Security operation method of wireless local area network
A wireless local area network and safe operation technology, applied in the field of wireless local area network safe operation, can solve the problems of weak wireless local area network security evaluation and monitoring capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] Below in conjunction with accompanying drawing, structure and working process of the present invention will be further described.
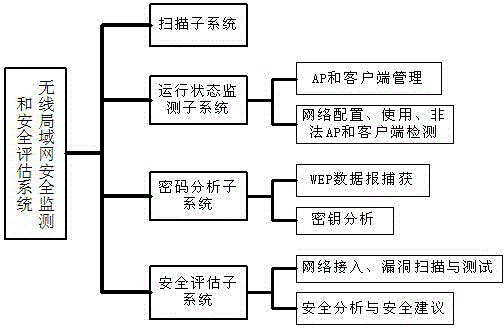
[0038] like figure 1 As shown, a method for safe operation of a wireless local area network includes the following steps:
[0039] Step 1. Perform a global scan on the wireless LAN to obtain the user names and MAC addresses of APs and clients accessing the LAN;
[0040] Step 2, monitor the running state of the client in the wireless local area network, manage the AP and the client, monitor the network configuration and usage status, detect illegal AP and client and generate an illegal user list;
[0041] Step 3, carry out cryptographic analysis to illegal AP and client, by capturing the WEB datagram of illegal AP and client, its password is cracked, obtains the key of illegal user;
[0042] Step 4. Carry out vulnerability scanning and testing on the client in the wireless local area network;
[0043] Step 5. Set up a wireless local area ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com