User identification card and its remote destruction method, system and equipment
A user identification and remote technology, applied in the field of communication, can solve problems such as legal user property loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
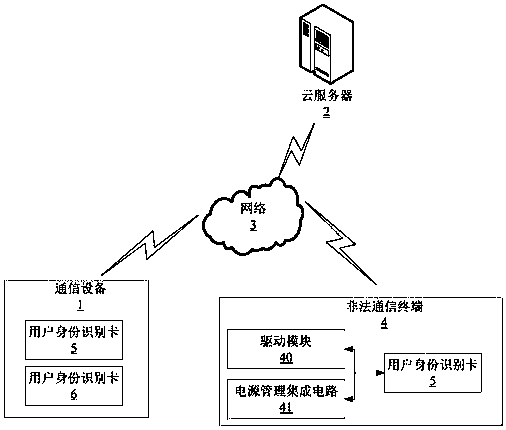
[0095] refer to figure 1 As shown, it is a schematic diagram of an application environment of a preferred embodiment of the method for remotely destroying a user identification card in the present invention.
[0096] The method for remotely destroying a user identification card can be executed by a communication device 1 and a user identification card 5 . In a preferred embodiment of the present invention, the communication device 1 may be a mobile phone, which is installed with the user identification card 5 .
[0097] The subscriber identification card 5 includes, but is not limited to, a customer identification module (Subscriber Identification Module, SIM) card, Micro SIM, Nano SIM, user identification module (User Identify Module, UIM) card, Micro UIM, Nano UIM card, etc.
[0098] In other preferred embodiments of the present invention, the communication device 1 may also be a dual-card mobile phone, and therefore, may also include a user identification card 6 .
[0099...
Embodiment 2
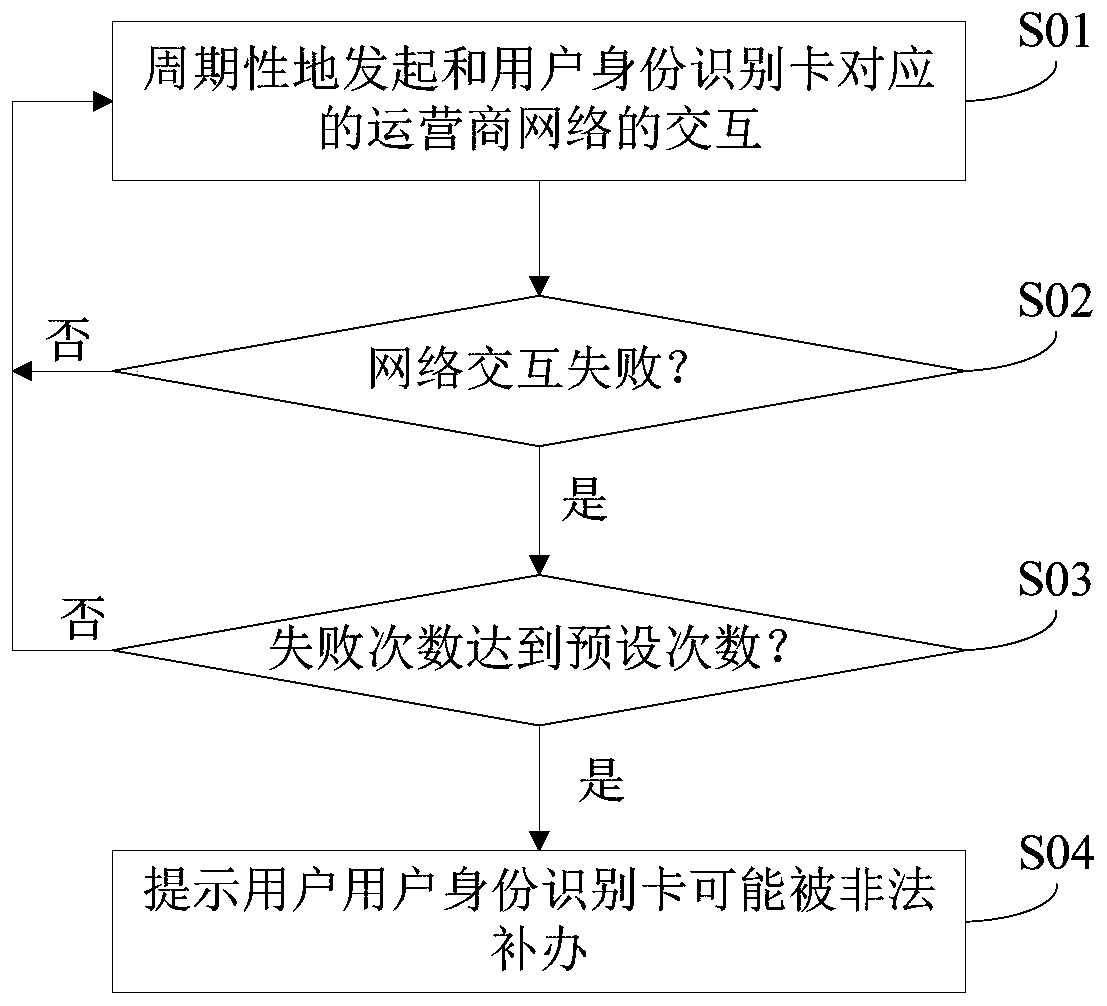
[0106] refer to figure 2 As shown, it is an implementation flowchart of a preferred embodiment of the detection of the user identification card in the method for remotely destroying the user identification card of the present invention. In a preferred embodiment of the present invention, the method for detecting a user identification card is executed by the communication device 1 .
[0107] According to different requirements, the execution sequence in the flow chart shown in this figure can be changed, and some can be omitted.
[0108] S01. The communication device 1 periodically initiates interaction with the operator network 7 corresponding to the user identity card 5 .
[0109] The interaction manner may include, but is not limited to, actively initiating a Tracking Area Update (Tracking Area Update, TAU), a Routing Area Update (Route Area Update, RAU), a Location Area Update (Location Area Update, LAU) and the like.
[0110] The period may include, for example, every 3...
Embodiment 3
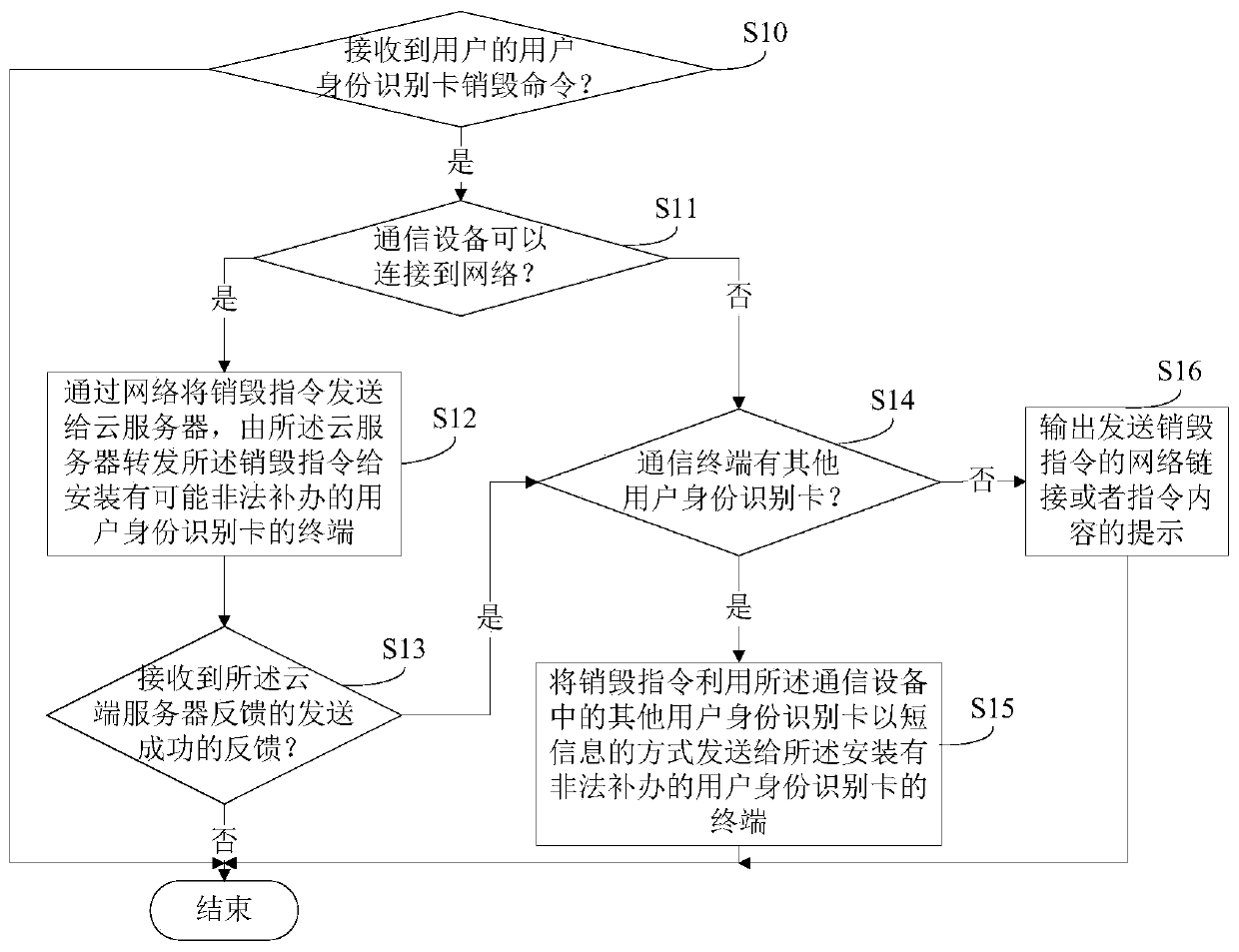
[0119] refer to image 3 As shown, it is an implementation flow chart of a preferred embodiment of the remote transmission of the destruction instruction of the user identification card in the method for remotely destroying the user identification card of the present invention. In a preferred embodiment of the present invention, the method for remotely sending the user identity card destruction instruction is executed by the communication device 1 .
[0120] According to different requirements, the execution sequence in the flow chart shown in this figure can be changed, and some can be omitted.
[0121] S10, the communication device 1 judges whether a user ID card destruction command of the user is received.
[0122] In a preferred embodiment of the present invention, the communication device may provide a function option to send the user identity card destruction command. For example, the command to destroy the user identification card can be integrated in the “Settings” m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com