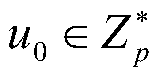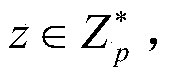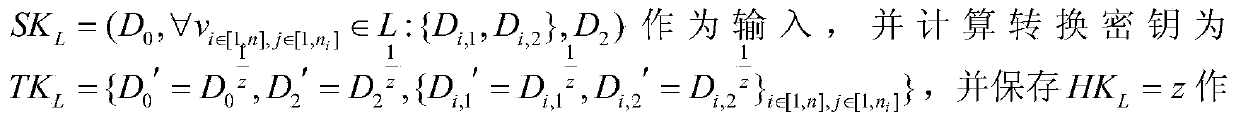Attribute-based encryption method and attribute-based encryption system capable of protecting privacy and supporting user Undo
A privacy protection and attribute encryption technology, applied in the field of information security, which can solve the problems of cloud cloud malicious attacks, uneconomical battery consumption and communication costs, and inability to verify the correctness of converted ciphertexts.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0085] The present invention will be further explained below in conjunction with the accompanying drawings and specific embodiments.
[0086] The specific process of the present invention will be described below in conjunction with the accompanying drawings.
[0087] Such as figure 1 As shown, a kind of ABE system provided by the present invention comprises following eight modules:
[0088] 1. System parameter setting module (Setup): input security parameter κ, return system public parameter params and master key MK.
[0089] 2. Key generation module (KeyGen): The authorization center runs a key generation algorithm to generate a private key for the user. The authorization center inputs the system public parameters params, a descriptive attribute set L, and calculates the private key SK associated with the user and the attribute set L L .
[0090] 3. Encryption module (Encrypt): Input the system public parameters params, message m, access policy W, and the encryptor encryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com