Patents
Literature
33 results about "Commutative encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
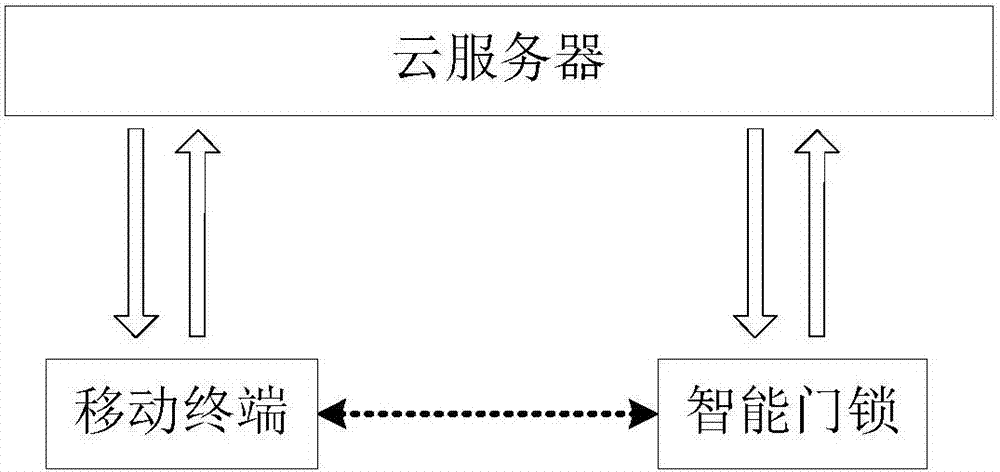
Secure communication method based on intelligent door lock system and intelligent door lock system
ActiveCN107038777AEnsure safetyIndividual entry/exit registersShort range communication serviceSecure communicationSecure communication channel
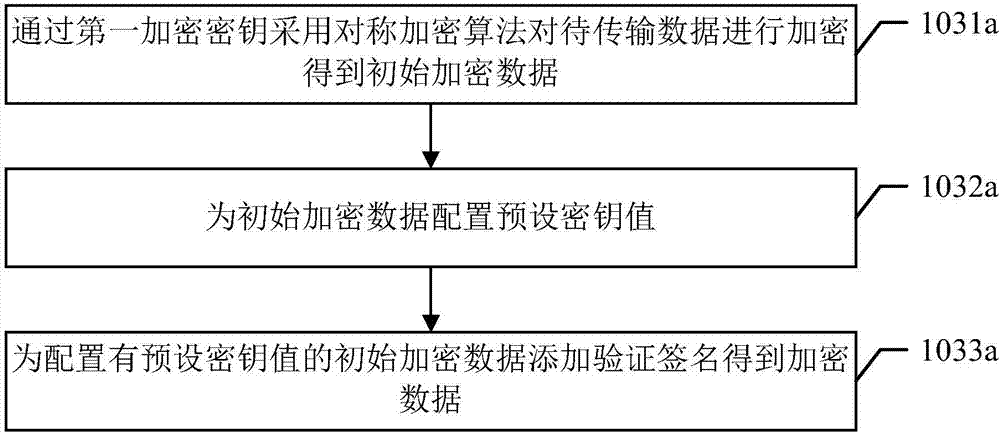
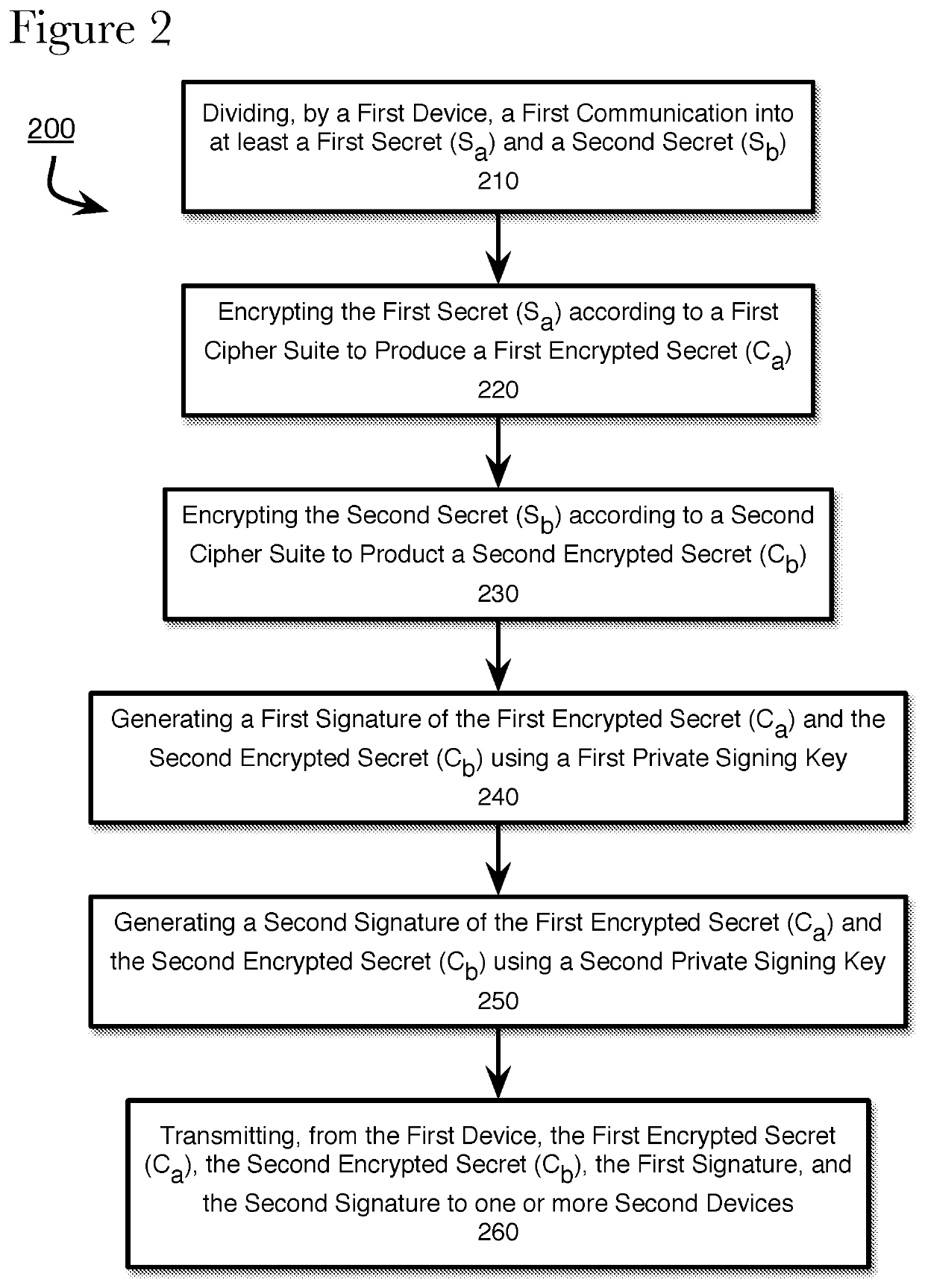
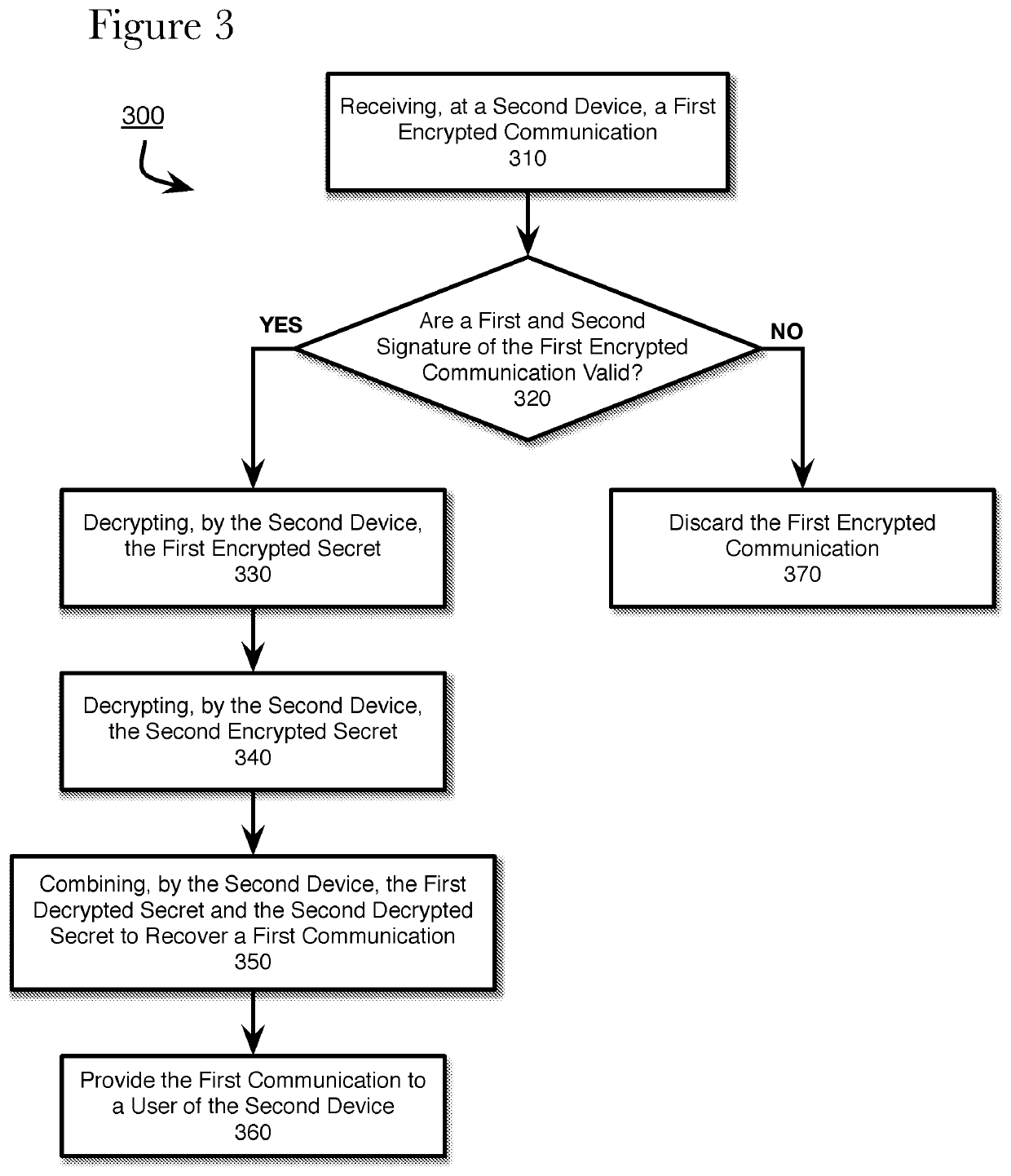
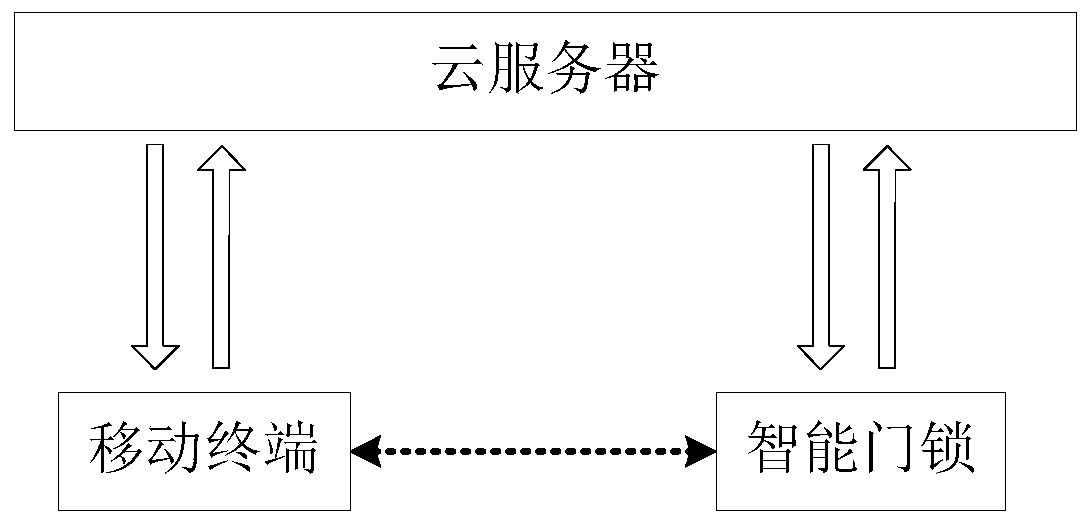
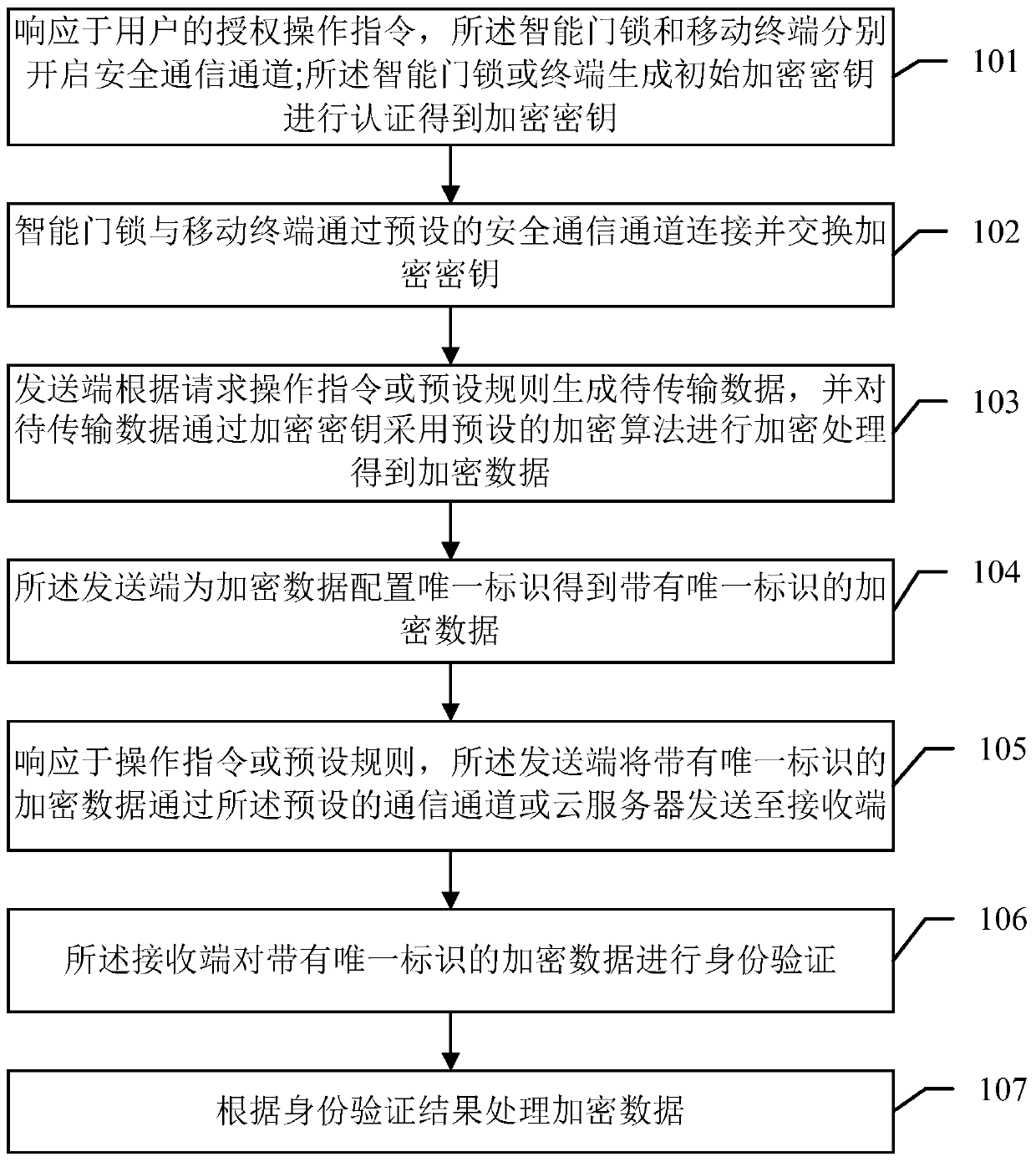
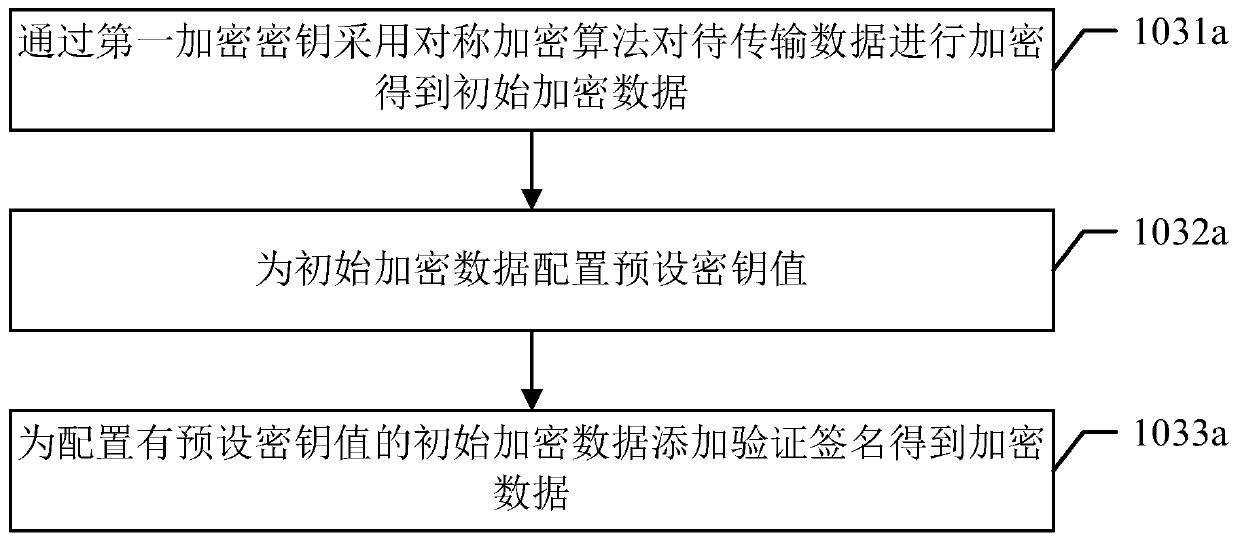
The invention discloses a secure communication method based on an intelligent door lock system and belongs to the technical field of intelligent home and security. The intelligent door lock system comprises an intelligent door lock and a mobile terminal which are in remote communication connection with a cloud server respectively. The method comprises the steps that the intelligent door lock and the mobile terminal are connected through a preset secure communication channel, and encryption keys are exchanged; to-be-transmitted data is generated through a sending end and encrypted through the encryption keys by using a preset encryption algorithm, and encrypted data is obtained; the sending end sends the encrypted data with the unique identification to a receiving end through the cloud server; identity authentication is conducted through the receiving end on the encrypted data with the unique identification, and the encrypted data is processed according to an identity authentication result. According to the method, no encryption key is saved in the server so that the server cannot understand the data forwarded through the server, even if the server is compromised, data encryption, identity authentication and replacement and tamper resisting in the communication between the intelligent door lock and the mobile terminal are still effective, and data security is ensured.
Owner:YUNDING NETWORK TECH BEIJING
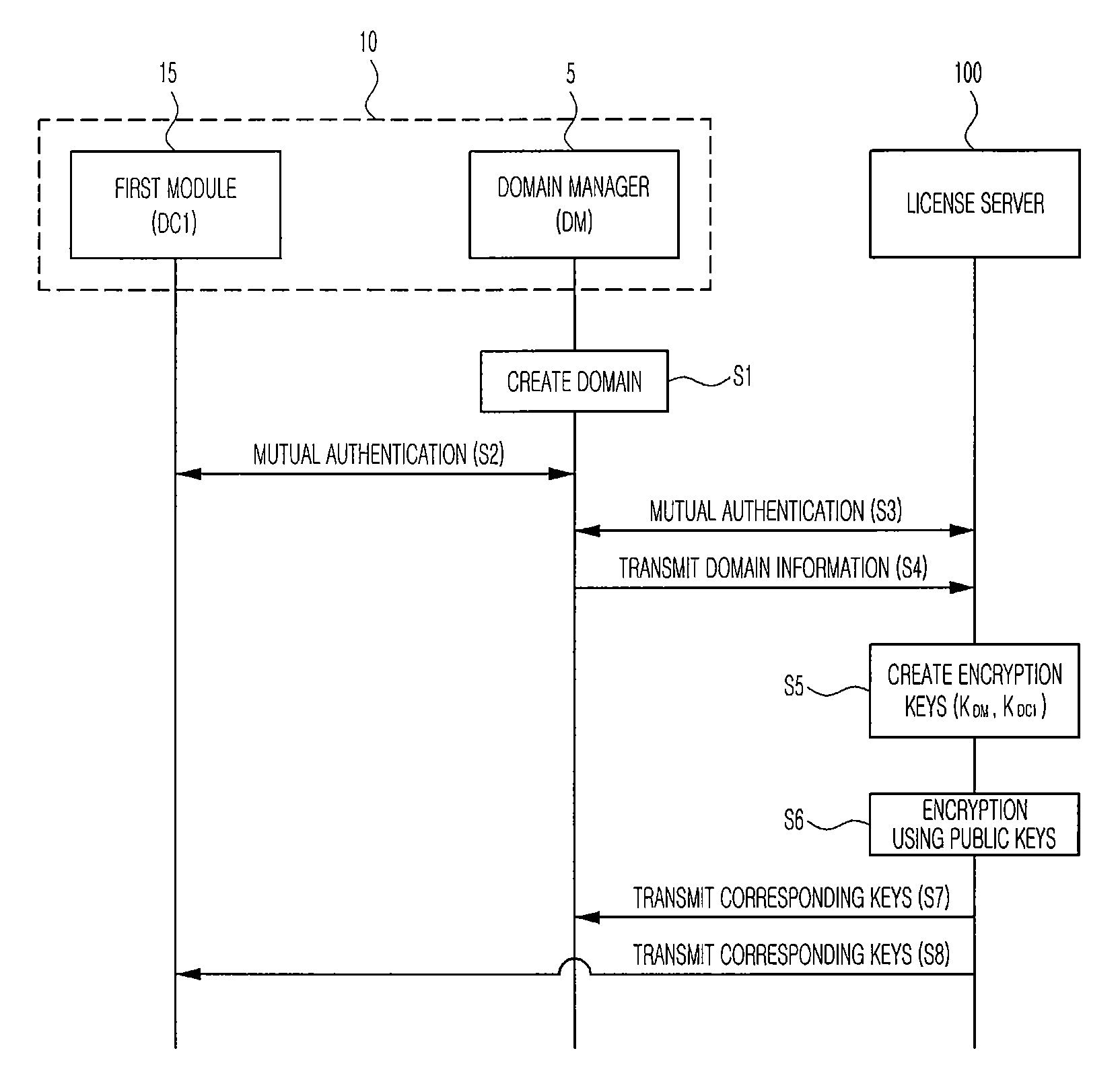
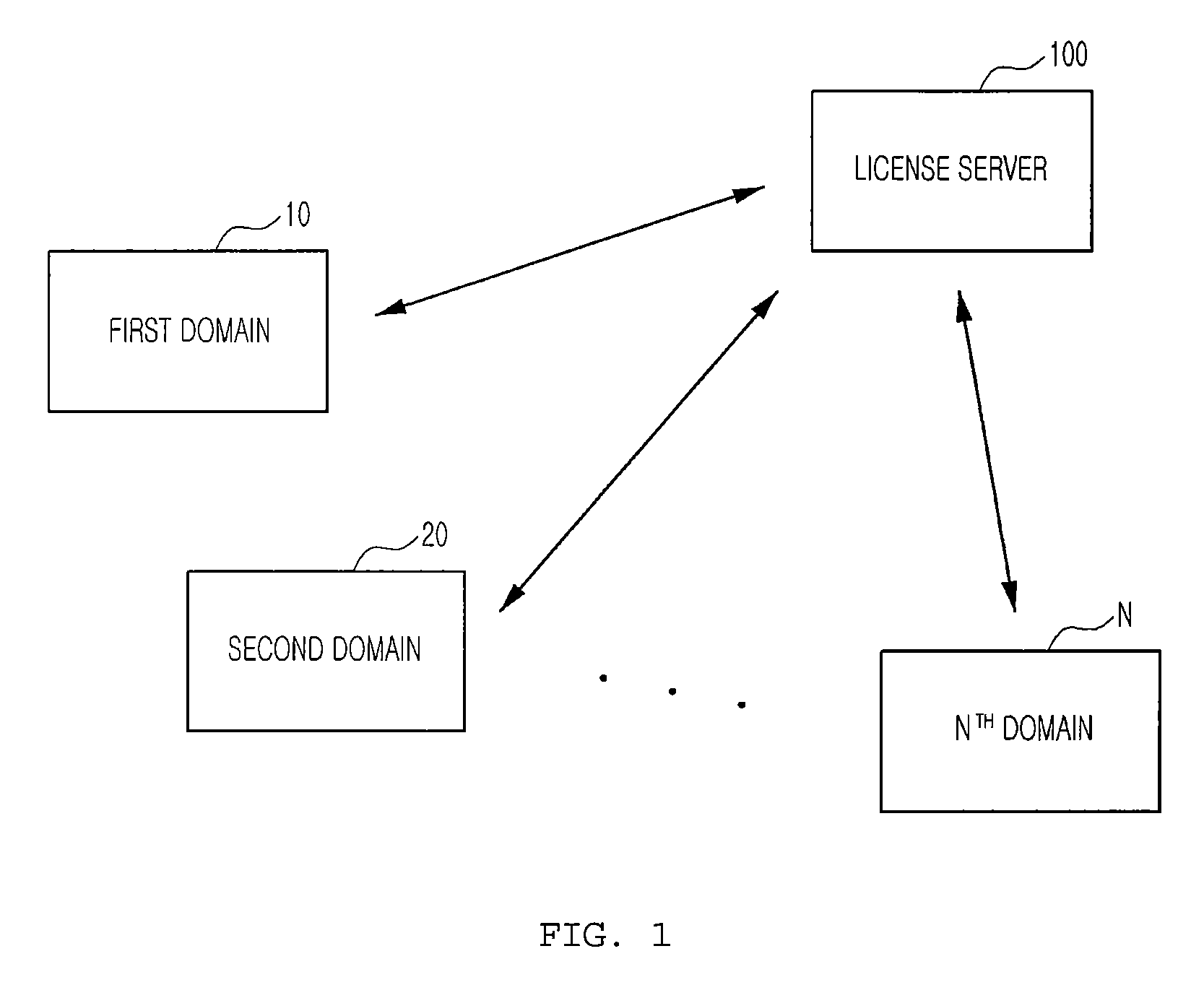
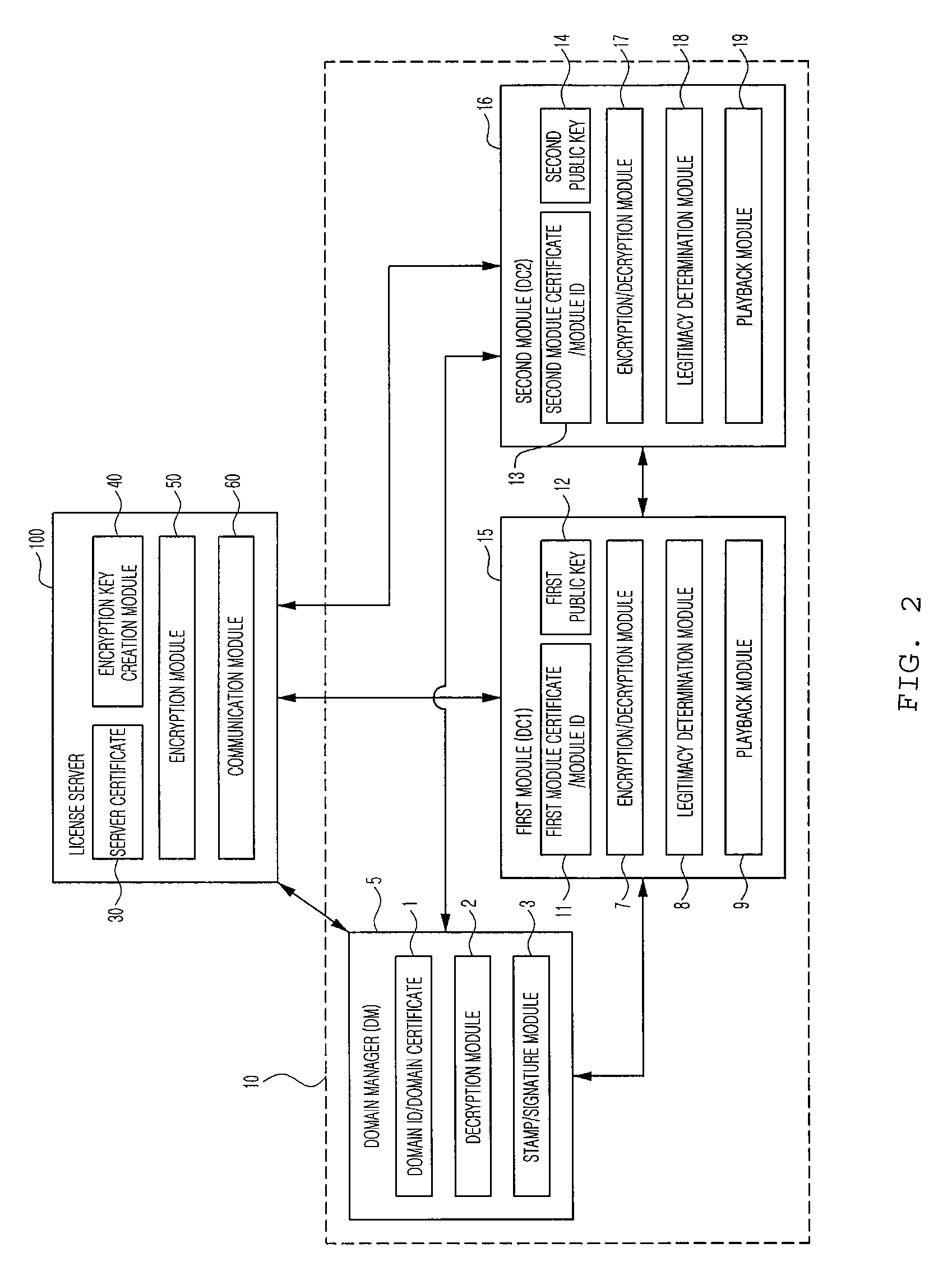
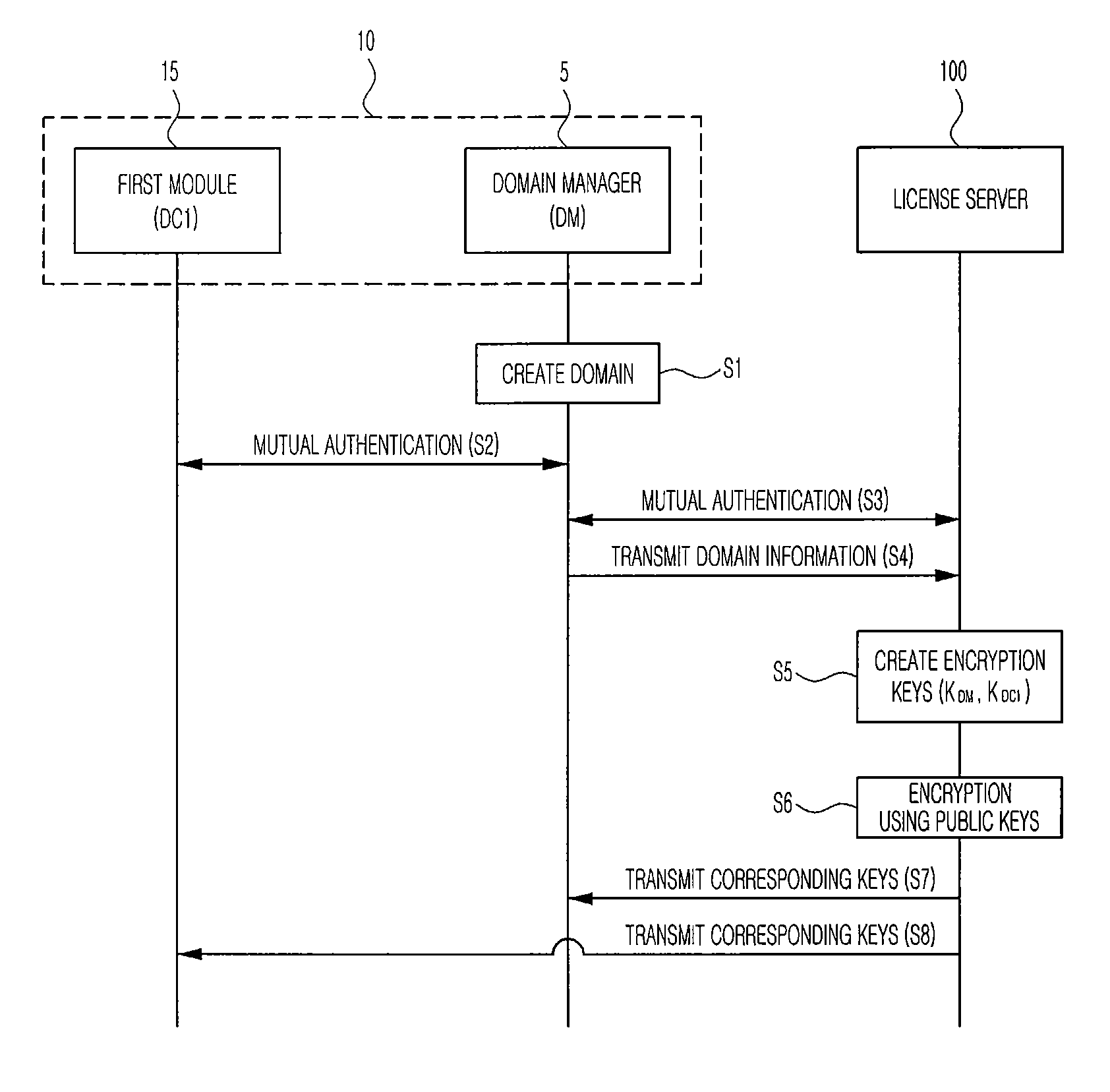
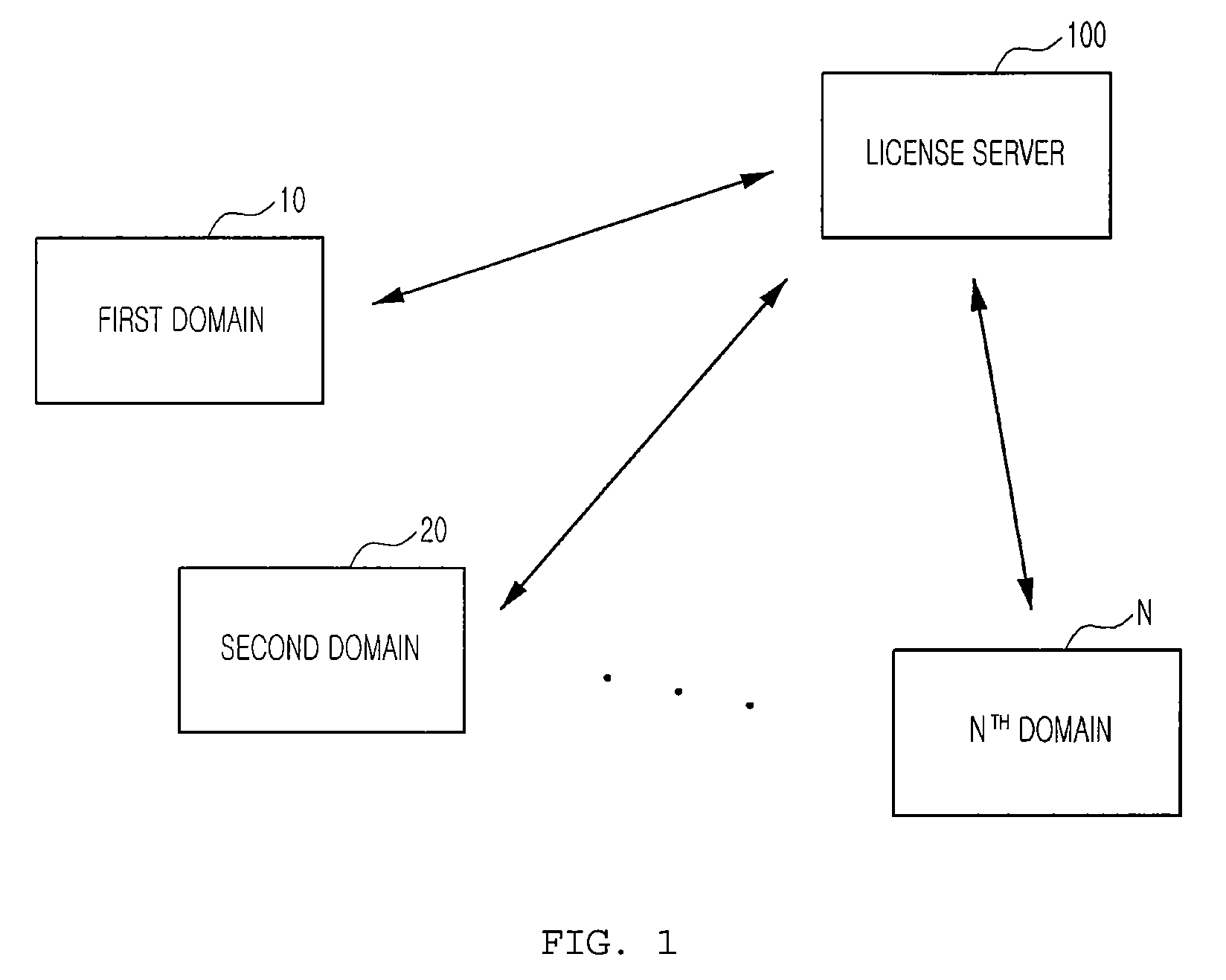
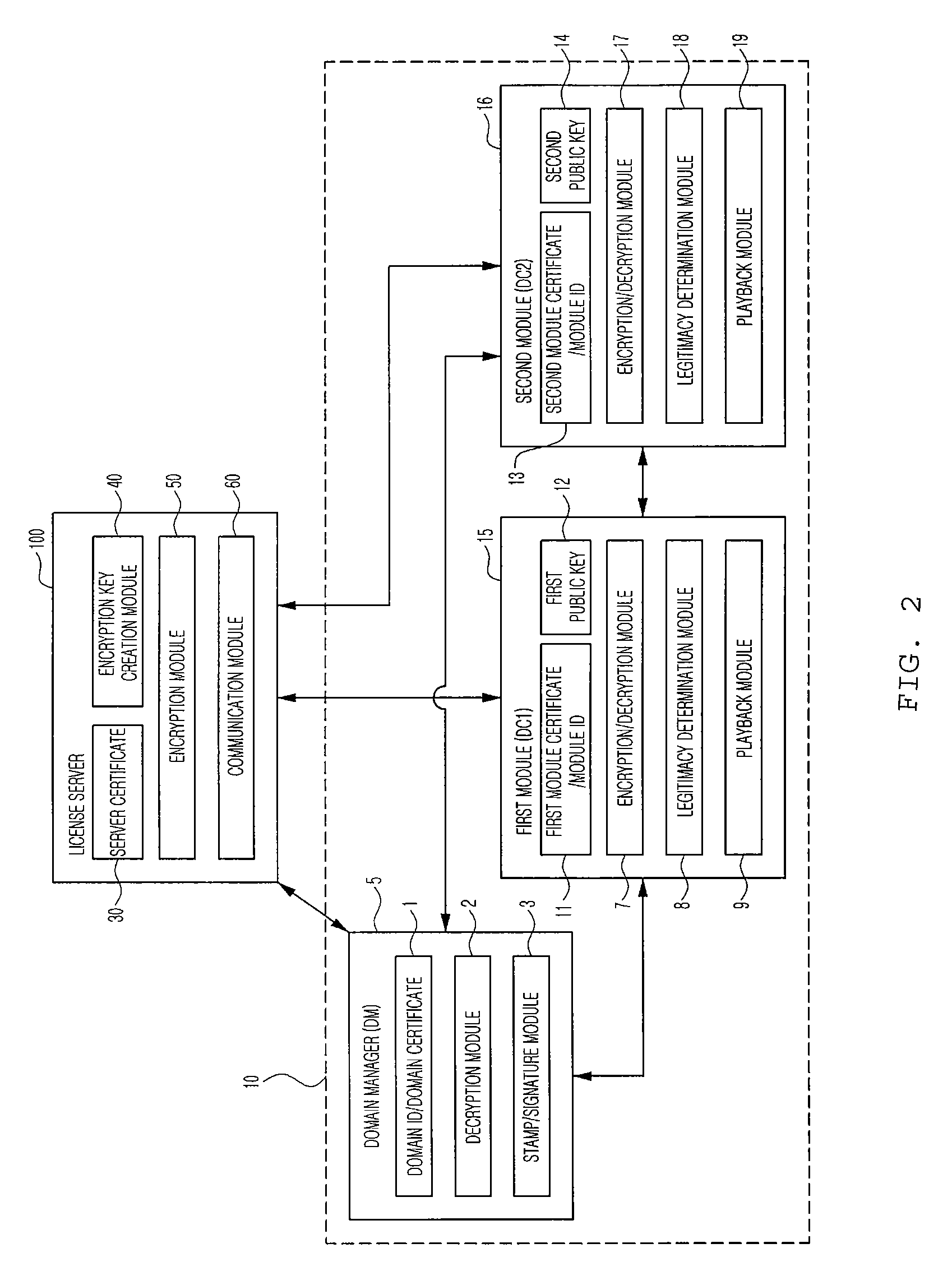
Domain digital rights management system, license sharing method for domain digital rights management system, and license server
ActiveUS20090208016A1Key distribution for secure communicationDigital data processing detailsDigital rights management systemRights management
Disclosed is a domain DRM system, a license sharing method for the domain DRM system, and a license server. The domain DRM system includes at least one domain including at least one user module adapted for encryption or decryption using a provided encryption key and a domain manager adapted for decryption using a provided encryption key, and a license server for creating encryption keys corresponding to the domain manager and the one user module, respectively, and providing them with the created contents, respectively, so that, when at least one user module requests contents, a contents encryption key used to encrypt the contents is encrypted by using an encryption key of the user module and an encryption key of the domain manager according to a commutative encryption scheme, and one of the domain manager and the user module is provided with a shared license obtained as a result of encryption.
Owner:RES & BUSINESS FOUND SUNGKYUNKWAN UNIV
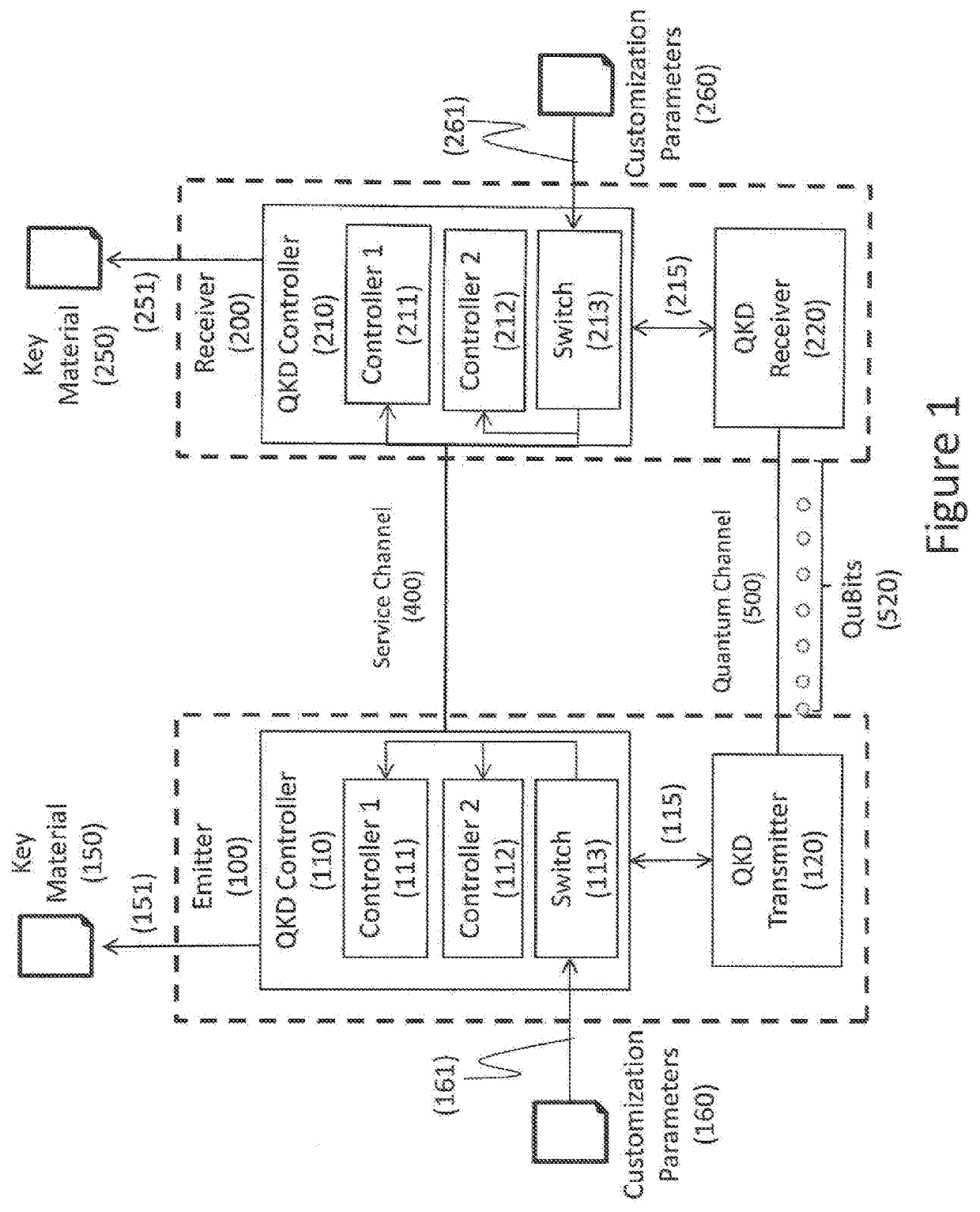
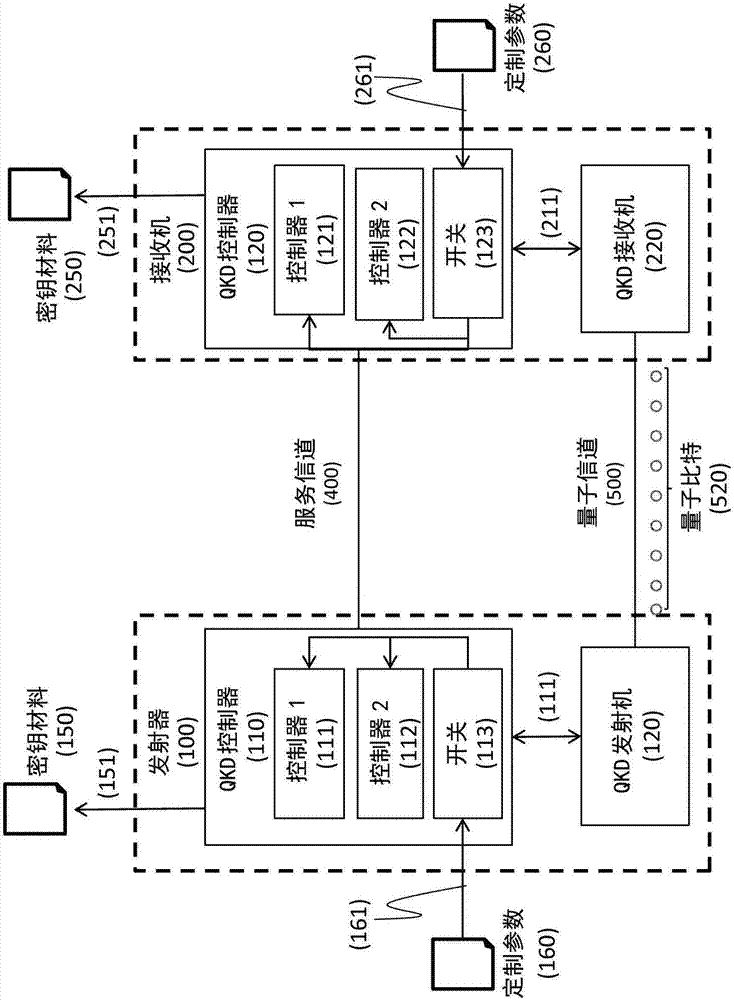
Apparatus and method for adding an entropy source to quantum key distribution systems
InactiveUS20200153619A1Increase its protection against attackQuantum computersKey distribution for secure communicationEngineeringComputational physics
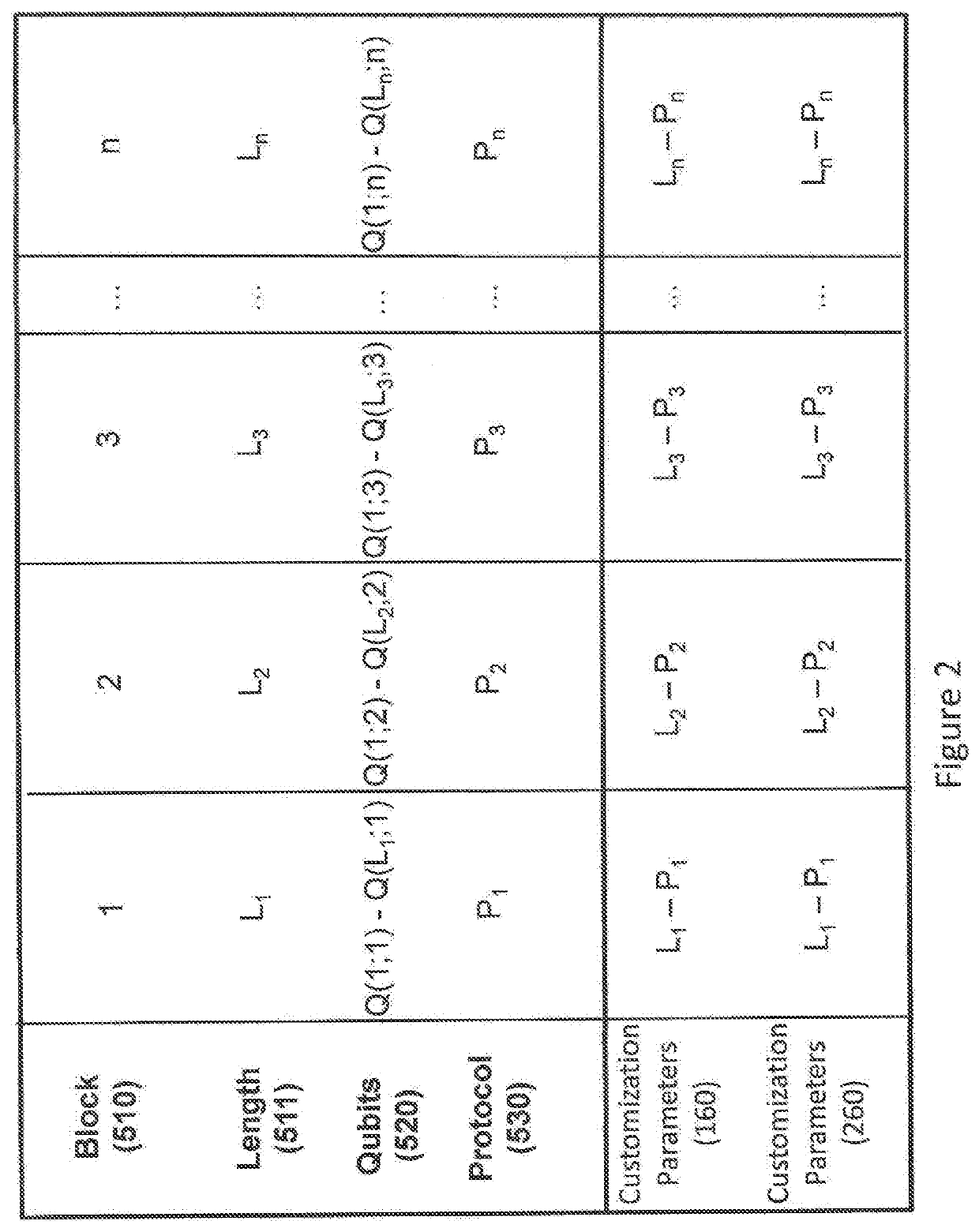
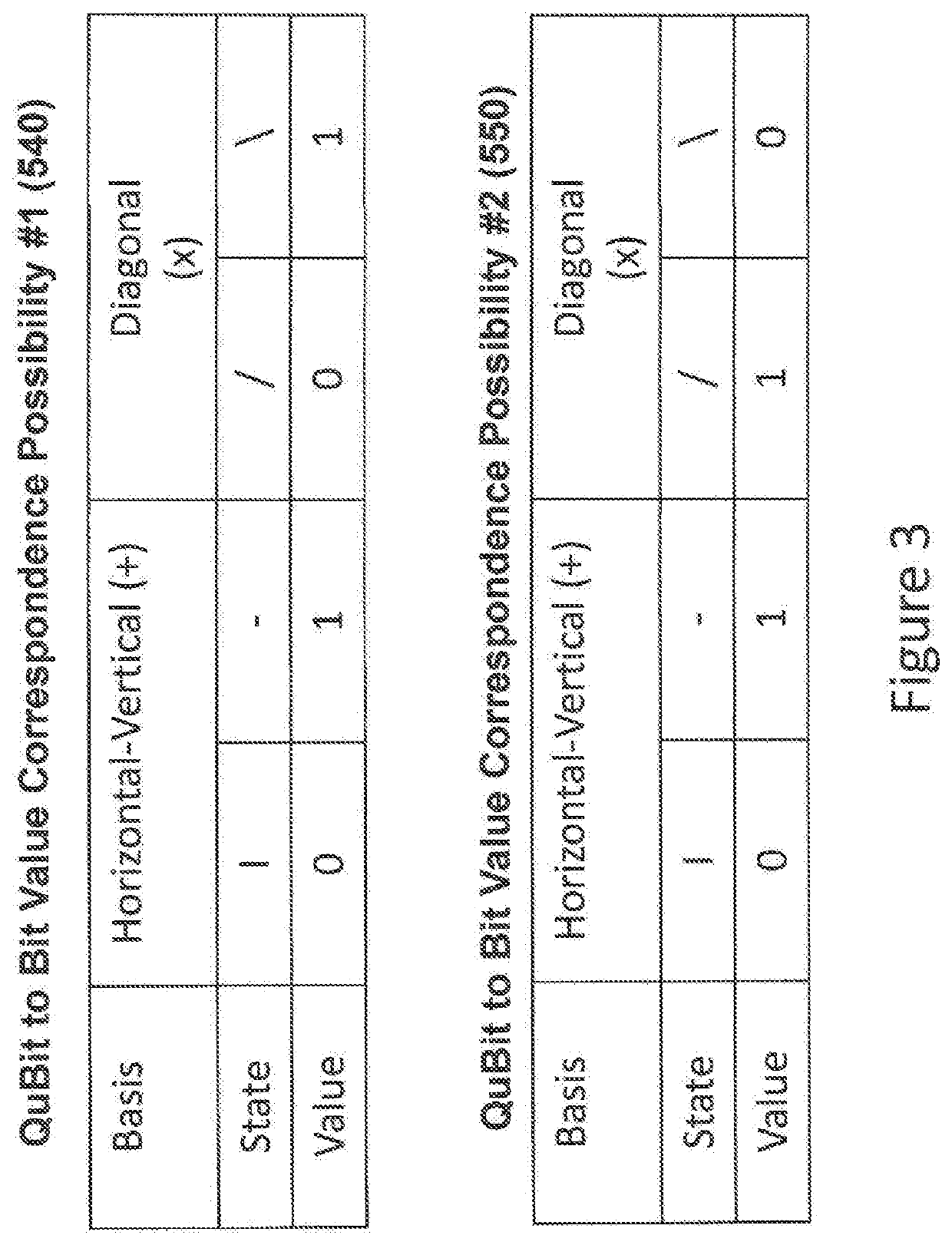
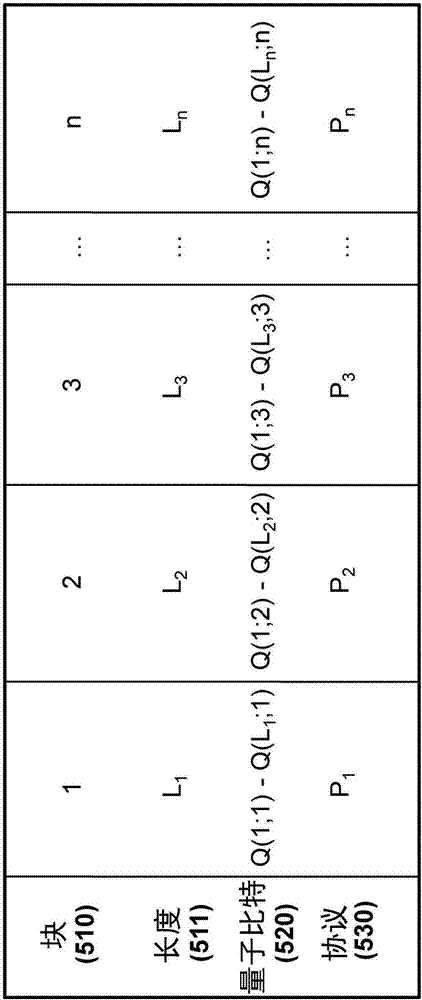
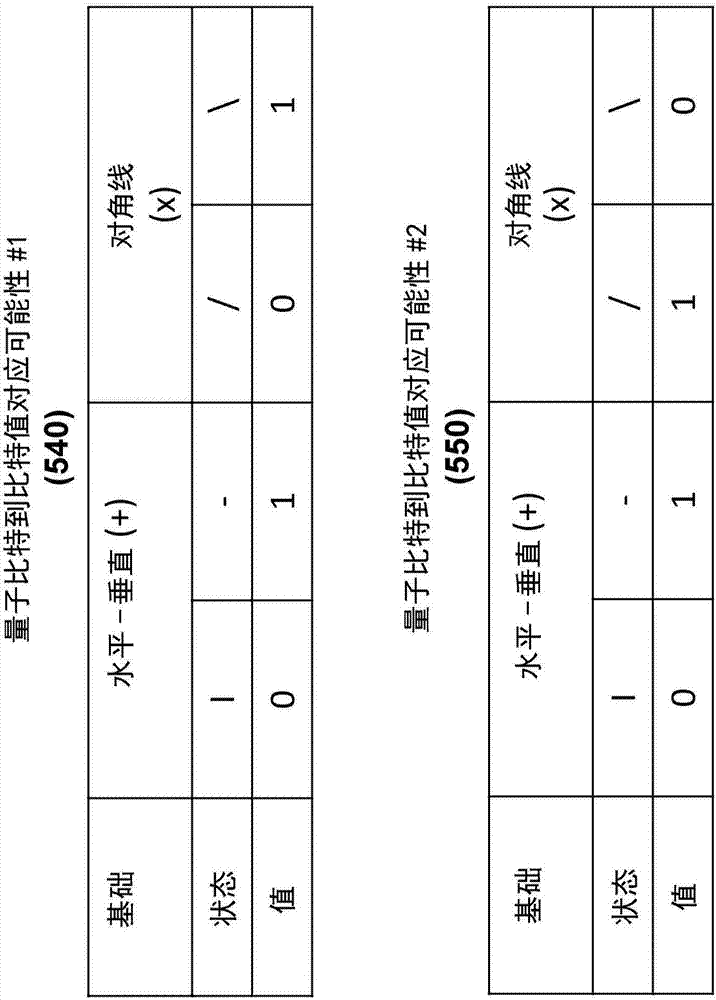
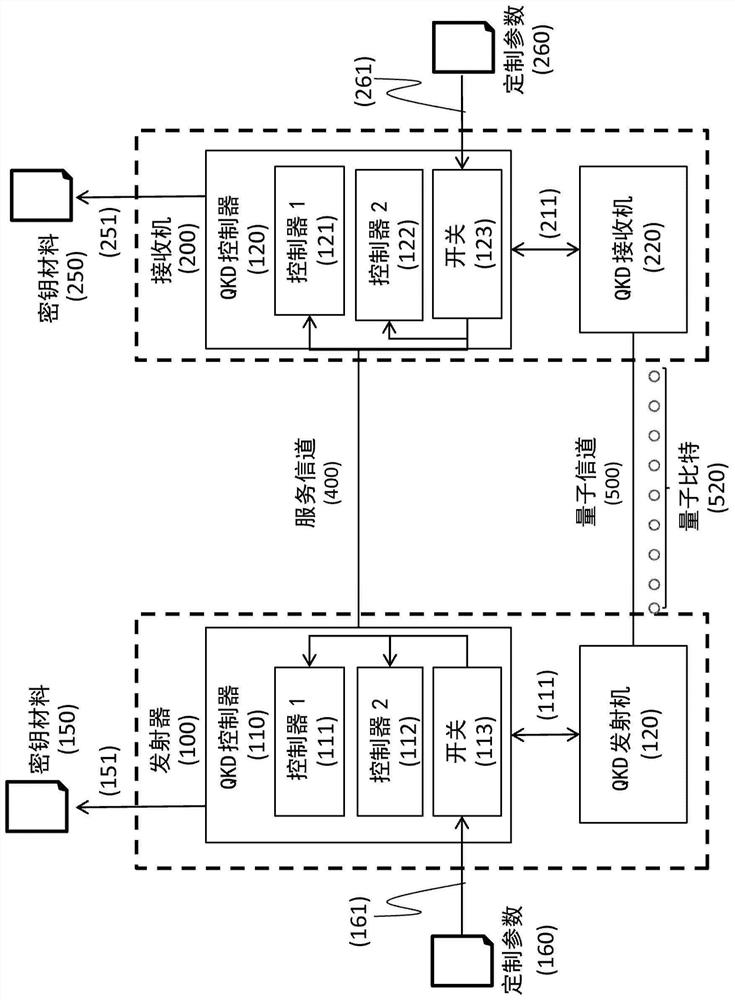
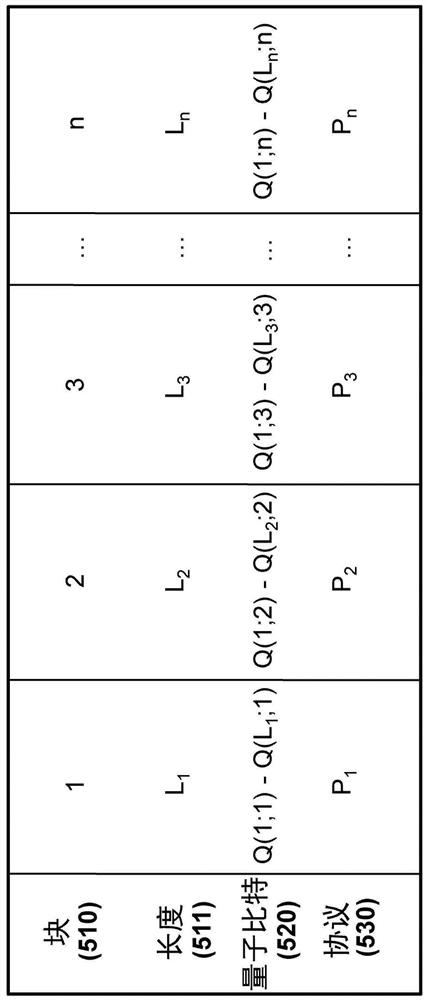
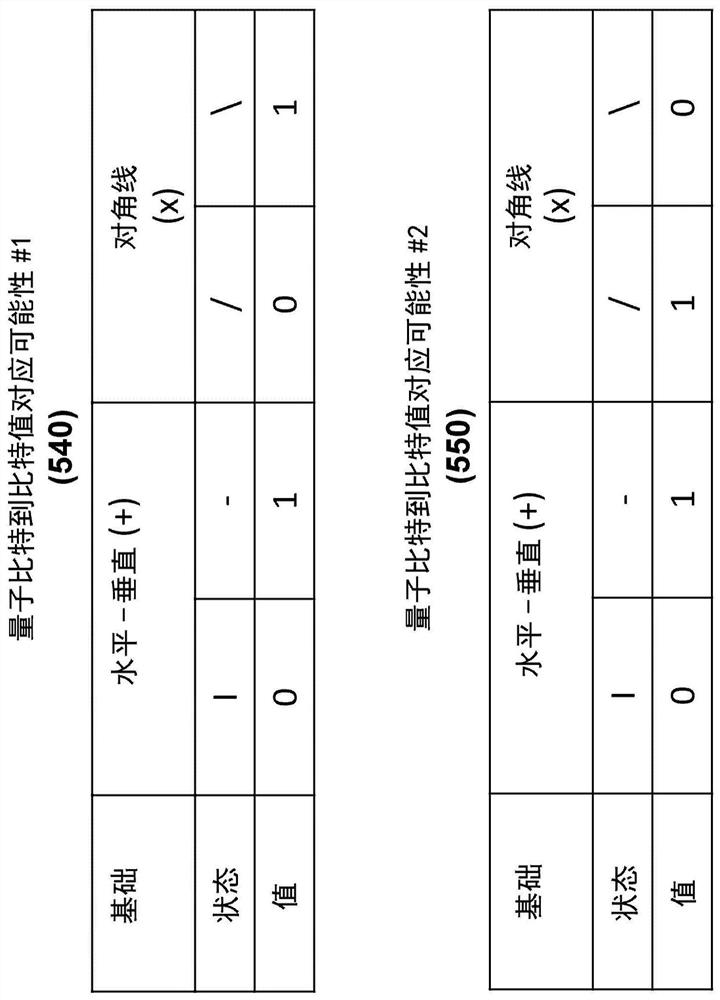
A QKD system used to securely exchange encryption keys between an emitter (100) and a receiver (200) modified to accept an additional customization parameter. Said QKD system consists of a QKD transmitter (120) and a QKD receiver (220) capable of implementing a plurality of QKD protocols forming a family of protocols. The QKD transmitter (120) and receiver (220) connected through a quantum channel (500) consist of optical and electronic components adapted to produce and detect a stream of qubits. The qubits (520) exchanged over the quantum channel (500) are grouped into blocks (510) consisting of at least one qubit and whose length is Li (511). For each, block (510) of qubits (520), one of the QKD protocol (530), selected from the family of protocols can be implemented using the emitter (100) and transmitter (200) is used.
Owner:ID QUANTIQUE SA
Transmit power control for wireless security
ActiveUS20060056636A1Increase transmit powerEnergy efficient ICTPower managementTransmitted powerWireless security
The present invention provides a method for establishing a secure channel between wireless devices. The method involves reducing the transmit power of the devices in conjunction with placing the devices in close proximity to one another. By reducing the transmit power, wireless communications between the devices cannot be detected by other devices beyond the short transmission range. The devices then generate and exchange encryption keys using the reduced-power transmissions in order to establish a secure, encrypted communications channel. Once the secure channel is established, the devices increase their transmit power back to normal operating levels, allowing them to be moved further apart while maintaining secure wireless communications.
Owner:QUALCOMM INC +1
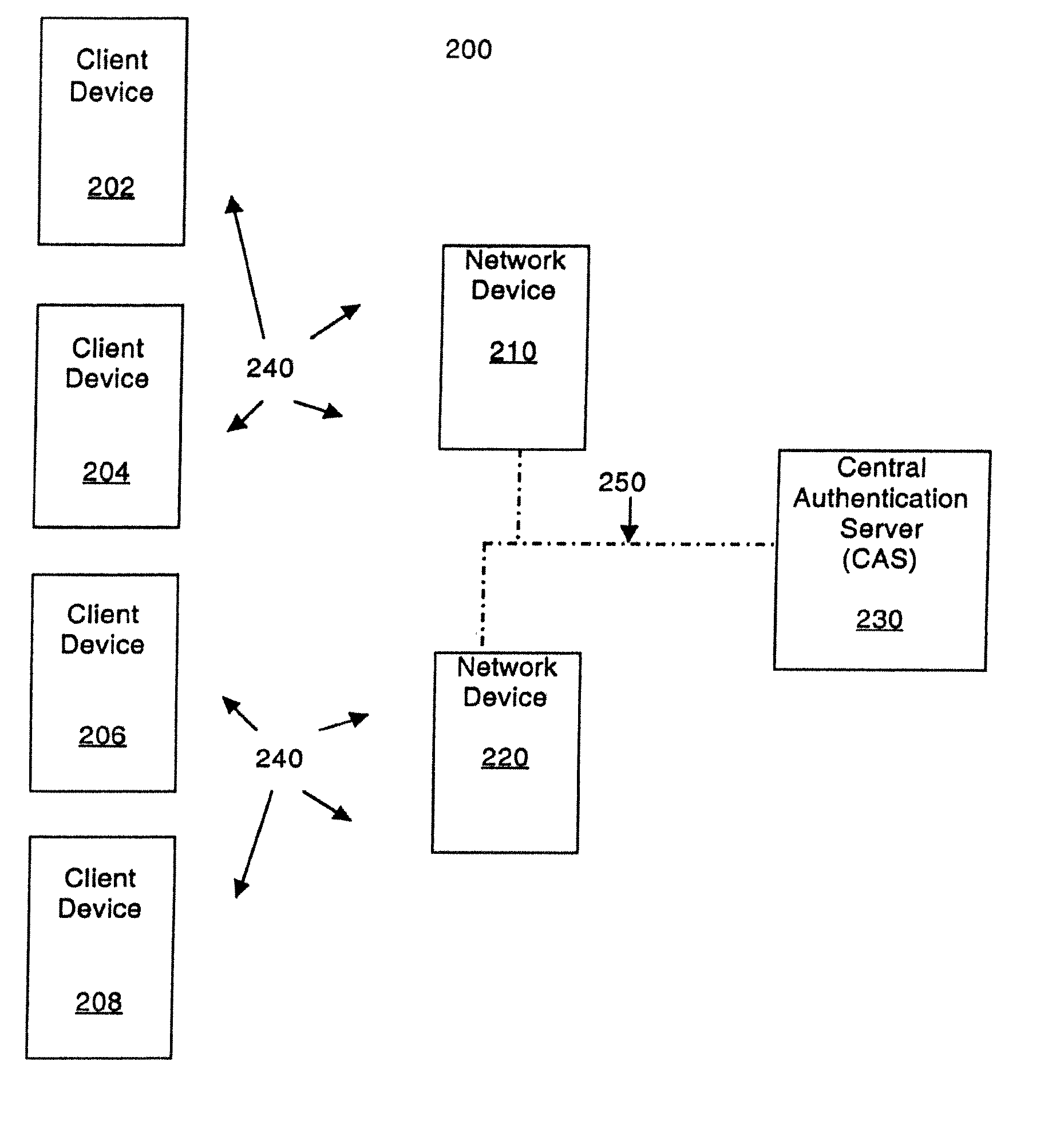
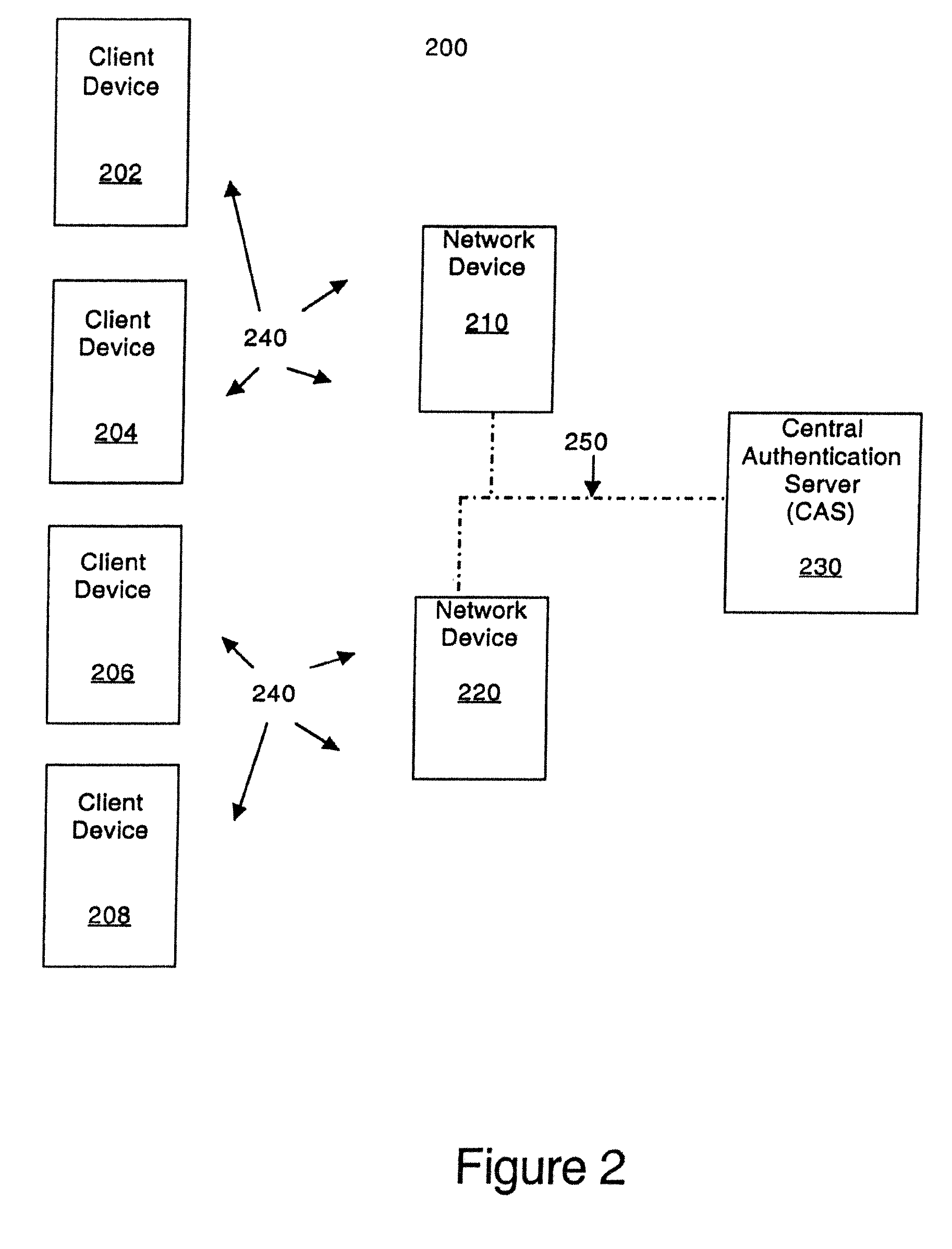
Scheme for device and user authentication with key distribution in a wireless network
InactiveUS20080115199A1Relieve burdenLight computational burdenRandom number generatorsUser identity/authority verificationUser authenticationClient-side
In a computer network, a method of mutually authenticating a client device and a network interface, authenticating a user to the network and exchanging encryption keys. In one embodiment, the method comprises authenticating the client device at the local network device point, with which the client device exchanges an encryption key and then the user is authenticated by a central authentication server. In another embodiment, the method comprises authenticating the client device at the central authentication server, with which the client device exchanges a key which is passed to the network device with a secret shared between the central authentication server and the network device. In this embodiment, the user is also authenticated at the central authentication server.
Owner:HEWLETT PACKARD CO
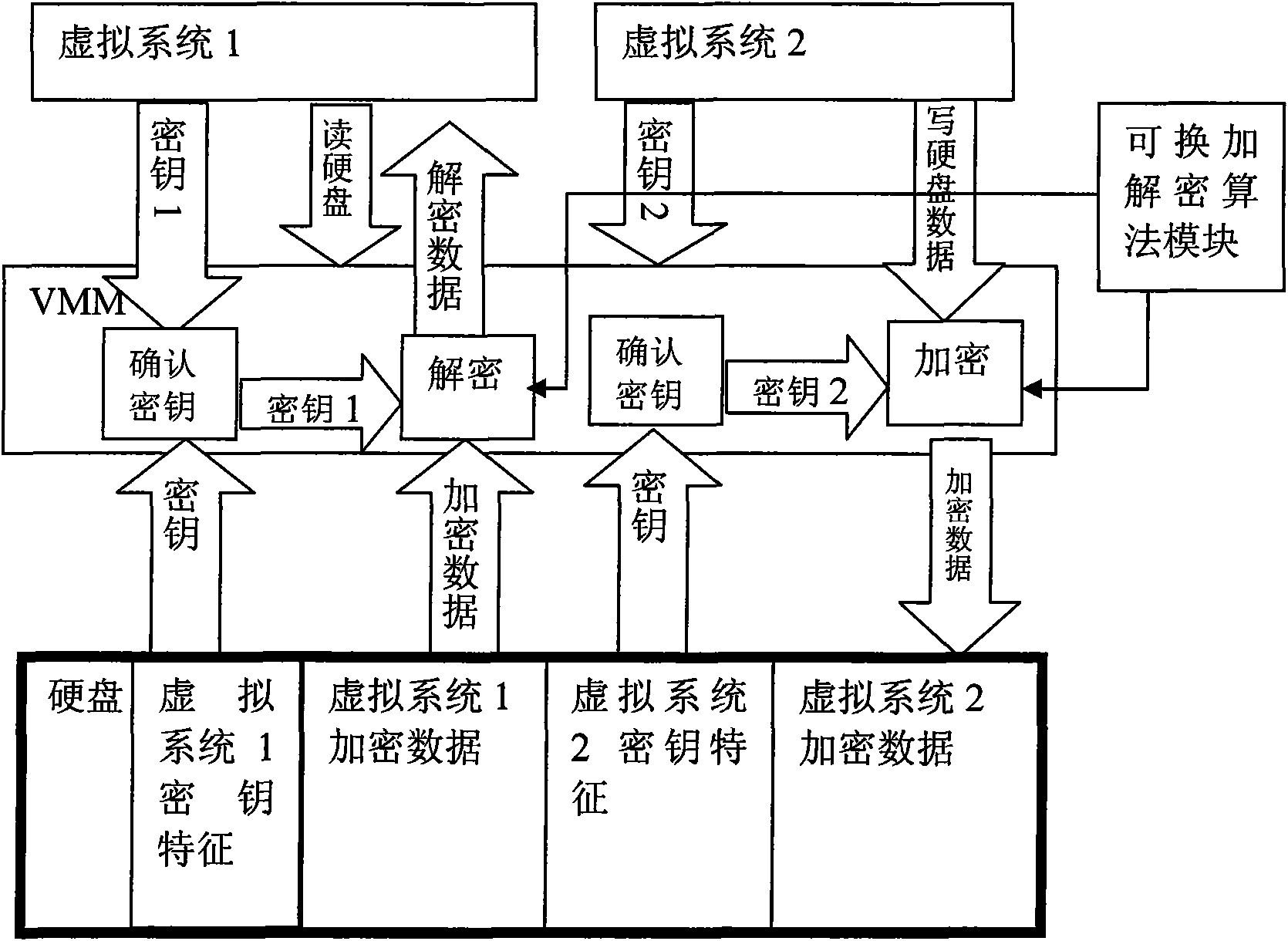
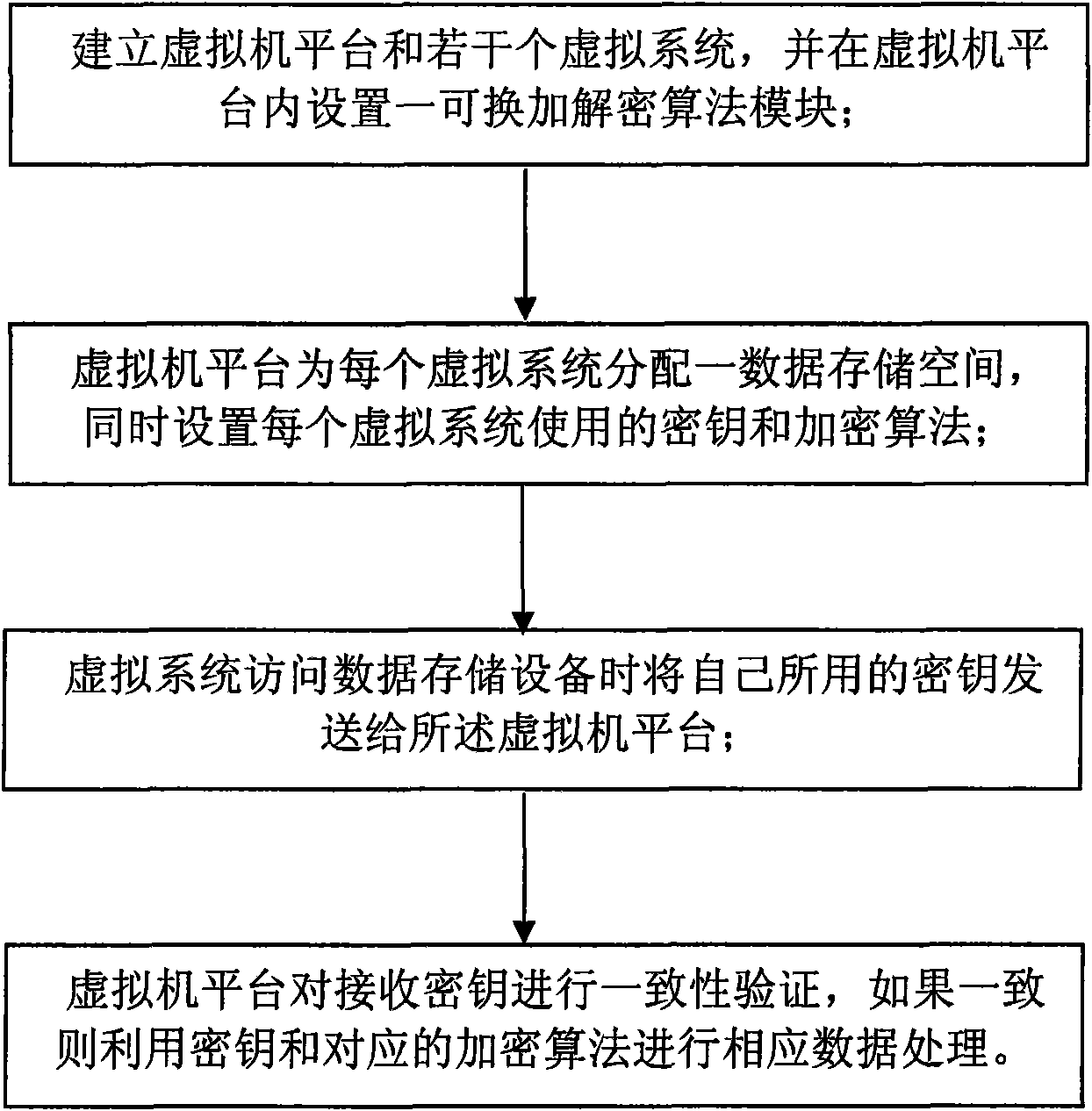
Method for encrypting data memory apparatus based on virtual system
ActiveCN101587524AEnsure safetyEasy to upgradePlatform integrity maintainanceSoftware simulation/interpretation/emulationData memoryCommutative encryption
The invention discloses a method for encrypting data memory apparatus based on virtual system, which belongs to the field of software technique. The method provided by the invention includes the steps of: (1) establishing a virtual machine platform and several virtual systems; (2) setting a commutative encryption and decryption algorithm module inside the virtual machine platform for providing an encryption algorithm for the virtual system; (3) dividing a data memory apparatus by the virtual machine platform, allotting a data memory space for each virtual system, meanwhile setting a cipher key and an encryption algorithm for each virtual system; (4) sending the used cipher key to the virtual machine platform when the virtual system accesses the data memory apparatus; (5) executing a consistency verification for the cipher key of the virtual system by the virtual machine platform, if consistent, and then using the cipher key and the corresponding encryption algorithm for executing a corresponding data-processing. The encryption algorithm provided by the invention is irrelevant to hard disk and VMM, and the encryption algorithm upgrade is convenient; moreover different storage zone can use different encryption keys for improving data safety.
Owner:宏电脑上海
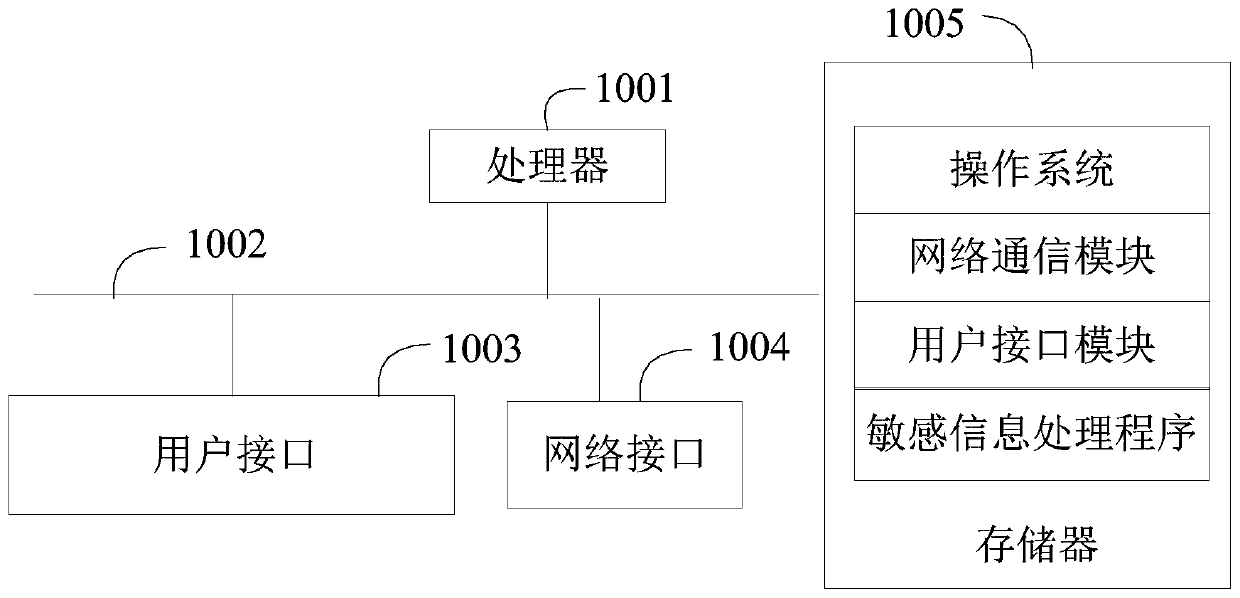
Sensitive information processing method and device and readable storage medium
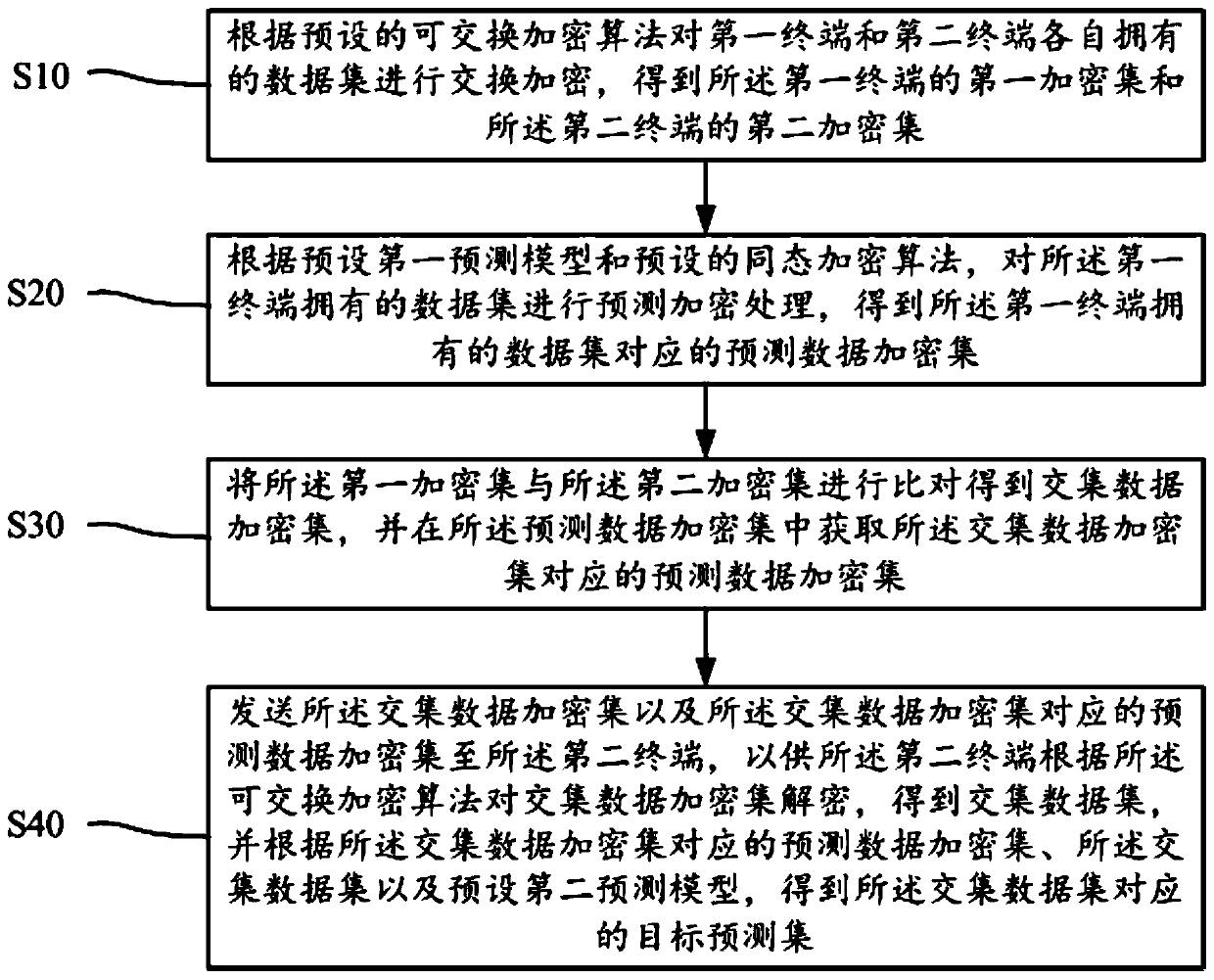
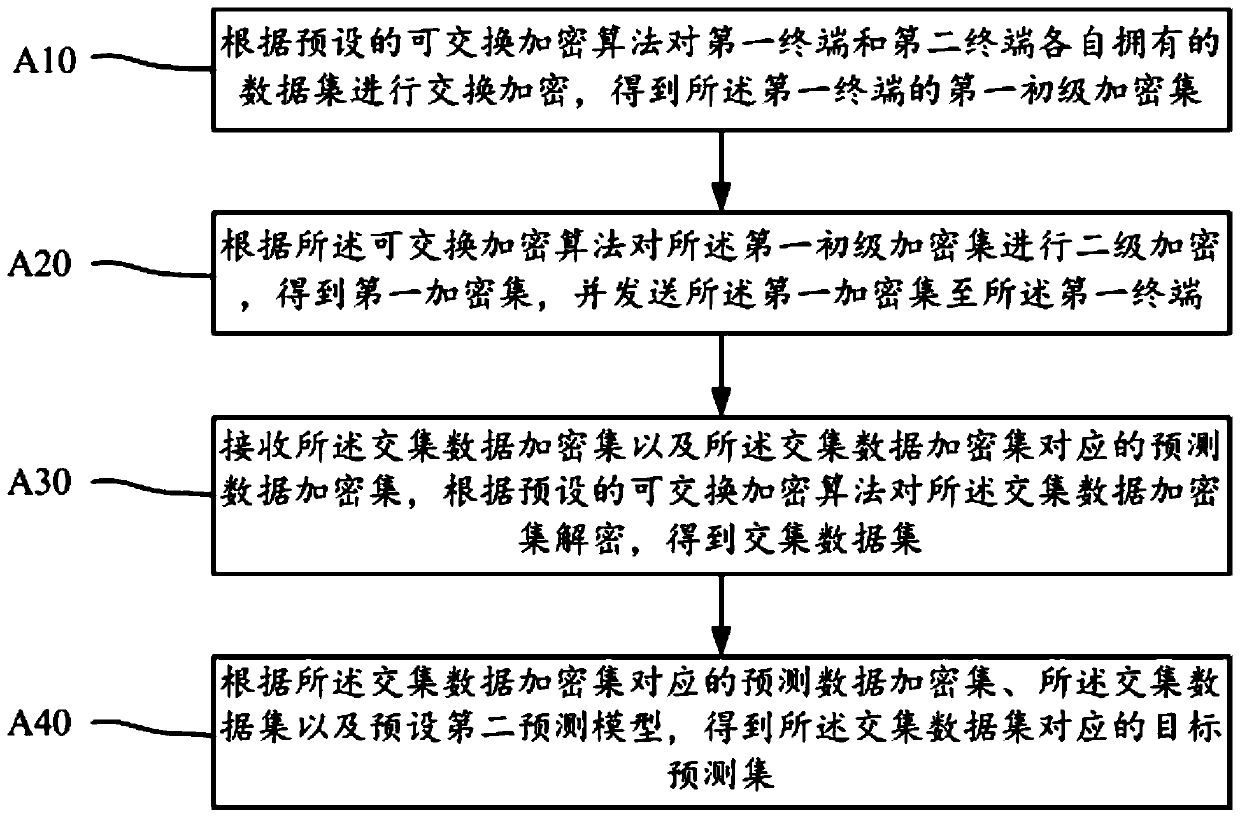
ActiveCN110851869AImprove securityProtect data privacyDigital data protectionInformation processingData set
The invention discloses a sensitive information processing method. The method comprises the following steps: exchanging and encrypting data sets of the first terminal and the second terminal accordingto an exchangeable encryption algorithm; obtaining a first encryption set of the first terminal and a second encryption set of the second terminal, according to the first prediction model, a data setowned by the first terminal and a homomorphic encryption algorithm, obtaining prediction data encryption set, obtaining intersection data encryption set of the first encryption set and the second encryption set, and acquiring prediction data encryption set of intersection data encryption set, and sending the intersection data encryption set and prediction data encryption set of the intersection data encryption set to the second terminal, so that the second terminal obtains a target prediction set corresponding to the intersection data set. The invention further discloses equipment and a readable storage medium. The multi-model joint prediction value corresponding to the intersection data can be obtained without disclosing respective data sets between the terminals, so that the data privacy is protected, and the information security is improved.
Owner:WEBANK (CHINA)
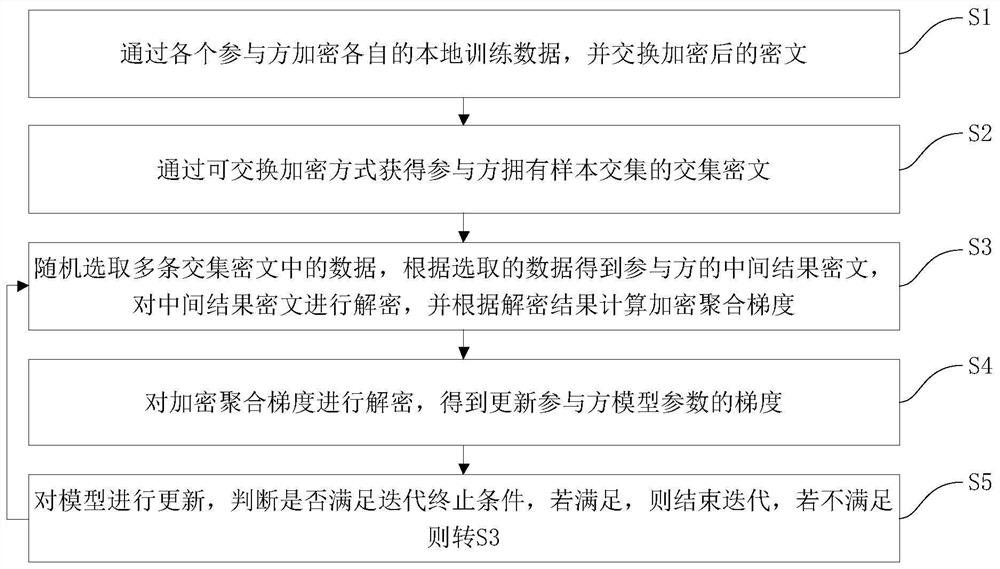
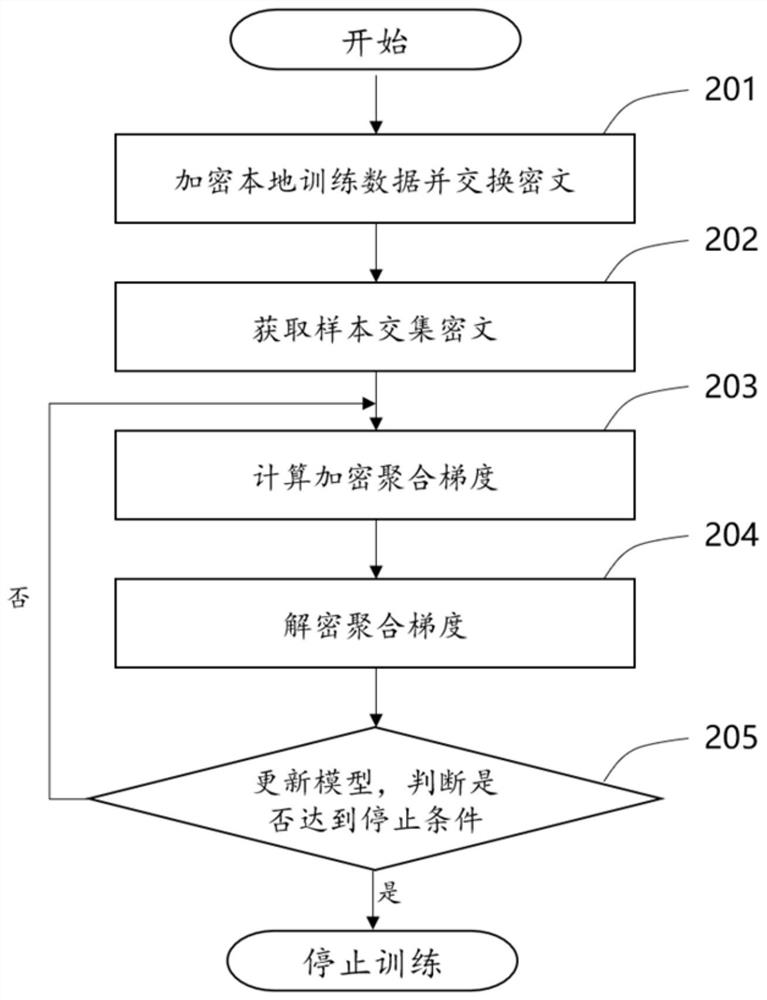
Longitudinal federated learning linear regression and logistic regression model training method and device
The invention discloses a longitudinal federated learning linear regression and logistic regression model training method and device, computer equipment and a storage medium, and the method comprises the steps: encrypting local training data of each participant through each participant, and exchanging the encrypted ciphertext; obtaining an intersection ciphertext of a sample intersection owned by the participant through an exchangeable encryption mode; randomly selecting data in the plurality of intersection ciphertexts, obtaining an intermediate result ciphertext of the participant according to the selected data, decrypting the intermediate result ciphertext, and calculating an encryption aggregation gradient according to a decryption result; decrypting the encrypted aggregation gradient to obtain a gradient for updating the parameters of the participant model; and updating the model, judging whether an iteration termination condition is met or not, if so, ending iteration, and if not, continuing training. The technical problem that in the prior art, due to data privacy and lack of trust among different organizations, sensitive data of all the organizations are difficult to fully utilize for distributed machine learning model training is solved.
Owner:BEIHANG UNIV
Domain digital rights management system, license sharing method for domain digital rights management system, and license server
ActiveUS8165304B2Key distribution for secure communicationDigital data processing detailsDigital rights management systemCommutative encryption
Owner:RES & BUSINESS FOUND SUNGKYUNKWAN UNIV
Apparatus and method for quantum key distribution with enhanced security and reduced trust requirements
ActiveCN106899403AQuantum computersKey distribution for secure communicationQuantum channelEngineering
A QKD system used to securely exchange encryption keys between an emitter (100) and a receiver (200) modified to accept an additional customization parameter. Said QKD system consists of a QKD transmitter (120) and a QKD receiver (220) capable of implementing a plurality of QKD protocols forming a family of protocols. The QKD transmitter (120) and receiver (220) connected through a quantum channel (500) consist of optical and electronic components adapted to produce and detect a stream of qubits. The qubits (520) exchanged over the quantum channel (500) are grouped into blocks (510) consisting of at least one qubit and whose length is L i (511). For each, block (510) of qubits (520), one of the QKD protocol (530), selected from the family of protocols can be implemented using the emitter (100) and transmitter (200) is used.
Owner:ID量子技术公司
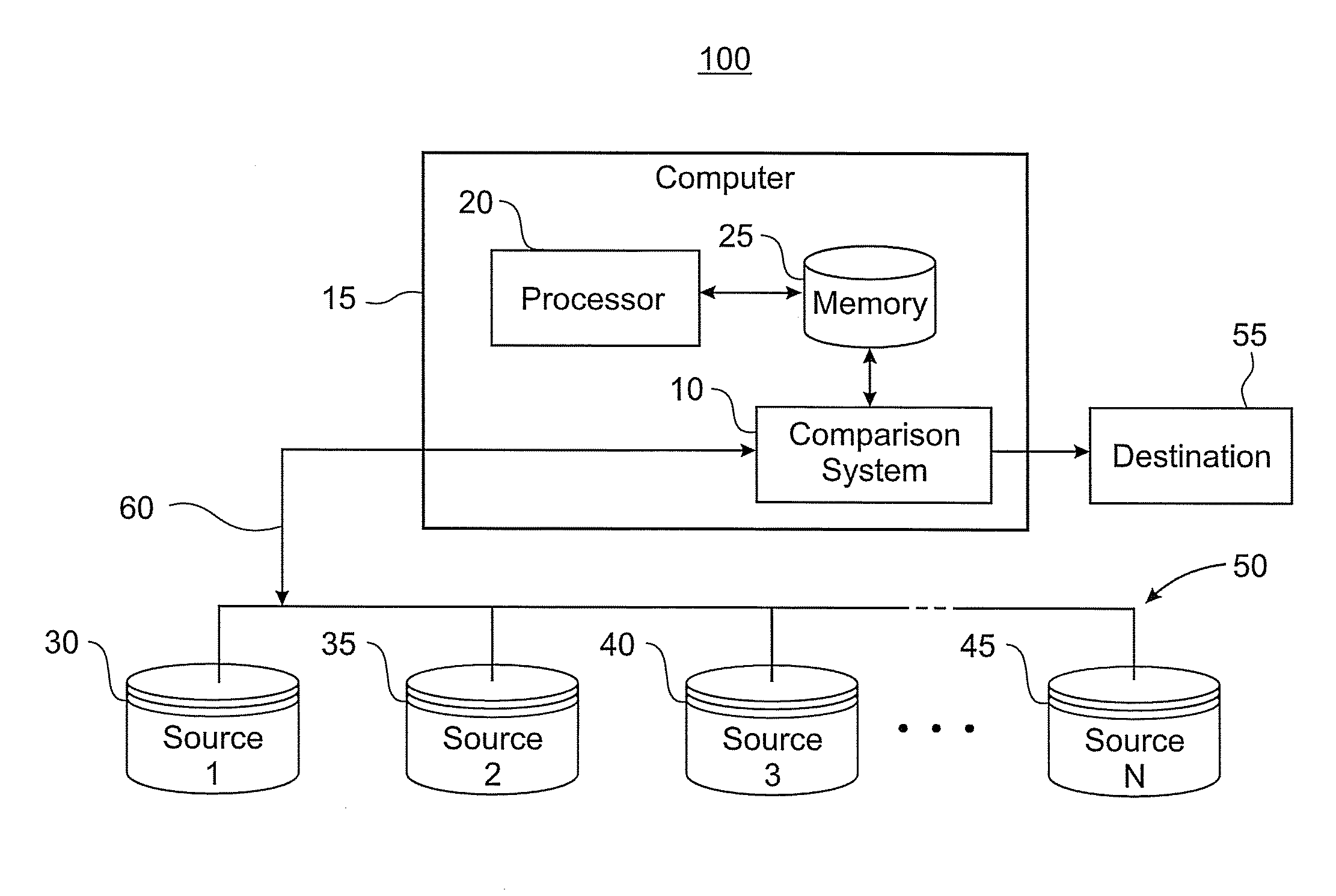
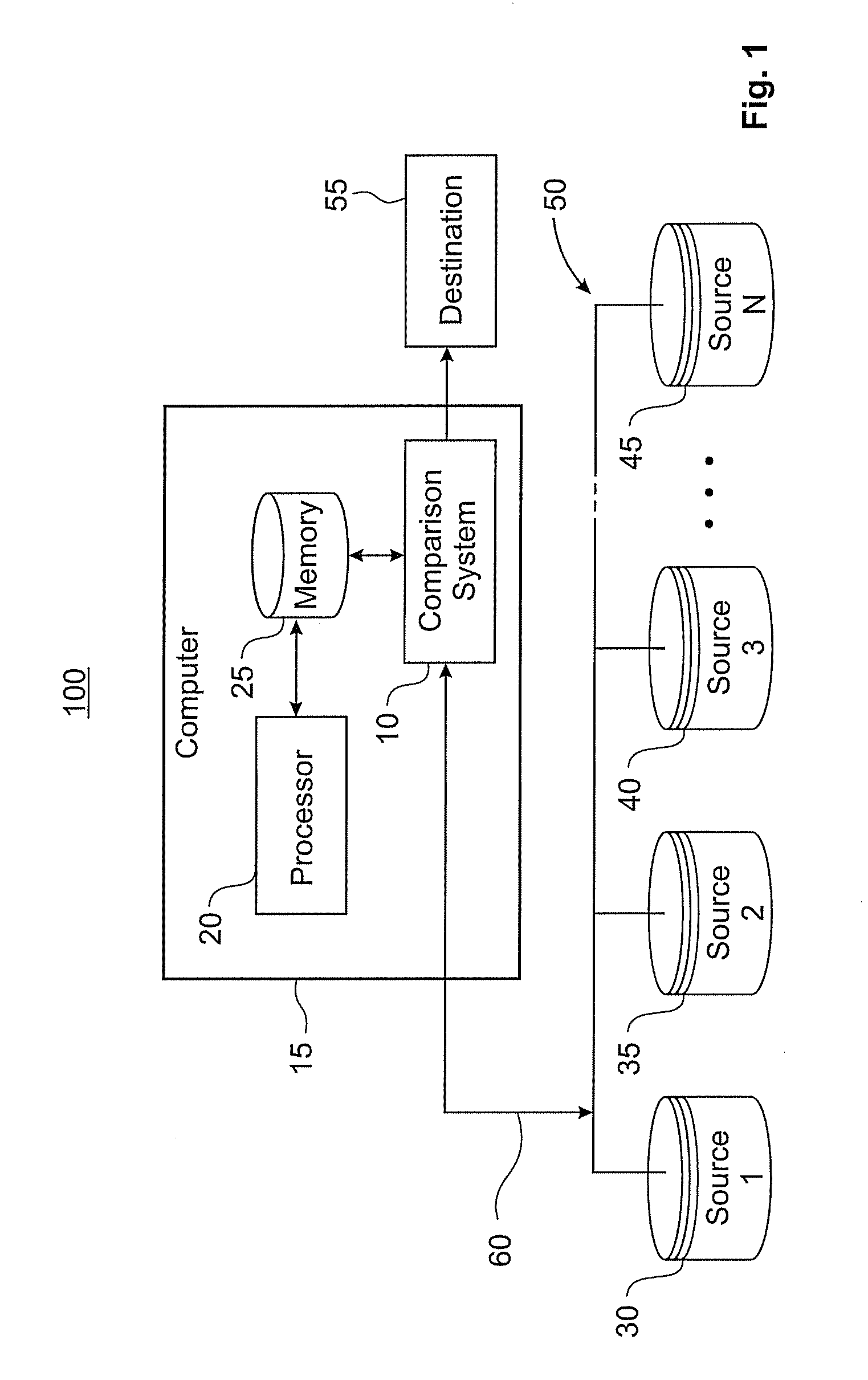
Privacy enhanced comparison of data sheets
InactiveUS20080310621A1Digital data processing detailsSecret communicationData setCommutative encryption
A computer implemented method for performing a privacy enhanced comparison of a plurality of data sets includes allocating a private encryption key to each of the data sets; performing an encryption operation for each of the data sets, the encryption operation comprising generating a commutatively encrypted data set of the respective data set, wherein the commutatively encrypted data sets are generated by successively applying a keyed commutative encryption function on the respective data set with the private encryption key of the respective data set itself and with the private encryption keys of the other data sets; and comparing the commutatively encrypted data sets.
Owner:IBM CORP
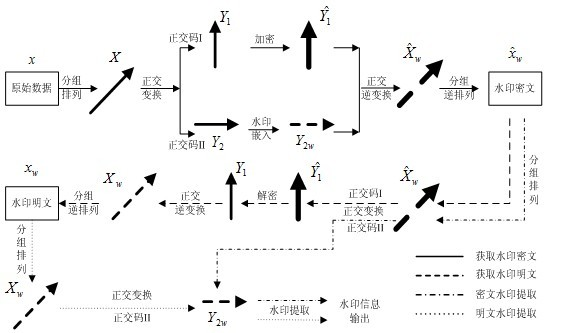
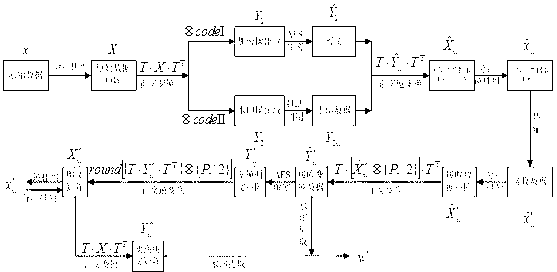
Method for commutative encryption and watermarking on identical operation domain
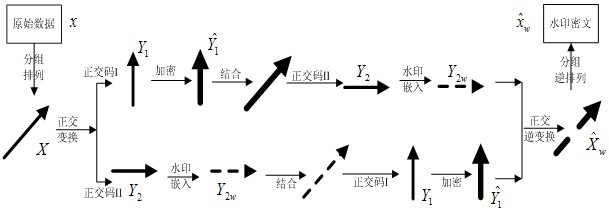
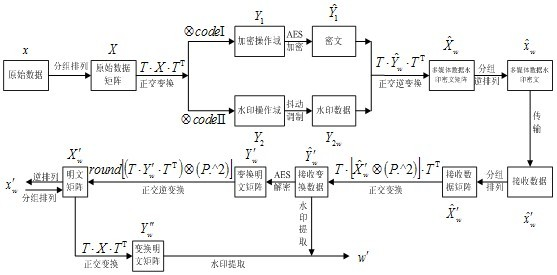
InactiveCN102185843AAchieve seamless integrationAvoid exposureUser identity/authority verificationMultiplexingData domain
The invention relates to a method for commutative encryption and watermarking on an identical operation domain. An encryption technology and a digital watermarking technology are seamlessly combined to provide deeper comprehensive protection for multimedia data. In the method, orthogonal code division and separately encryption and watermarking operations are performed in an orthogonal commutationdomain by the principle of code division multiplexing in the field of communication, thereby realizing commutation between the encryption and watermarking operations; and simultaneously, encryption and watermarking operation results are superposed in the same data domain and displayed to a user under the control of orthogonal codes to realize the fusion of encryption and watermarking operation domains. In addition, related encryption operations and digital watermarking operations are not specially required, so a relatively larger space is ensured in specific algorithm designing. By the method, a commutative encryption and watermarking technology is realized on the identical operation domain, the encryption and watermarking operations can be conveniently performed at the same time, and relatively higher security and universality are ensured.
Owner:WUHAN UNIV
Data query method, device and system based on exchangeable encrypted data confusion
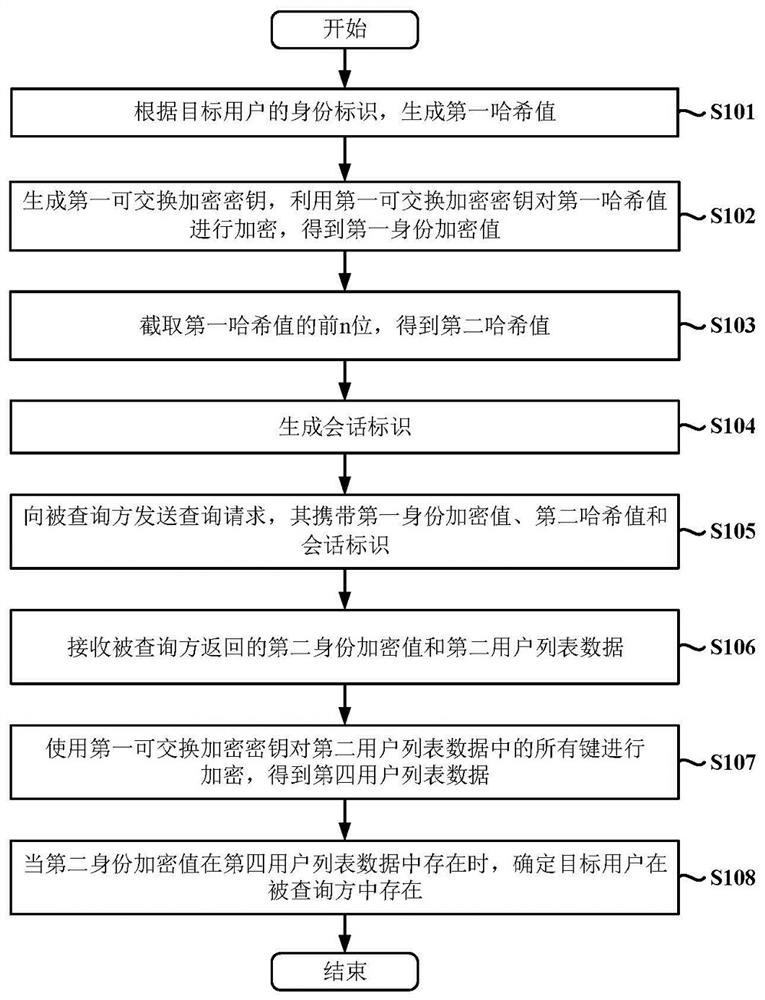
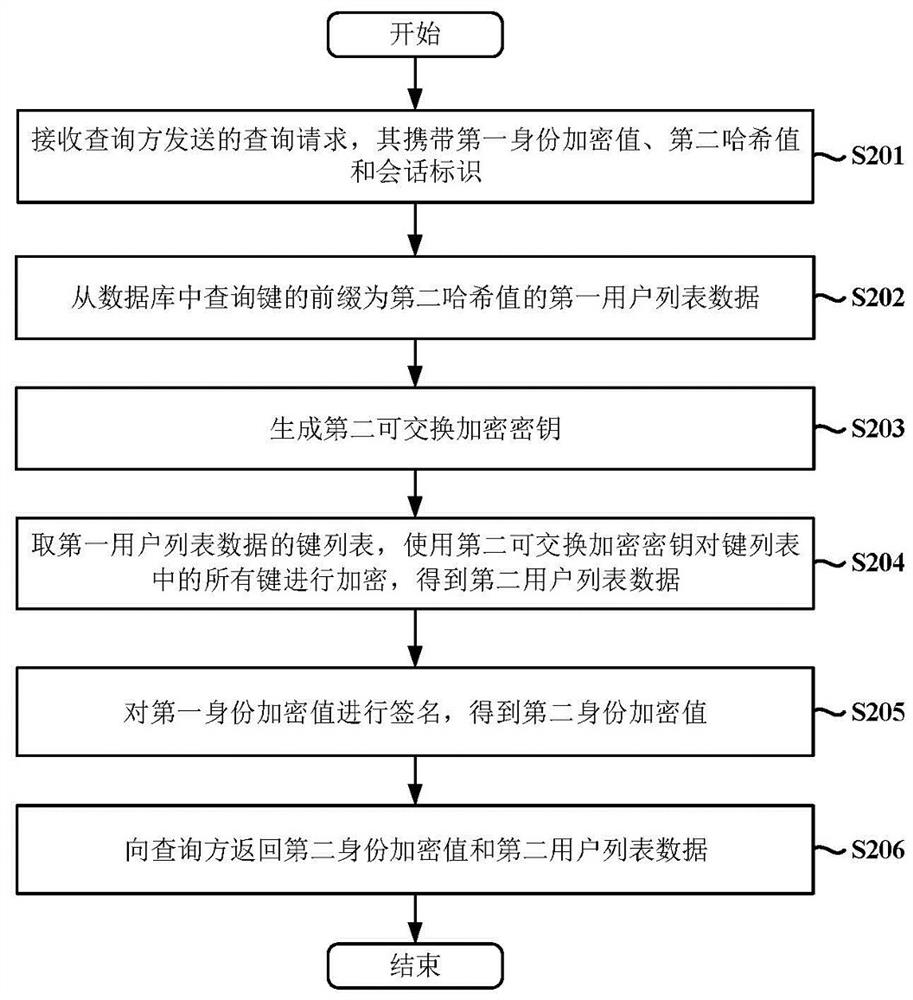
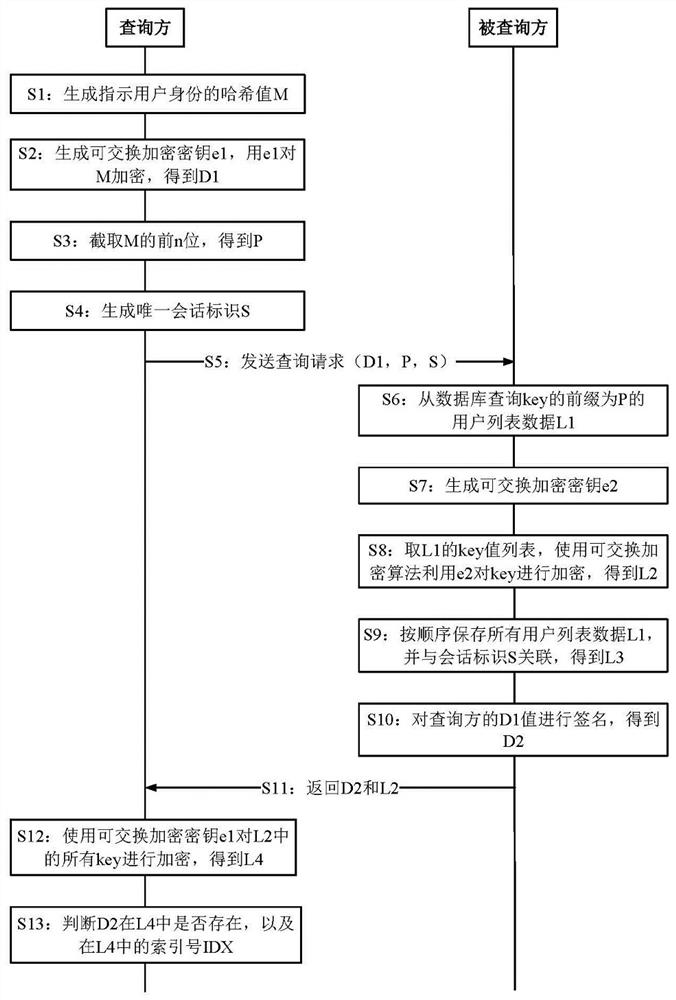
ActiveCN114840867ARealize anonymous queryRandom number generatorsFinanceCommutative encryptionUser identifier
The invention provides a data query method, device and system based on exchangeable encrypted data confusion, and the method comprises the steps: generating a first hash value according to a user identifier; encrypting the first hash value by using the first exchangeable encryption key to obtain a first encrypted value; intercepting the first n bits of the first hash value to obtain a second hash value; generating a session identifier; sending a query request to a queried party, wherein the query request carries the first encryption value, the second hash value and the session identifier; receiving a second encryption value and a second user list returned by the queried party; the second encrypted value is obtained by performing signature processing on the first encrypted value; the second user list is obtained by encrypting all keys of the first user list by using an exchangeable encryption algorithm; encrypting all keys in the second user list to obtain a fourth user list; and determining whether the target user exists in the queried party or not according to the second encryption value and the fourth user list. The method can be used for hiding traced queries and minimizing information leakage.
Owner:北京融数联智科技有限公司
Data collision method and device, storage medium and electronic equipment
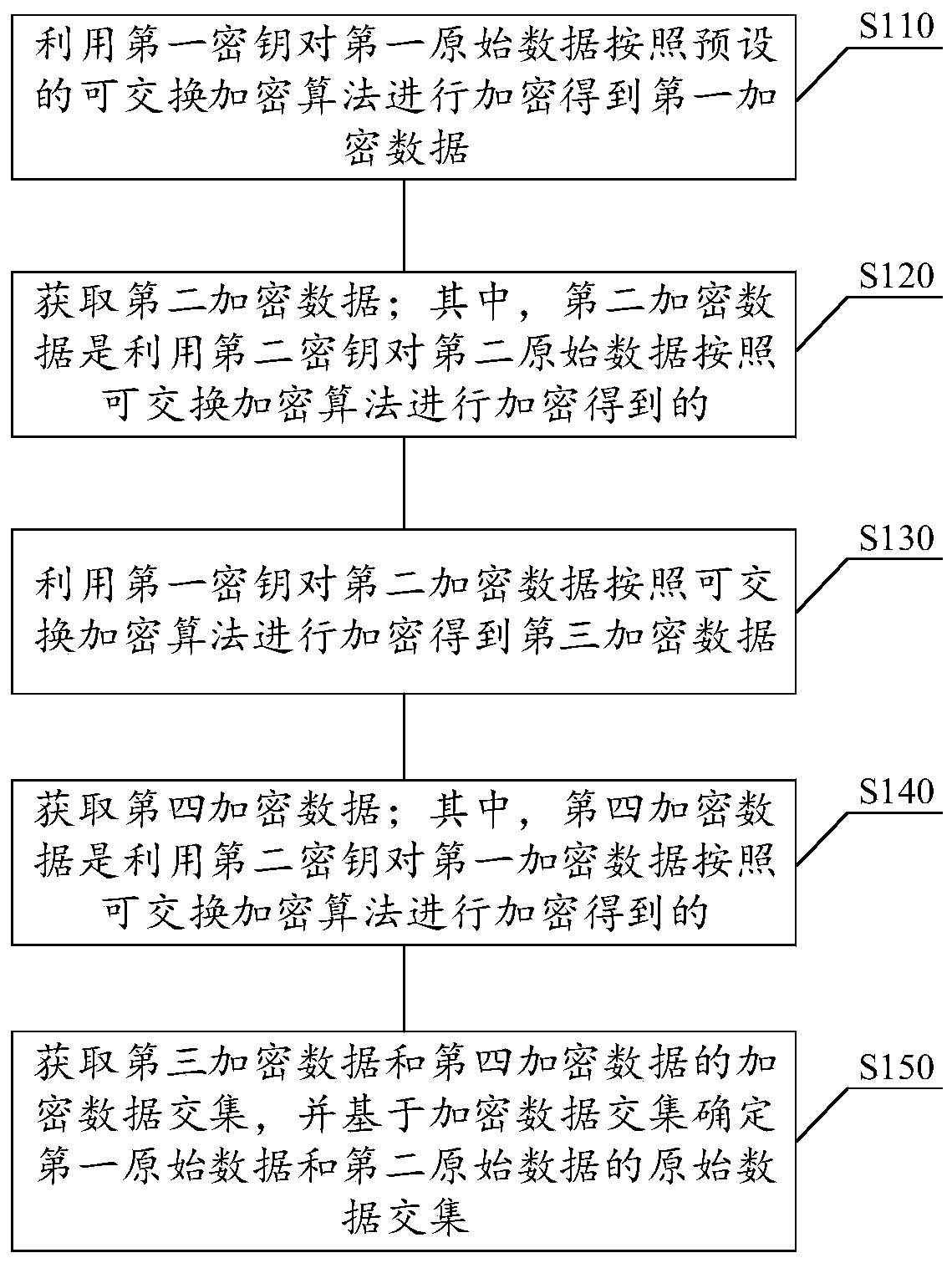
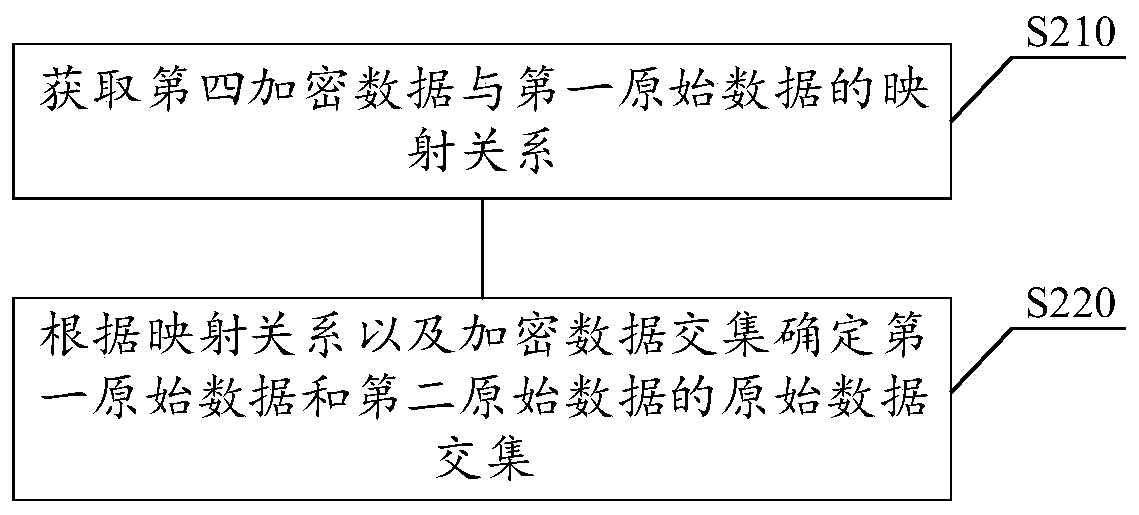
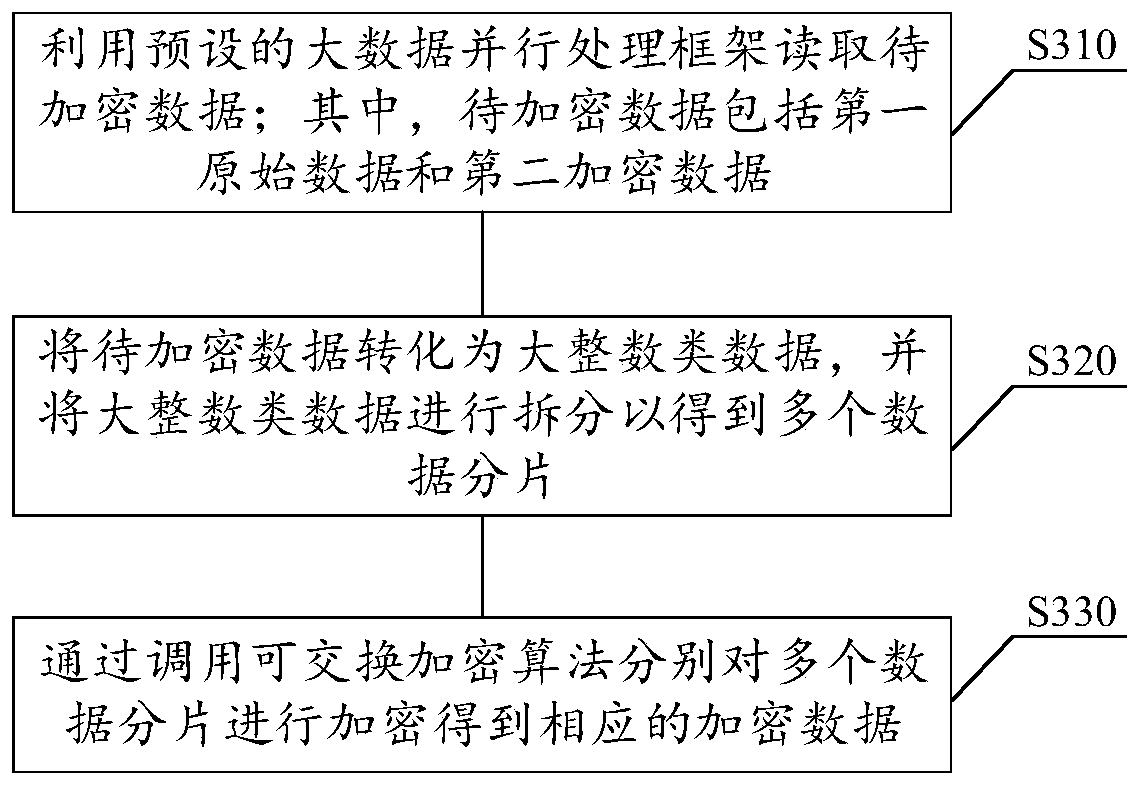
ActiveCN111555880AGuaranteed privacyEnsure safetyMultiple keys/algorithms usageDigital data protectionOriginal dataTheoretical computer science
The invention relates to the technical field of computers, in particular to a data collision method and device, a storage medium and electronic equipment. The method comprises the following steps: encrypting first original data by using a first key according to a preset exchangeable encryption algorithm to obtain first encrypted data; acquiring second encrypted data, wherein the second encrypted data is obtained by encrypting the second original data by using a second key according to an exchangeable encryption algorithm; encrypting the second encrypted data by using the first key according toan exchangeable encryption algorithm to obtain third encrypted data; acquiring fourth encrypted data, wherein the fourth encrypted data is obtained by encrypting the first encrypted data by using thesecond key according to an exchangeable encryption algorithm; and obtaining an encrypted data intersection of the third encrypted data and the fourth encrypted data, and determining an original dataintersection of the first original data and the second original data based on the encrypted data intersection. According to the method, data collision can be completed under the condition of protecting private data from being leaked.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
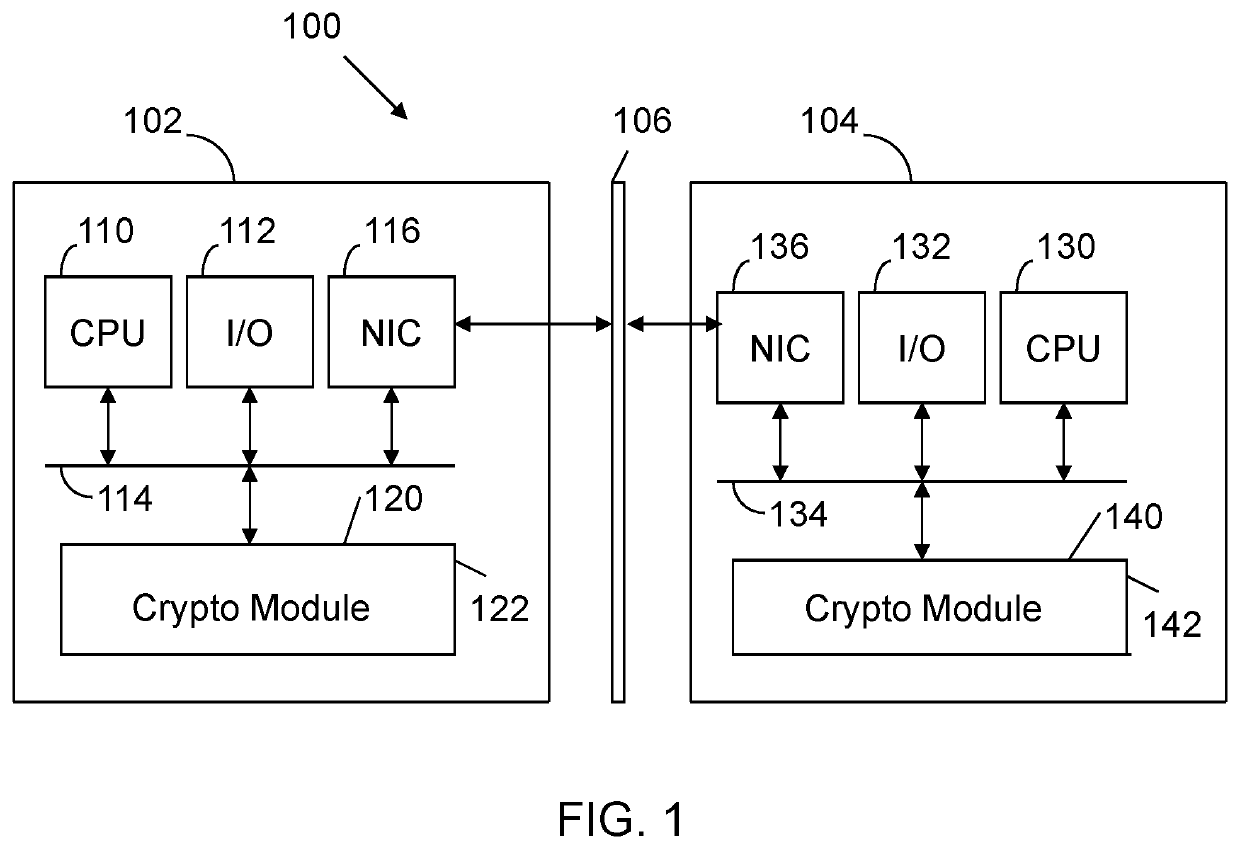
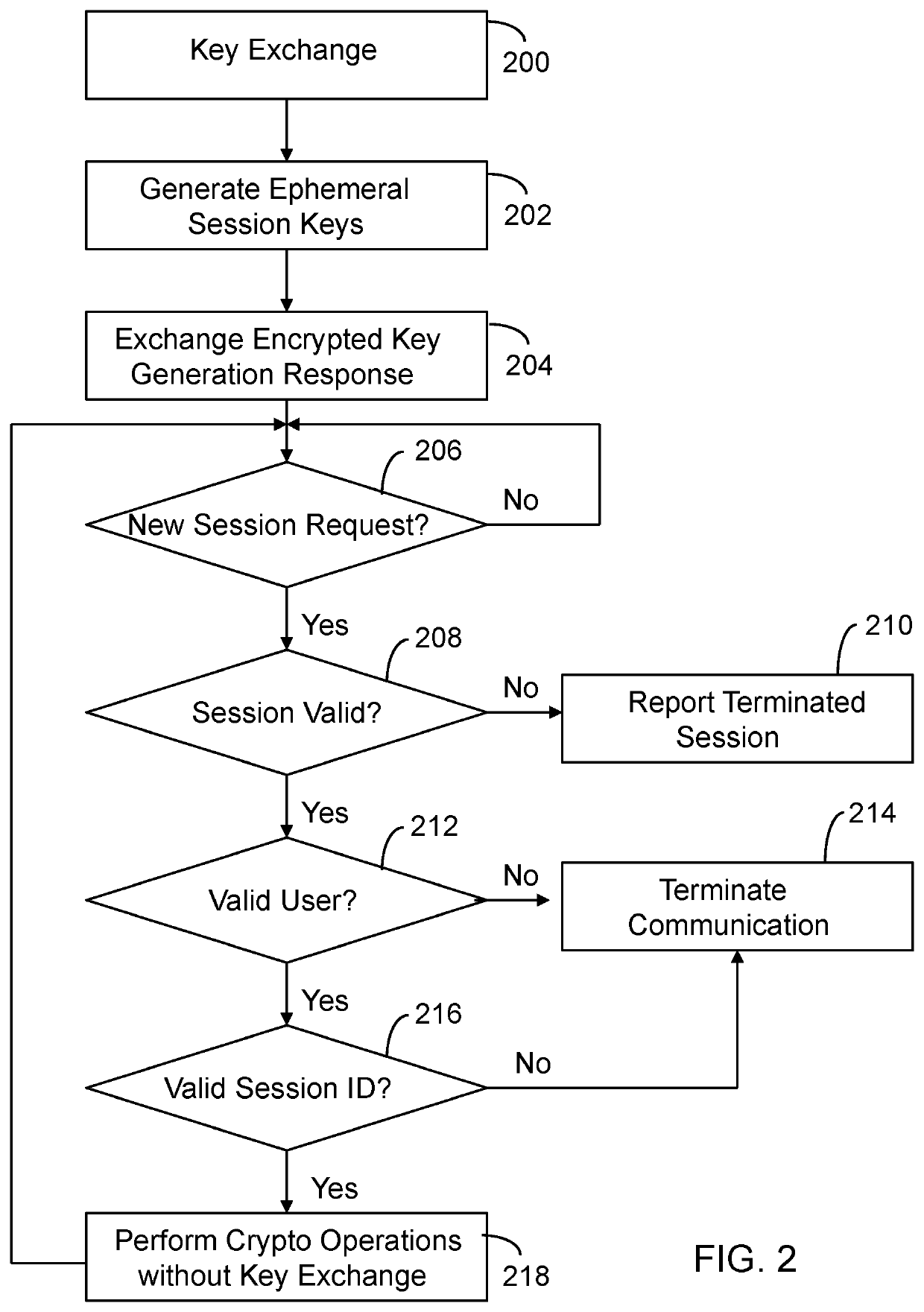
Apparatus and method for exchanging cryptographic information with reduced overhead and latency
ActiveUS10630466B1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesCommutative encryptionHuman–computer interaction
A method implemented by computers includes exchanging a key between a first user and a second user. Ephemeral session keys are generated. The ephemeral session keys are generated by a first computer associated with the first user and a second computer associated with the second user. An encrypted key generation response is exchanged between the first computer and the second computer. A new session request is received. It is determined that there is a valid session state. It is confirmed that there is a valid user. It is determined that there is a valid session identification. Information between the first computer and the second computer is cryptographically exchanged in response to the valid session state, the valid user and the valid session identification.
Owner:HOLOGRAM INC
Sending secure communications using a local ephemeral key pool
ActiveUS11082412B2Key distribution for secure communicationMultiple keys/algorithms usageSecure communicationInternet privacy
Owner:WICKR +1
Method for commutative encryption and watermarking on identical operation domain
InactiveCN102185843BAchieve seamless integrationAvoid exposureUser identity/authority verificationComputer hardwareMultiplexing
The invention relates to a method for commutative encryption and watermarking on an identical operation domain. An encryption technology and a digital watermarking technology are seamlessly combined to provide deeper comprehensive protection for multimedia data. In the method, orthogonal code division and separately encryption and watermarking operations are performed in an orthogonal commutationdomain by the principle of code division multiplexing in the field of communication, thereby realizing commutation between the encryption and watermarking operations; and simultaneously, encryption and watermarking operation results are superposed in the same data domain and displayed to a user under the control of orthogonal codes to realize the fusion of encryption and watermarking operation domains. In addition, related encryption operations and digital watermarking operations are not specially required, so a relatively larger space is ensured in specific algorithm designing. By the method, a commutative encryption and watermarking technology is realized on the identical operation domain, the encryption and watermarking operations can be conveniently performed at the same time, and relatively higher security and universality are ensured.
Owner:WUHAN UNIV
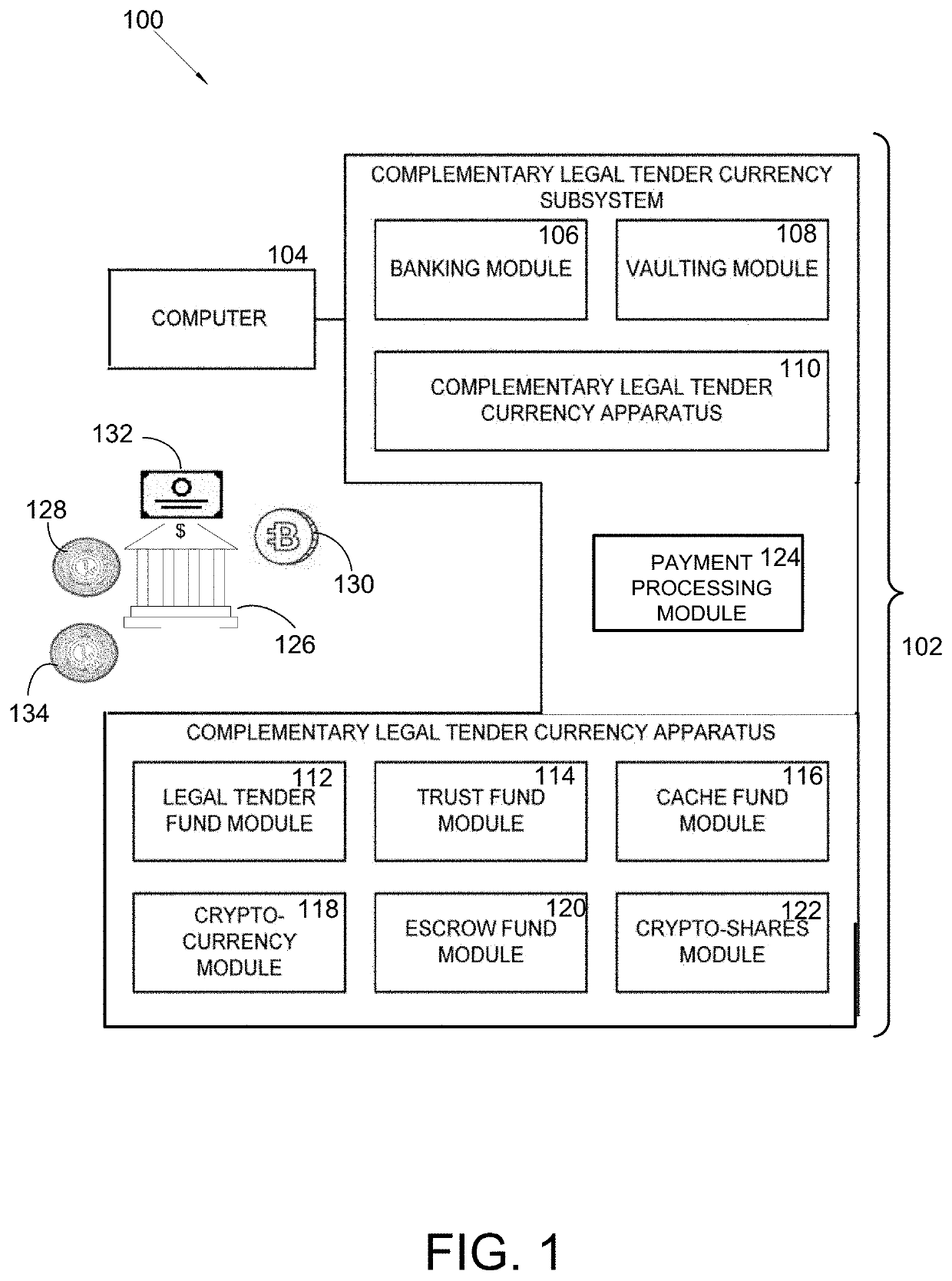
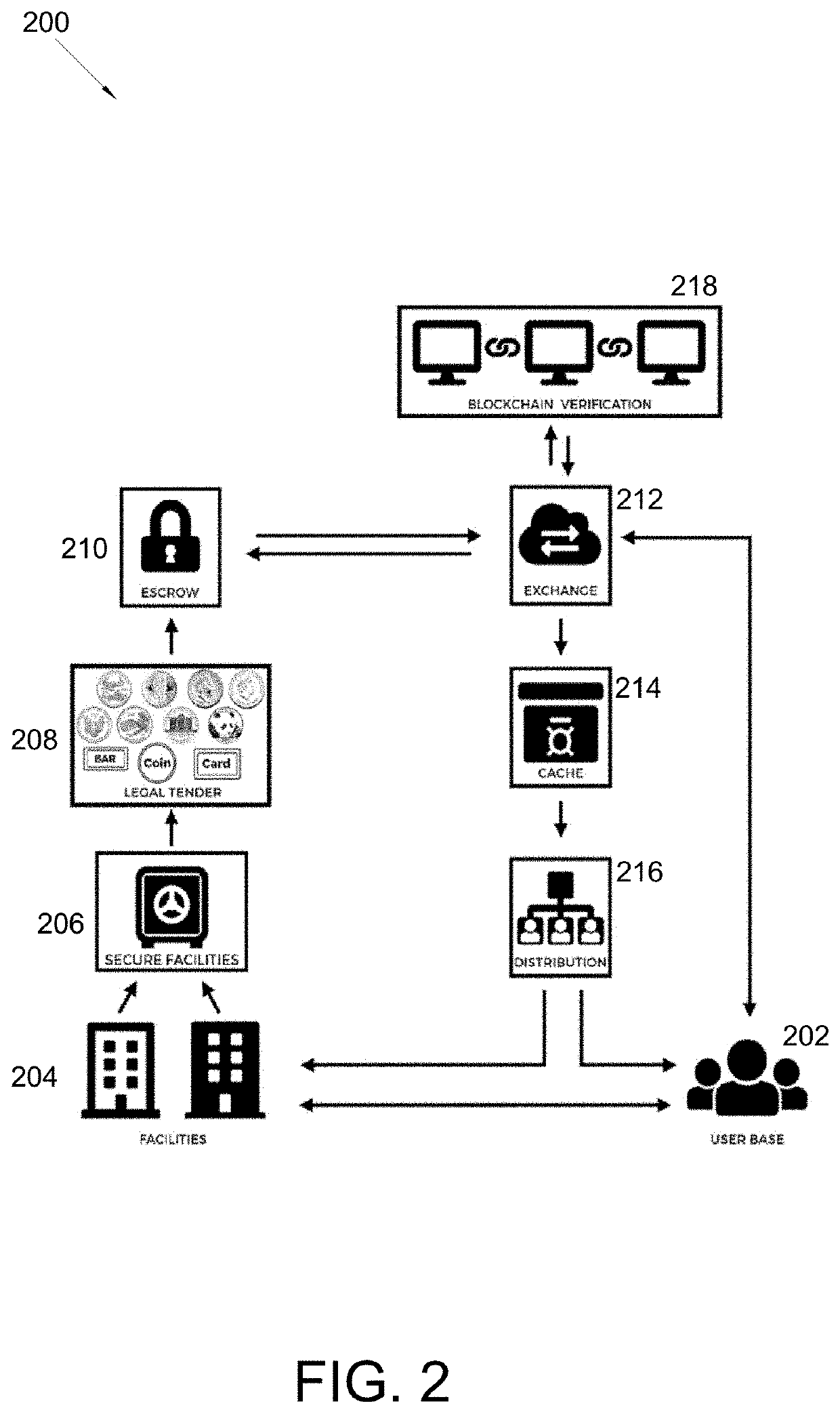
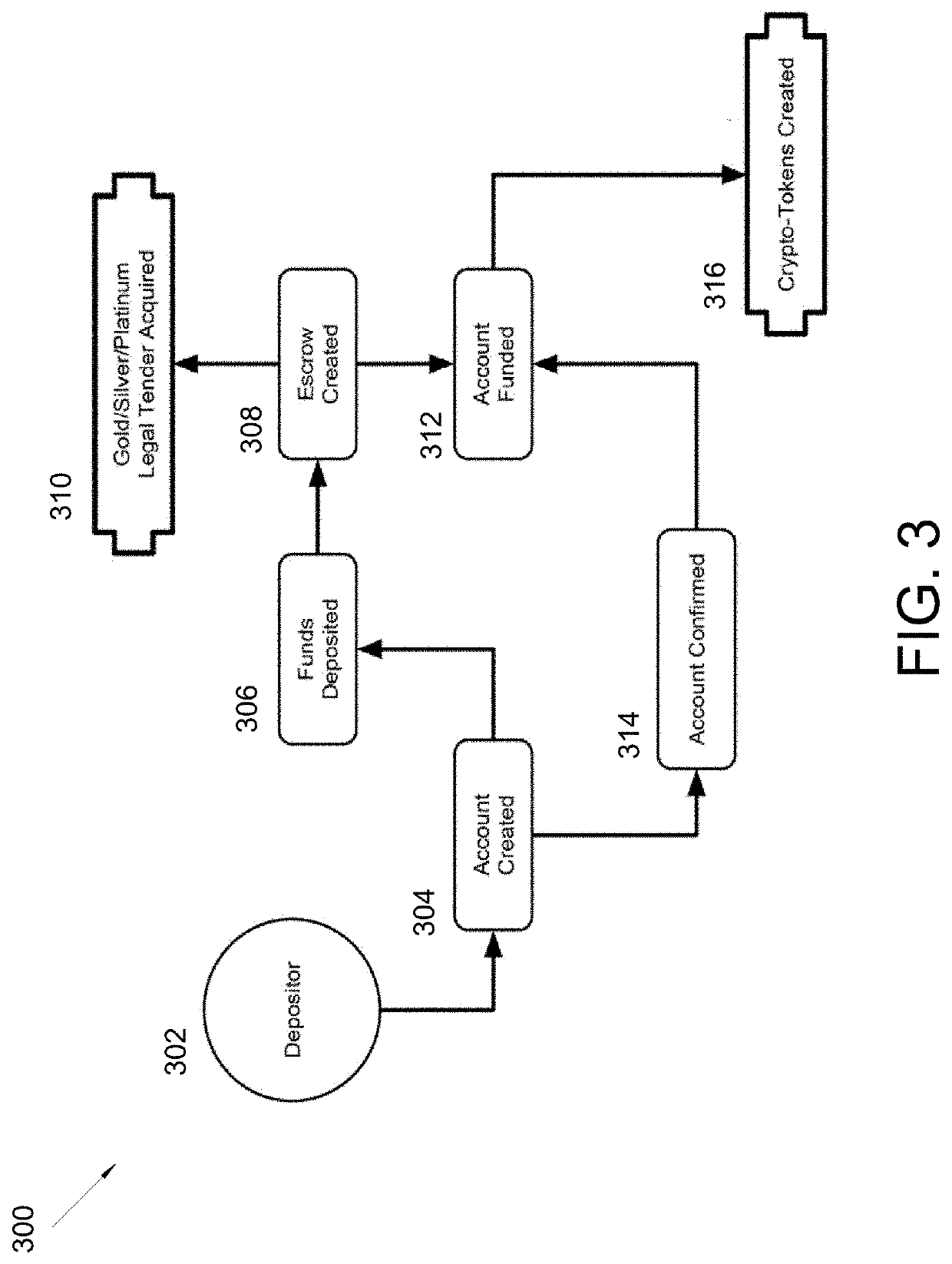
Method for Performing Transactions With Exchangeable Cryptocurrency and Legal Tender Currency
A system and method for performing transactions with exchangeable cryptocurrency and legal tender, and more particularly relates to system and method that utilizes a complementary legal tender currency subsystem for operating a banking module, a vaulting module, a legal tender fund module that has accounting information for complementary legal tender, a cache fund module, a crypto-currency module that has accounting information for virtual monetary tokens, a crypto-shares module that has accounting information for virtual share tokens, an escrow fund module, a trust fund module, a payment processing module, banking module, and vaulting module. The modules store, exchange, and maintain accounts for cryptocurrency and legal tender through a payment processing module. The payment processing module allows a customer and manger to transact for products and services through legal tender and cryptocurrency; and then generate revenue for the merchant through affiliate profits, trading the currencies for profit, and lower transaction fees.
Owner:HILTON LAWRENCE
Modeling and predicting method and device based on cross characteristics, equipment and storage medium
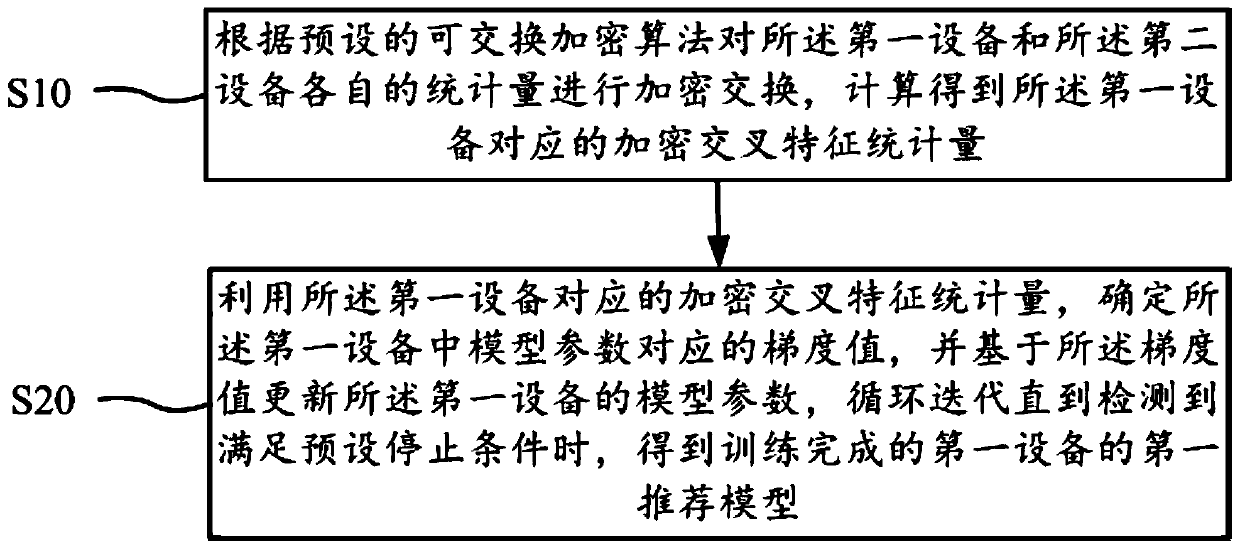
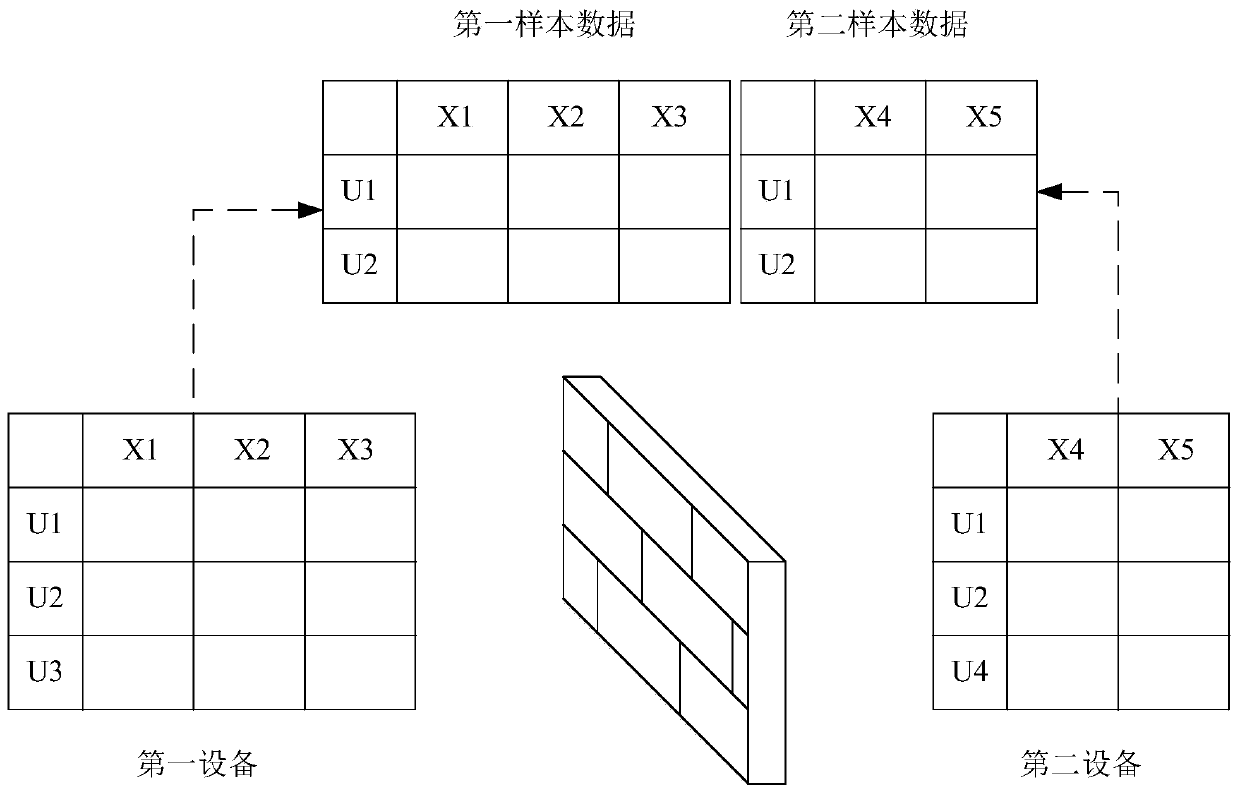
PendingCN111368314AIncreased complexityImprove recommendation prediction abilityEnsemble learningDigital data protectionRecommendation modelAlgorithm
The invention discloses a modeling and prediction method and device based on cross characteristics, equipment and a storage medium. The method comprises the following steps of: performing encryption exchange on respective statistics of the first device and the second device according to a preset exchangeable encryption algorithm, calculating to obtain encrypted cross feature statistics corresponding to the first device, and then determining a gradient value corresponding to a model parameter in the first device by using the encrypted cross feature statistics corresponding to the first device,updating the model parameter of the first device based on the gradient value, and performing loop iteration until a preset stop condition is detected to be satisfied to obtain a trained first recommendation model of the first device. Under the condition that the data is not local, the feature intersection between the feature components in the equipment and the feature intersection between the feature components between the equipment are completed at the same time, the complexity of the recommendation model is increased, and therefore the recommendation prediction capacity of the model is improved.
Owner:WEBANK (CHINA)
Facilitating communications using hybrid cryptography
ActiveUS10841086B2Key distribution for secure communicationMultiple keys/algorithms usageEngineeringCommutative encryption
Owner:AMAZON TECH INC +1
Private data intersection method and system for transmitting trace data by one party
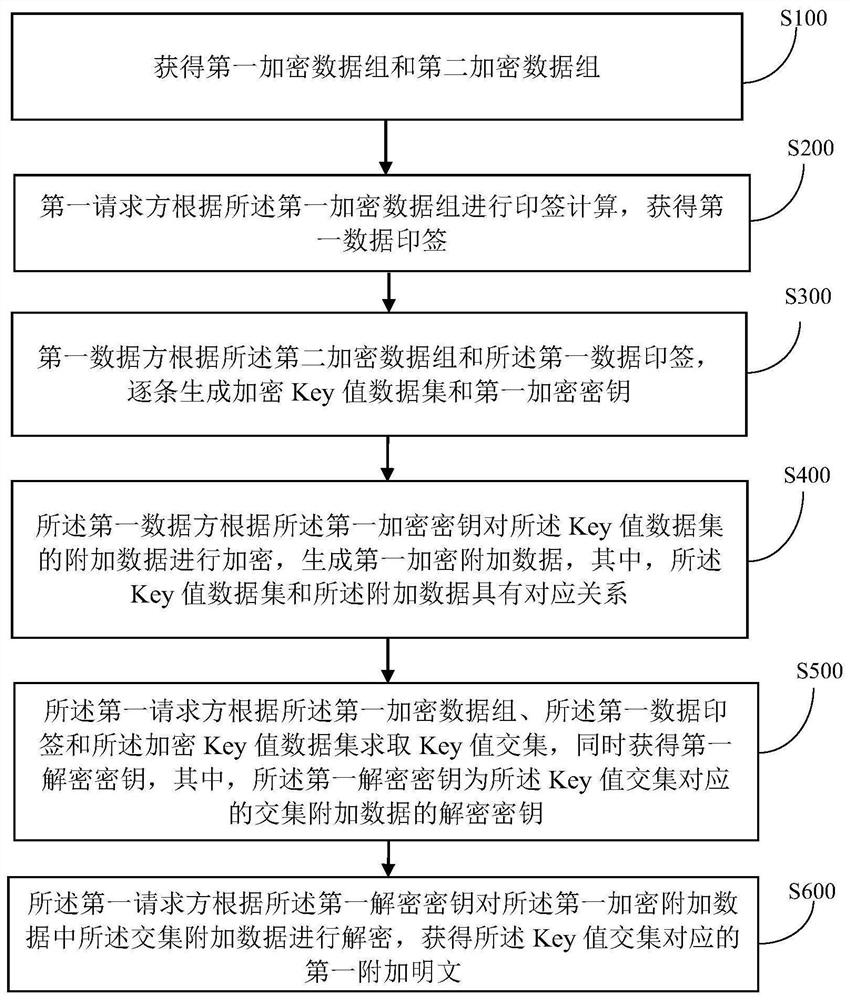
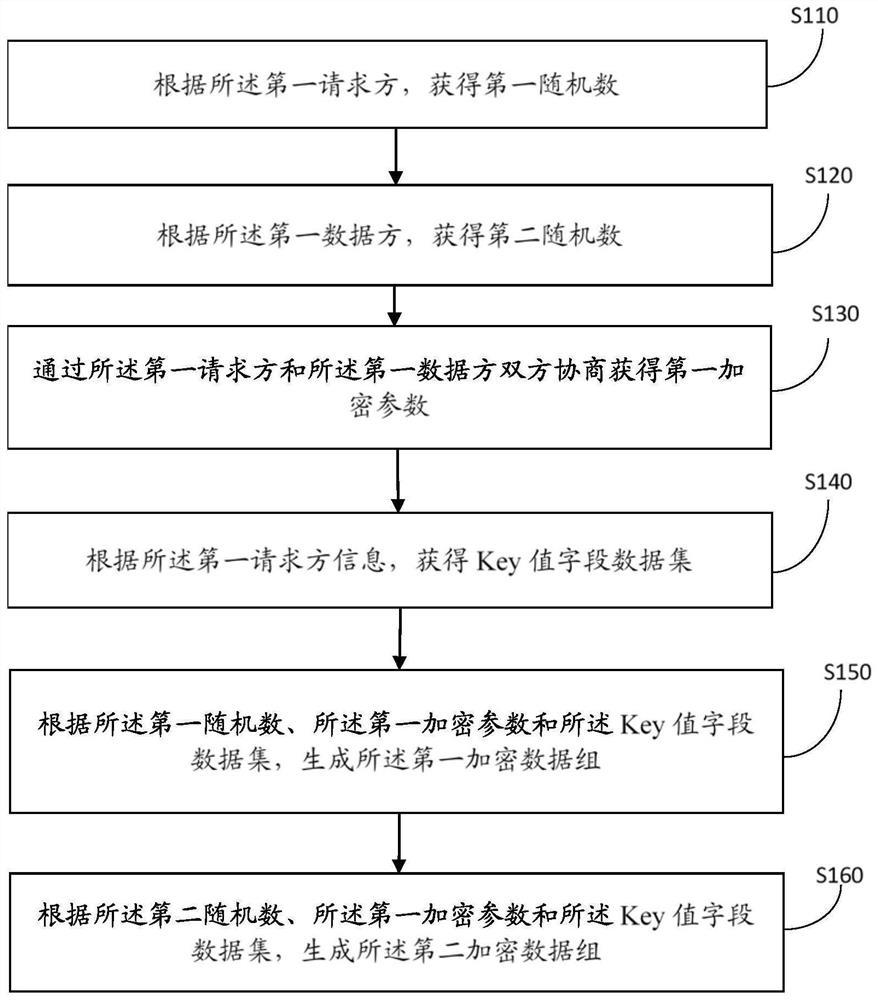
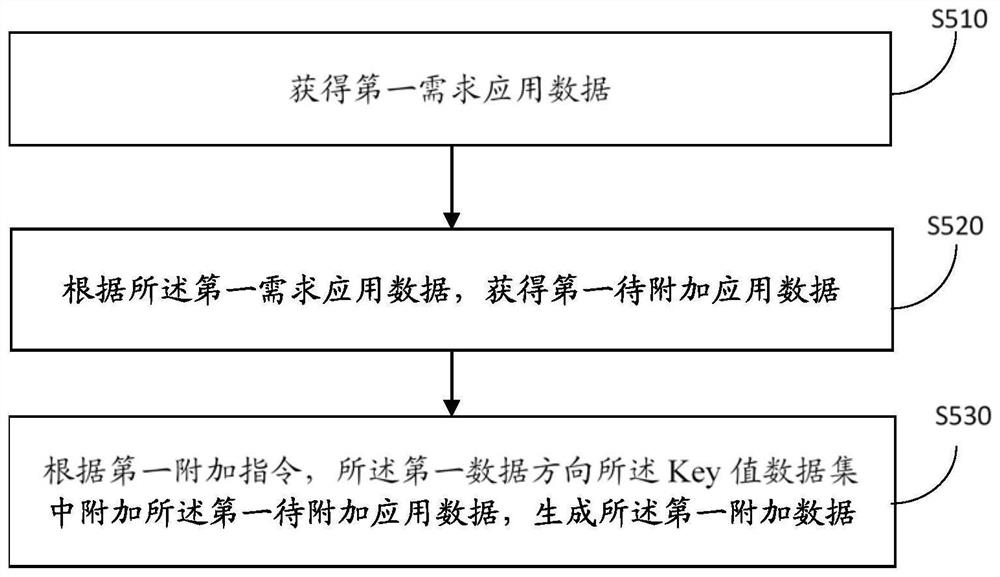
The invention discloses a privacy data intersection method and system for transmitting trace data by one party, and the method comprises the steps: generating an encryption Key value data set and a first encryption key one by one according to a second encryption data set and a first data stamp; encrypting additional data of the Key value data set to generate first encrypted additional data; solving a Key value intersection according to the first encrypted data set, the first data stamp and the encrypted Key value data set, and obtaining a first decryption key at the same time; and decrypting the intersection additional data in the first encrypted additional data according to the first decryption key to obtain a first additional plaintext corresponding to the Key value intersection. The technical problems that in the prior art, multiple times of communication and encrypted data exchange are needed in the intersection process, the requirements of some application scenes cannot be met, and data of intersection operation is limited to one field, and other meaningful application data cannot be attached are solved.
Owner:百融至信(北京)科技有限公司
Distributed privately subspaced blockchain data structures with secure access restriction management
ActiveUS20210350010A1Good synchronizationEasy transferEncryption apparatus with shift registers/memoriesUser identity/authority verificationEngineeringCommutative encryption
Disclosed herein is a system for providing a cryptographic platform for distributing data structures within a peer-to-peer network wherein encrypted messages are exchanged among nodes. The system provides for the creation and management of privately subspaced blockchains that include subspaces that are private, yet verifiable through the use of global state roots. The global state roots are updated based on subspace roots that are in term generated based on the data in that subspaces.
Owner:SCHVEY INC D B A AXONI
Encryption device, communication system and method of exchanging encrypted data in communication network
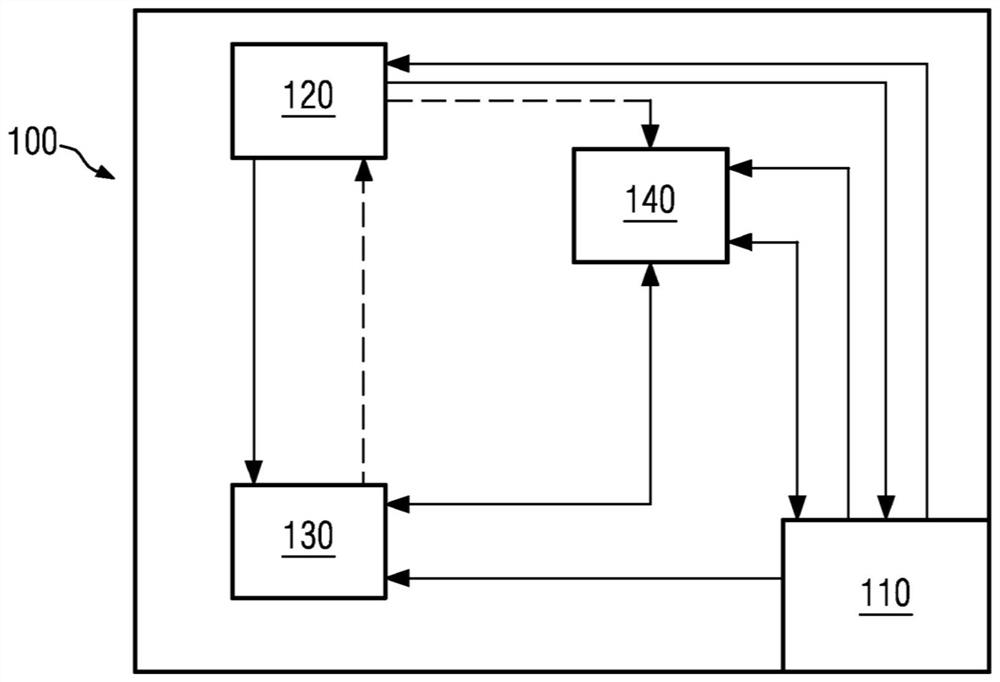
PendingCN112534790AKey distribution for secure communicationSynchronising transmission/receiving encryption devicesPlaintextCommunication interface
The present disclosure provides in various aspects an encryption device (100), a communication system and a method of exchanging encrypted data in such a network. In accordance with some illustrativeembodiments of an aspect, the encryption device (100) comprises a communication interface (110), a variable key generator (120) configured to generate at least two keys, a memory (130) configured to store keys that are either generated by the variable key generator (120) and / or received at the communication interface (110), and an encryption / decryption component (140) configured to successively use keys stored in the memory (130) for encrypting a plaintext received at the communication interface (110) and for decrypting a ciphertext received at the communication interface (110), wherein the communication interface (110) is configured to communicate with an associated separate communication device which is used by a user of the encryption device (100) for communicating in a communication network.
Owner:LINXENS HLDG SAS
Access authentication method of IMS network
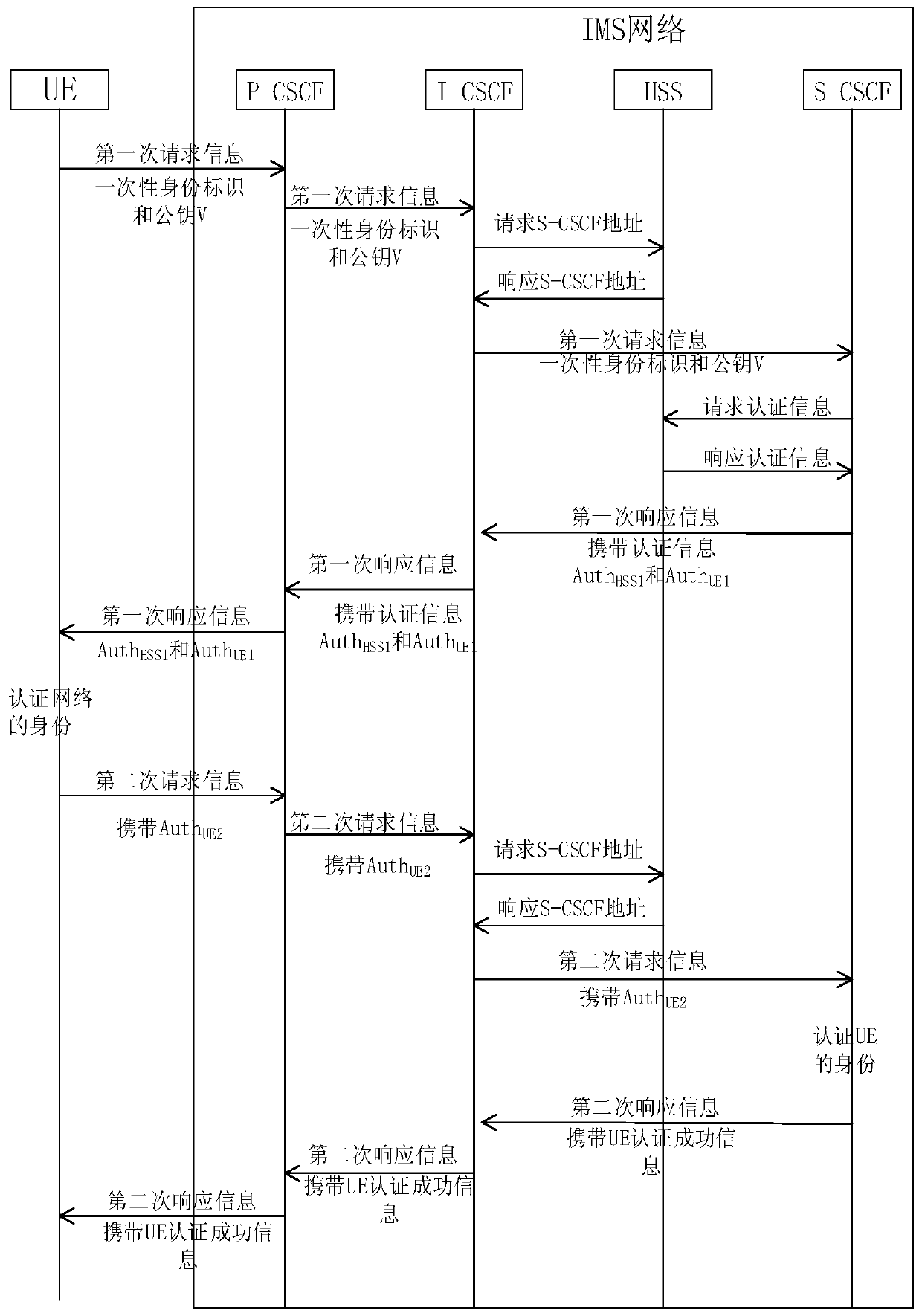
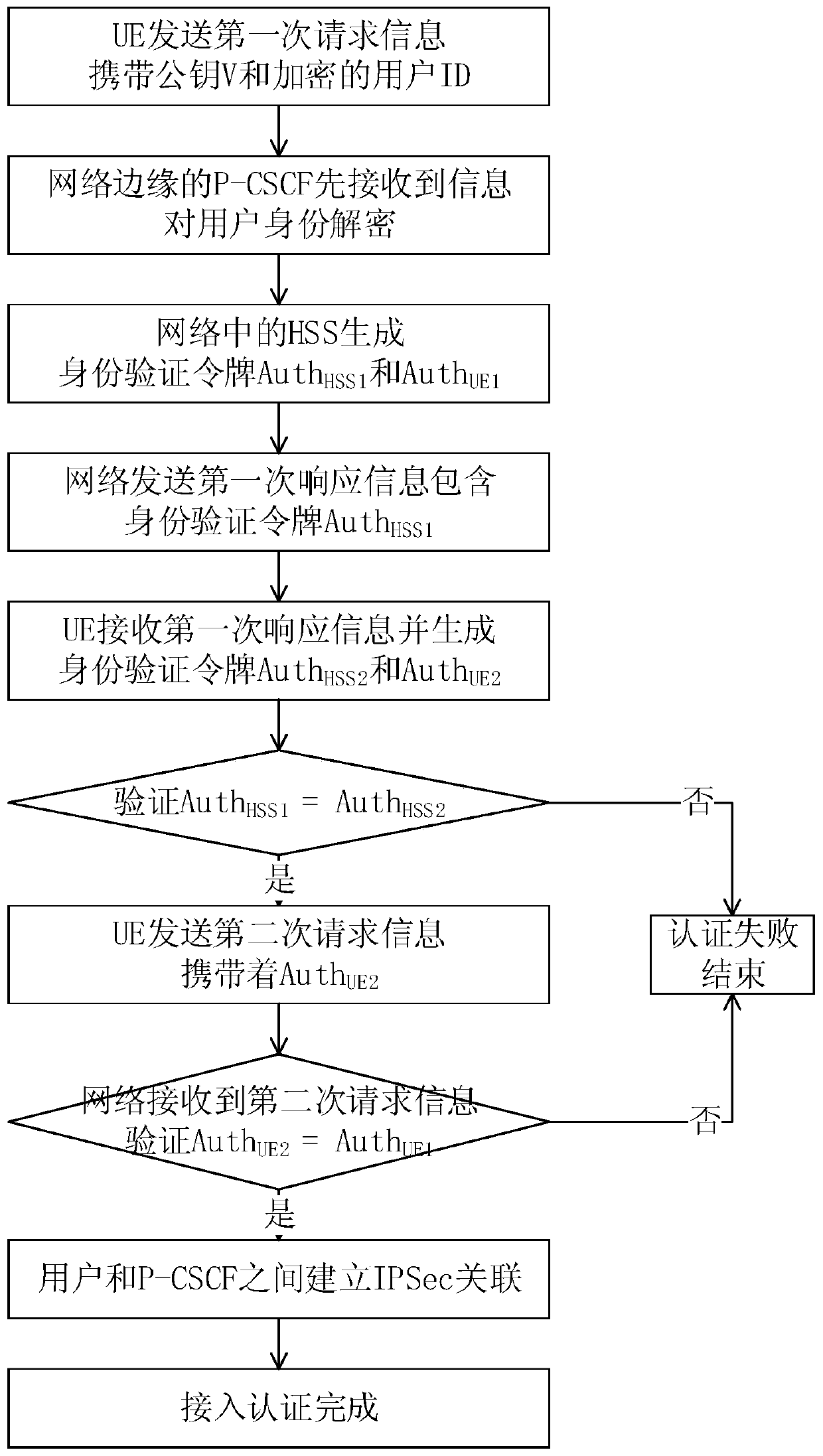
PendingCN110933673AReduce lossThe parameters are simplePublic key for secure communicationUser identity/authority verificationConfidentialityIPsec
The invention discloses an access authentication method of an IMS network. The method comprises: encrypting a user identity, performing dual encryption on a user ID through an exchange encryption function according to a random key generated by UE and a random key generated by a P-CSCF in a network, and decrypting the P-CSCF after entering the network, thereby avoiding leakage of a real identity ofthe user; performing identity authentication between the UE and the network through identity authentication tokens generated by the UE and the network respectively, so that parameters carried in information during identity authentication are simplified; and establishing IPSec association between the UE and the P-CSCF, and adopting a session key in a bidirectional identity authentication process to generate a negotiation key, so that the confidentiality and integrity of data transmitted between the UE and the P-CSCF are ensured.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +3
Apparatus and method with enhanced security and reduced trust requirements for quantum key distribution
ActiveCN106899403BQuantum computersKey distribution for secure communicationQuantum channelComputational physics
A QKD system for securely exchanging encryption keys between a transmitter (100) and a receiver (200) modified to accept additional customization parameters. The QKD system consists of a QKD transmitter (120) and a QKD receiver (220) capable of implementing multiple QKD protocols forming a protocol family. The QKD transmitter (120) and receiver (220) connected by a quantum channel (500) consist of optical and electronic components suitable for generating and detecting qubit streams. The qubits (520) exchanged on the quantum channel (500) are grouped into blocks (510) of at least one qubit and of length Li (511). For each block (510) of qubits (520), one of the QKD protocols (530) selected from the family of protocols that can be implemented using the transmitter (100) and transmitter (200) is used.
Owner:ID QUANTUM TECH
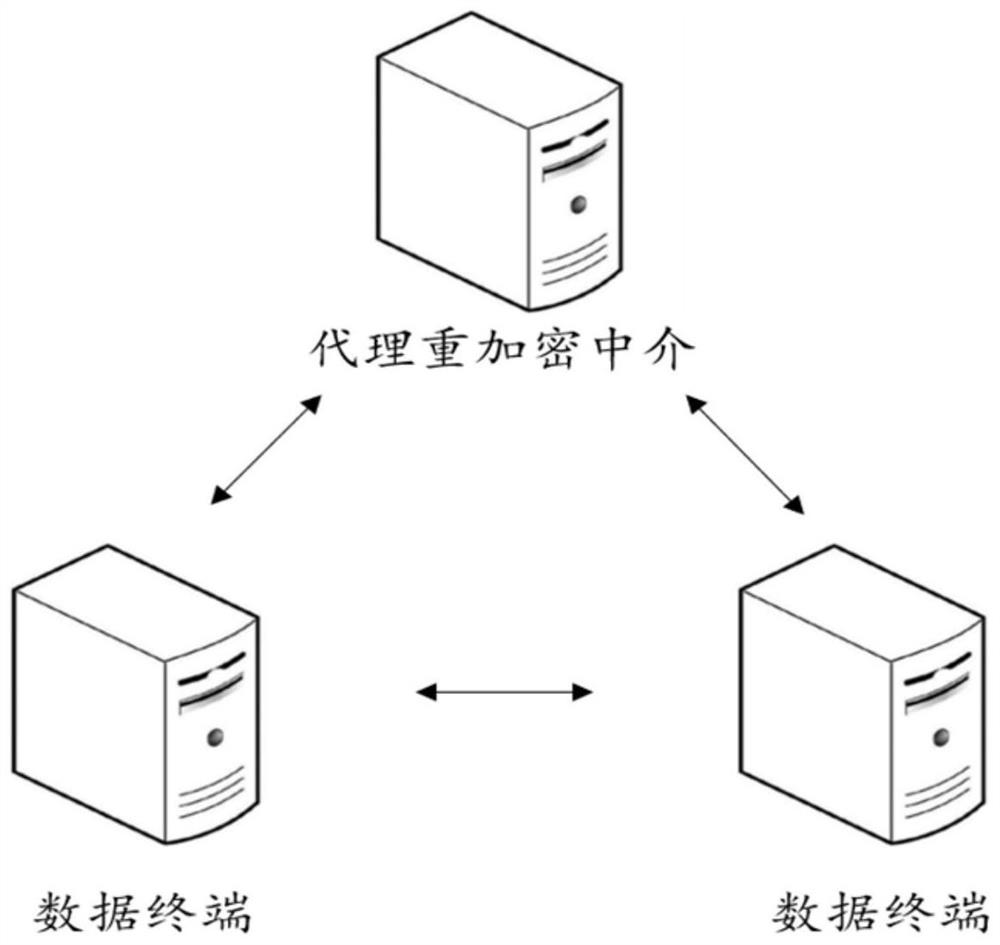
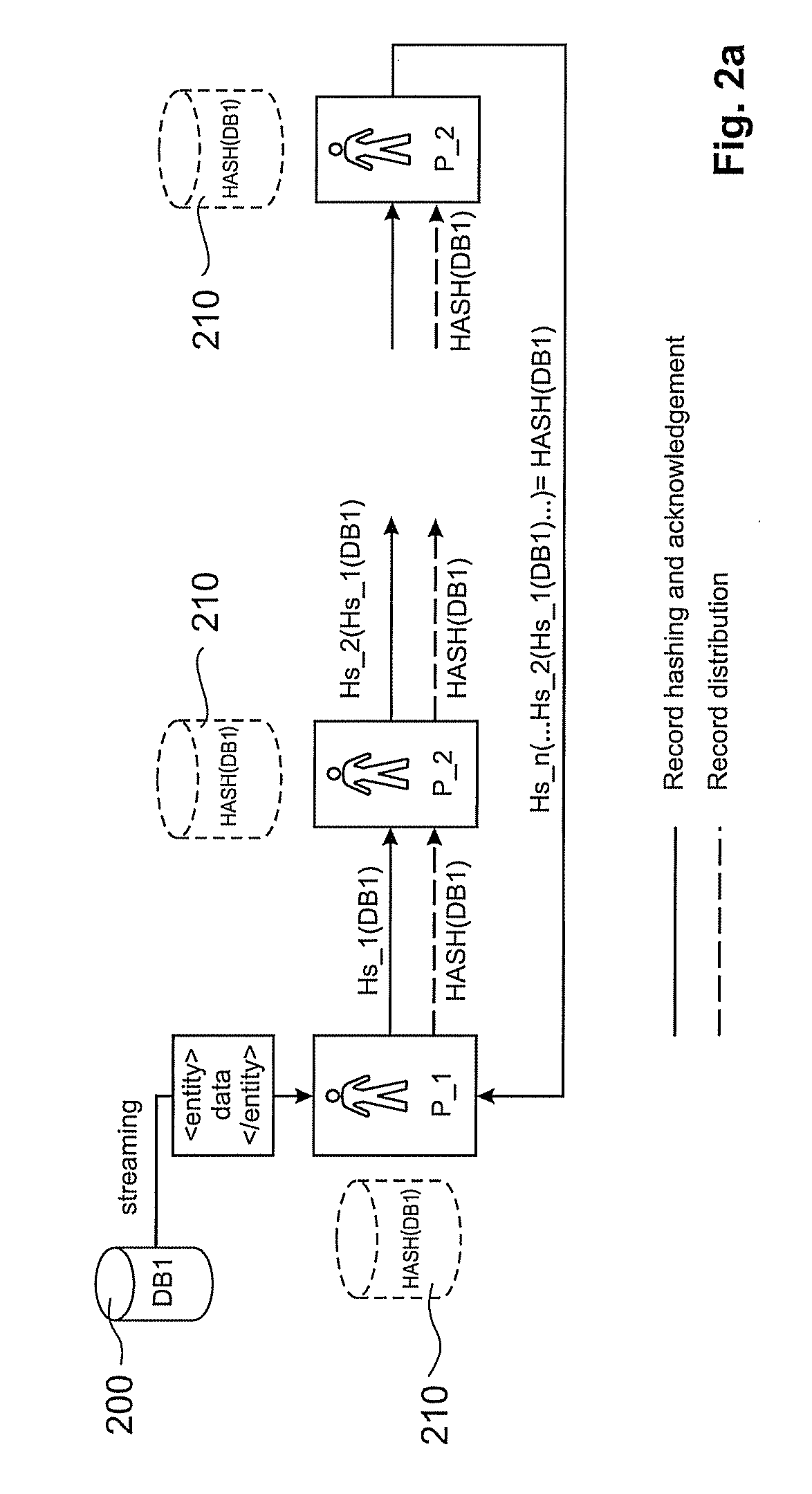
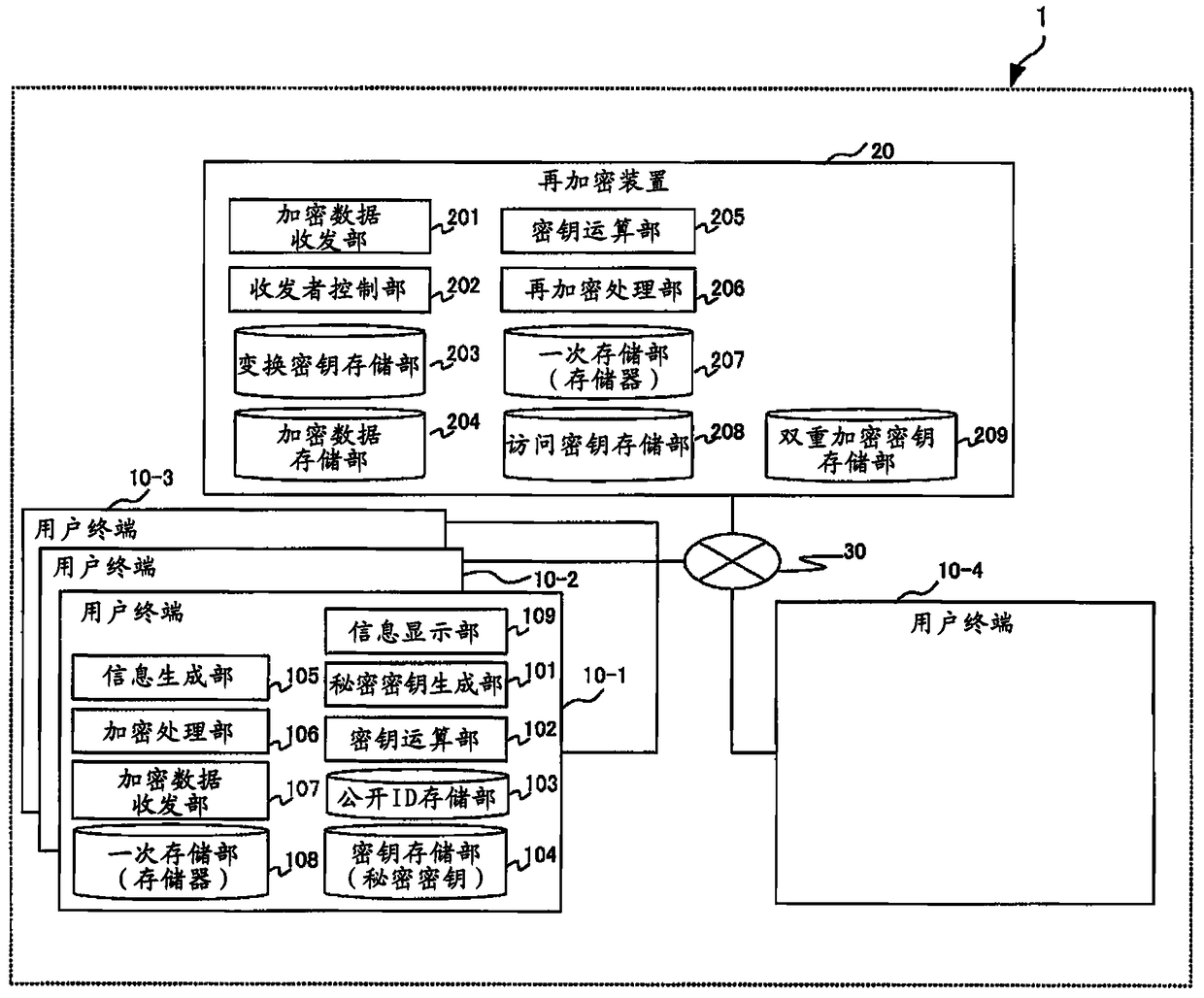
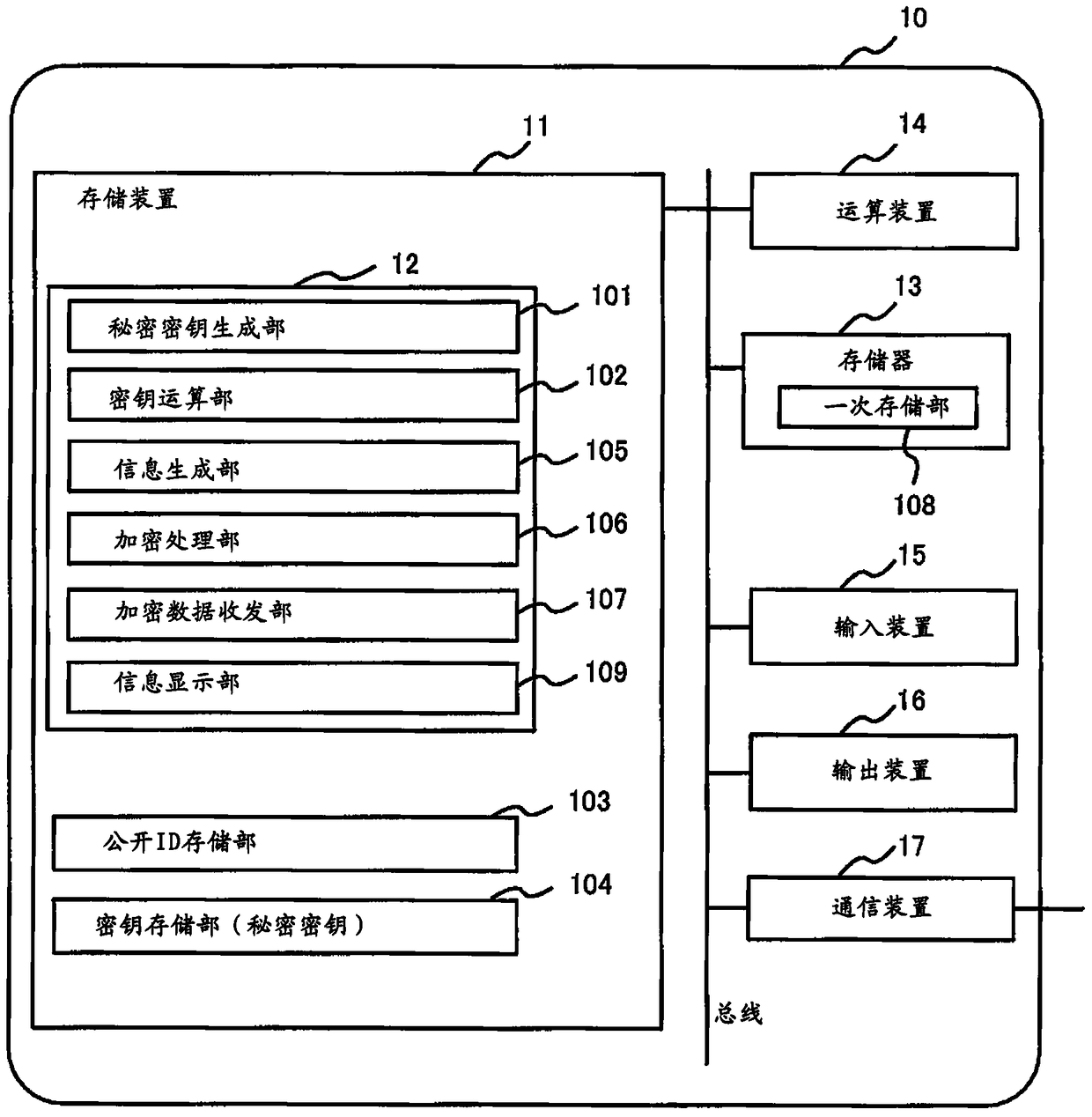
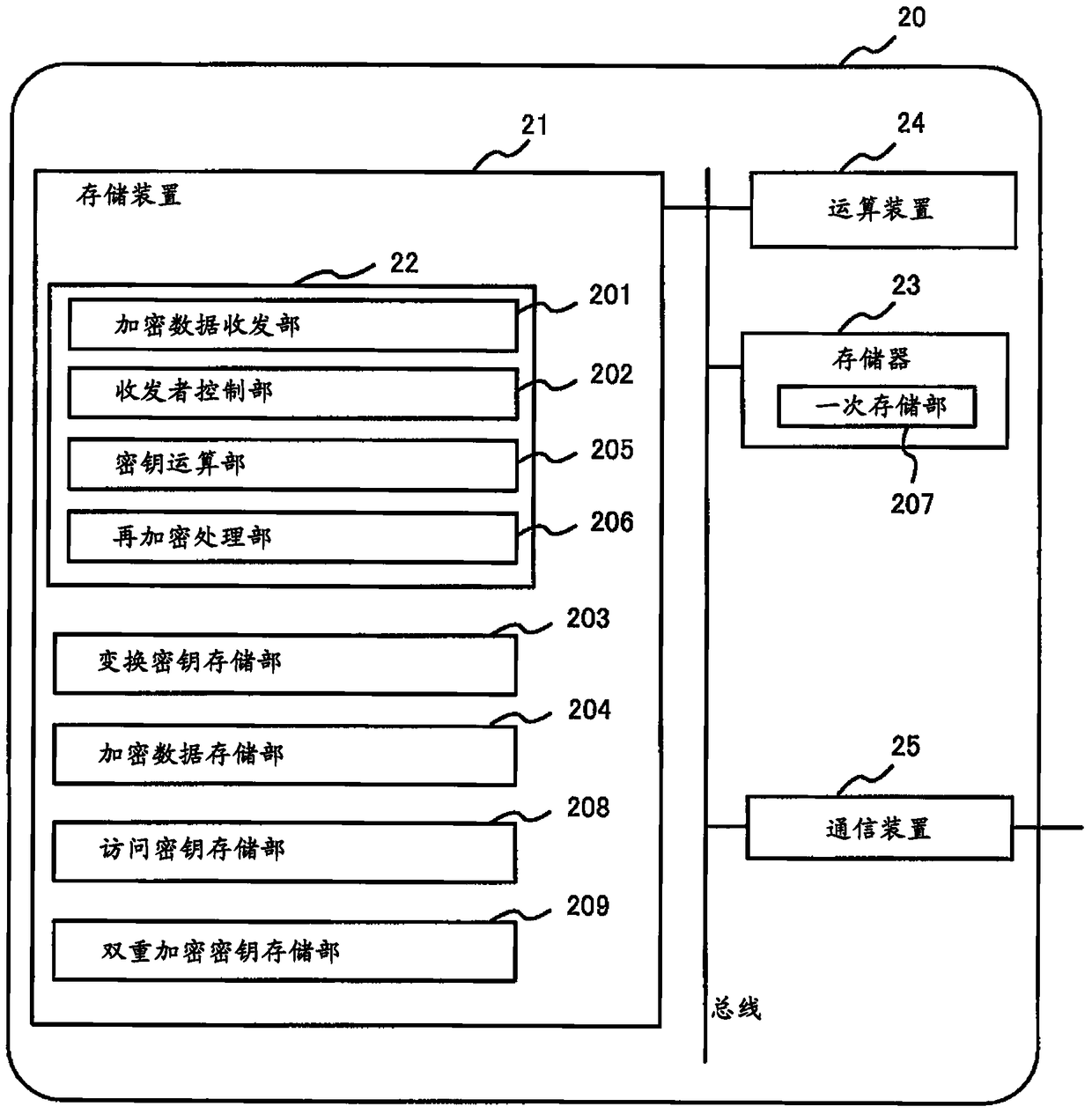
Re-encryption method, re-encryption system and re-encryption device
The invention provides a re-encryption method, a re-encryption system and a re-encryption device. The re-encryption system (1) comprise the re-encryption device (20) which receives first encryption data obtained by a first encryption secret key of a data manufacturer from a user terminal of the data manufacturer, receives second encryption data and third encryption data obtained by encryption on the first encryption secret key and predetermined data generated from the first encryption secret key through a predetermined algorithm respectively through commutative encryption algorithms and is capable of using a decryption secret key of a user having a browsing authority to carry out re-encryption on the second encryption data and the third encryption data in a decryption manner; and a user terminal (10) which obtained the first encryption data and the re-encrypted second encryption data and third encryption data from the re-encryption device (20), decodes the first encryption secret key from the re-encrypted second encryption data through a decryption secret key of itself, and decrypts the first encryption data through the first encryption secret key so as to output a plaintext.
Owner:HITACHI LTD
A secure communication method based on an intelligent door lock system and its intelligent door lock system
ActiveCN107038777BEnsure safetyIndividual entry/exit registersShort range communication serviceSecure communicationTamper resistance
The invention discloses a safe communication method based on an intelligent door lock system, which belongs to the technical field of intelligent home and security protection. The smart door lock system includes a smart door lock, and a mobile terminal is remotely connected to a cloud server. The method includes: connecting the smart door lock and the mobile terminal through a preset secure communication channel and exchanging encryption keys; The data is transmitted and encrypted with the encryption key using a preset encryption algorithm to obtain encrypted data; the sender sends the encrypted data with a unique identifier to the receiver through the cloud server; the receiver authenticates the encrypted data with a unique identifier , to process encrypted data based on authentication results. In the method of this application, since the server does not save any keys, the server cannot understand the data forwarded by it. Even if the server is compromised, the data encryption, identity verification, anti-replay and anti-tampering in the communication between the smart door lock and the mobile terminal are still valid , ensuring data security.
Owner:YUNDING NETWORK TECH BEIJING
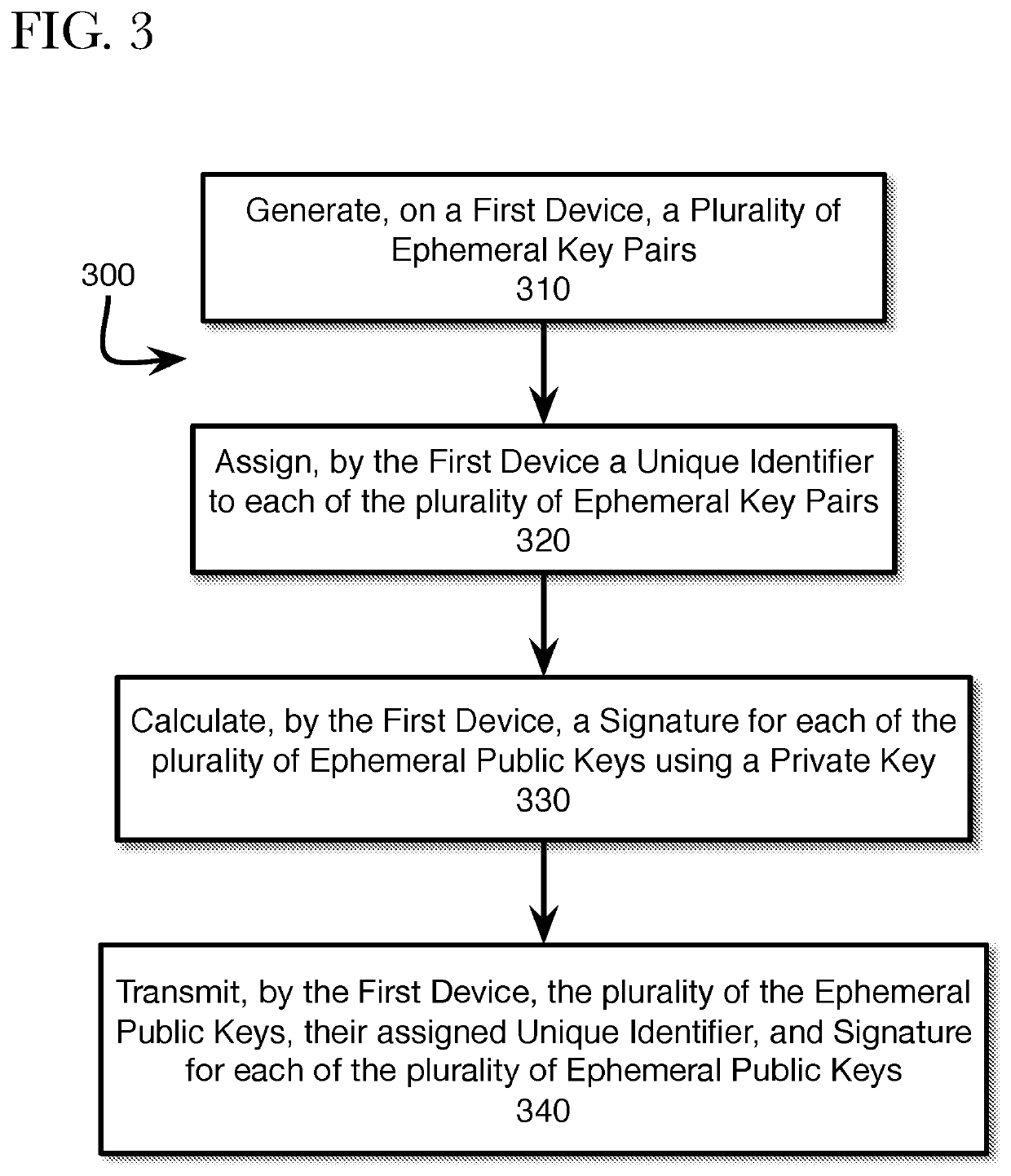
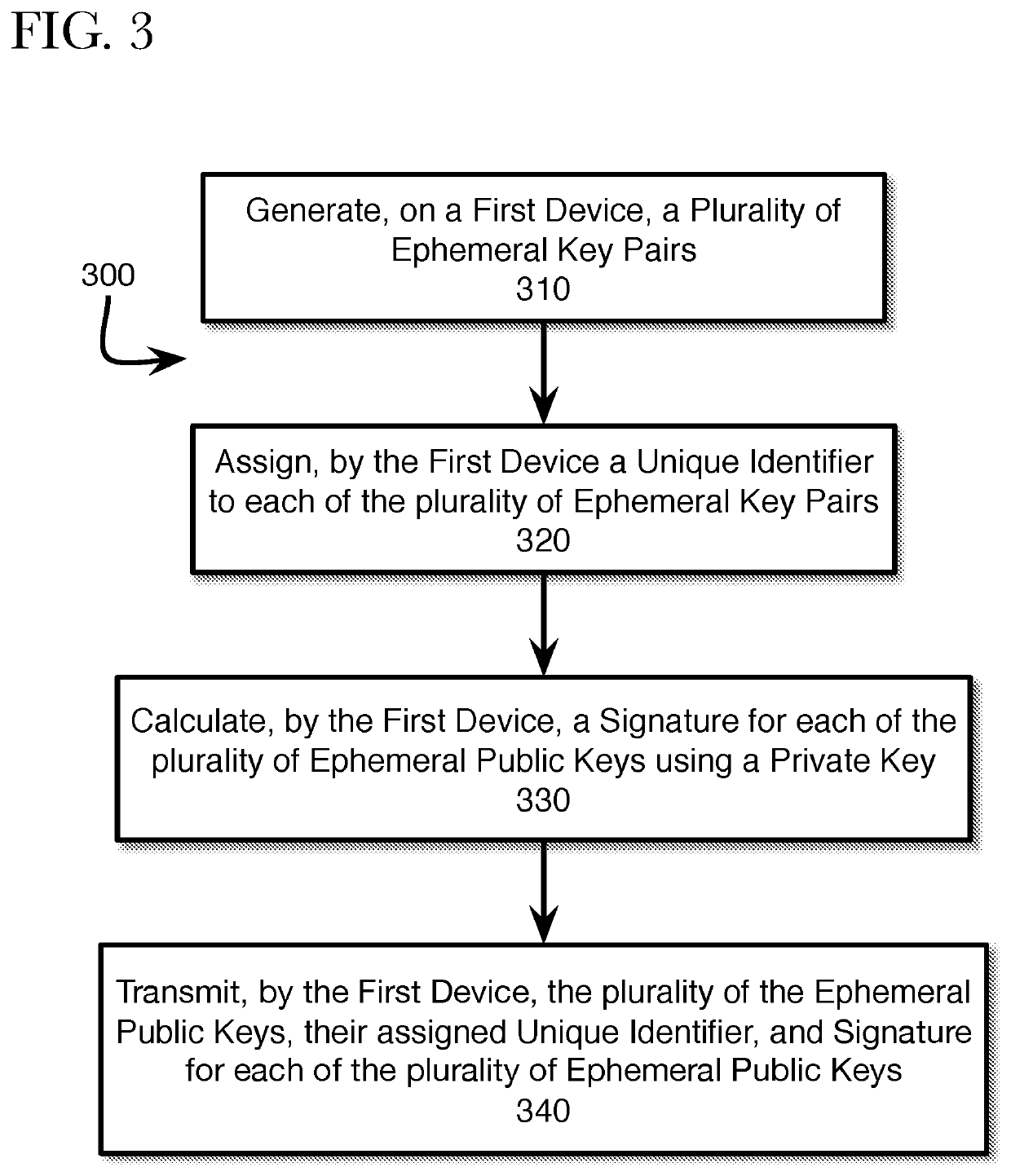
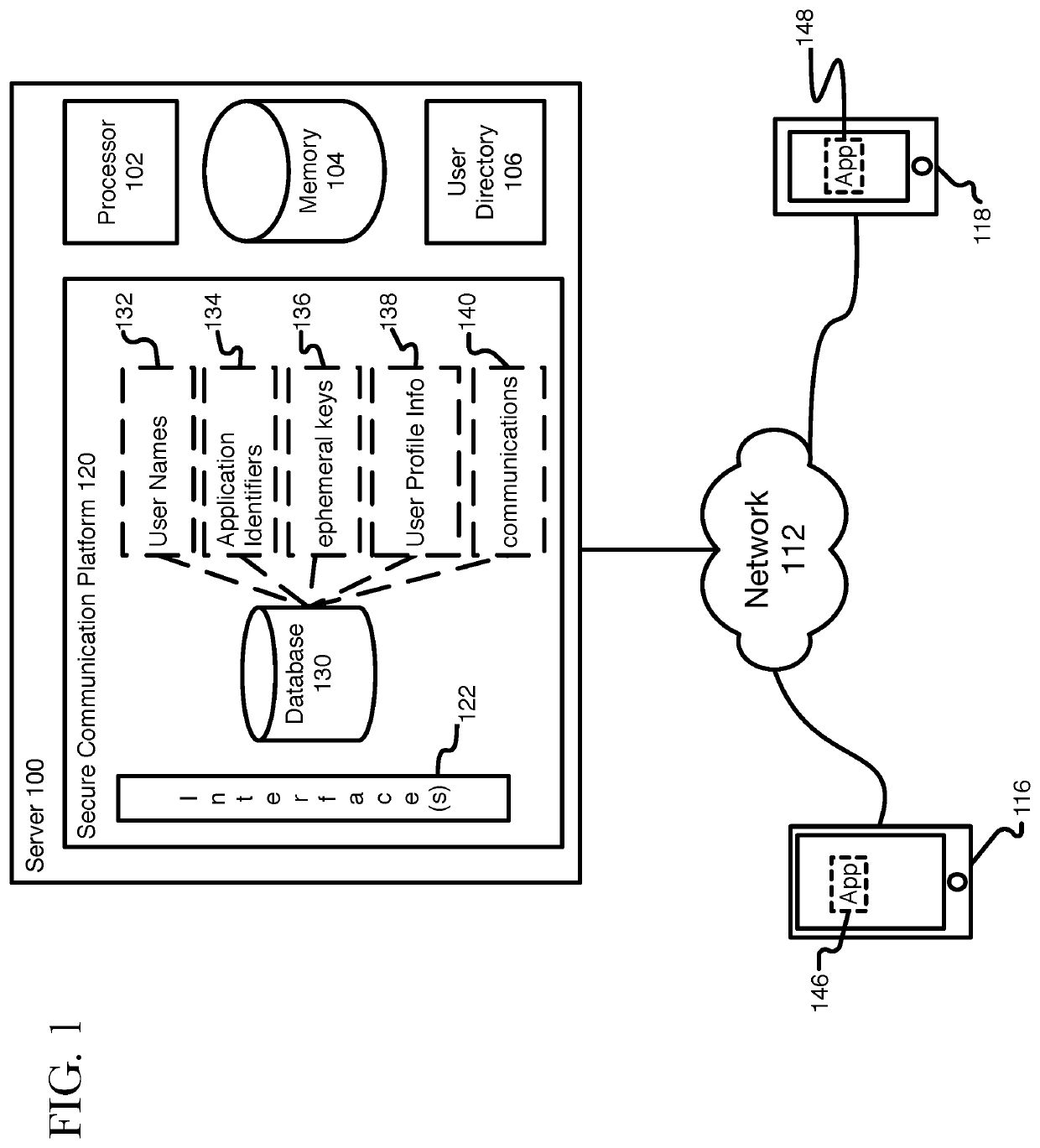
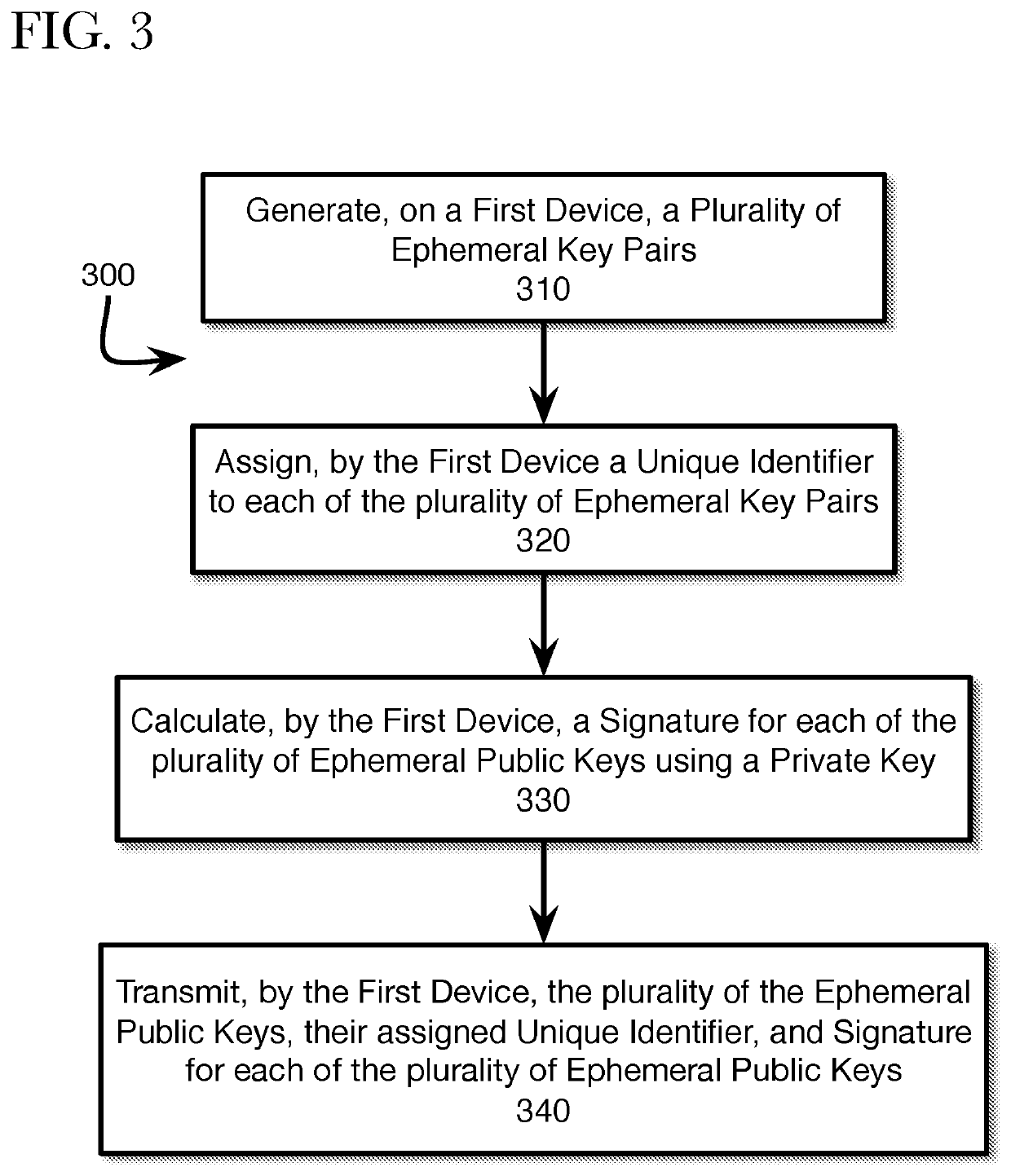
Generating ephemeral key pools for sending and receiving secure communications
ActiveUS11316666B2Key distribution for secure communicationMultiple keys/algorithms usageSecure communicationInternet privacy
A method, system, and non-transitory computer readable medium are described for providing a sender a plurality of ephemeral keys such that a sender and receiver can exchange encrypted communications. Accordingly, a sender may retrieve information, such as a public key and a key identifier, for the first receiver from a local storage. The retrieved information may be used to generate a key-encrypting key that is used to generate a random communication encryption key. The random communication encryption key is used to encrypt a communication, while the key-encrypting key encrypts the random communication key. The encrypted communication and the encrypted random communication key are transmitted to the first receiver.
Owner:AMAZON TECH INC +1
Encryption-based Wireless Unlocking Method
ActiveCN109448182BAuthorization is controllableEnsure safetyIndividual entry/exit registersSecurity arrangementInternet privacyWireless data
Owner:广州创想云科技有限公司
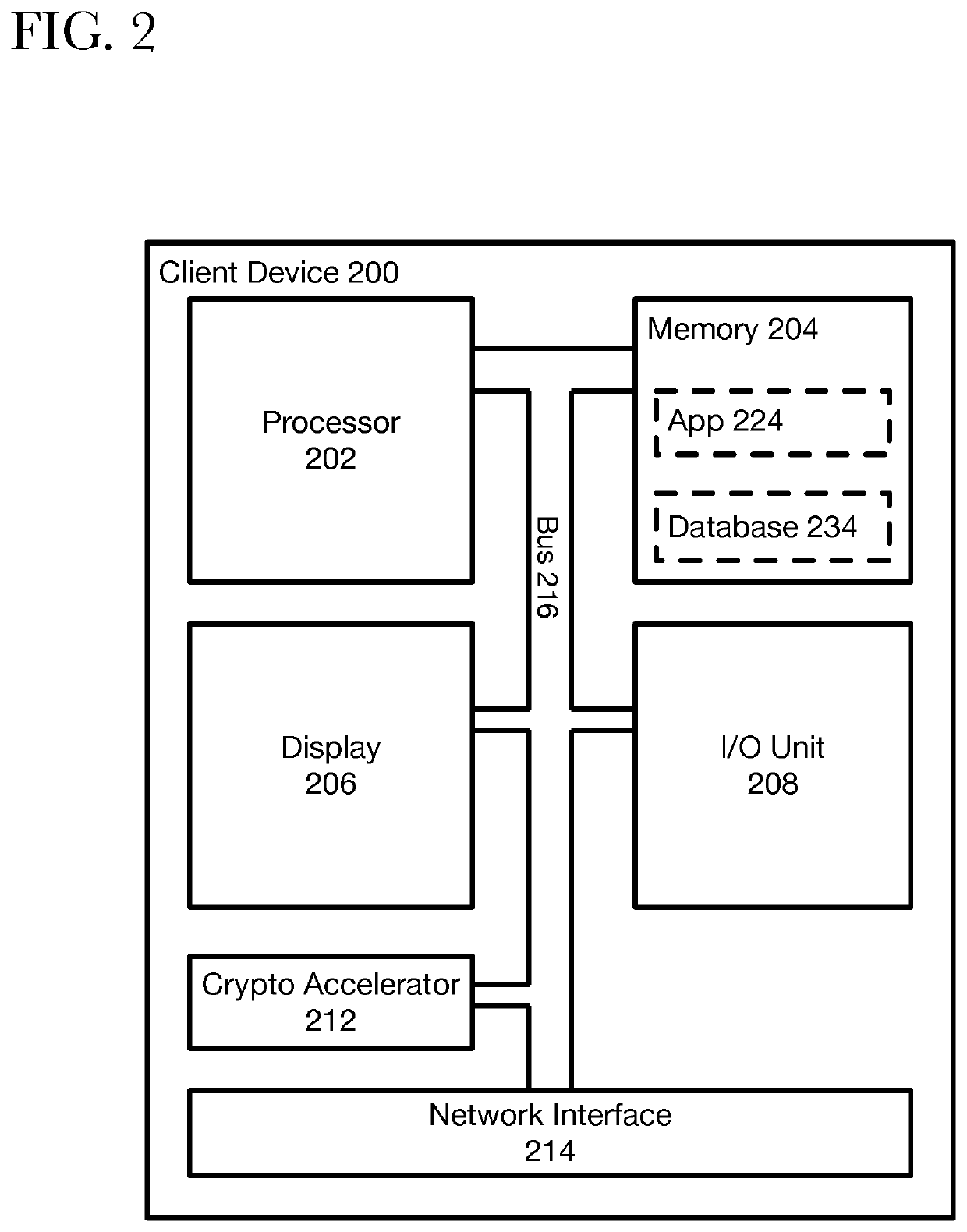
Provisioning ephemeral key pools for sending and receiving secure communications
ActiveUS10715504B2Key distribution for secure communicationMultiple keys/algorithms usageSecure communicationInternet privacy
A method, system, and non-transitory computer readable medium are described for providing a sender a plurality of ephemeral keys such that a sender and receiver can exchange encrypted communications. Accordingly, a sender may retrieve information, such as a public key and a key identifier, for the first receiver from a local storage. The retrieved information may be used to generate a key-encrypting key that is used to generate a random communication encryption key. The random communication encryption key is used to encrypt a communication, while the key-encrypting key encrypts the random communication key. The encrypted communication and the encrypted random communication key are transmitted to the first receiver.
Owner:AMAZON TECH INC +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com