Quantum secret key distribution privacy amplification method supporting large-scale dynamic changes
A quantum key distribution and security enhancement technology, applied to key distribution, can solve the problems of time-consuming, reduce the processing performance of the security enhancement method, and the security enhancement method cannot meet real-time high-speed processing, etc., to achieve strong flexibility and high processing performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described in detail below with reference to the drawings and specific embodiments of the specification.
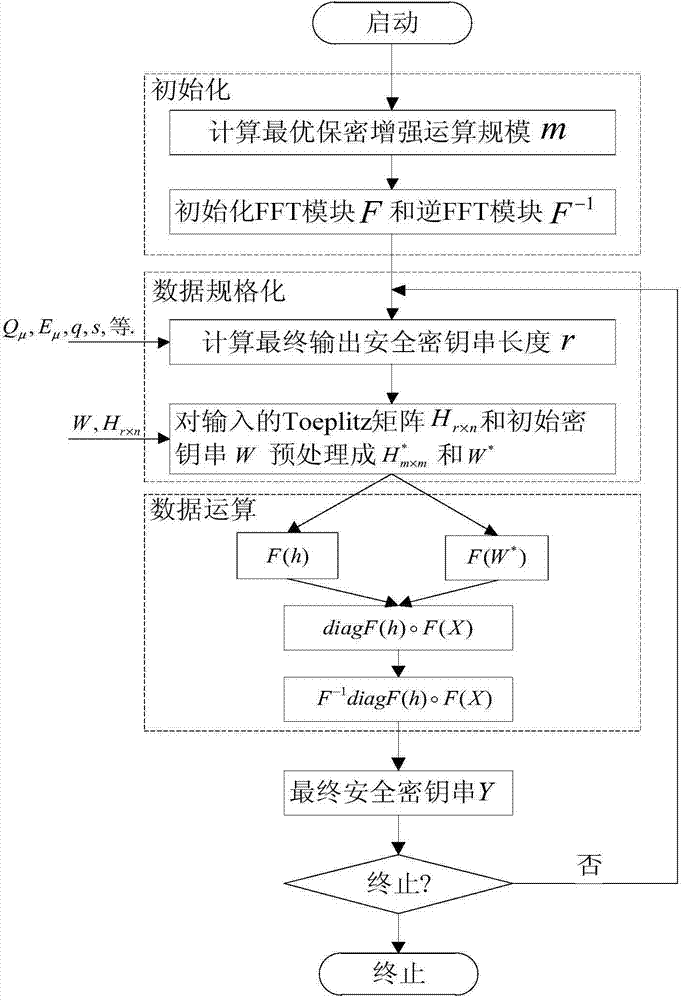
[0036] Such as figure 1 As shown, the steps of the method of the present invention for supporting large-scale dynamic change of quantum key distribution confidentiality enhancement are:
[0037] S1: Initialization;
[0038] When the security enhancement method is started, calculate the optimal operation scale m of the FFT module according to the actual operating parameters of the quantum key distribution system; initialize the FFT operation and inverse FFT operation modules with the scale m;
[0039] S2: Data normalization;
[0040] According to the detector count rate Q of the quantum key distribution system μ , Qubit error rate E μ , After the error correction, the weak security key length n and the quantum key distribution system security parameter s are calculated to calculate the final security key length r, and the initial key str...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com