A multi-stage filtering source code data detection method and device
A source code, level filtering technology, applied in the field of multi-level filtering source code data detection, can solve the problems of complex code labeling words, inappropriate detection, non-standard identifier naming, etc., to enhance the ability of security management and control, speed up Information processing speed, avoiding the effect of excessive calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
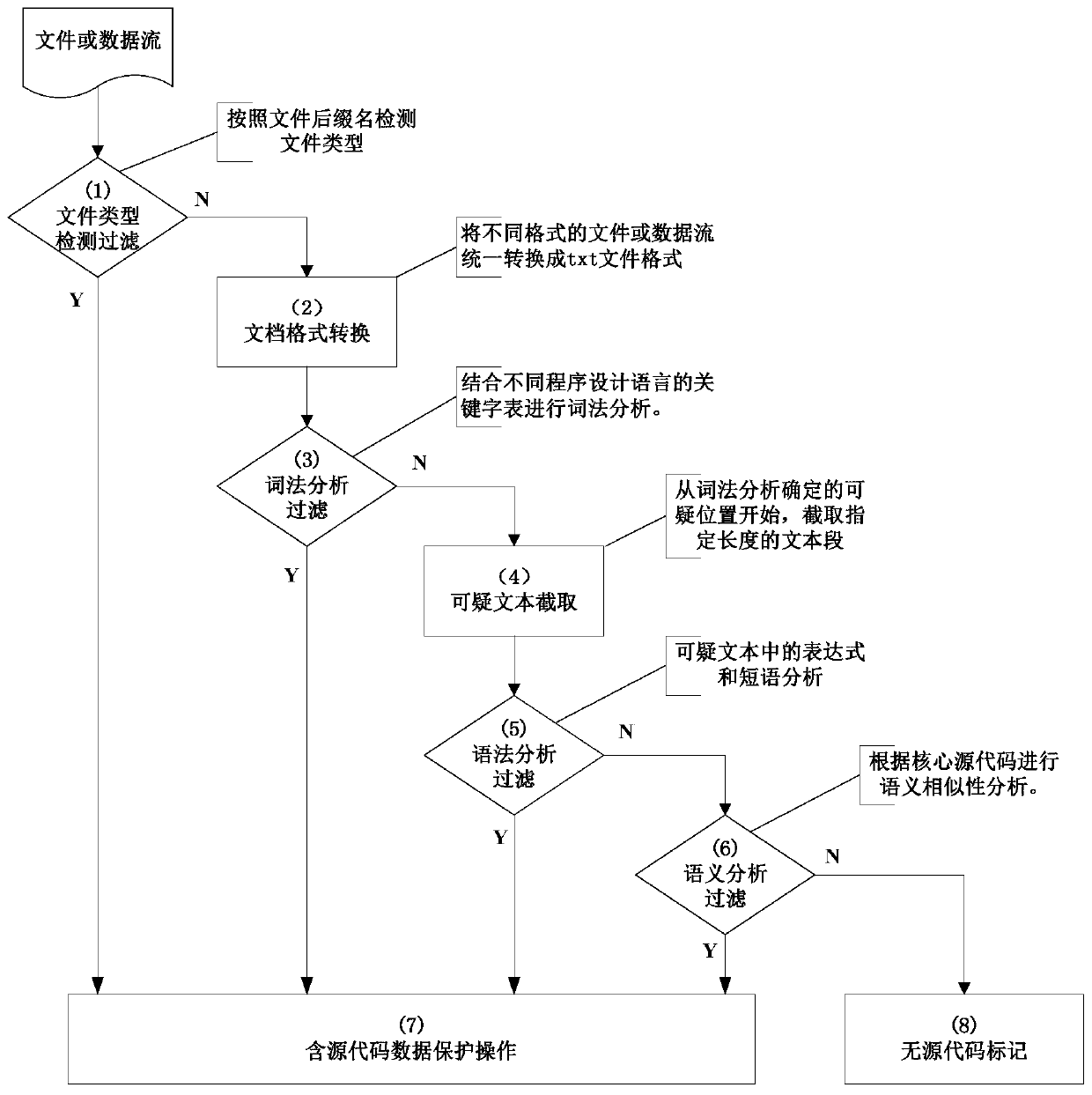
[0079] The developer downloads a CPP source code file from the enterprise code server to his own client computer, and the data security software on the client side scans the newly added file.
[0080] When the file type detection and filtering module of the source code data detection device finds that the file suffix is ".cpp", the file is determined as a source code file. Based on this determination, the data security software only allows this file to be saved to the client computer's secure area.
specific Embodiment 2
[0082] When a developer was writing a user manual, he pasted multiple source code programs into a text document and saved it in pdf format. The data security software installed by the enterprise conducts a full disk scan, and the file is input into the device for detection.
[0083] After being detected by the file type detection and filtering module of the source code data detection device, the file is not a source code file, but belongs to a text file format, so it is converted into a document format and processed subsequently. After performing lexical analysis on the converted txt file, it is found that the sum of the weighted scores of the lexical tokens contained in it exceeds the discrimination threshold, so it is determined to contain source code data. After obtaining the test result, the enterprise should limit the scope of dissemination of this file.
specific Embodiment 3
[0085] A person who is about to resign wants to take some core source codes of the enterprise out, so he modified the suffixes and keywords in these source code files in batches. When transferring these files to the USB flash drive, the data security software will Input them into the device one by one for detection.
[0086] After being detected by the file type detection and filtering module of the source code data detection device, the file is not a source code file, but belongs to a text file format, so it is converted into a document format and processed subsequently. After performing lexical analysis on the converted txt file, it is found that the sum of the weighted scores of the lexical tokens contained therein does not exceed the discrimination threshold, so it is turned to grammatical analysis. In the syntax analysis stage, it is found that the file contains multiple expressions, so it is judged that the file contains source code data. After the data security softwar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com