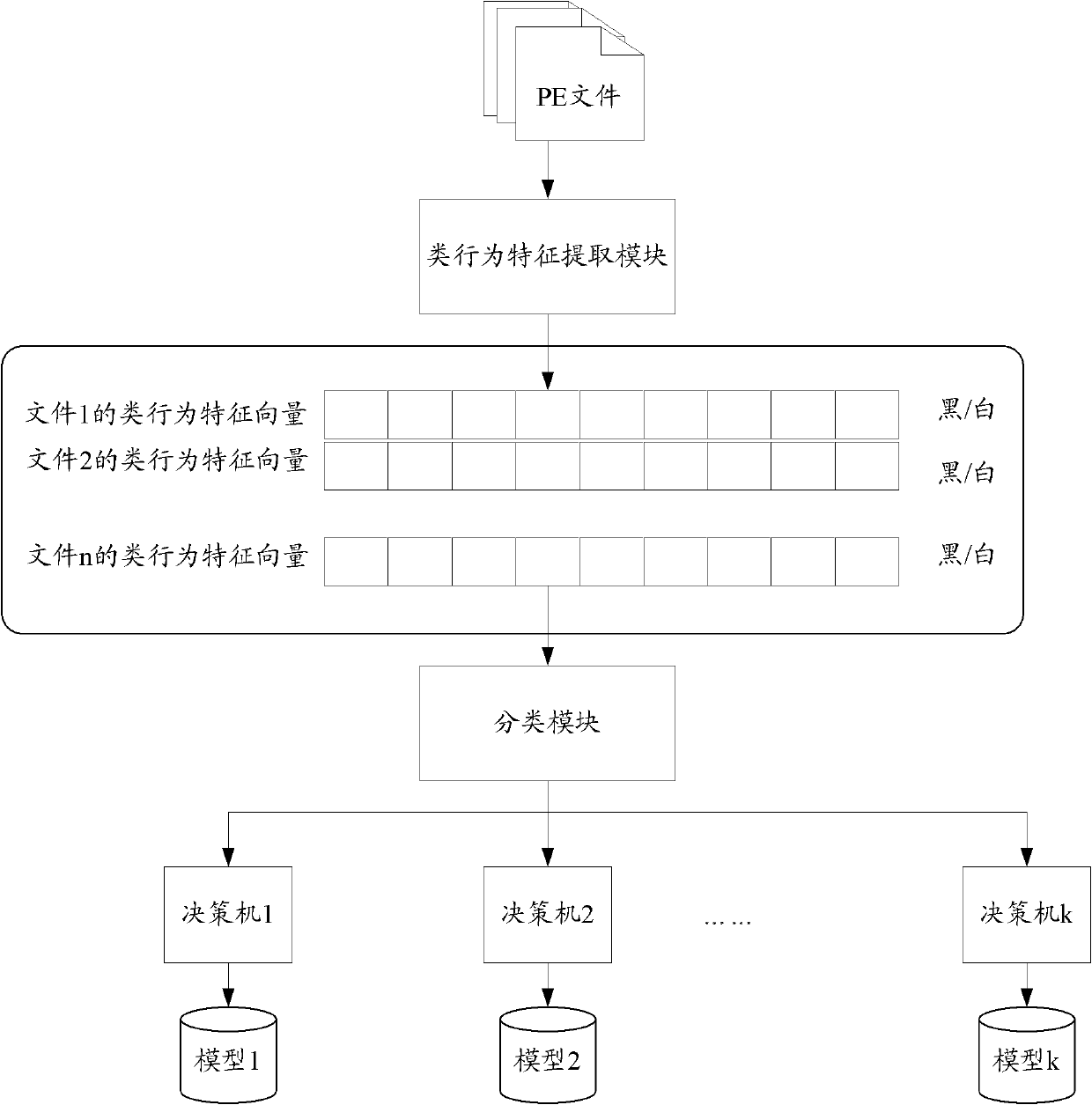
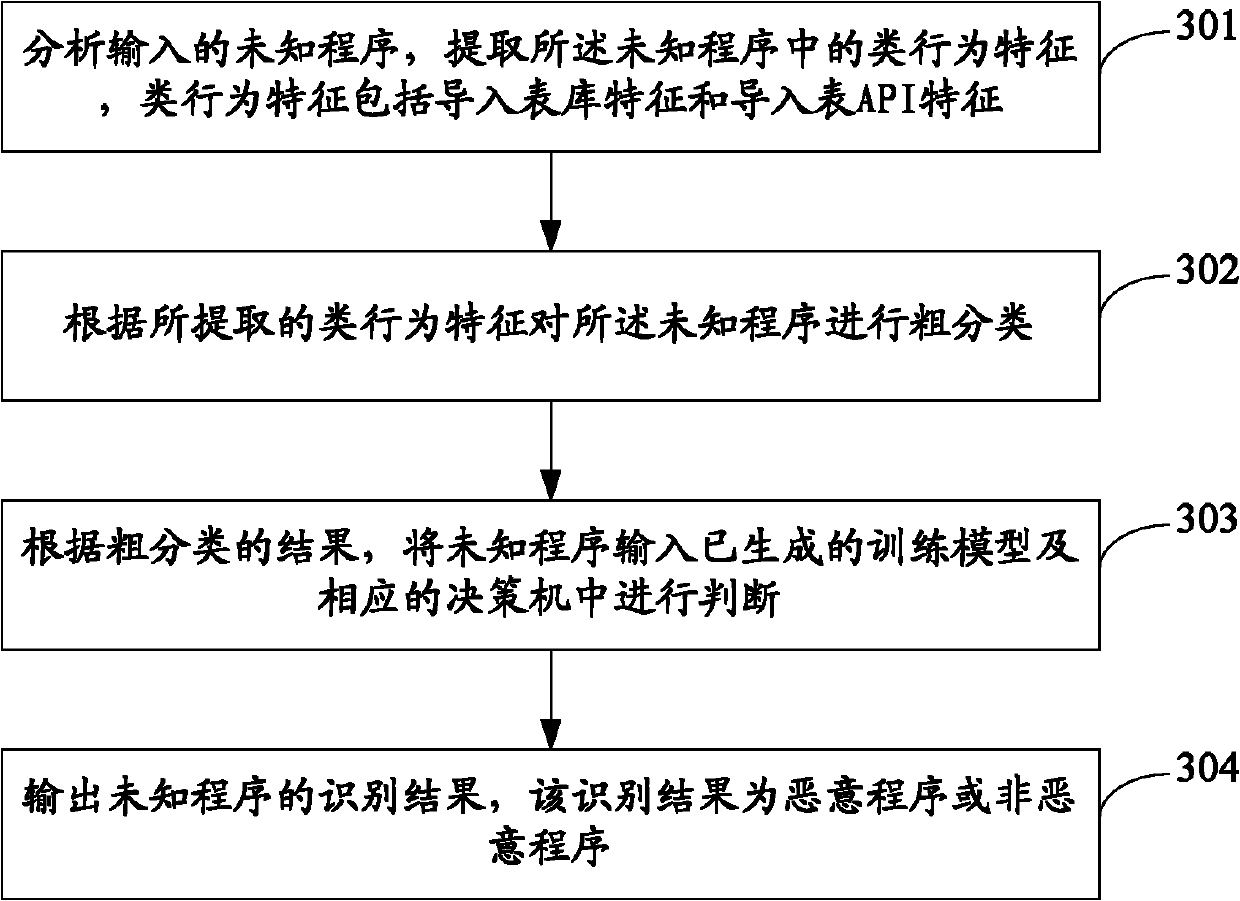
[0150] see Figure 5 , which is the block diagram of the first embodiment of the program recognition device based on machine learning in this application:
[0151] The device includes: an extraction unit 510 , a classification unit 520 , a judgment unit 530 and an output unit 540 .
[0152] Wherein, the extracting unit 510 is configured to analyze an input unknown program, and extract class behavior features in the unknown program, where the class behavior features include import table library features and import table application programming interface API features;
[0153] A classification unit 520, configured to roughly classify the unknown program according to the extracted class behavior characteristics;
[0154] Judgment unit 530, configured to input the unknown program into the generated training model and the corresponding decision machine for judgment according to the result of the rough classification;
[0155] The output unit 540 is configured to output an identif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com