User identity verification method, server and client
A technology of user identity and verification method, which is applied in the fields of user identity verification method, server and client, can solve problems such as malicious cracking, answers easily cracked by hackers, and high risk of account theft, so as to ensure security and reduce vulnerability The possibility of being leaked and cracked, the effect of improving resource utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
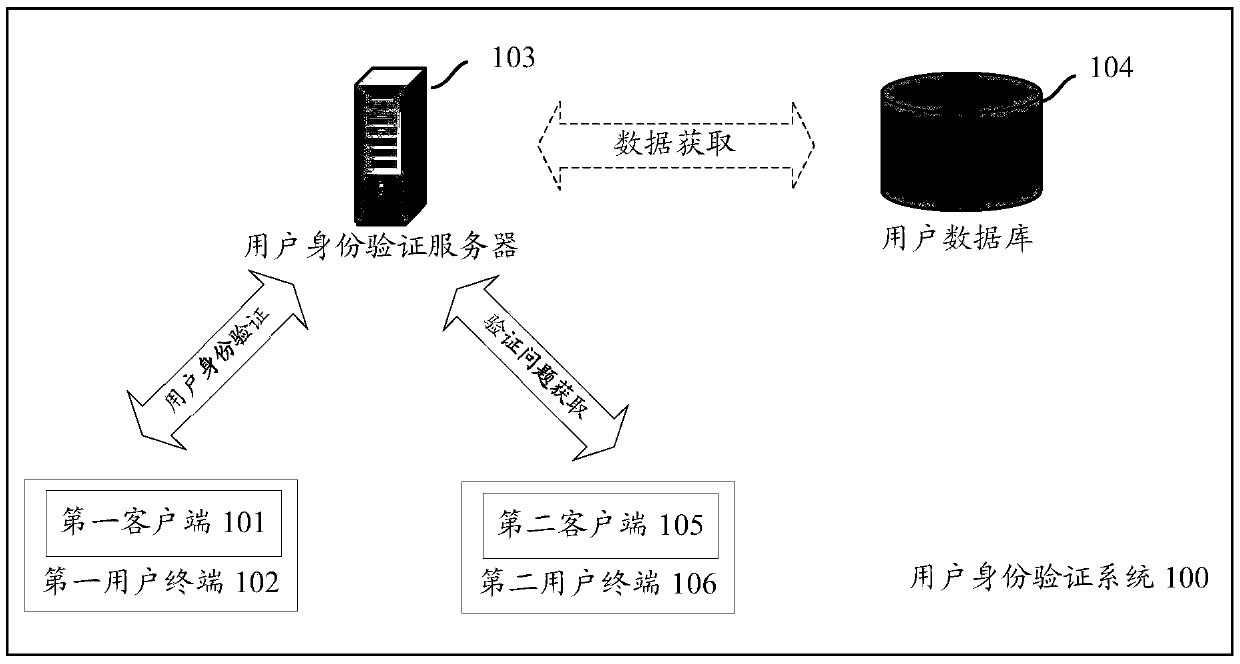
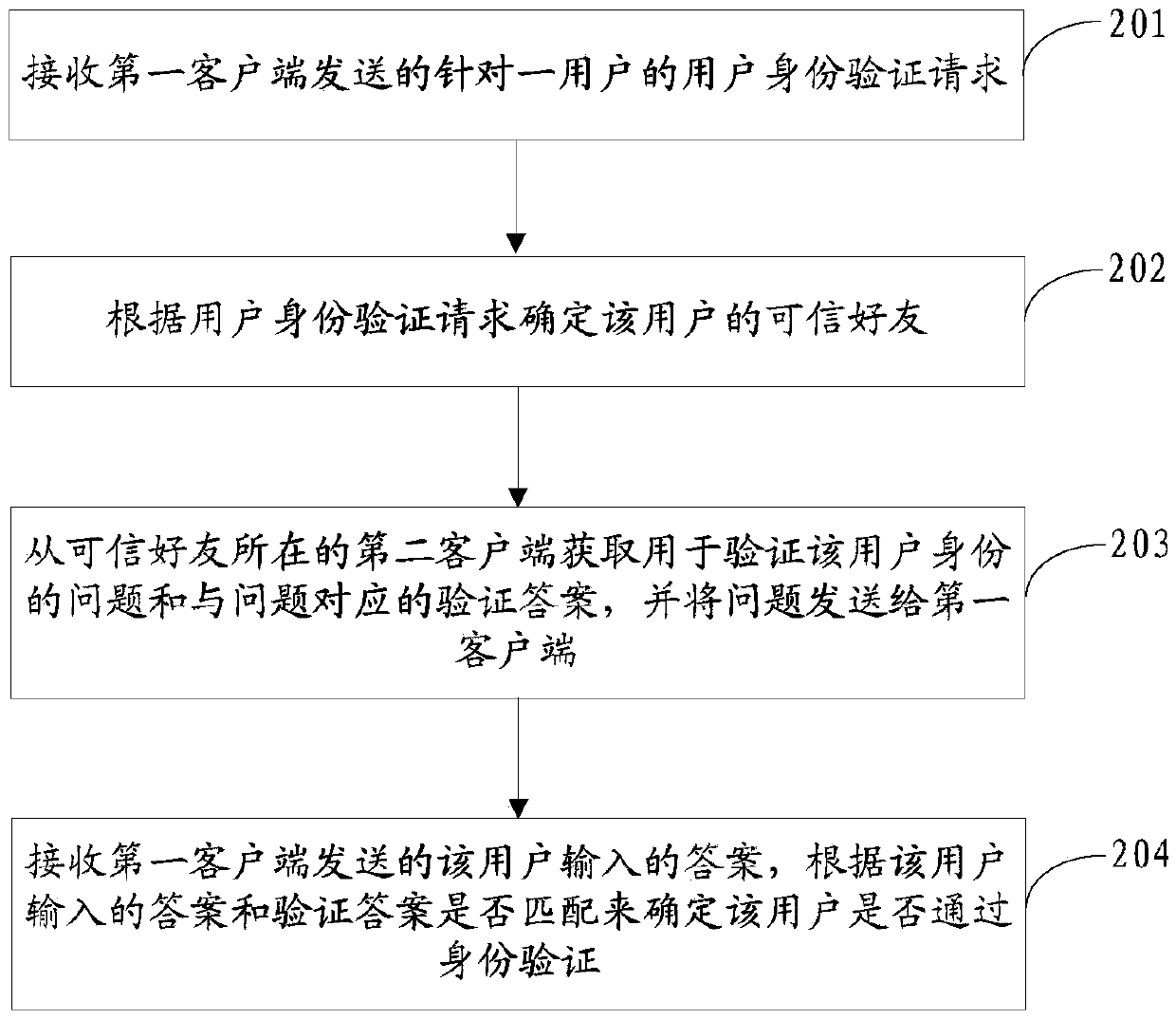
[0040] Embodiment 1: The social intimacy between the user and each friend is determined according to the social records of the user and each friend in the friend relationship chain, and friends whose social intimacy is greater than a preset threshold are determined as trusted friends.
[0041] Specifically, the server may request the social record of the friend from the user database, and then the server determines the social intimacy according to the social record requested from the user database. Or, in addition to saving the social records of each user and each friend in the friend relationship chain, the user database further determines and saves the social intimacy between the user and each friend. At this time, the server can directly request the user database to obtain The social intimacy between the user and each friend, and then the friends whose social intimacy is greater than the preset threshold are determined as trusted friends.
[0042] The social records may inc...
Embodiment approach 2
[0044] Embodiment 2: According to the account security records of each friend in the user's friendship chain within a predetermined period of time, determine the total number of times each friend's account is stolen and / or publish illegal information within the predetermined period of time, and the total A friend whose number of times is less than a preset threshold is determined as a trusted friend.
[0045] The server can request the account security record of each friend from the user database, and judge whether the account is in a safe state for a period of time through the records of each friend's account being stolen and / or publishing illegal information, and determine whether the account is in a safe state As a trusted friend, the predetermined time period can be half a year or one year, and the preset threshold can be the threshold of the number of times the account is stolen and / or illegal information is published, for example, the preset threshold is 1 time within hal...
Embodiment approach 3
[0046] Embodiment 3: Determine the social intimacy between the user and each friend according to the social records of the user and each friend in the friend relationship chain, if the social intimacy is greater than the preset threshold and the account is stolen within a predetermined period of time and / or A friend whose total number of times of posting illegal information is less than a preset threshold is determined as a trusted friend.
[0047] Step 203: Obtain from the second client where the trusted friend is located a question for verifying the user's identity and a verification answer corresponding to the question, and send the question to the first client.
[0048] After receiving the user identity verification request, the server sends a verification question acquisition request to the second client, receives the question and verification answer returned by the second client, and uses them as the question to be sent to the first client and the verification used for ve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com