Traffic safety control method and system based on DPI and cloud synchronization
A technology of security control and flow control, applied in transmission systems, electrical components, etc., can solve problems such as only finding WIFI providers, overwhelming free WIFI, and inability to achieve real-name Internet access, achieving significant social and economic benefits, Alter unsafe, broadly inclusive effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
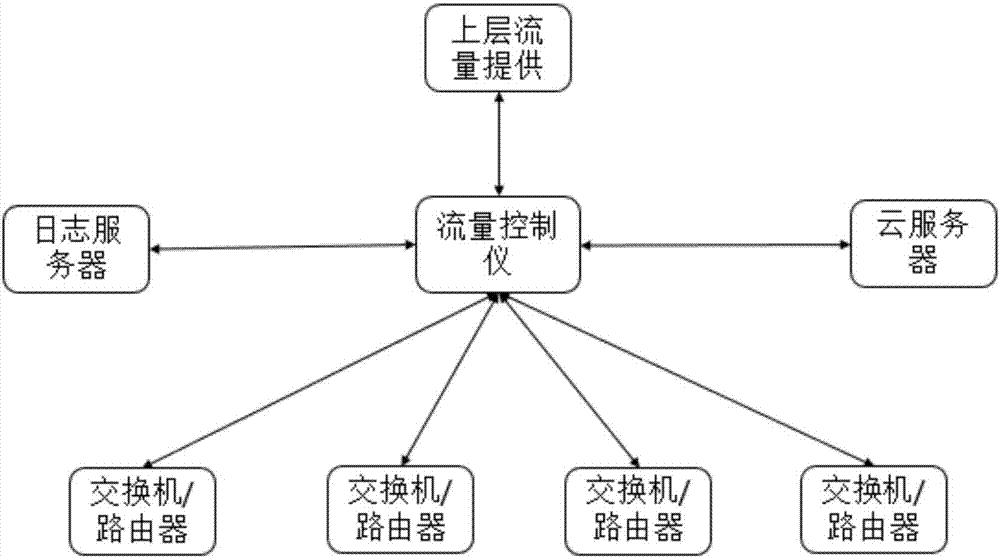
[0030] see figure 1 , the present invention provides a DPI-based and cloud-synchronized security traffic control system, including a traffic controller and a log server, a router / switch, a cloud server, and an upper-layer traffic provider respectively connected to the traffic controller.
[0031] Flow controller: used to realize the function of flow analysis, detection and filtration. At the same time, the system log will be uploaded to a dedicated log server, which is convenient for later error analysis and system tuning.
[0032] The flow control device is provided with a malicious website filtering module, a malicious behavior identification and response module, a VLAN isolation module and a secondary authentication module.
[0033] The malicious URL filtering module uses cloud synchronization technology to synchronize the malicious URL stored in the cloud database to the AP. When the user issues a command to visit a website, the AP will match the URL with the URL in the m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com