Trust management method based on nested game in center base cognitive wireless network
A technology of cognitive wireless network and trust management, applied in the field of trust management based on nested game
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
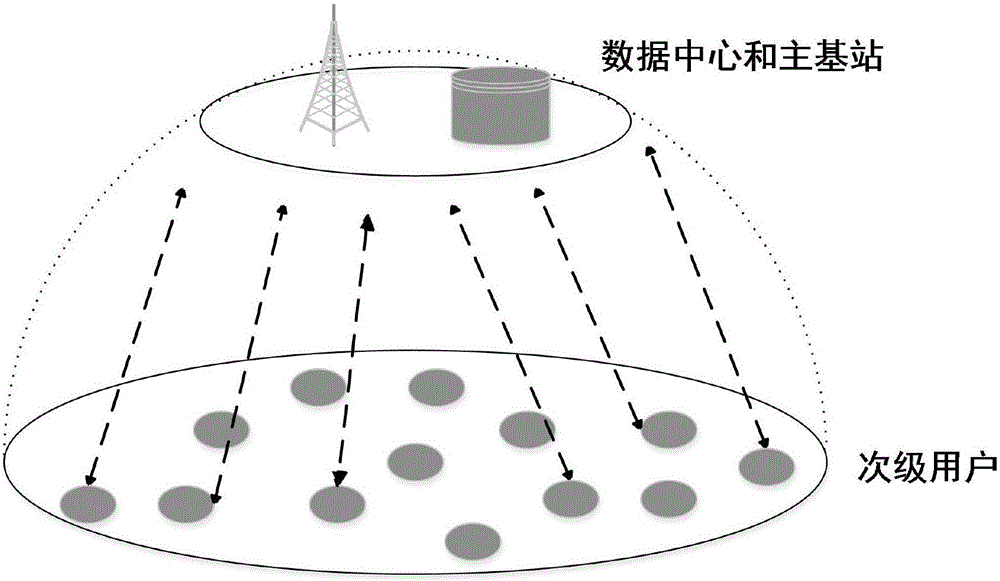
[0057] The application scenario of the present invention is a central cognitive wireless network. The secondary users in the network are located in the same geographical location, and there is a data center to record user behavior and store the user's reputation value. communication.
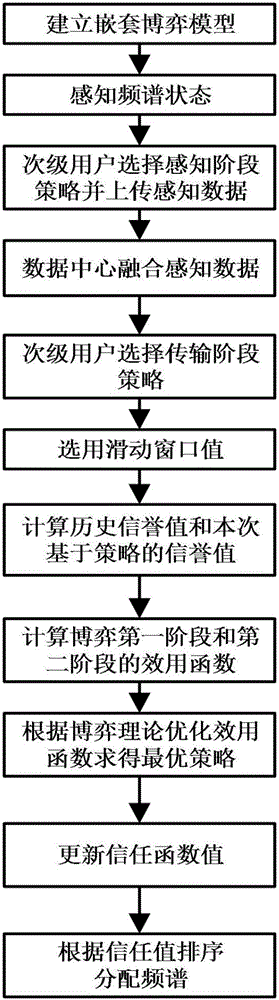
[0058] Such as figure 1 , 2 As shown, the present invention provides a trust management method based on nested game in a centralized cognitive wireless network, which is characterized in that it includes the following steps:
[0059] Step 1. Build a model:
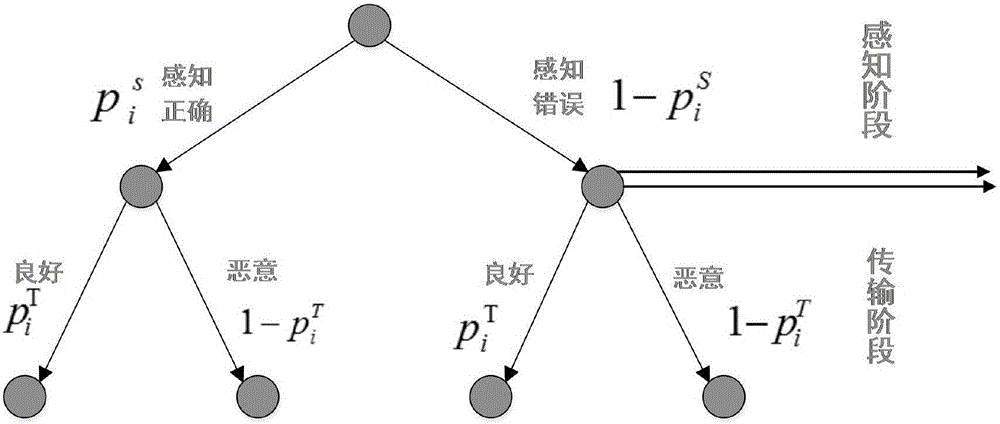
[0060] The activities of the secondary users in the central cognitive wireless network are divided into two periods: the perception stage and the transmission stage, and a game model is established according to the behavior of the secondary users in the two periods. The game tree model is as follows: image 3 shown.
[0061] Step 2. The secondary user perceives spectrum status information:
[0062] For secondary users participating in s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com