Computer network safety control method
A computer network and security control technology, applied in data exchange networks, hardware monitoring, digital transmission systems, etc., can solve the problems of inability to warn and block, low security, inconvenient use, etc., to improve monitoring efficiency, shorten length, The effect of reducing the amount of data transferred
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
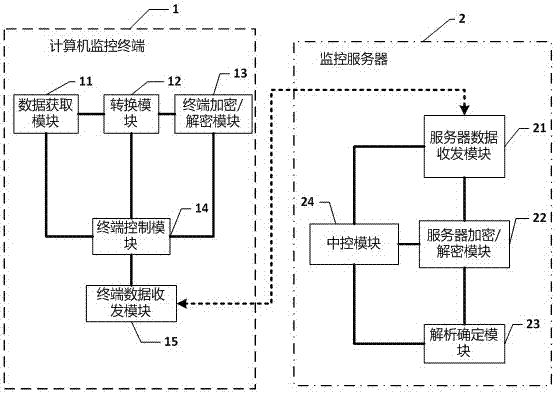
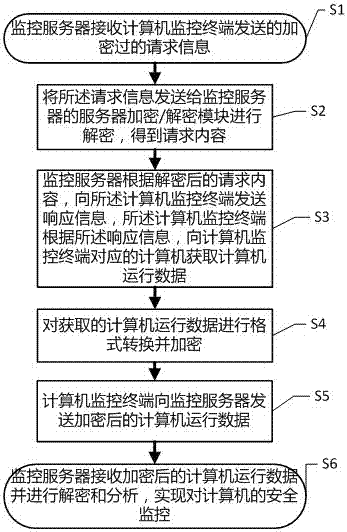
[0052] figure 1 is a block diagram showing a computer network security control system of the present invention. The monitoring system includes a plurality of computer monitoring terminals 1 and monitoring servers 2 .
[0053] Wherein, the computer monitoring terminal 1 includes: a data acquisition module 11, which is used to obtain the operating data of the monitored network computer; a conversion module 12, which is used to convert the acquired computer operating data into numbers according to a preset strategy, and obtain data to be encrypted; The terminal encryption / decryption module 13 is used to encrypt the data to be encrypted according to a preset encryption algorithm to obtain encrypted data, and can also be used to encrypt request information; the terminal control module 14 is connected to the data acquisition module 11 and the conversion module 12 And terminal encryption / decryption module 13, is used for controlling each module of computer monitoring terminal, and s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com