Stream data analysis based Web attack real-time and online detection system
A detection system and streaming data technology, applied in the transmission system, electrical components, etc., can solve the problems that it is difficult to meet the real-time requirements of massive log data analysis, and does not consider the real-time detection requirements of Web attacks, so as to improve processing capacity and timeliness, Guarantee real-time performance and reliability, and realize the effect of load balancing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with accompanying drawing.
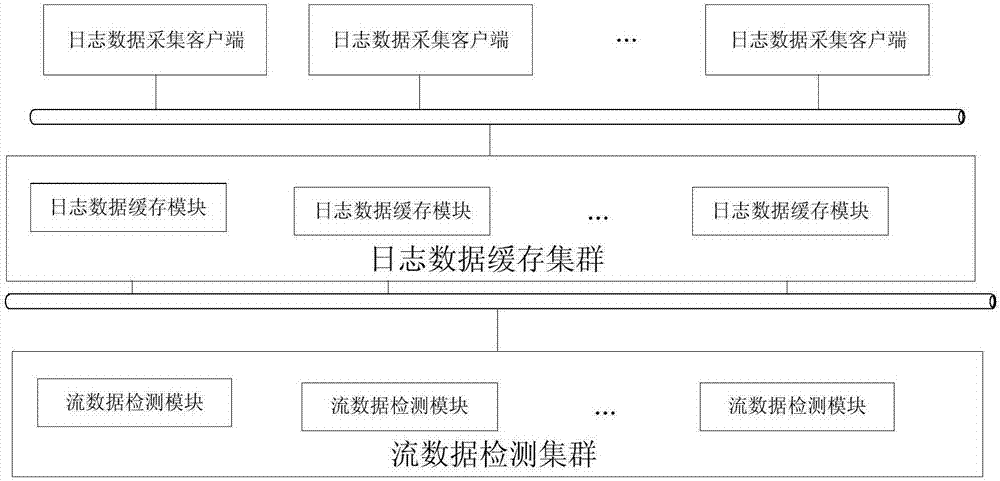
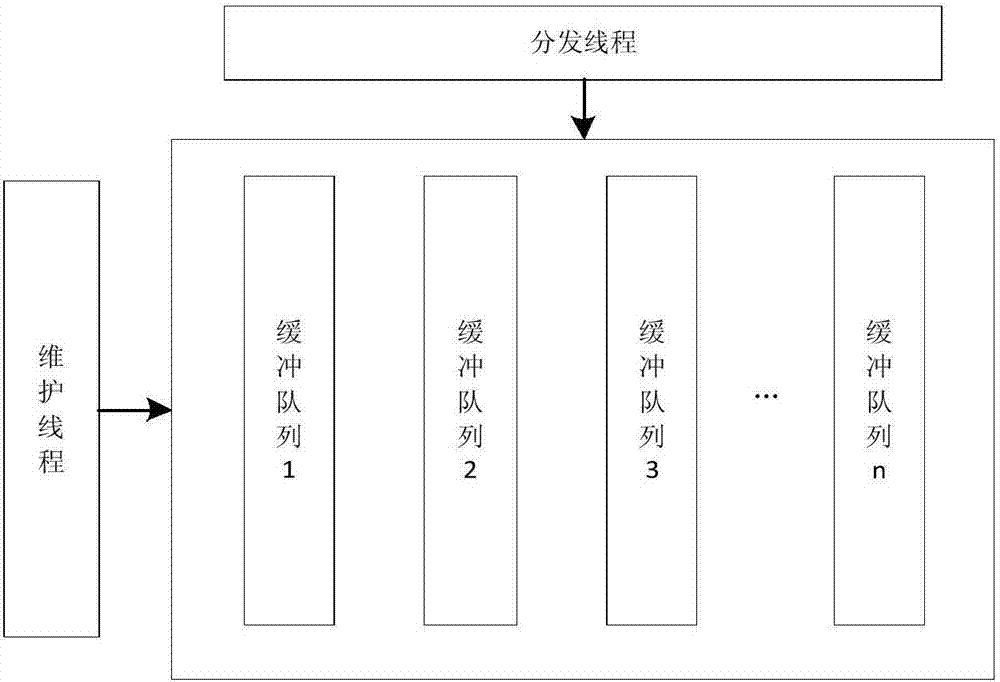
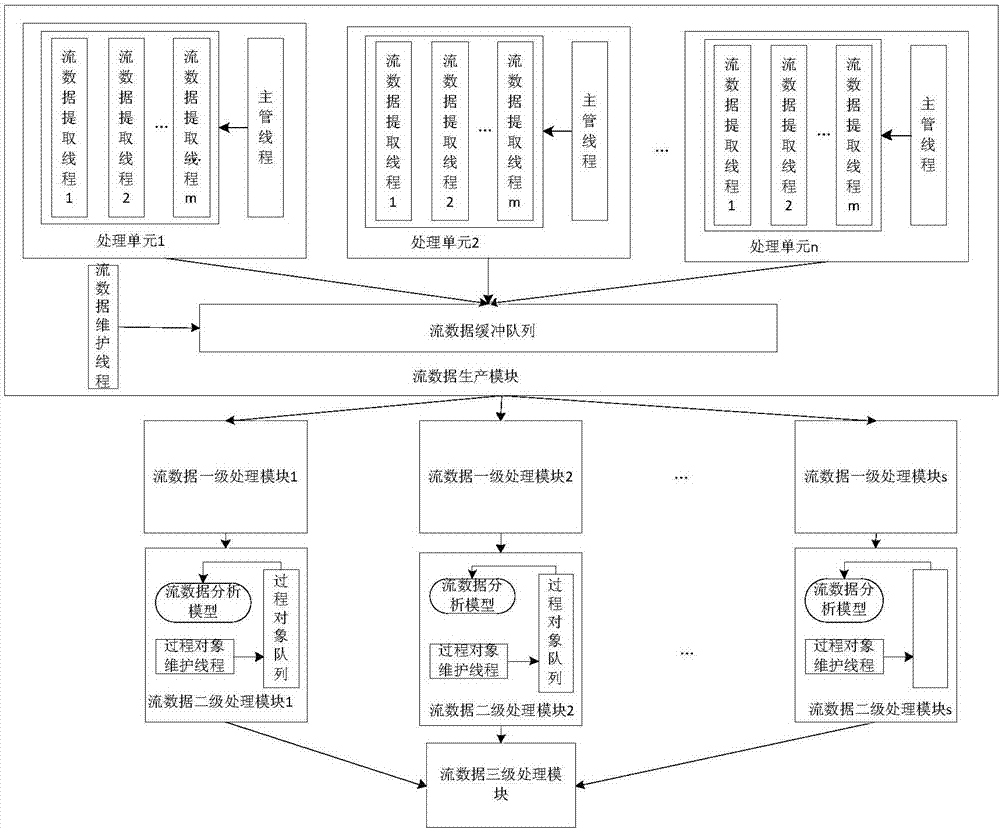
[0035]This embodiment is implemented through the following process. In the first step, a real-time online detection system for web attacks is built. The system consists of a log data collection client, a log data cache cluster, and a flow data detection cluster. The log data collection client is a client software that encapsulates the information system application server logs into a Syslog (a standard used to transmit record file messages in an Internet protocol network) message format. The common open source Syslog software is NXLog And Evtsys, the present invention for using Syslog software on Windows and Linux hosts is NXLog. The log data cache cluster consists of k (k>1) log data cache modules, which are connected to the log data collection client and the flow data detection cluster through Ethernet. The stream data detection cluster consists of r (r>1) stream data de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com