Verifying method and system for intelligent secret key
A technology of smart password key and verification method, which is applied in the direction of user identity/authority verification, etc. It can solve the problems of smart password key no longer safe, key leakage, etc., and achieve the effect of reducing the possibility of cross-selling and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
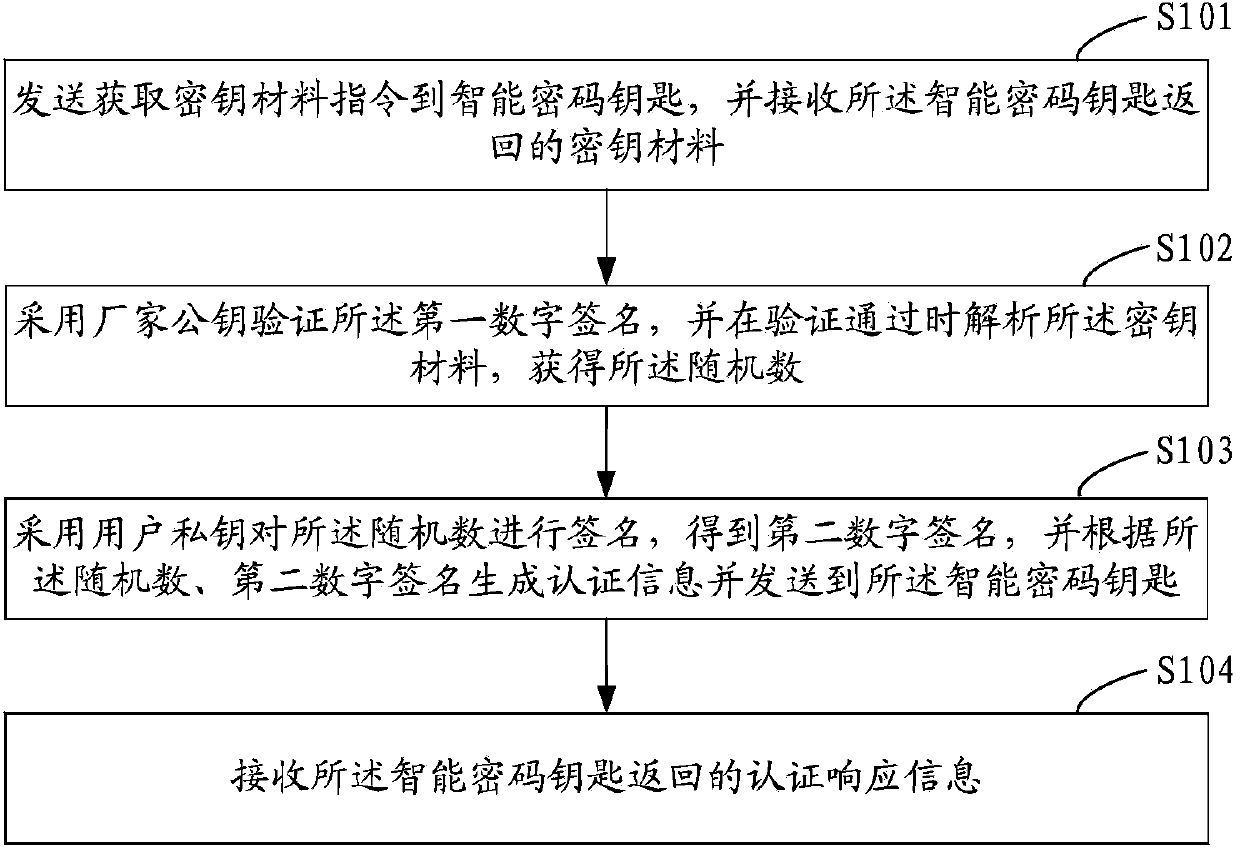
[0035] figure 1 A schematic flowchart of Embodiment 1 of the verification method for the smart encryption key of the present invention is shown in . In the first embodiment, the processing procedure of the user terminal is taken as an example for description.
[0036] see figure 1 Shown, a kind of verification method of intelligent password key, comprises the following steps:
[0037] Step S101, sending the key material acquisition instruction to the smart encryption key, and receiving the key material returned by the smart encryption key; the key material includes: the smart encryption key generated according to the key material acquisition instruction The random number, the first digital signature obtained after the smart cryptographic key signs the random number with the private key of the manufacturer. That is, in the embodiment of the present invention, after receiving the key material acquisition instruction sent by the client, the smart encryption key will randomly g...
Embodiment 2
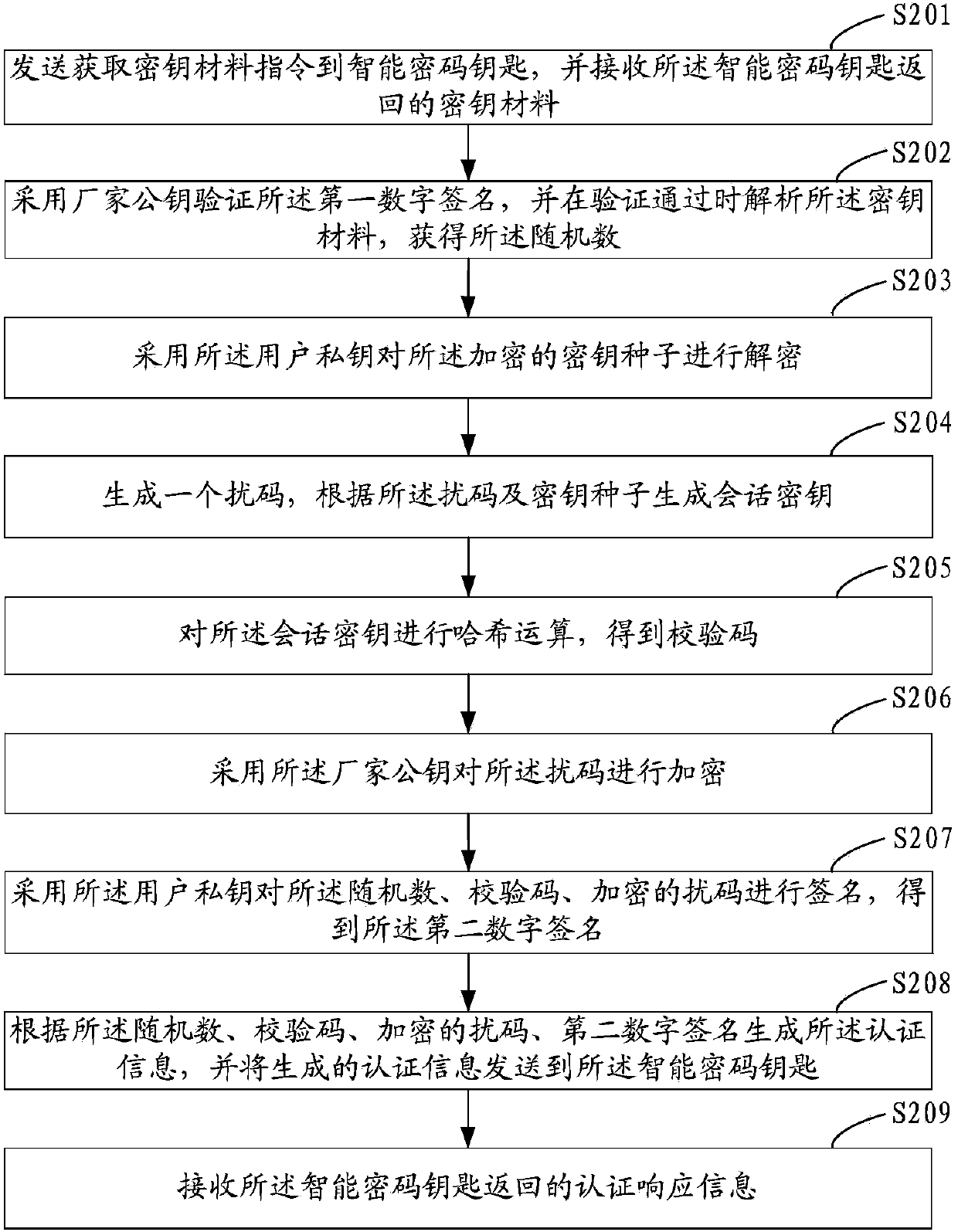
[0048] The present invention also provides a verification method of the smart cryptographic key, which can generate a session key while realizing bidirectional verification of the smart cryptographic key. In the second embodiment, the processing procedure of the client is still taken as an example for description.
[0049] Such as figure 2 As shown, a verification method for an intelligent password key comprises the following steps:
[0050] Step S201. Send the key material acquisition instruction to the smart encryption key, and receive the key material returned by the smart encryption key; the key material includes: the smart encryption key generated according to the key material acquisition instruction random number, the key seed generated by the smart cryptographic key according to the key material acquisition instruction and encrypted with the user’s public key, and the random number and the encrypted key seed encrypted by the smart cryptographic key using the manufactu...
Embodiment 3
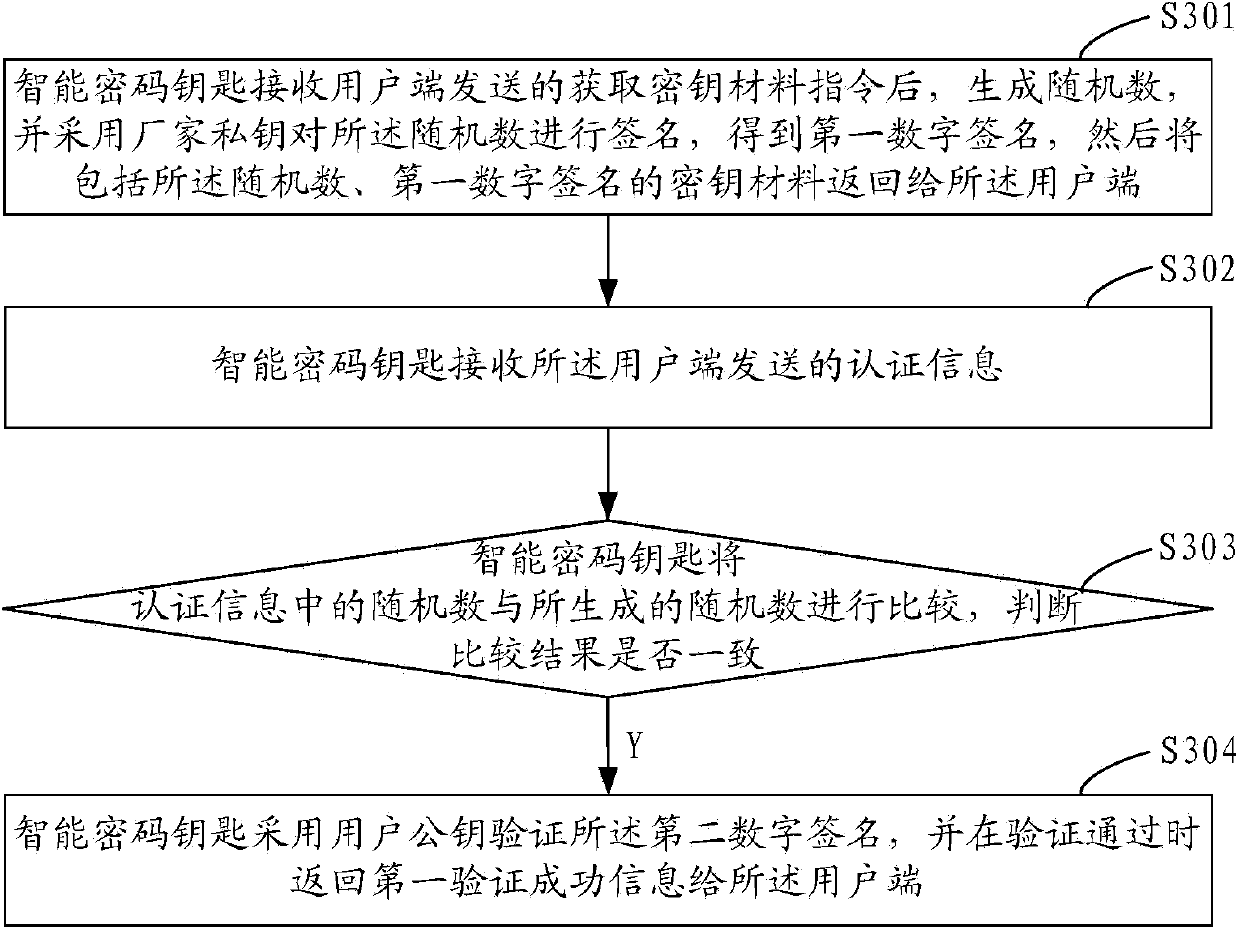
[0072] image 3 A schematic flow chart of Embodiment 3 of the verification method for the smart cryptographic key of the present invention is shown in . In the third embodiment, the processing process of the smart password key terminal is taken as an example for illustration.
[0073] Such as image 3 As shown, in the third embodiment, the processing of the smart password key terminal includes the following steps:
[0074] Step 301: After receiving the key material acquisition instruction sent by the client, the smart cryptographic key generates a random number, and signs the random number with the manufacturer's private key to obtain a first digital signature, and then includes the random number, The key material of the first digital signature is returned to the client;
[0075] Step 302, the smart cryptographic key receives the authentication information sent by the client; the authentication information includes: the client uses the manufacturer's public key to verify th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com