Method for detecting capability of RIPEMD-160 algorithm in defending differential fault attacks
A RIPEMD-160, differential fault attack technology, which is applied in the countermeasures of attacking encryption mechanisms, digital transmission systems, electrical components, etc., can solve problems such as hidden dangers of cryptographic equipment security, and achieve the effect of easy implementation and simple and accurate method.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
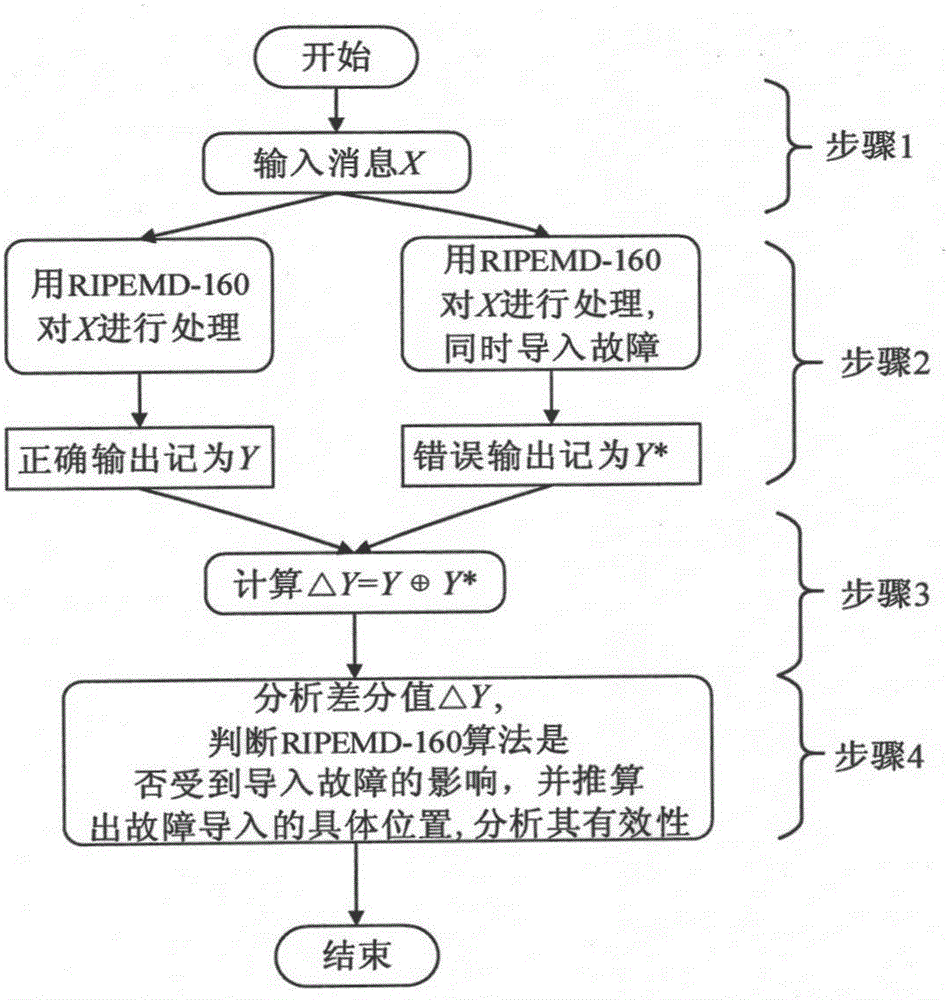
[0040] In order to make the present invention more clear, the preferred embodiments are listed, and the detailed illustrations are as follows.
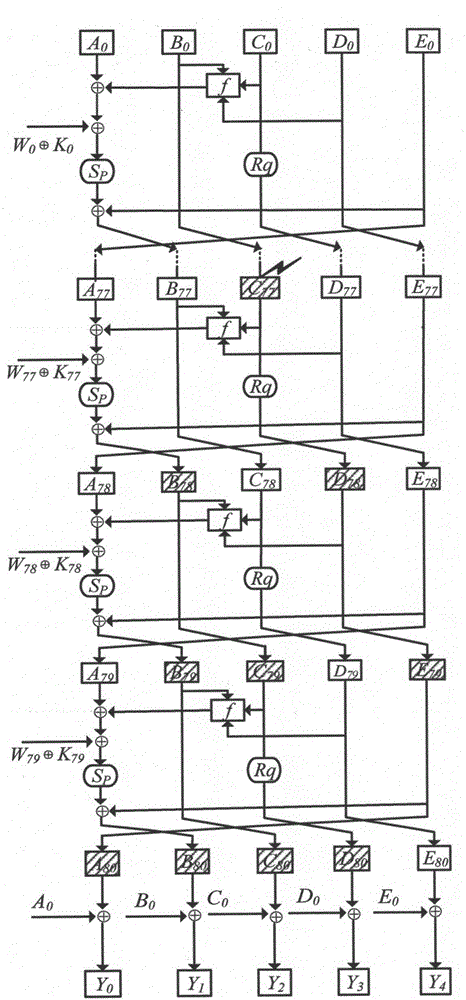
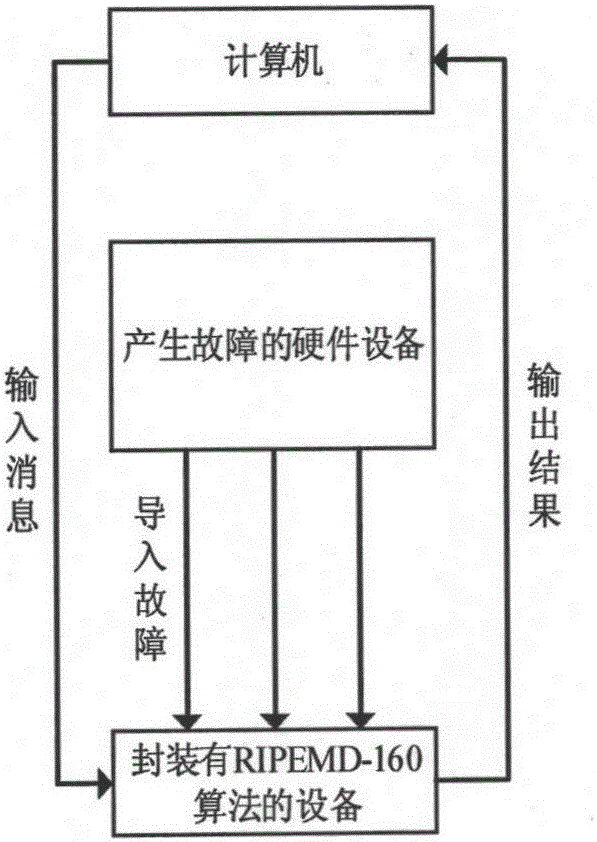
[0041] When using the RIPEMD-160 algorithm to process the same plaintext message X with the same key, if the experimental environment (such as clock, voltage, humidity, radiation, pressure, light and eddy current, etc.) is different, the attacker can obtain the correct output respectively Y and the error output Y*, by calculating the output difference value of these two values, that is Indicates the XOR operation, and the key information can be deduced. Attackers can induce faults to occur while the processing device is running the RIPEMD-160 algorithm, but they do not know the specific location of the fault and the specific error value. Under some specific conditions, the position of fault introduction can be deduced from the difference ΔY, and the fault introduced at this time is called an effective fault. On the contrary, when ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com