Network verification system based on fingerprints and verification method thereof
A verification system and verification method technology, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve the problems of cumbersome user name and password input process, poor user experience, etc., and achieve efficient entry and network reconstruction. Easy, match to find convenient effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
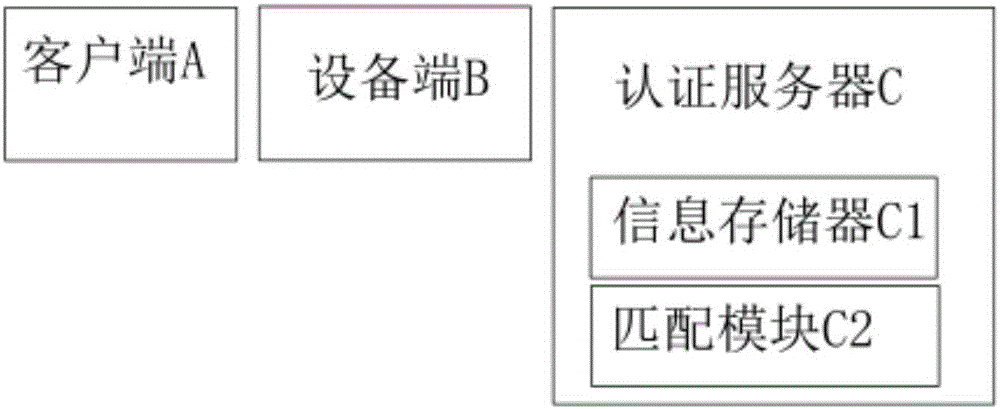
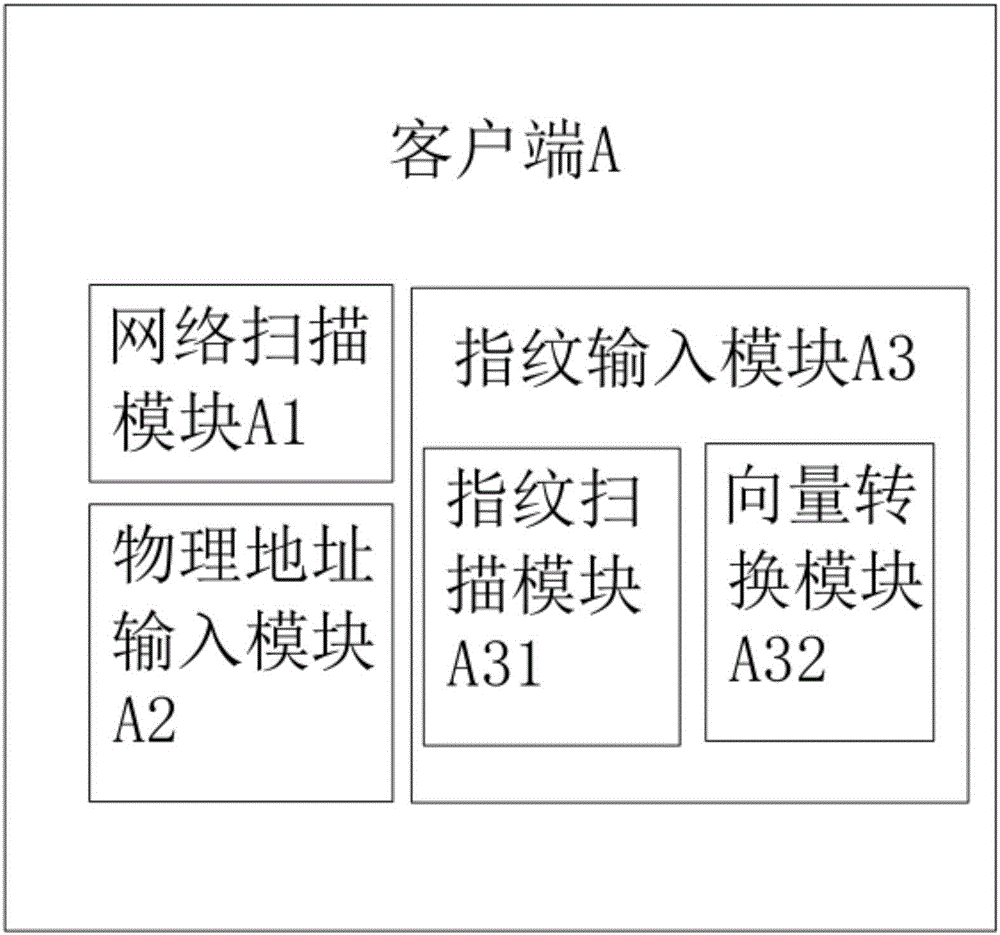
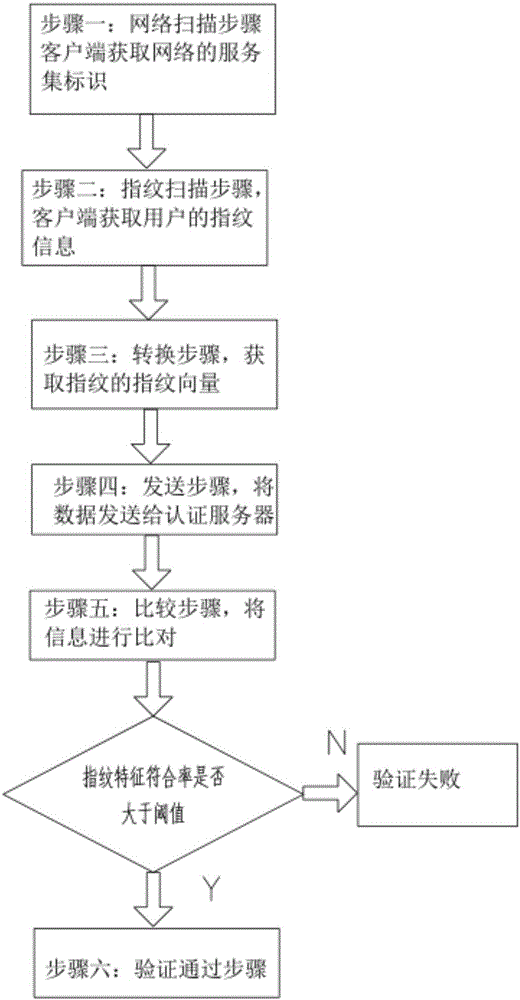
[0035] Embodiment 1, as described in the background of this article, with the development of mobile Internet technology and the hardware update of mobile smart devices, more and more people use mobile smart devices to connect to the Internet. In order to solve the network security problem of WLAN, the 802.1X protocol is proposed, which is widely used in Ethernet as the access control mechanism of LAN ports, and it is used to solve the problems of authentication and security in Ethernet; 802.1 Protocol X is a port-based network access control protocol, and port-based network access control refers to the authentication and control of the connected client at the port of the LAN access device. If the client can pass the authentication, it can access the resources in the LAN; if it cannot pass the authentication, it cannot access the resources in the LAN.
[0036] In this technical solution, the hardware construction of the entire network verification system has not changed much fr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com