Privacy protection method based on content center
A content-centric network and privacy protection technology, which is applied in the field of privacy protection based on content-centric networks, can solve the problems of inability to protect sensitive information privacy, content publishers' privacy is easy to leak, and retrieval cannot be realized, so as to reduce key storage and calculation. burden, dynamically control the requester's access to resources, and improve the effect of cache utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
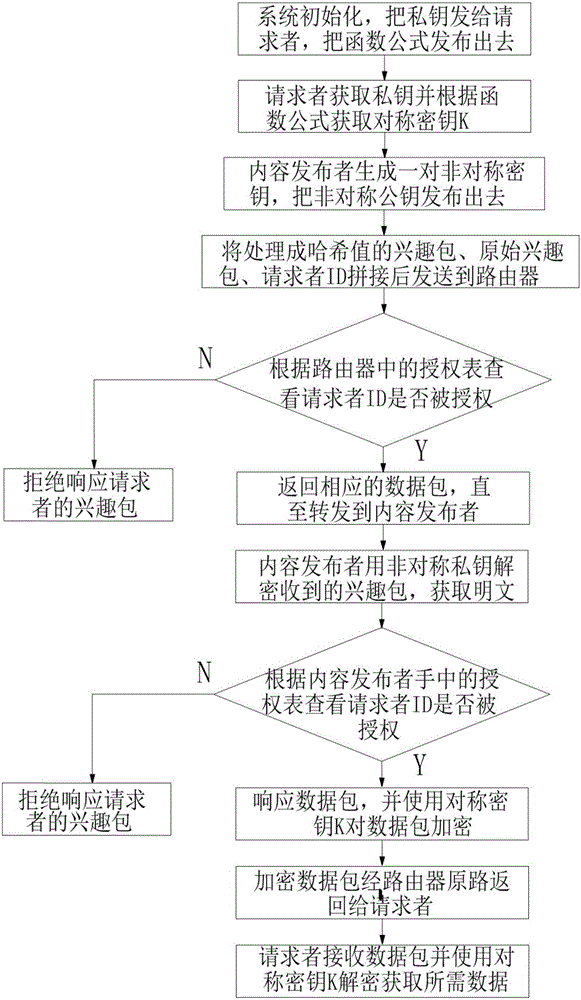
[0019] The present invention will be further described below in conjunction with specific embodiment:
[0020] See attached figure 1 As shown, a privacy protection method based on a content-centric network described in this embodiment includes the following steps:
[0021] (1) The broadcast system completes the initialization, generates a private key and securely transmits the private key to the requester, and releases the function formula that can calculate the symmetric key K;
[0022] (2) Each authorization requester obtains the symmetric key K according to the received private key and the function formula issued by the system;
[0023] (3) The content publisher generates a pair of asymmetric public key and private key (puk_p|pri_p), and publishes the asymmetric public key puk_p in the content-centric network at the same time;
[0024] (4) The requester processes the interest packet into H(I) through the hash value, and at the same time encrypts the original interest pack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com