Security attack alarm positioning system based on Spark big data platform of Tachyou
A big data platform and security attack technology, which is applied in the field of security attack alarm positioning system based on Tachyou Spark big data platform, can solve the problems of unclear security responsibilities, low processing efficiency, untimely fault diagnosis, etc., and achieve easy expansion and The effect of reducing and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] Below is further detailed description of the present invention according to accompanying drawing and example:
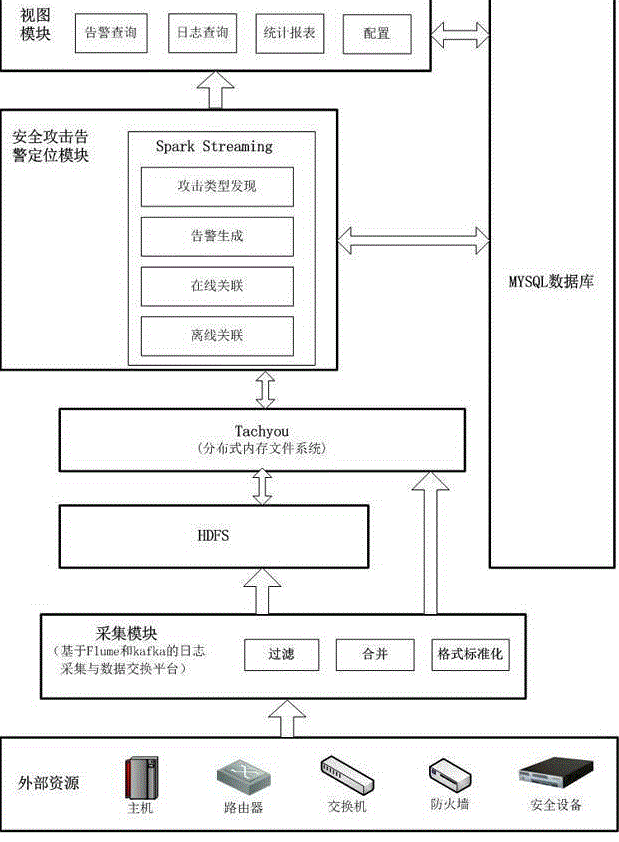
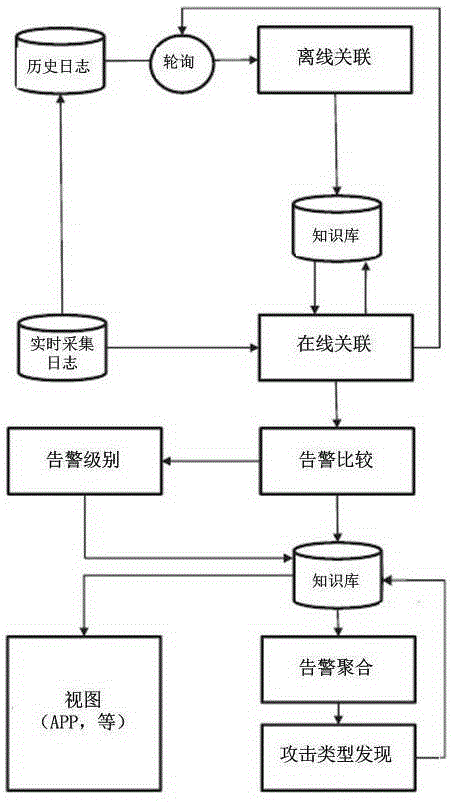
[0057] A security attack alarm positioning system based on Tachyou's Spark big data platform of the present invention collects logs of various devices in the enterprise environment by integrating flume into the kafka distributed data exchange system, and preprocesses and transmits them to the positioning module in real time . The positioning module provides real-time analysis of the knowledge base, pushes the analysis results to the foreground, and provides alarm information traceability and proof functions. Its structure is as follows figure 1 Shown: (1) The acquisition module is composed of the kafka distributed data exchange system. (2) Security attack alarm location module, which is composed of SparkStreaming; (3) View module, which provides alarm information and analysis, log information and analysis query.
[0058] The collection module is the premise...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com