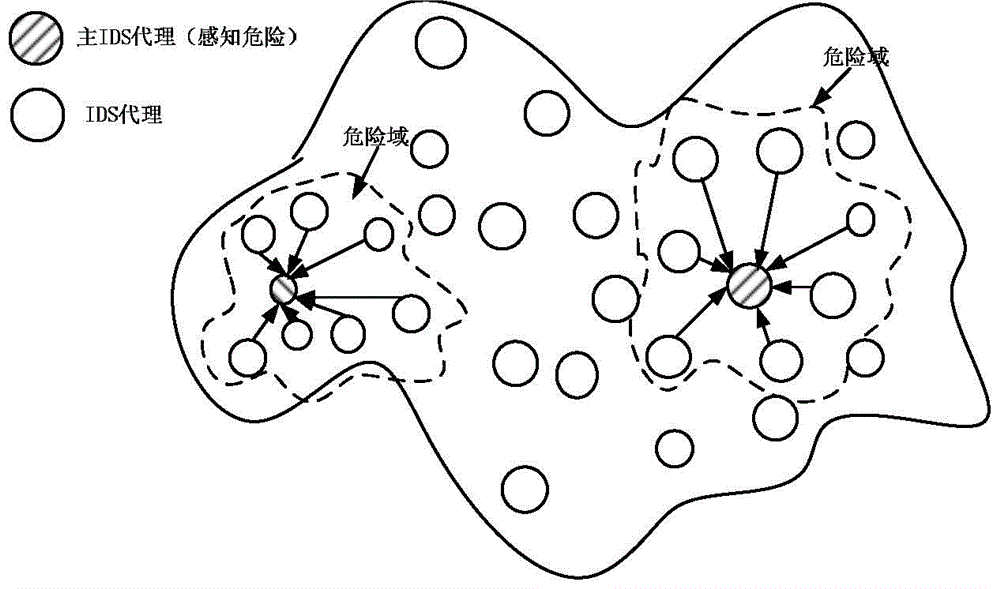
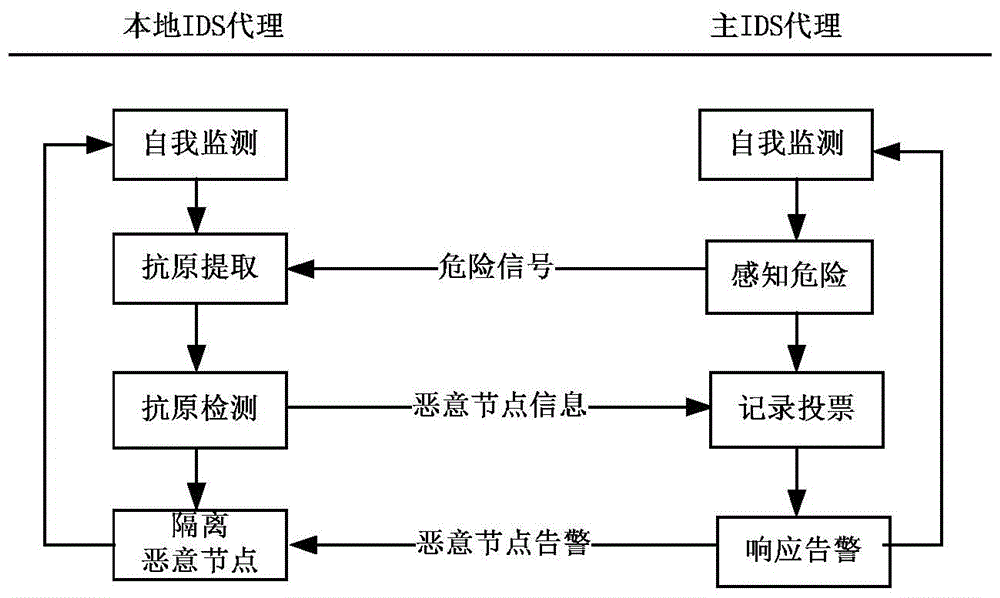
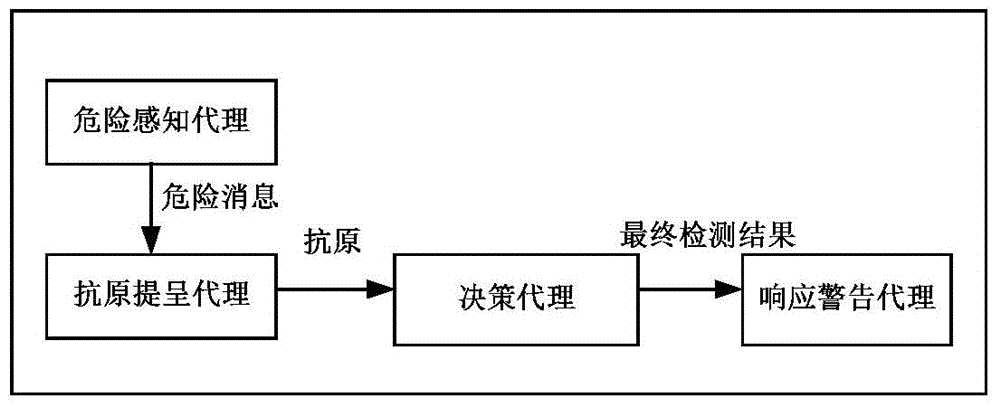
A joint intrusion detection method for wsns based on dangerous multi-agent
An intrusion detection, multi-agent technology, applied in advanced technology, security devices, electrical components, etc., can solve the problems of increasing network communication load, long training time, and large training overhead, saving detection energy consumption, enhancing detection efficiency, The effect of extending the operating life
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0077] The embodiment is named DT-MASC. In order to verify the functional characteristics of DT-MASC, it will be simulated and compared with the master-slave multi-agent detection scheme DT_MAS based on risk theory and the typical multi-agent detection scheme MAIDS. The comparison performance includes the detection rate and detection of energy consumption, the simulation platform is OMNET++, and the main parameter settings of the simulation scene are shown in Table 2.
[0078] Table 2 Simulation experiment parameters
[0079]
[0080]
[0081] According to the simulation parameters in Table 2, the nodes are randomly deployed in the network, and the location of malicious nodes can be randomly selected according to the simulation needs. By adjusting the number of malicious nodes to adjust the intensity of network malicious attacks, the detection performance of each intrusion detection scheme under different attack intensities is studied, and each data is the average value ob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com