Trusted third-party software building method
A construction method and credible technology, applied in the fields of information security and trusted computing, can solve the problems that users cannot trust security requirements, cannot prove authenticity, and monitoring methods are not credible, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] The present invention will be further described below in combination with embodiments.
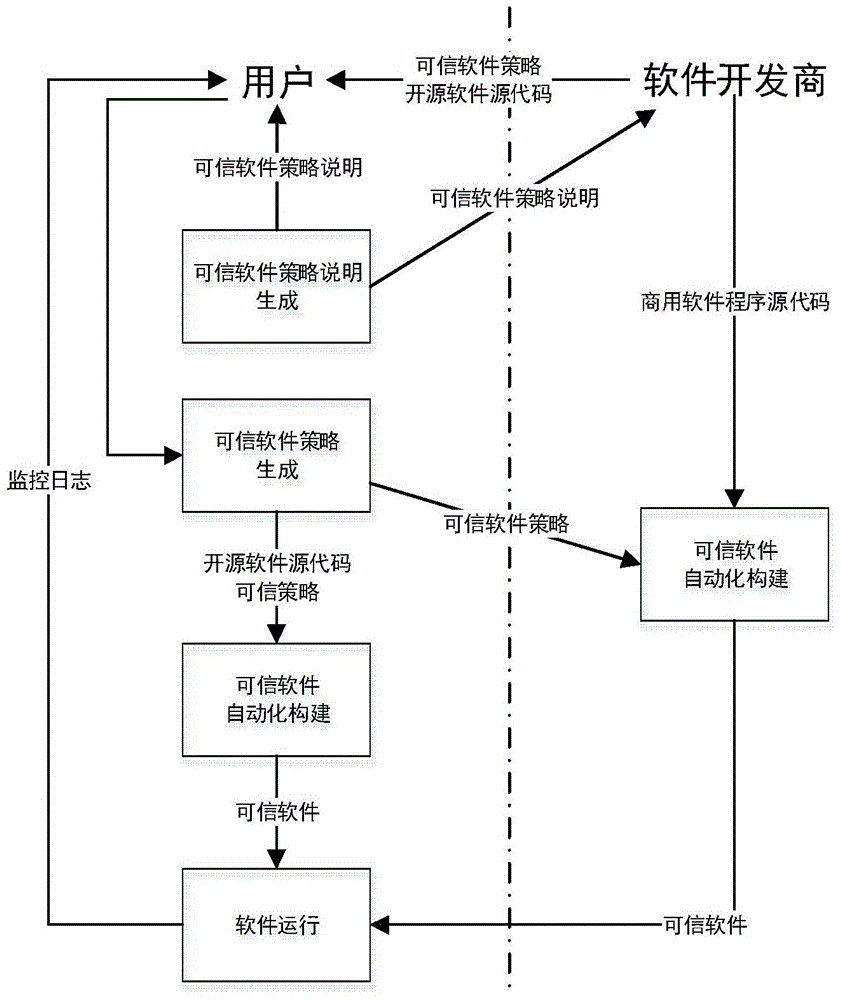
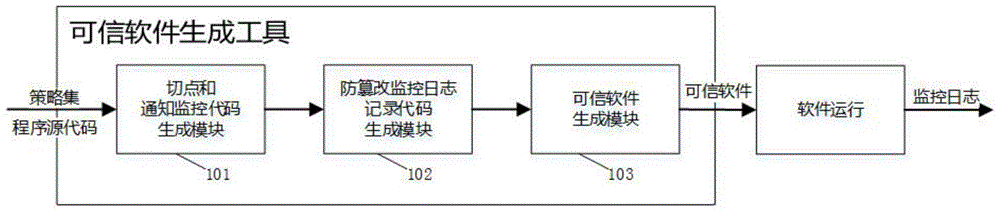
[0074] For third-party software whose security is unknown, users can use the method involved in the present invention to build trusted software that meets their security requirements. The flow chart of the implementation method is as follows: figure 1 shown, including the following steps:
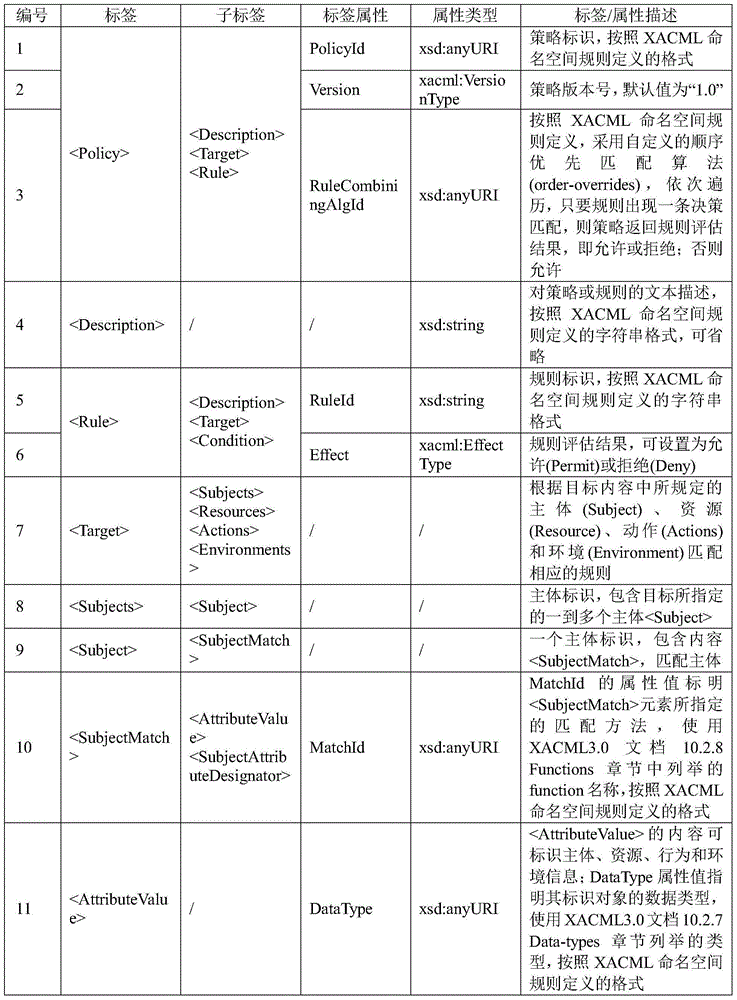
[0075] Step 1, generate the syntax and semantics description of the XACML trusted software policy, as shown in Table 1 and Table 2, to help users formulate trusted software policies that meet their own needs.
[0076] Step 2, generating a trusted software policy. Generate baseline policies, custom parameter extensions, custom policies.
[0077] 1) Baseline policy generation, according to the trusted software policy semantic description in step 1, write the corresponding content of the general policy listed in the trusted software policy semantic description into the corresponding la...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com