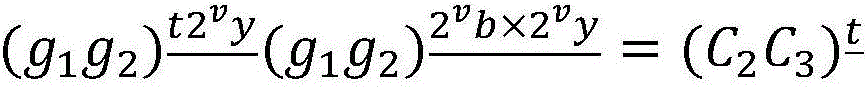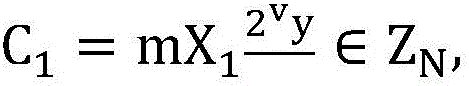A Public Key Encryption Method in Signed Quadratic Residue Groups
A quadratic residual, public key encryption technology, applied in the direction of public key of secure communication, digital transmission system, electrical components, etc., can solve the problems of inefficient one-time signature technology, low efficiency, etc., to achieve high computing efficiency and practical value , the effect of reducing the number of public and private keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be described in detail below in conjunction with the accompanying drawings.
[0037] The invention provides a public key encryption method in a signed quadratic residual group, comprising the following steps:
[0038] Step 1: Set system parameters;
[0039] The receiver or a unified security communication platform is responsible for setting the security parameters. After the parameters are set, it is broadcast to all users; the system parameters to be set are as follows: k is a security parameter, and v is the bit length of the hash function value.
[0040] Step 2: Generate a key;
[0041] 2.1. The receiver selects two prime numbers P and Q according to the security parameter k, and calculates N=PQ, where P=2p+1, Q=2q+1, and both p and q are prime numbers;
[0042] 2.2. Select a collision-resistant hash function H to satisfy H: Among them, Z N is the remainder group modulo N, is the signed quadratic residue group modulo N;
[0043] 2....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com