A POS and mobile terminal communication method, encryption method and device, and a POS
A mobile terminal communication and mobile terminal technology, applied in the field of encryption, can solve the problems of information leakage, low operation rate, restricted use, etc., and achieve the effects of less hardware resources, high uniqueness, and small amount of calculation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
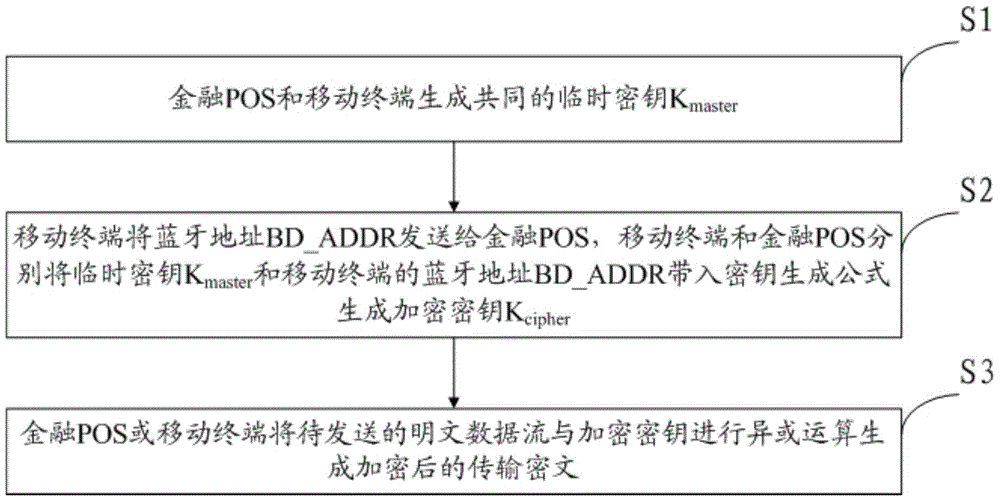
[0038] see figure 1 , the present embodiment is a kind of encryption method of financial POS and mobile terminal communication, comprises steps:
[0039] S1, the financial POS and the mobile terminal generate a common temporary key K master .
[0040] S2. The mobile terminal sends the Bluetooth address BD_ADDR to the financial POS, and the mobile terminal and the financial POS respectively send the temporary key K master Bring the Bluetooth address BD_ADDR of the mobile terminal into the key generation formula to generate the encryption key K cipher ;
[0041] S3. The financial POS or the mobile terminal performs an XOR operation on the plaintext data stream to be sent and the encryption key to generate encrypted transmission ciphertext.
[0042] In this embodiment, the temporary key K master and encryption key K cipher The length is 128 bits, so it greatly reduces the amount of calculation for key generation and the amount of calculation when using the encryption key to...
Embodiment 2
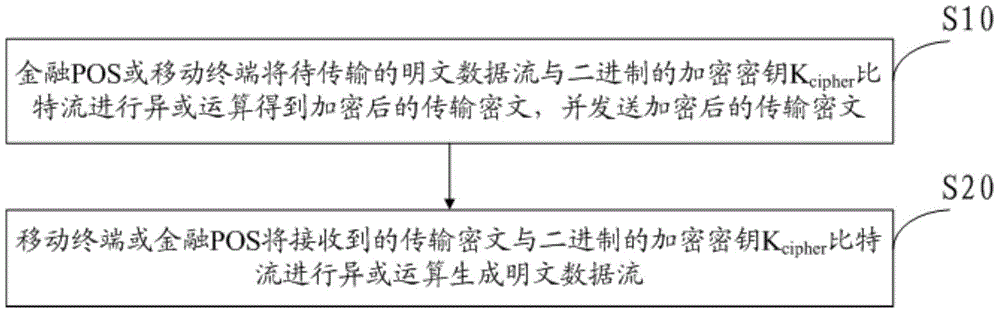
[0068] see figure 2 , the present invention also provides a kind of financial POS and mobile terminal communication method, the data of this communication transmission adopts above-mentioned encryption method to encrypt, after encrypting, also comprise steps:
[0069] S10. The financial POS or mobile terminal combines the plaintext data stream to be transmitted with the binary encryption key K cipher Perform XOR operation on the bit stream to obtain the encrypted transmission ciphertext, and send the encrypted transmission ciphertext;
[0070] S20, the mobile terminal or financial POS will receive the transmission ciphertext and the binary encryption key K cipher The bit stream is XORed to generate a plaintext data stream.
[0071] In this embodiment, the financial POS and mobile terminal communication method data encryption encryption key length is short, the algorithm is simple, and occupies less software and hardware resources, so it is especially suitable for financial ...
Embodiment 3
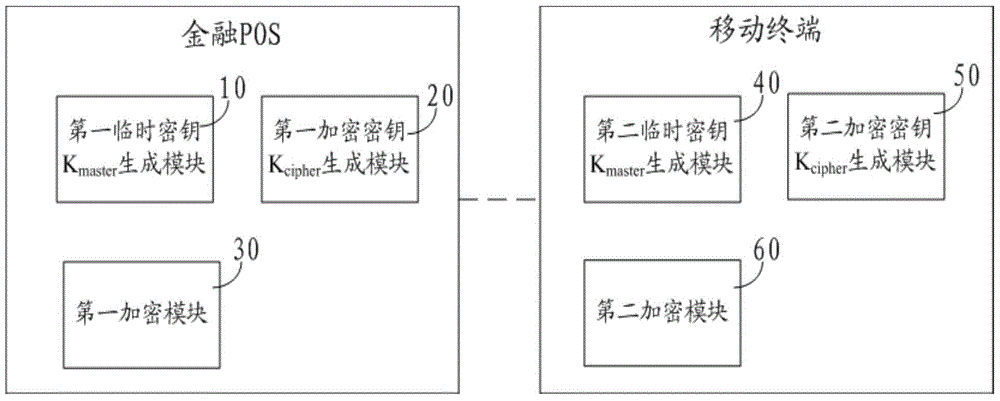
[0073] see image 3 , the present invention also provides an encryption device for communication between a financial POS and a mobile terminal, the encryption device includes a mobile terminal and a financial POS, and the financial POS includes a first temporary key K master Generating module 10, first encryption key K cipher Generating module 20 and first encryption module 30, described mobile terminal comprises the second temporary key K master r generation module 40, the second encryption key K cipher Generating module 50 and second encryption module 60;
[0074] The first ephemeral key K master Generation module 10 and second temporary key K master Generating module 40 is respectively used for financial POS and mobile terminal to generate common temporary key K master ;
[0075] The second encryption key K cipher The generating module 50 is used to send the bluetooth address BD_ADDR to the financial POS, and the temporary key K master Bring the Bluetooth address BD...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com