Information security event automatic association and rapid response method and system based on big data analysis
An information security and automatic correlation technology, applied in the field of information security technology and big data, can solve problems such as difficulty in meeting the needs of large data volume correlation analysis, inversion, correlation analysis engine misreporting or omission, etc., to shorten the alarm response time, Eliminate false positives, improve accuracy and confidence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
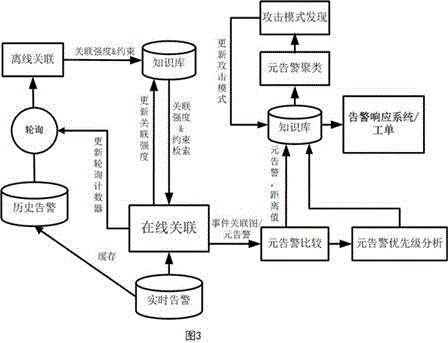
[0044] Below is further detailed description of the present invention according to accompanying drawing and example:
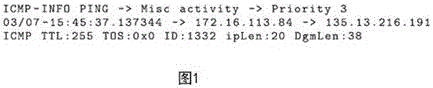
[0045] figure 1 It is the alarm log format of the IDS security equipment produced by a certain company. Line 1 indicates the alarm type, alarm category and alarm priority. Line 2 indicates the time when the intrusion occurred, the IP address and port number of the sender and receiver, as well as TTL, network protocol, service type and length.
[0046] figure 1 The log uses 6 attributes, so that each alarm is represented as a 6-dimensional array ( , , , , , ). The attributes of the 6-dimensional array are alarm occurrence time, source IP, source port, destination IP, destination port and alarm type. These attribute values are either text, IP addresses, times, or numbers. An alarm type is The alarm is actually when The value is An example of an alarm at time.
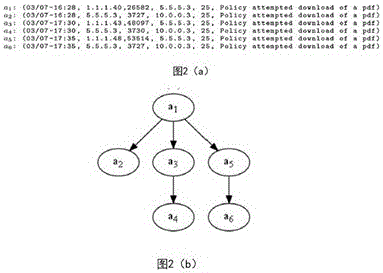
[0047] Generally, meta-alerts are used to describe related alarms. A meta-ala...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com