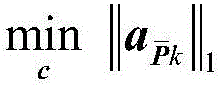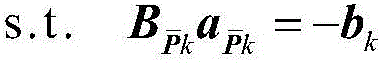Transmission network false data attack defense method based on protection measurement point
A false data attack and measurement point technology, applied in the field of power system information security, can solve the problems of detection strategy attack, long cycle, and high development risk, achieve the effect of defending against false data attacks and enhancing the ability to defend against false data attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below with reference to specific embodiments and accompanying drawings.
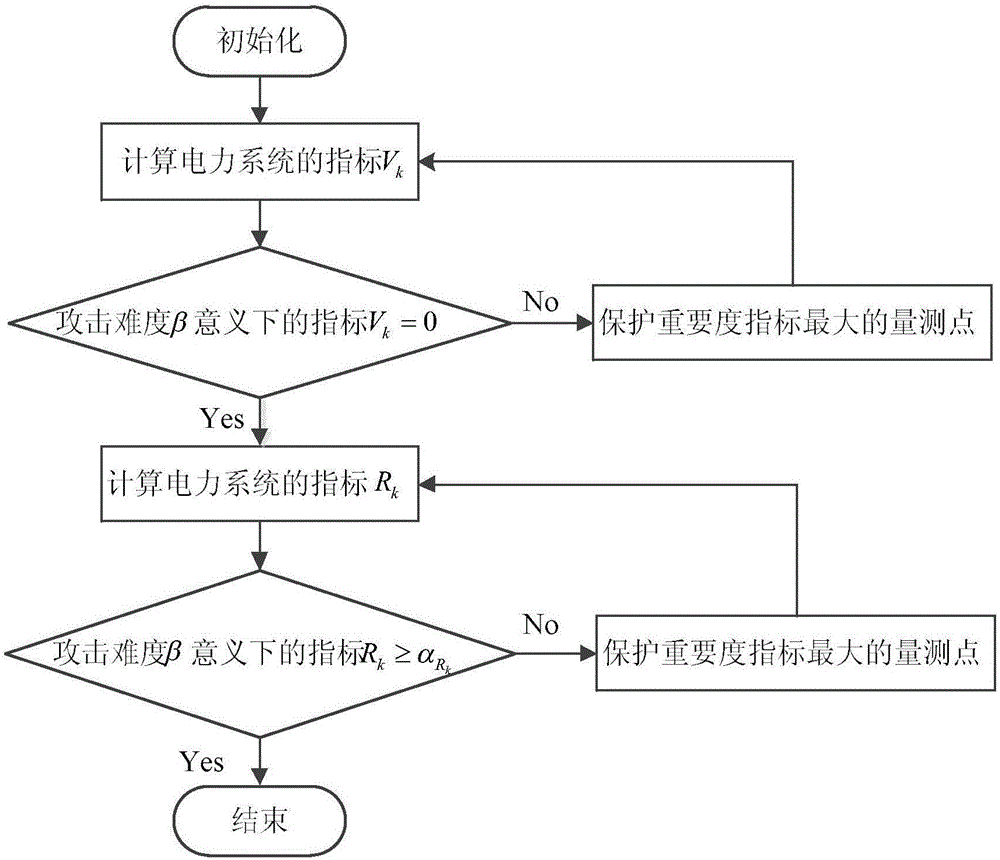
[0030] figure 1 is based on the indicator V k and the indicator R k The flow chart of the fake data attack defense method, the specific implementation steps are as follows:
[0031] Step 1: Attack all the measurement points in the power system in turn, obtain the attack vectors corresponding to all the measurement points according to the fake data attack vector optimization model, and calculate the index V of the power system k , if the index V in the sense of attack difficulty β k =0, go to step 3, otherwise go to step 2.
[0032] In a power system with N buses, the state variable is generally taken as the complex voltage of each bus, including the voltage amplitude and phase angle. Except for the reference node, there are a total of 2N-1 state variables, and the state variables are uniformly expressed as x =[x 1 ,x 2 ,…,x n ] T, n=2N-1. F...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com