Security defense method, device and system based on NLS (negative logic system)
A security defense and negative logic technology, applied in the field of network information security, can solve the problems of high network defense overhead and low network security factor, and achieve the effect of increasing network overhead and cost, reducing cost, and saving resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
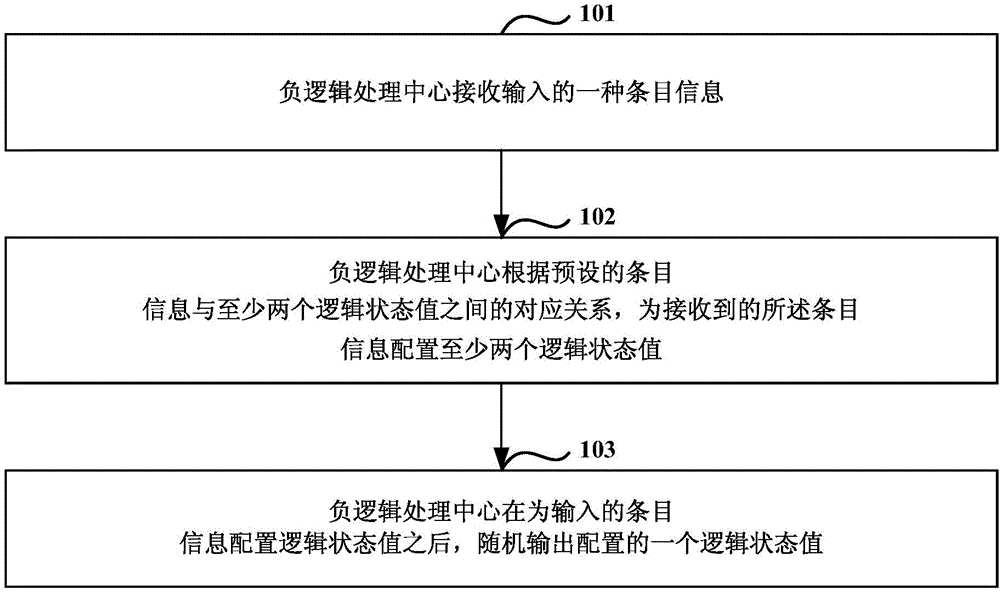
[0035] Such as figure 1 As shown, it is a flow chart of a security defense method based on the NLS negative logic system provided by Embodiment 1 of the present invention, and the method includes:
[0036] Step 101: The negative logic processing center receives an input item information.
[0037] In step 101, the negative logic processing center receives an input item information through the communication interface, wherein the expression form of the item information includes at least one of the following: data information expressed in binary, data information expressed in decimal, hexadecimal Data information, text information, etc. represented by the system.
[0038] For example: the entry information received by the negative logic processing center is 01010101, and it is determined that the entry information is data information in binary representation; the entry information received by the negative logic processing center is 0123456789, and it is determined that the entry...
Embodiment 2
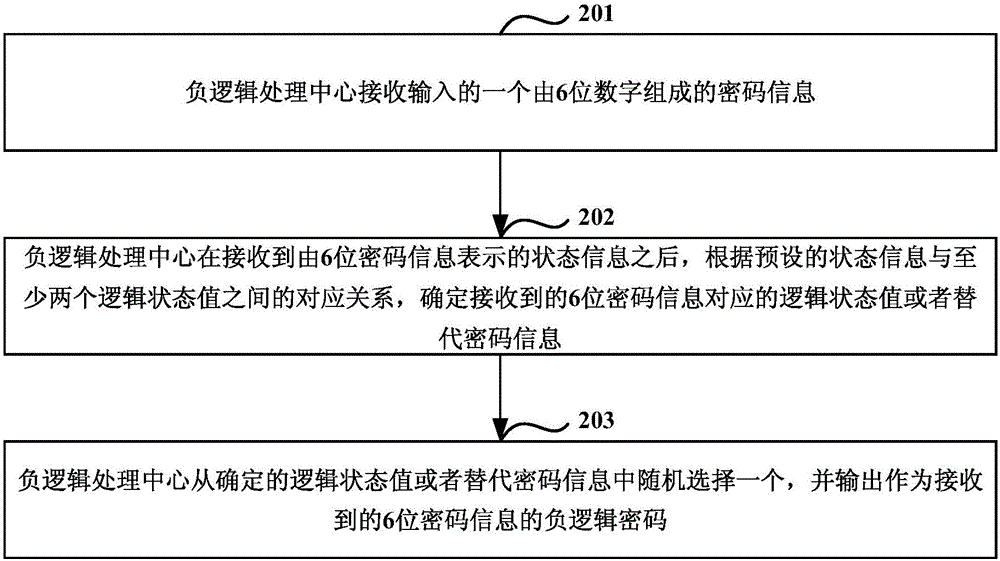
[0063] Such as figure 2 As shown, it is a flowchart of a security defense method based on the NLS negative logic system provided by Embodiment 2 of the present invention. Embodiment 2 of the present invention is a detailed description of each step in Embodiment 1 of the present invention. Embodiment 2 of the present invention is described by taking the input entry information as password information of 6 digits as an example. The methods include:
[0064] Step 201: The negative logic processing center receives an input password information consisting of 6 digits.
[0065] Wherein, the password information may be 6 digits or multiple digits, which is not specifically limited here.
[0066] In step 201, since the user needs to encrypt and save an office document, a 6-digit password information is set for the office document, for example: 123456, and the set 6-digit password information is transmitted to the negative logic process through the communication interface Center, ...
Embodiment 3
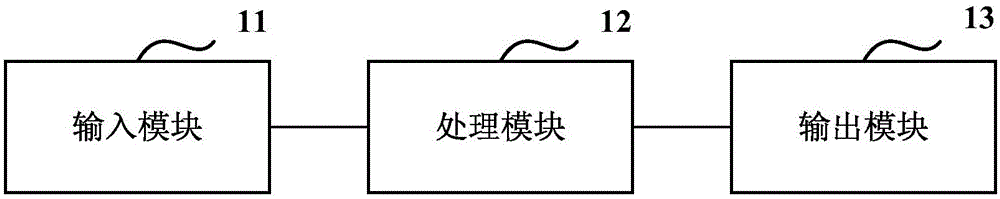
[0079] Such as image 3 As shown, it is a schematic structural diagram of a security defense device based on the NLS negative logic system provided by Embodiment 3 of the present invention. Embodiment 3 of the present invention is an invention under the same inventive concept as Embodiment 1 and Embodiment 2 of the present invention. Including: an input module 11, a processing module 12 and an output module 13, wherein:
[0080] An input module 11, configured to receive an input entry information;
[0081] The processing module 12 is configured to configure at least two logic state values for the received entry information according to the preset correspondence between the entry information and at least two logic state values, wherein the configured at least two logic state values The value does not include the logical state value corresponding to the state information determined by the positive logic mechanism;
[0082] The output module 13 is configured to randomly outp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com