Method for inhibiting topology oscillation through IS-IS (intermediate system to intermediate system) protocol
A topology and protocol technology, applied in the field of network equipment, can solve problems such as consumption of computing resources and interruption of business data flow, and achieve the effects of saving computing resources, avoiding communication interruption, and ensuring smooth communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] A method for IS-IS protocol to suppress topology oscillation,
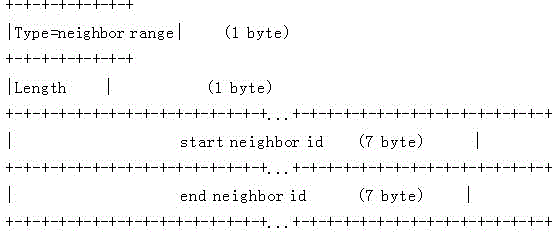
[0034]A: When the target intermediate system, that is, the target IS, fills in the neighbor information in the neighbor TLV in the LSP, it fills in the neighbor IDs in ascending order of the neighbor IDs.
[0035] B: When the target intermediate system, that is, the target IS, generates an LSP, if the LSP is filled with a neighbor TLV, it must fill in a neighbor range TLV.
[0036] C: When the target intermediate system (i.e., the target IS) generates an LSP, the neighbor ID in the neighbor range TLV starts to fill in the neighbor ID: if this LSP fragment is the first LSP fragment to fill in the neighbor TLV, the neighbor ID starts The neighbor ID is filled with all 0x00; if this LSP segment is not the first LSP segment to fill in the neighbor TLV, then the start neighbor ID, that is, the start neighbor ID is filled with the last neighbor ID filled in the previous LSP segment plus 1.
[0037] D: When the t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com