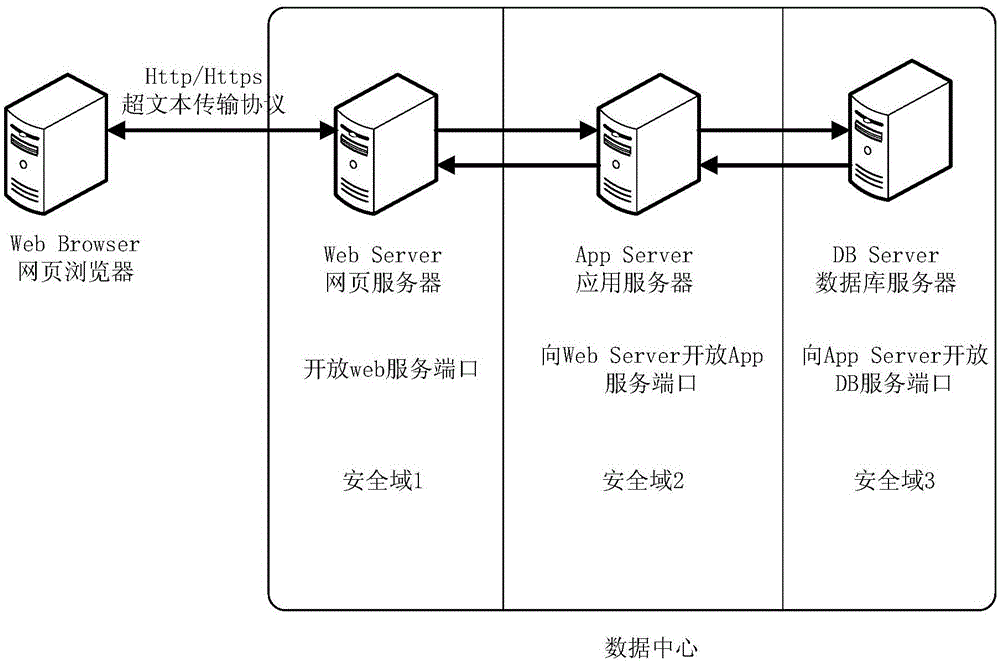
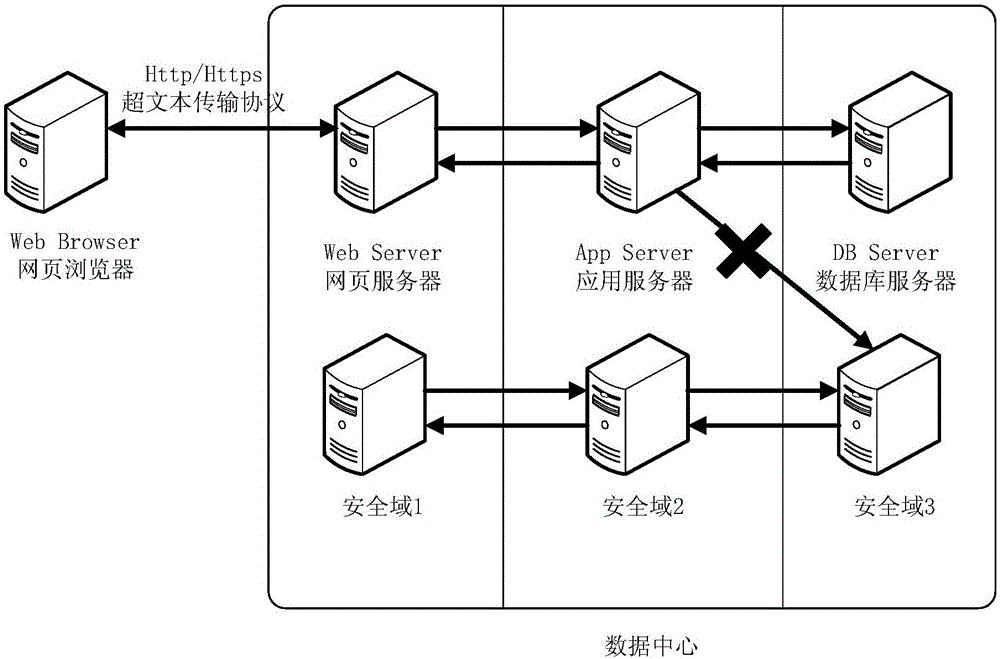
Method and device for deploying security access control policy
A security access control and policy technology, applied in the field of network security, can solve problems such as heavy configuration work, time-consuming, human configuration errors, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
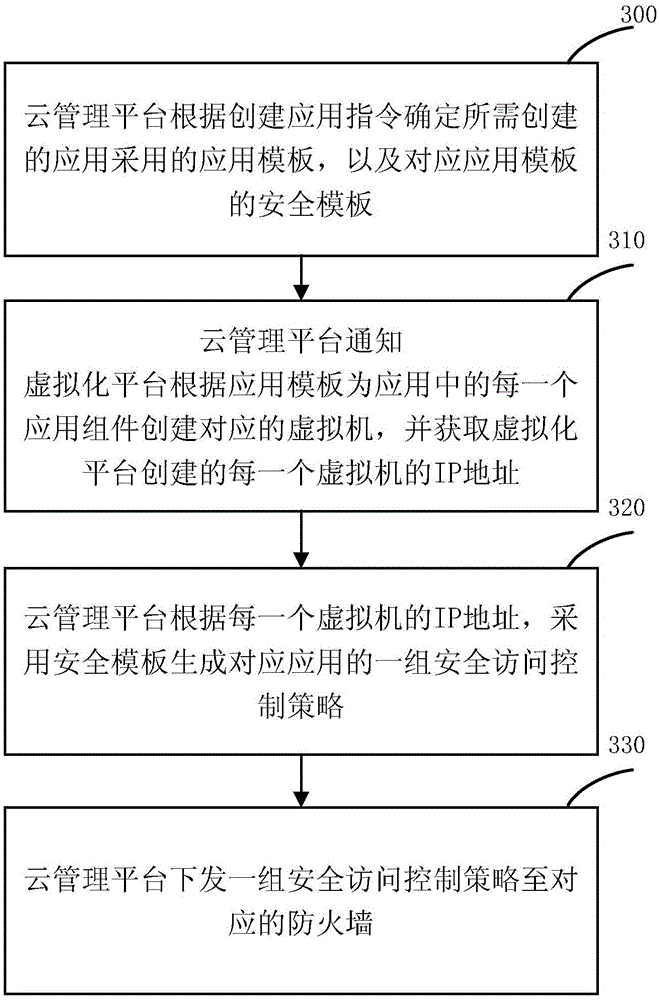
[0148] refer to Figure 5 As shown, it is a specific flow chart of deploying security access control policies:
[0149] Step 501: The user determines the application template and the corresponding security template required for creating the application, generates an application creation instruction according to the confirmation result, and sends the application creation instruction to the cloud management platform through the client.
[0150] Step 502: The cloud management platform calls the virtualization platform interface according to the application creation instruction and the determined application template, creates a virtual machine VM in the application, and sets an IP address for each created VM, or uses DHCP for each created virtual machine. The machine is assigned an IP address.
[0151] Step 503: the virtualization platform sends a confirmation instruction to the cloud management platform, indicating that the VM is created successfully, and returns the IP address ...
Embodiment 2
[0157] refer to Figure 6 As shown, when the application is migrated, the cloud management platform resets the security access control policy for the migrated application.
[0158] Step 601: The user selects the application to be migrated, selects the destination network and destination firewall to which the application needs to be migrated, and generates an application migration command according to the selection result, and the user sends the application migration command to the cloud management platform through the client.
[0159] Wherein, the destination network generally refers to another network segment, and after the network segment changes, it may be in another firewall.
[0160] Step 602: The cloud management platform invokes the virtualization platform interface, uses the application template to create a corresponding new virtual machine for each application component in the application, obtains the IP address of each new virtual machine, and converts each applicati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com