Secure data processing
A technology for secure data and secure processing, which is used in electrical digital data processing, secure communication devices, computer security devices, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0078] overview
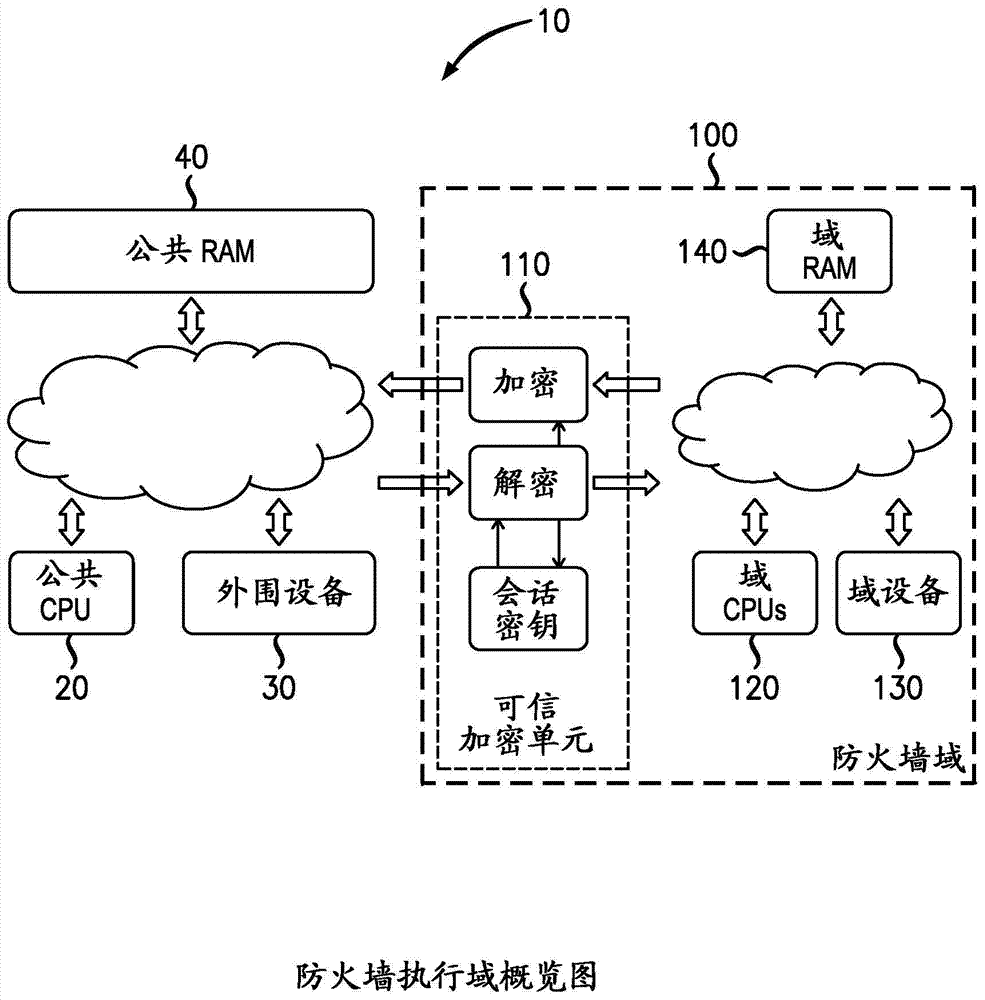
[0079] figure 1 Firewall enforcement domain 100 is generally shown implemented in system 10 . figure 1 The system shown in includes a firewall execution domain 100 , a common processing unit 20 , a common peripheral 30 and a common RAM 40 . Firewall Enforcement Domain (FDE) 100 includes Trusted Cryptography Unit (TCU) 110 , which is operable to encrypt and decrypt data leaving and entering FDE 100 . The FDE further includes a domain processing unit 120 , domain devices and peripherals 130 , and domain RAM 140 .
[0080] In any of the following CPUs, a peripheral, DMA controller, or general-purpose initiator operable to issue RAM access requests on the memory access bus is called a "host". Hosts inside the FDE 100 are called "domain hosts" and hosts outside the FDE domain are called "public hosts".
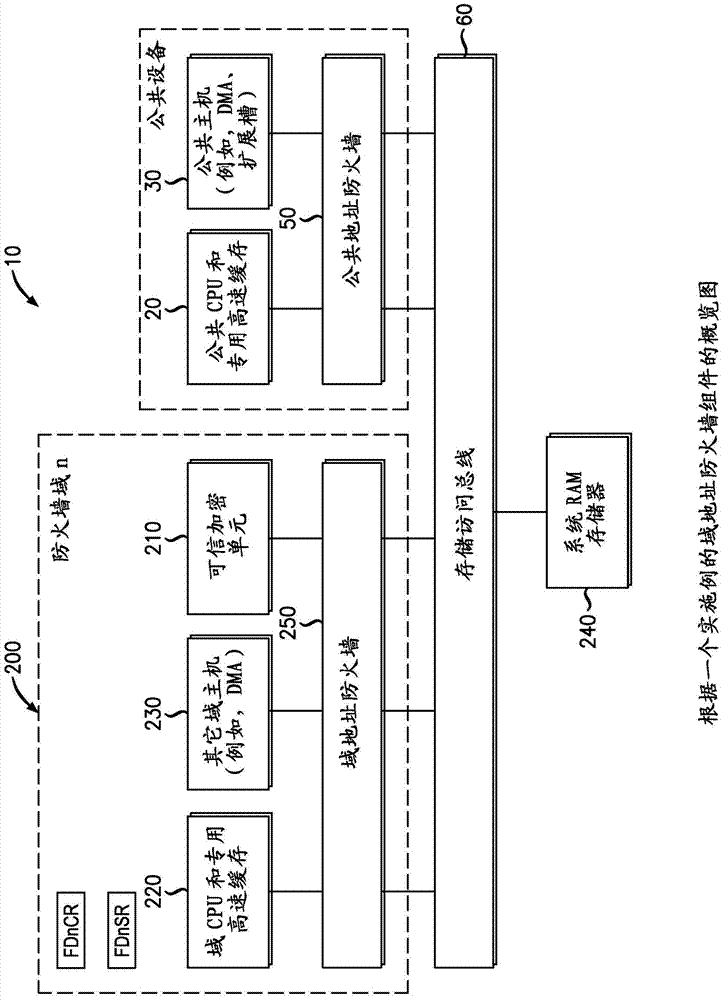
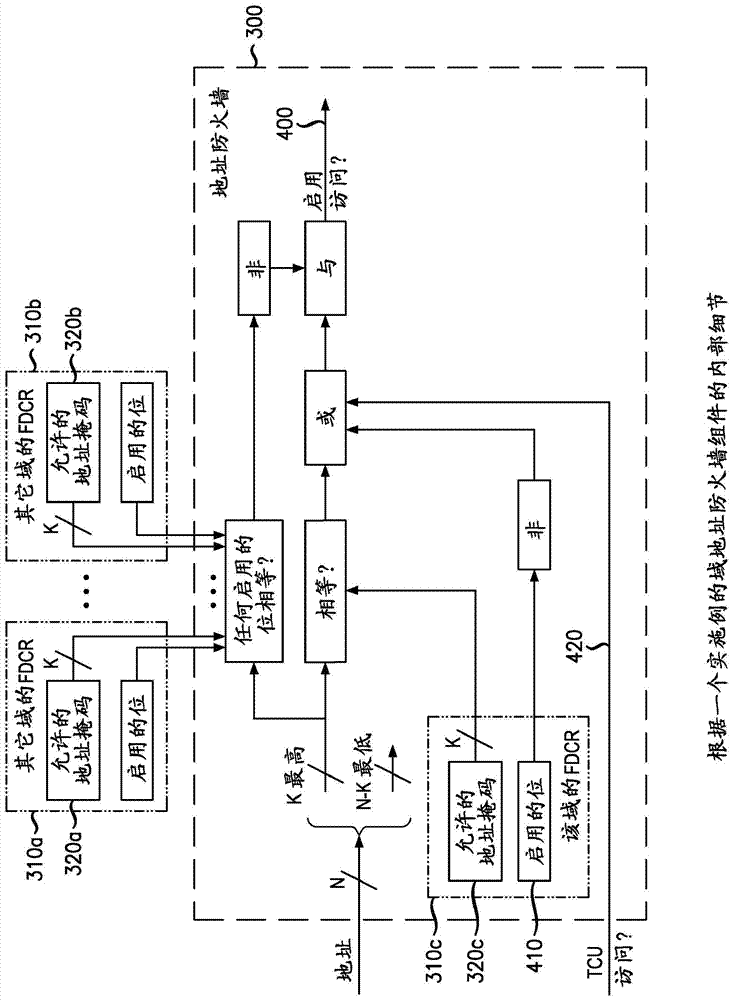
[0081] FDE 100 has a plurality of devices 130 (including hosts, such as processors 120 (and DMA channels)) and storage spaces 140 (specified in terms of physi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com