Improved method for quickly generating big prime number
A technology of large prime numbers and prime numbers, applied in the field of improved rapid generation of large prime numbers, can solve problems such as increasing the length of RSA keys, and achieve the effect of reducing the number of modular exponentiation operations, increasing the length, and ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The invention will be described in further detail below in conjunction with the accompanying drawings.
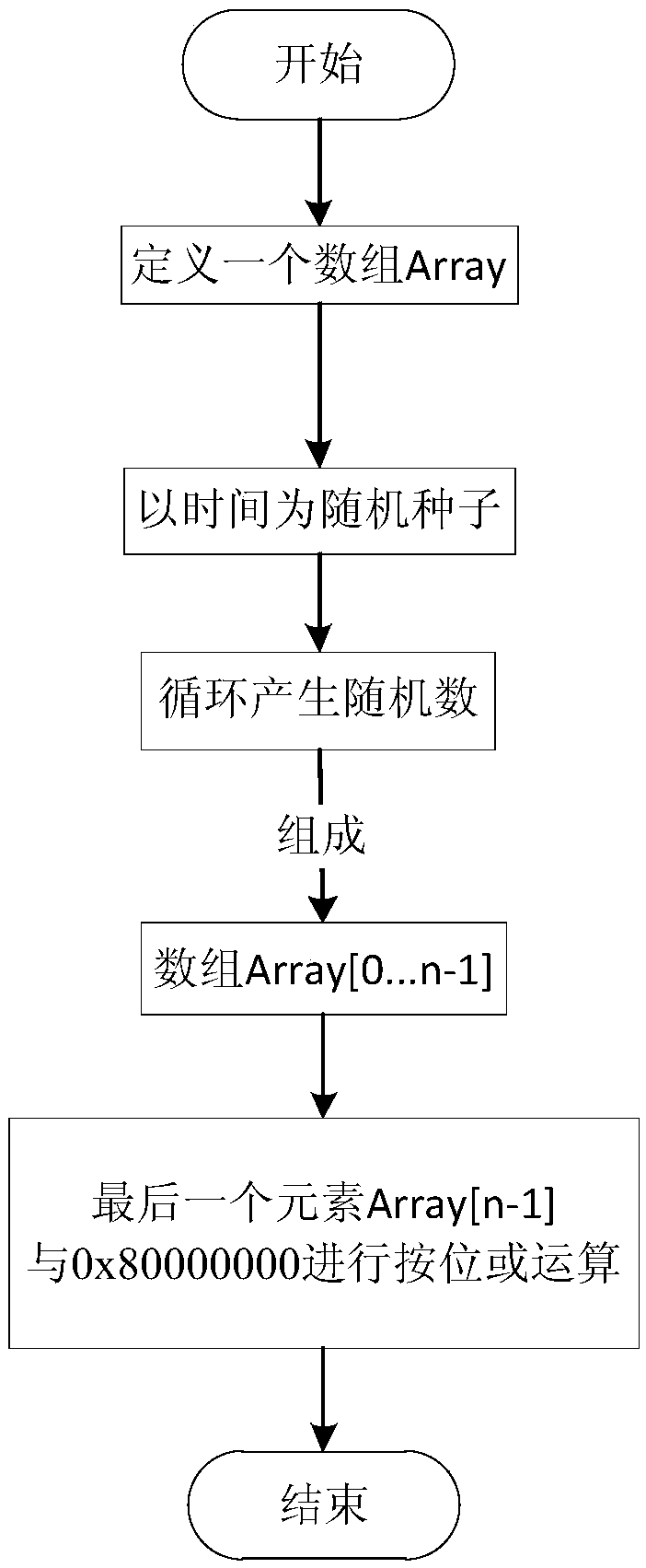
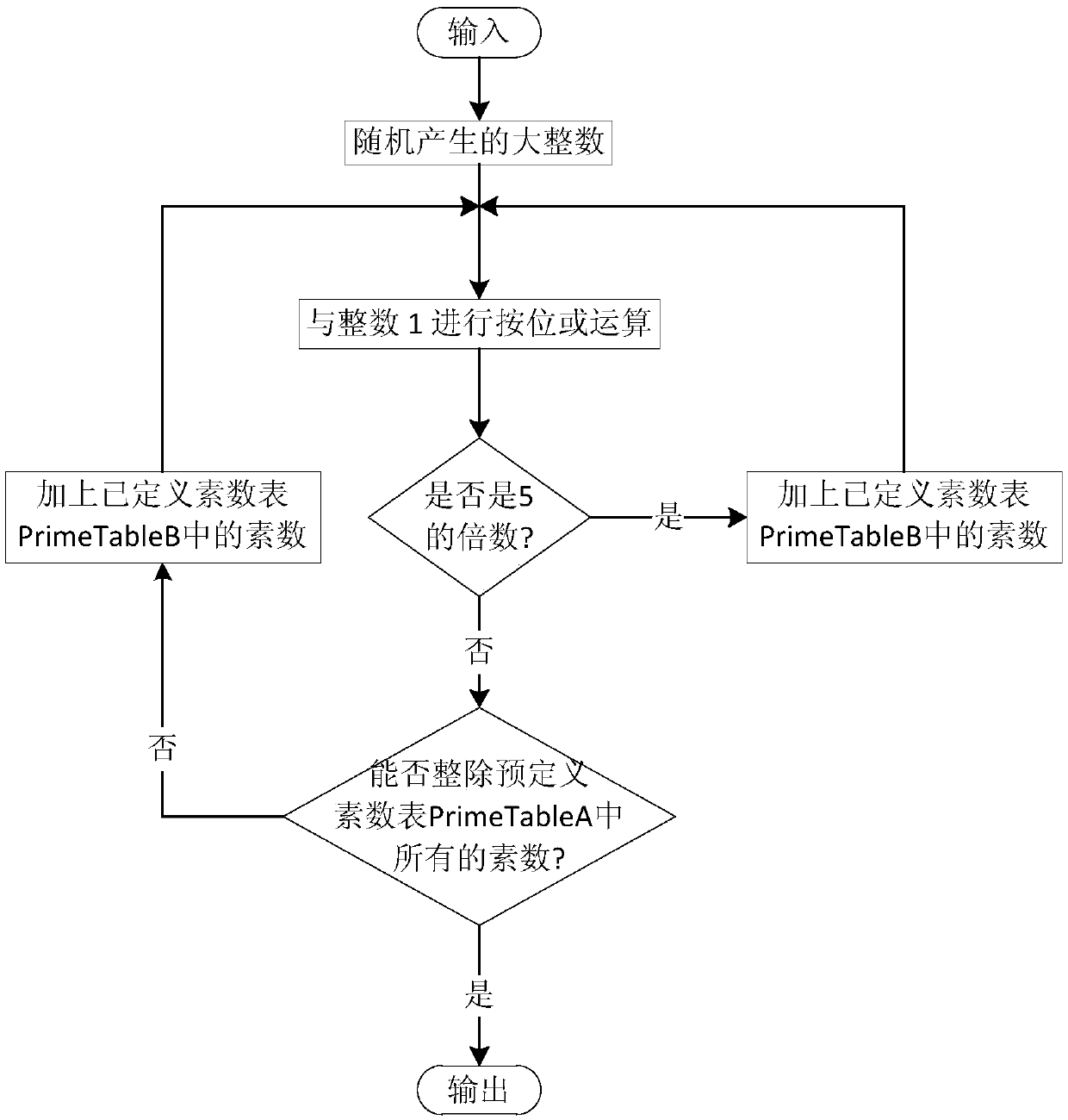
[0036] like figure 1 As shown, at the beginning of the present invention, corresponding large integers will be generated according to the specified number of digits (i.e., taking 1024 bits as an example), and PrimeTableB[N] is similar to PrimeTableA[M], both of which are one-dimensional arrays, except that the number of dimensions N is greater than that of M large, as shown in Table 1.
[0037] Table 1
[0038] PrimeTableA[M]=
[0039] 3 7 11 13 17 19 23 29 31 37 41 43 47 53 59 61 67 71 73 79 83 89 97 101 103 107 109 113 127 131 137 139 149 151 157 163 167 173 179 181 191 193 197 199 211 223 227 229 233 239 241 251
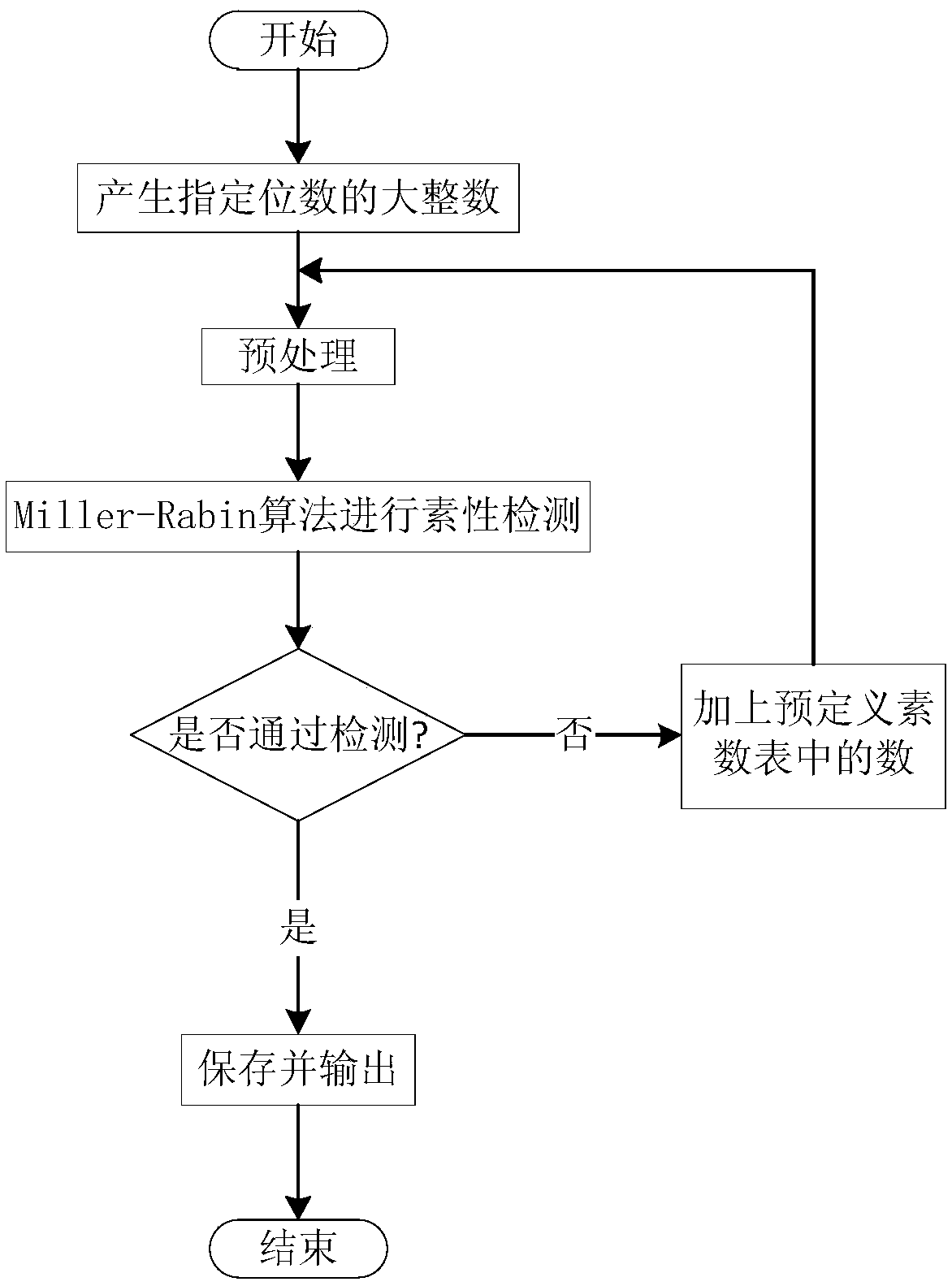
[0040] Concrete flow process of the present invention is as figure 2 shown, including:
[0041] (1) First of all, it is necessary to define an array Array of unsignedlong type...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com