Lightweight authentication and key agreement protocol applicable to electric information acquisition
A technology for authenticating key negotiation and electricity consumption information, which is applied in the field of lightweight authentication key negotiation protocol suitable for electricity consumption information collection, and can solve the problems of high computational cost of SSL protocol, man-in-the-middle attack, and insufficient anti-attack capability. Achieve the effects of low storage and computational overhead, resistance to asynchronous attacks, and fewer communication interactions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] (1) Implementation steps
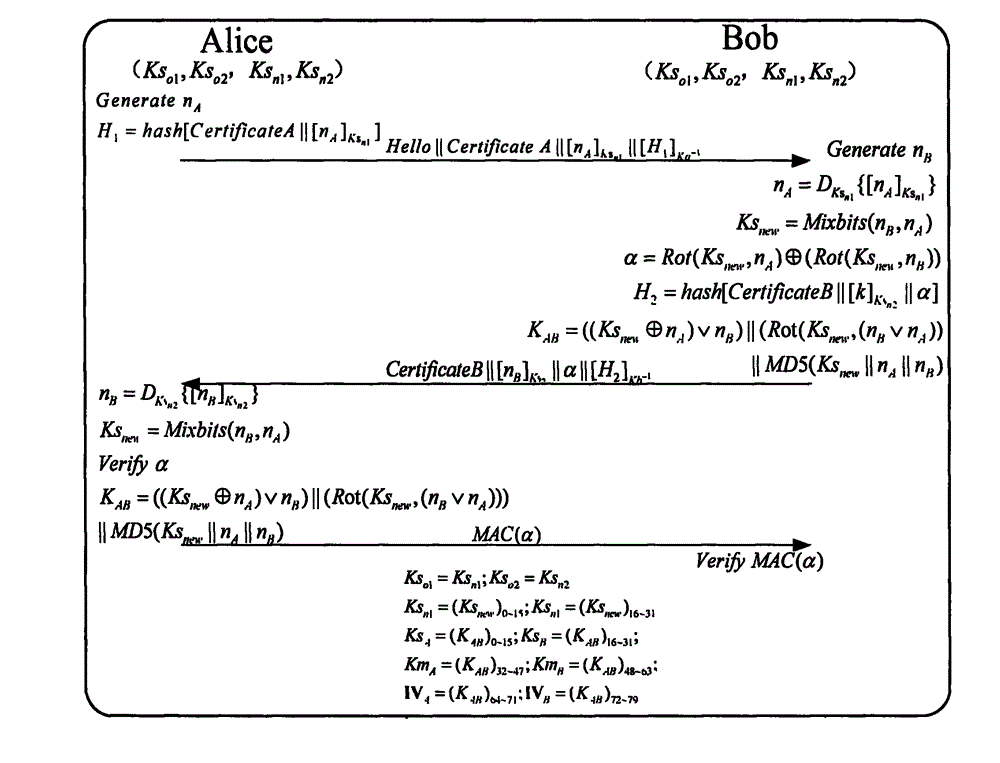
[0021] Such as figure 1 As shown, the protocol includes three stages: identity authentication, key agreement, and key update. The two communicating entities share the old participation key Ks in advance. o1 , Ks o2 And the new insured key Ks n1 , Ks n2 Under normal circumstances, the agreement uses the new insured key to protect the exchange of important parameters. When the identity authentication or key negotiation of the two parties fails, Alice activates the old insured key to make Ks n1 =Ks o1 , Ks n2 =Ks o2 , Restart Hello to initiate the conversation. The specific communication process of the protocol is described as follows:
[0022] 1. Alice sends a Hello message to Bob to start the conversation and generates a 32-byte random number n A , And use the participation key Ks n1 Encryption, attach Alice's digital certificate and Calculate the message digest and encrypt it with Alice's private key to generate a digital signature.
[0023] 2. Afte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com