Method of application classification in Tor anonymous communication flow
A technology for anonymous communication and application classification, applied in the research field of anonymous communication and traffic analysis, it can solve problems such as abuse and network security threats, and achieve the effect of fast running speed, less network load and good classification effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
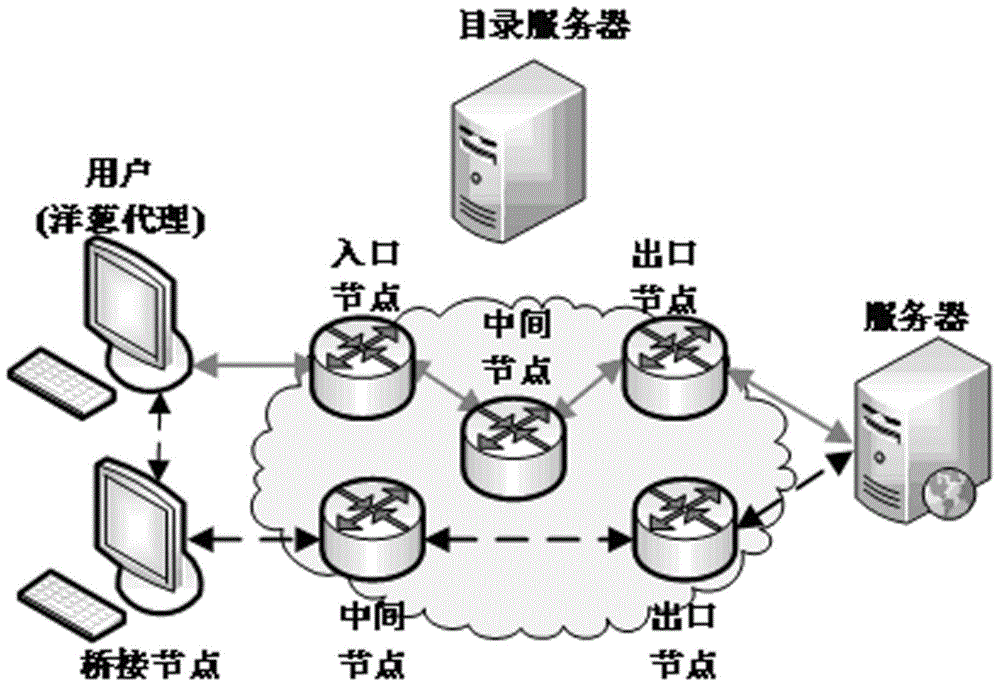
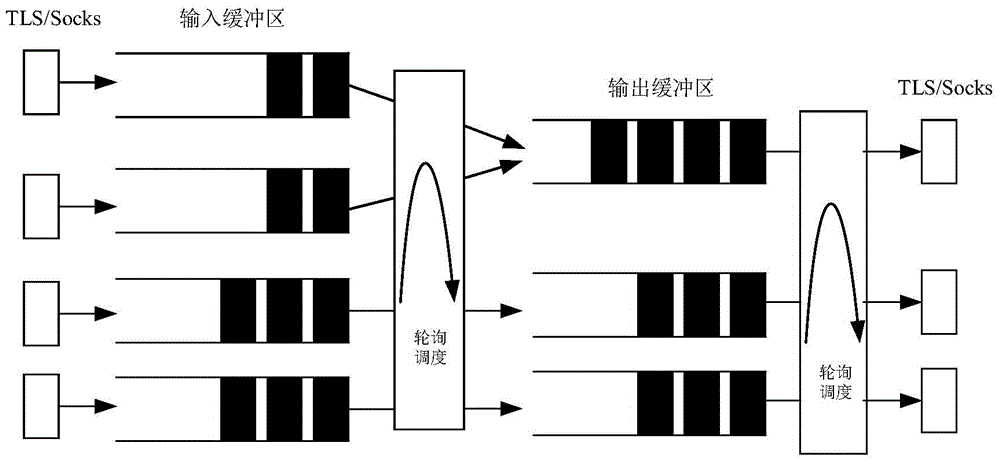
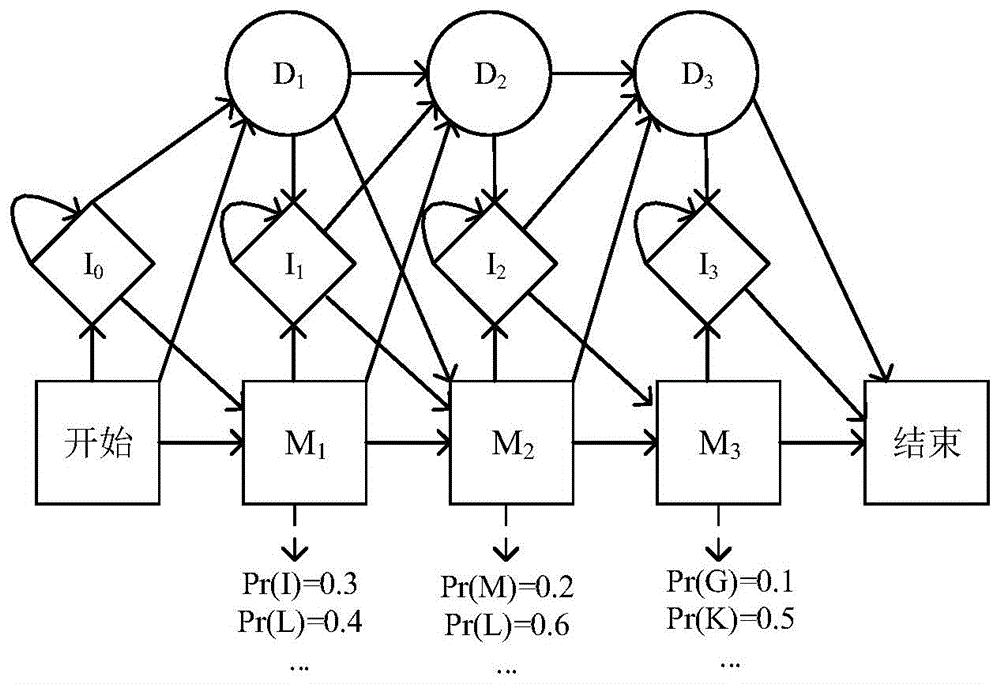
[0024] This method mainly solves the problem of obtaining upper-layer application type information in Tor anonymous communication traffic, and involves related technologies such as feature selection, sample preprocessing, and traffic modeling. This method first uses Tor's data packet scheduling mechanism to define the concept of flow bursts, and uses the volume and direction of flow bursts as classification features. Then the data samples were preprocessed based on the K-means clustering algorithm and the multiple sequence alignment algorithm, and the overfitting and length inconsistencies of the data samples were solved by numerical symbolization and gap insertion. Finally, using the Profile Hidden Markov Model to model the uplink and downlink Tor anonymous communication traffic of different applications, a heuristic algorithm is proposed to quickly establish the Profile Hidden Markov Model. In the specific classification, the characteristics of the network traffic to be clas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com