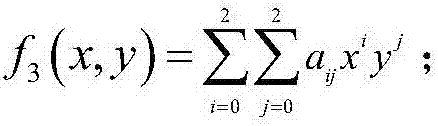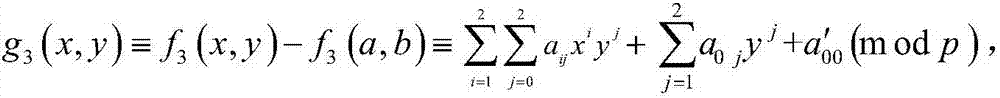Noiseless fully homomorphic public key encryption method based on binary truncated polynomial ring
A binary polynomial, public key encryption technology, applied in the field of fully homomorphic encryption, which can solve the problems of too long keys and ciphertext, and low efficiency of ciphertext homomorphic computation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
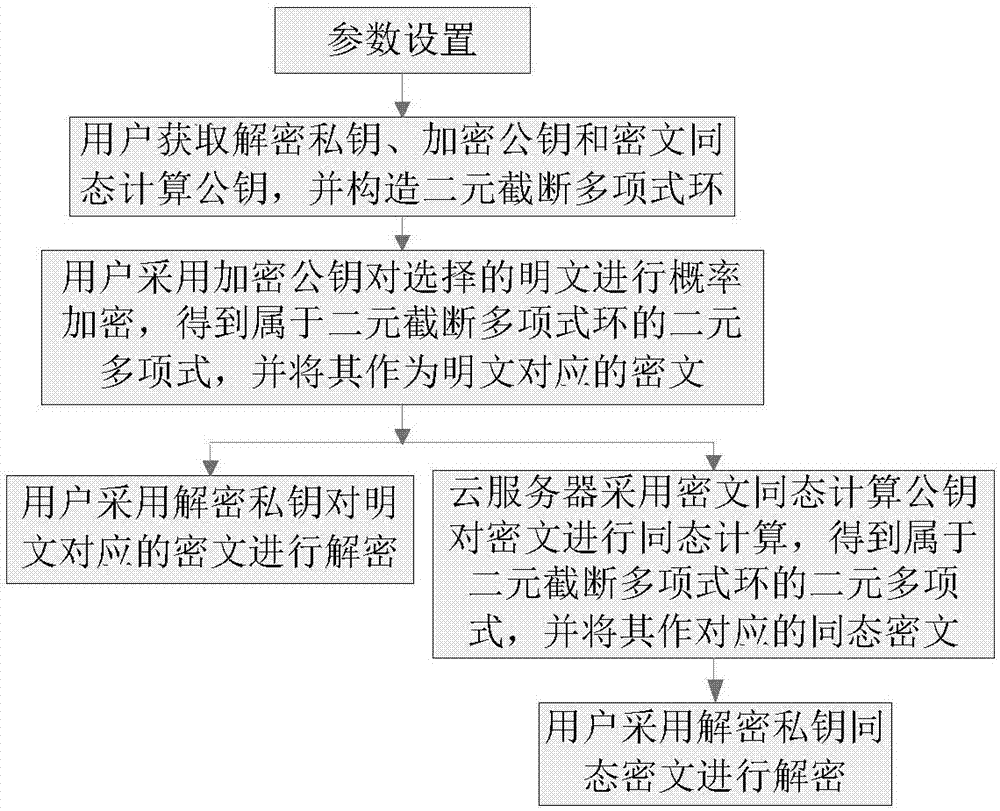
[0049] Refer to attached figure 1 , a noiseless fully homomorphic public key encryption method based on binary truncated polynomial rings, the implementation steps are:
[0050] Step 1) Parameter setting: the user sets the security parameter k according to his own security requirements, and defines the plaintext space M={0,1} k-1 is the set of all k-1 bit long integers, where k=1024;
[0051] Step 2) The user obtains the decryption private key sk and the encryption public key pk E Calculate the public key pk homomorphically with the ciphertext H , and construct the binary truncated polynomial ring The implementation steps are:
[0052] Step 2.1) Under the control of the security parameter k, the user randomly generates two large prime numbers p and q with a length of k bits, and calculates the RSA modulus N, N=pq, and then respe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com