Method and system for distributed firewall security policy configuration based on overlay network
A distributed firewall and security policy technology, applied in the field of network security, can solve problems such as the inability to implement firewall policy configuration in the global network, the lack of network device bearer status awareness, and the inability to generate security policies, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
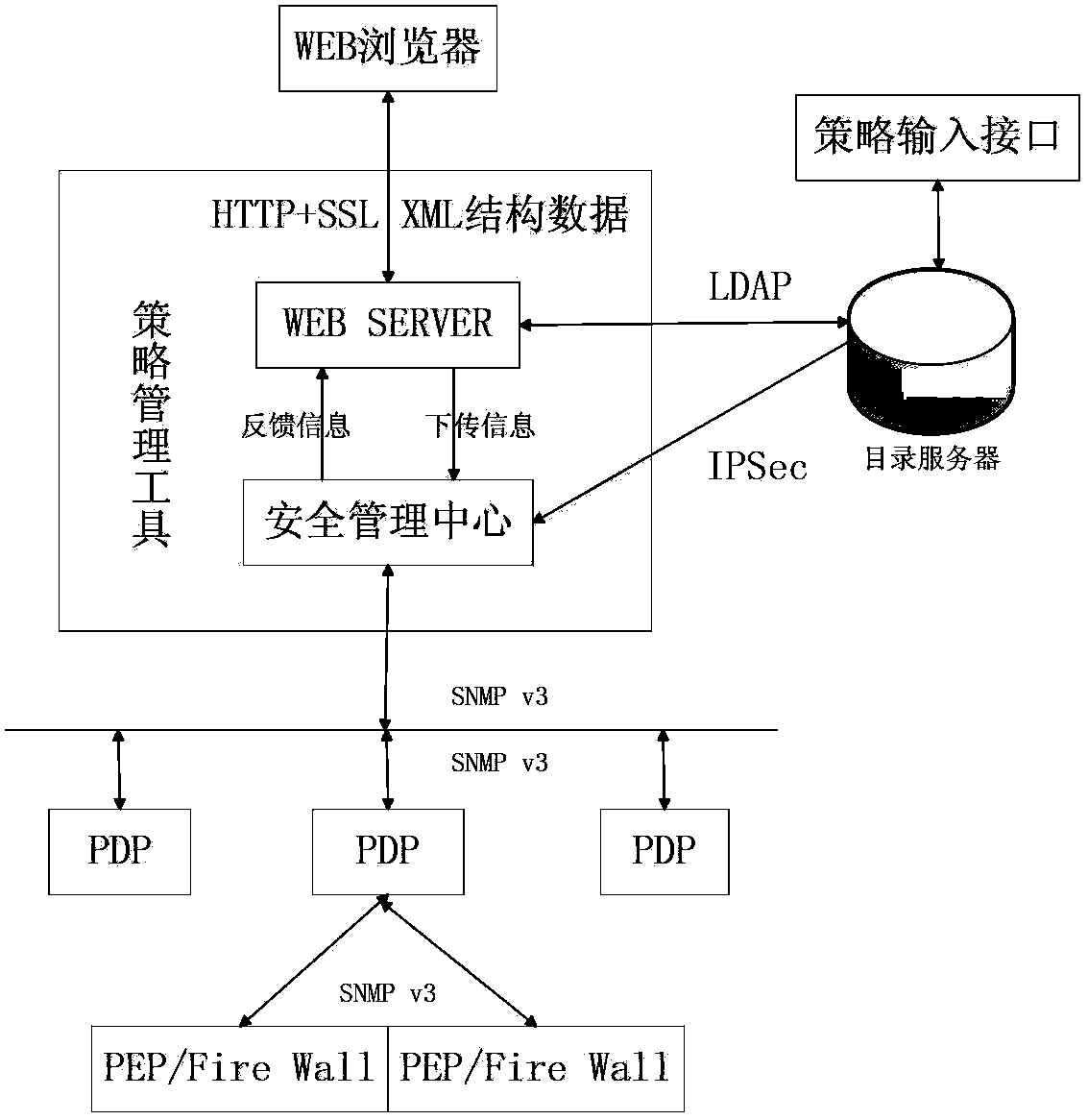
Method used
Image
Examples
Embodiment 1
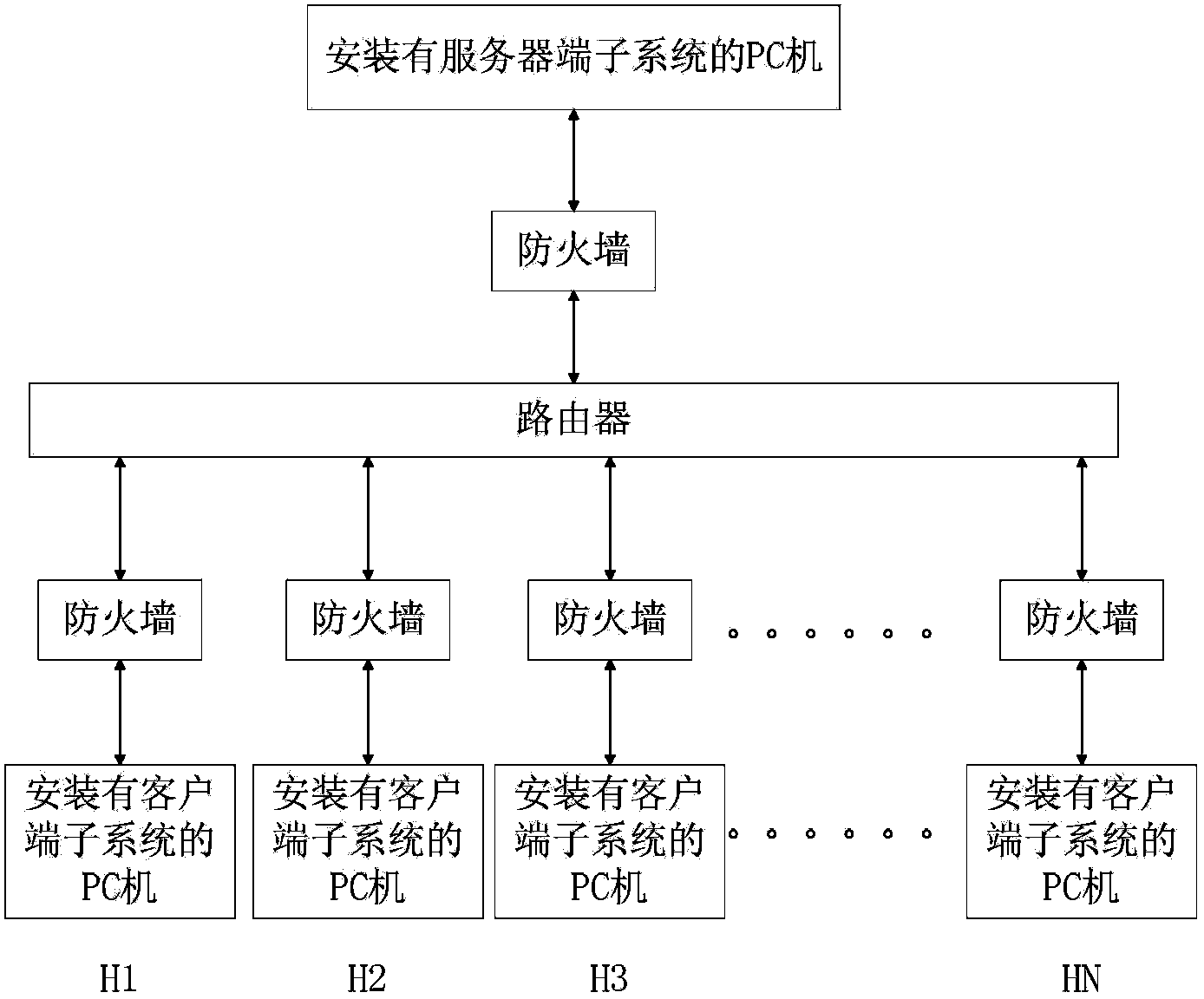
[0096] topology such as Figure 7 Shown:
[0097] In the experimental topology, logical domain 1 and logical domain 2 are two logical domains.
[0098] Smart node 1 (IP address 192.168.11.100, subnet mask 255.255.255.0) in logical domain 1 is the policy decision point of the firewall in the logical domain; firewall 1 (H3CF100S firewall) is host PC1 (IP address 192.168.1.1 , with a subnet mask of 255.255.255.0) can control the traffic and access behavior of the host PC1; the host PC1 uses the application program Scanport to perform port scanning on the host Server.
[0099] Intelligent node 2 (IP address 192.168.12.100, subnet mask 255.255.255.0) in logical domain 2 is the policy decision point of the firewall in the logical domain; firewall 2 (CISCOASA firewall) is host PC2 (IP address 192.168.2.1 , with a subnet mask of 255.255.255.0) can control the traffic and access behavior of the host PC2; the host PC2 uses the application program Scanport to perform port scanning on t...
Embodiment 2
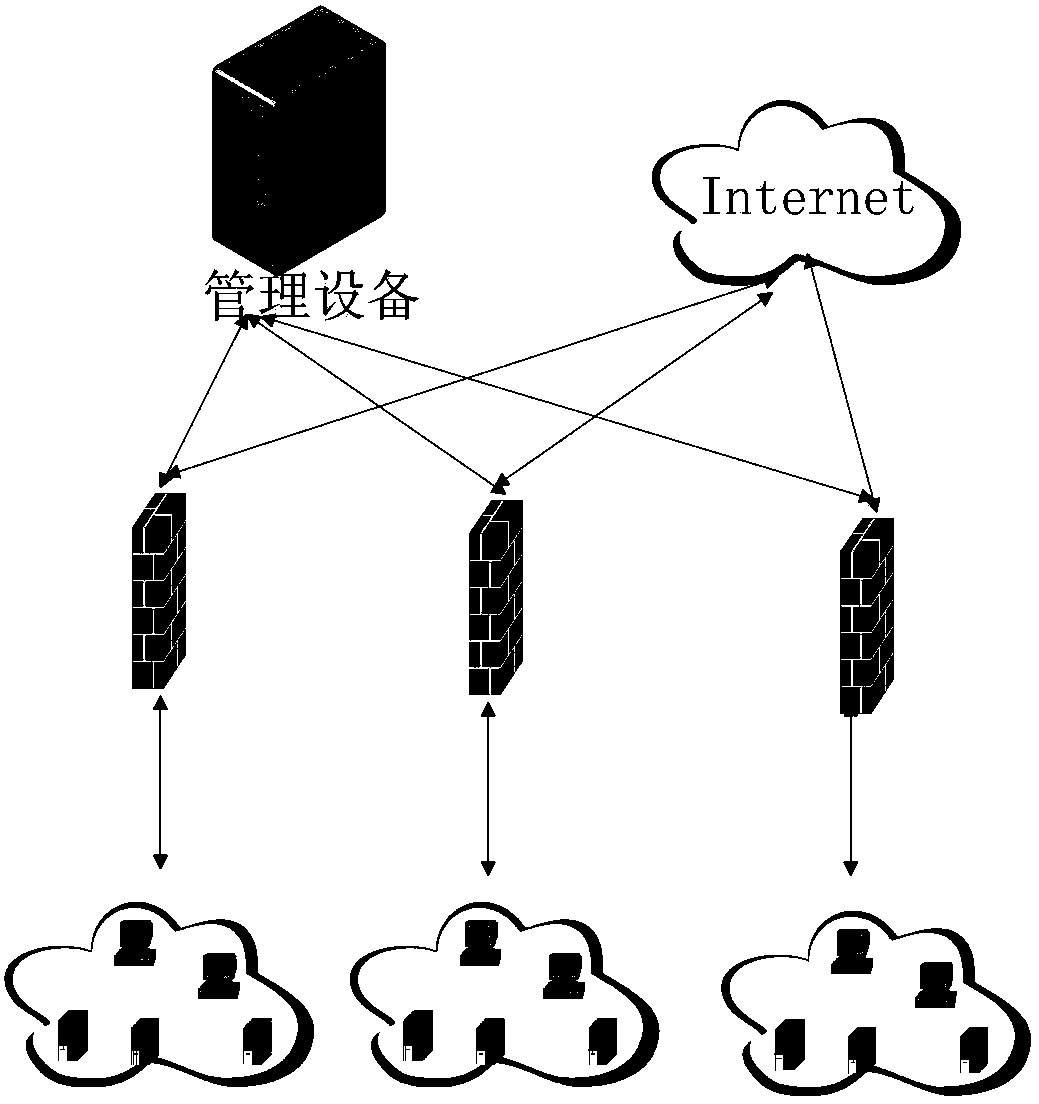
[0136] topology such as Figure 13 Shown:
[0137] In the experimental topology, logical domain 1 and logical domain 2 are two logical domains.
[0138] Intelligent node 1 (IP address 192.168.11.100, subnet mask 255.255.255.0) in logical domain 1 is the policy decision point of the firewall in the logical domain; firewall 1 (H3CF100S firewall) is the PC-VOD host (IP address 192.168 .1.2, subnet mask is 255.255.255.0) and the egress firewall of PC-FTP1 host (IP address is 192.168.1.1, subnet mask is 255.255.255.0), can control PC-FTP1 host and PC-VOD host Traffic and access behavior; the PC-VOD host is installed with the application program VLC Media Player, which can obtain video-on-demand services from the Server host; the PC-FTP1 host runs the application program FlashFXP, which can download FTP data from the Server host;
[0139] Intelligent node 2 (IP address 192.168.12.100, subnet mask 255.255.255.0) in logical domain 2 is the policy decision point of the firewall in th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com