File security method in limited area based on position information
A technology of location information and limited area, applied in the field of information security, can solve the problems of difficult expansion, no third party, fixed security area, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
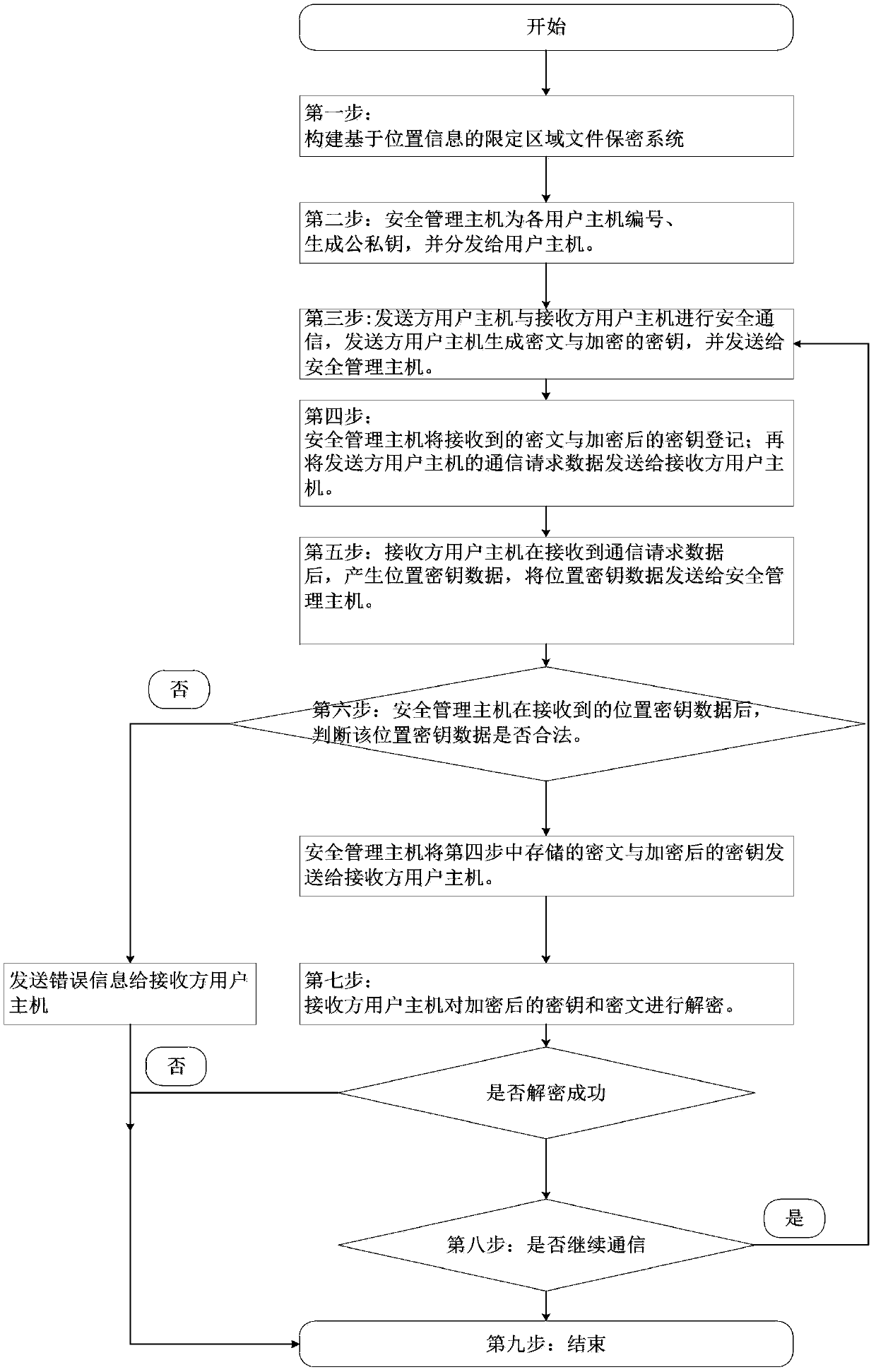
Image
Examples
Embodiment Construction
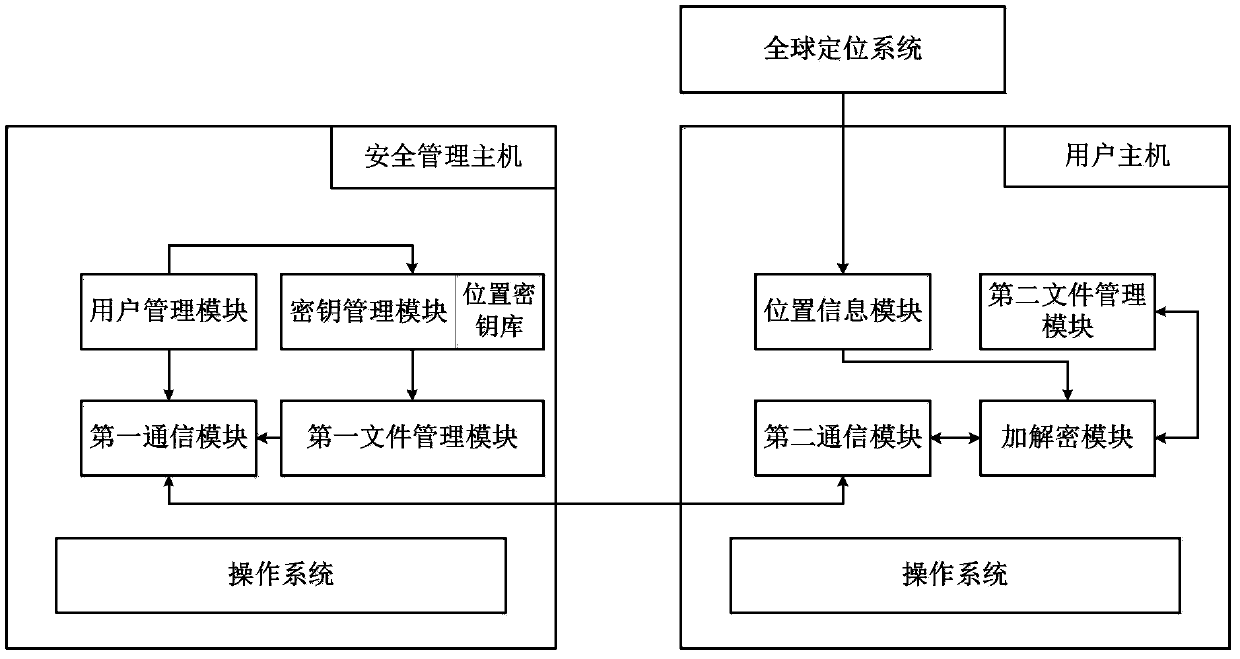
[0054] Such as figure 1 as shown,
[0055] Construct a limited area file security system based on location information, which is composed of user host, security management host, and global positioning system. The user host is the endpoint of the communication network, which is connected to the global positioning system through wireless signals, and the user hosts are connected through the communication network (only one user host is drawn in the figure as an illustration, and there are multiple user hosts in the actual system); security management The host is the core of the entire network, and is connected to the user host and the global positioning system through wireless signals.
[0056] The global positioning system is the existing GPS positioning system, Beidou positioning system, or other positioning systems that can provide location information for user hosts.
[0057] The security management host is a computer used to manage user host communication, on which an oper...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com